
Index:
UPDATED ✅ Do you need to know how a Bluetooth wireless connection works? ⭐ ENTER HERE ⭐ and discover everything about it ✅ EASY and FAST ✅
Bluetooth technology is one of the tools most useful and used that exist today. Thanks to it we can perform different tasks in our homes without having to move too much. We can control different equipment through our mobile and computer, providing us with a high level of comfort.
There are two versions of Bluetooth that are used today, with version 2.0 being the most widely used and with which up to 3 Mbps can be transmitted. Manufacturers of electronic equipment add this technology to their products on a mandatory basis because they understand that, without her, her equipment will be out of the market.
In this article we will talk to you how this data transmission system works and how we can build a network of 8 nodes via Bluetooth.
What is a Bluetooth connection and what uses does it currently have?
![]()
Bluetooth is a technology that uses the IEEE 802.15.1 wireless communication standardby which two devices can communicate with each other through a low-power radio frequency of 2.4 GHz and can thus transmit data and voice packets.
This technology was born from the research carried out by the Erikson company and is named after King Harald Blåtand and can be classified into four classes according to the range that radiofrequency waves can have.
class 1 up to 100 metersthe second category reaches up to 10 metersclass 3 has a limit of 1 meter and the last one is for 0.5 meters.
This technology is present in mobile devices, computers, digital cameras and also in printers, so its use today is linked more than anything to the transmission of information between these devices that we have named.
But we cannot also leave aside those products such as garden irrigation equipment, microwaves, security cameras, wireless speakers, car audio equipment, among others, in which we will also find the Bluetooth logo and its operation is closely related to this kind of data transmission.
How does a Bluetooth connection work? Process phases

To explain how the connection of two nodes via Bluetooth works, we will first have to mention the conditions that are needed for it to work.
The working conditions that this technology needs are:
- Through a physical arrangementwhich is necessary for this function to be activated in order to transmit the data we need via radio frequency.
- The second condition is from a protocol point of viewwhere it is required as a requirement that there be mutual authorizations of the devices to link to each other or for one to control another team.
Once these two conditions are met, the Bluetooth process is very simple since a transmitting device sends the data via radio waves, being received by other electronic equipment.
This last equipment decodes this data according to different previously assigned protocols and translates them into a conventional format for understanding. This happens thanks to the installation of transmitter and receiver plates that each device has.
What is the data limit that can be passed in a transfer via Bluetooth?
There are different limitations that this technology presents to transmit information to another device
We can name some of them: the low transfer speed, the distance between the equipment has to be correct and try to ensure that there are no interferences between the devices to be connected.
With this we can conclude that data size limit is not a system weaknesssince the entire amount of data needed can be transferred, the limit will be set by the memory capacity of the receiving device.
We must consider at this point that it is also necessary to have a significant battery charge so that the mobile device does not turn off when we are making the transfer, since it will be annulled.
What are “Piconets” in a Bluetooth system?
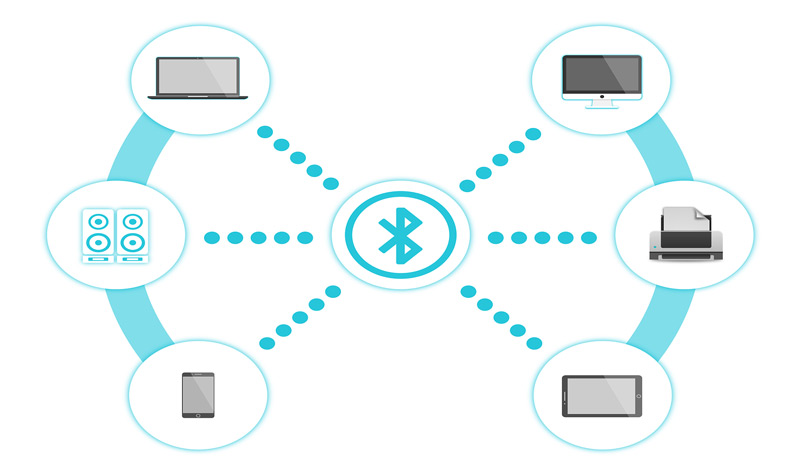
When we connect two devices through this technology what we are doing is creating a small network between them, if we can join more devices to this network we are going to have a computer network named Piconet. The Piconet set is called Scatternet.
in which it consists of having one master device and up to 7 slaves, since no more than 8 nodes are allowed in a network formed by this technology. The master device has the function of choosing the hop to be able to maintain the link, establish the connections so that the data packets can occupy a slot in the emission and another slot to be able to receive them alternately.
Finally, the most important mission of the master computer is to generate a unique code for each of the computers, or nodes, that participate in the Piconet network and a clock frequency to be able to generate a frequency hopping sequence.
This type of network is very common today for those places where there are different electronic devices that need to respond to a computer to broadcast, for example, videos, music and any other entertainment element without the need for cables in sight. the users.
How secure is a Bluetooth wireless connection?
Being a technology that is based on radio wave transmission, there is a need to take precautions so that no unauthorized device has the possibility of intercepting the information we exchange or being able to access our device.
The most known dangers of hacking through Bluetooth technology are the following:
- Bluejacking attack: Which is a method in which messages can be sent anonymously through our mobile to different devices close to ours and that are connected with Bluetooth.
- Car Whisperers Method: This attack is based on the fact that most car audio equipment needs a 4-digit password to be able to connect with the driver’s mobile, so they are much easier to hack. Once this key is decrypted, the attacker has all permissions to access the device.
- Bluebuggin access: Which consists of remotely accessing our mobile via Bluetooth, even allowing us to manage our entire device without us realizing it.
Based on these dangerous methods, security measures were developed, both at the device level and for the service. Working these two variables at the same time can protect devices with this technology in a perfect way and thus do not allow the transmission of data from unauthorized users.
We recommend having Bluetooth mode enabled as “not detectable” either “invisible” so that we can only connect with those devices that interest us, and at the same time also keep in mind the identification procedures to be able to carry out a correct connection authorization.
Computing