
Index:
UPDATED ✅ Do you want to know about zero-day attacks and how they affect the user? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
you will meet what is a vulnerability or zero-day attack and what is it for. It will be necessary for you to continue reading until the end because you will find all the related information on this important topic.
Pay attention to every detail, you will know what the Main methods used to perform a Zero Day vulnerability and what is the goal of a hacker who performs this activity.
we will explain how these attacks affect users and it is dangerous or not for your security and personal information. Finally, you will find the main controversies about the Zero Day Ethic. Check out.
What is a vulnerability or zero-day attack and what is it for?
to understand what is a vulnerability or a zero-day attack it is necessary to take into account how computer programs are composed. The software is developed with a large number of codes, which are usually formed with already designed structures joined by new ones to each other by processes carried out by the developers themselves. On other occasions, the software programming schemes are made entirely with the programmer’s ideas.
By joining or using the development codes it is common to find vulnerabilities, which are windows or failures of the information system that can jeopardize the operation, integrity and management of the program. This weakness also it can be a window through which a hacker can enter and steal information Confidentiality of users, for this reason every time a vulnerability appears, it must be corrected as quickly as possible through patches or updates.
Analyzing the above, it is possible to understand what a zero-day attack is. It is understood as a Zero Day vulnerability attack that has software that was released, which is detected by intruders before it is known by the developers themselves. This means that there is no patchas the programmers don’t know where the bug iswhich is exploited by hackers and cyber attackers to achieve their goal.
Within the concept of vulnerability zero-day finds the method or zeroday exploit code, which is used by the attackers to advance on the vulnerability found and that does not yet have a patch. When using that exploit while the bug was not fixed, This technique is known as a zero-day attack.
What are the main methods used to perform a Zero Day vulnerability?
The Main methods used to perform a Zero Day vulnerability of an operating system, app for mobile phones, IoT systems or open source components are varied.
We show you the most common:
- Email: It is the main method used by cyber attackers to access the source codes of a program. It is about sending emails from mailboxes that seem safe or using names of frequent contacts, generating confidence to open links or visit malicious pages. Once you enter or click on these links it is possible to enter the software development structure.
- Scan to a web page: Another tool chosen by attackers is to directly know the codes through advanced scans with which vulnerabilities can be detected.
- Download the application or any program as a true user: A quick way to access bugs found in software is to become a user. That is, attackers download or register on the platform to learn about the features, available tools, and work it performs. Through your experience, it is possible to detect what types of plugins or codes were used, which can generate windows to enter.
- Attacks on the server database: It is common to find DoS attacks used by hackers to limit system service to legitimate users, which can be used to learn about weaknesses in software development.
- Implementation of codes in web pages: This type of tool is used to detect vulnerabilities in different online programs, but especially in browsers.
- Applications to open special documents: The intruders carry out the development of these programs to be used and detect the failures, with which it is possible to open the vulnerabilities of the system.
What is the goal of a hacker who performs a zero-day attack?
The goal pursued by a hacker who performs a zero-day attack is:
- Steal confidential information of the users.
- collapse the page or the program.
- Generate mistrust within the community about an app, operating system, browser or any other computer development.
- Prevent growth in the market of a competing program.
- make threats to countries or governments.
- limit development of articles related to the Internet of things.
- attack the image of some powerful person or organization.
How do these attacks affect users? It could be dangerous?
Zero-day vulnerability attacks pose a high risk to users of applications, programs and any technological development. This is because when cyber attackers detect a flaw they can access the software database, in which they are hosted. all the data related to the privacy of these people and also the financial and economic information.
Knowing this information, intruders can use in the most beneficial way for them Personal information. This causes users of software with zero-day vulnerabilities, for example, to see purchases made with credit cards that were not made and withdrawals from unauthorized bank accounts. In addition, there may be an exposure of your personal and family data in public places, which may affect your interests.
Zero Day Ethics What are the main controversies surrounding these practices?
Please note that some Zero Day Attack analysts spend their time finding vulnerabilities and then selling them to other developers or companies interested in weakening their competition. But this is not the only point of view that can be analyzed, since there are organizations dedicated to finding zero-day bugs which are sold to the same designers or not so that they continue investigating and a better product is achieved.
under certain parameters the sale of vulnerabilities can become legal, so there are controversies around these practices. The information security companies they must choose whether the zero-day bugs found in their studies can be sold.
And if the answer is positive, Who should they give this valuable information to?. To their own owners? To the competition? To other companies that are programming similar software and can affect users? Or, keep the information and get a very profitable financial reward.
Tips to protect yourself from a Zero Day attack on your favorite apps and programs
For protect you from a Zero Day attack on your applicationsfavorite programs and web pages keep these tips in mind, which will remain protected at all times.
Look below:
Pay attention to phishing activities
The phishing It is a frequent activity that tries to deceive the victim through a false identity, which generates an appearance similar to that of a reliable platform for the user. For this reason, to prevent this remote attack and prevent a hacker from enter your databaseyou have to pay attention to the name servers and databases that you use frequently for your favorite applications and programs.
This means that, the cyber attacker will try to impersonate the server where you have the software hosted, by recognized and trusted plugins that you have used or by any other platform necessary for its computer development. Pay attention to details and do not write your personal data or password to entereven more so when you should never go through this process to enter your provider.
Avoid opening emails
Remember that to access applications or programs, hackers have to enter the structure of your development codes. To do this, one of the routes most chosen by criminals is email. Through this tool they send links so that you press them and make the exploit codes start doing their job. It is also common to use emails to send invitations to visit harmful web pages, which contain documents that manage to explore vulnerabilities.
For this reason, never open an email from a stranger or from those contacts with whom you maintain another type of conversation. Always verify the sender’s email address, this will help you quickly detect the veracity of the identity of your friends, family or co-workers. If you do not recognize the names or the mailbox, it is recommended not to open them.
Domains with HTTPS protocol
If you have a web page it is necessary that it works with the HTTPS security protocol. This method prevents third parties from knowing the information that is transferred from the server to the user, so it is difficult to intercept and listen to the conversation between the two computers.
So that the HyperText Transfer Protocol Secure protect data transfer you will need to buy the HTTPS certificate, activate it in WordPress and change the addresses urls from the server database. Then you have to notify Google that you have performed this action to perform its checks and make the changes.
Protect yourself from DDoS attacks
Denial of service attacks attempts to crash the page through excessive malicious traffic. This makes users cannot access and that attackers can find weaknesses more easily. To prevent attacks on the infrastructure layer and OSI layers 6 and 7, you need to use efficient firewalls.
Besides, the antivirus implementation updated is very helpful because it quickly detects the presence of newly created viruses and exploit code. But you should not only keep the latest version of the antivirus but also the operating system you use on your computerr for the development of the application and your favorite program.
Do not forget that a good idea to prevent this type of cyber attack is the use of virtual private networks. Thanks to a VPN provider you will prevent the IP address is easily detected. Finally, you can frequently reset the IP, for this you will need to disconnect the router for a few minutes to regenerate a new address.
Check that your apps do not have Trojan viruses
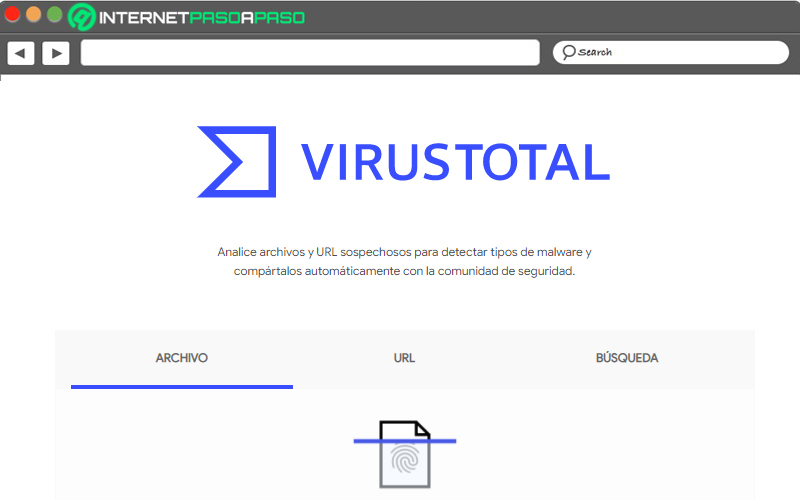
A good way to checking that your applications do not have viruses, malicious codes or Trojans that can detect zero-day vulnerabilities is to use the VIRUSTOTAL platform. To do this, you will need to enter with your trusted browser and write in the address bar https://www.virustotal.com/gui/home/upload. Then you can choose if you want to upload a file, a urls or a link.
You can also perform this process automatically and periodically using the API of the platform. Enter to https://developers.virustotal.com/reference/overview and lower the programming interface.
List of the most popular and famous Zero Day attacks so far that you should know about
exist zero-day attacks that became famous because of the platform on which they found the Zero Day vulnerabilities. Get to know the list of these popular attacks so that you are aware that even the largest projects can be victims of these cyber attacks.
Look below:
Chrome – 2021
A JavaScript weakness was detected in the V8 enginewhich affected the functioning of the freed memory with which arbitrary code could be executed within the browser. It also affected security, since it allowed the leak of user information. The bugs were named CVE-2021-37975 and CVE-2021-37976.
iOS-2021
The Apple mobile phone and tablet operating system suffered an attack of zero-day vulnerabilities with which cyber attackers could break into iPhone and steal private information. Errors were reported as CVE-2021-1782, CVE-2021-1870 and CVE-2021-1871while in the year 2020 it was possible to know CVE-2020-27930, CVE-2020-27950 and CVE-2020-27932 as vulnerabilities.
Zoom-2020
Through this weakness the attackers could enter the computer of a user who used the videoconferencing platform, as long as the Windows operating system is not updated. The risk increased when the attacked was the administrator.
Windows-2019
The bug found as a zero-day vulnerability allowed attackers to execute actions and change information in downloaded applications. This was not the only error found in Microsoft, it is also possible to mention the year 2017 where the text editor Word compromised the bank account information of the registered user.
Informatic security