
If we are tired of stealing Internet signal and because of this we have a very slow browsing connection, there are different alternatives offered by our router to strengthen the security of access to WiFi.
One of those tools is making the router signal invisible . With this we will get many benefits that we will analyze in this article.
In addition, we will focus on the steps that we will have to perform to configure the router and on each of the tips that we must keep in mind to have an efficient configuration. Finally, we will show if it is true that by setting the signal invisibly we lose browsing speed .
Index:
Why should I make my WiFi signal invisible? Benefits

Making the WiFi signal invisible is nothing but hiding the broadcast of the SSID. That is, devices that are near our router will not be able to detect the signal from our wireless network .
This is due to the configuration that we can perform directly on the router. In this way it becomes very difficult to decrypt the password and enter the network clandestinely, since applications that decrypt password cannot intercept the signal.
Based on the last paragraph, we will demonstrate the most important advantages of this tool offered by the router:
Decrease the possibility of hacking
People who want to access our wireless network must enter through an 8-digit number that supplants the password. In order to carry out this task, the intruders carry out a massive verification of these PINs , until one that is in their database and with the corresponding one of the router matches.
When we make the WiFi signal invisible, it is very difficult for these people to be able to perform this massive PIN attack task since, since they cannot intercept the signal, the programs they use cannot efficiently perform your task.
Increase our privacy

We rarely consider this topic . When someone hacks our WiFi, this person has access to the devices that are part of the wireless network, being able to access confidential information or data that would jeopardize our privacy .
Therefore, when we turn the WiFi signal invisible we are also protecting our security.
Nobody will ask us for the password
Using this alternative configuration we will avoid personal commitments where people who come to our house ask us for access to WiFi. We will also avoid situations committed to neighbors who are often those who disclose our access password .
Only authorized devices will be able to access
It is true that this is the main objective of the configuration of making the WiFi signal invisible, but what we want to demonstrate is that we will have absolute control of the devices that access the network since , as we will see later, to connect you need to enter the network name plus the password.
Therefore, by having the SSID intervened, we will also have access to it monitored by the double control it requires.
Steps to configure your router and hide the Wi-Fi signal easy and fast
The steps necessary to configure the router are as follows:
We get router IP
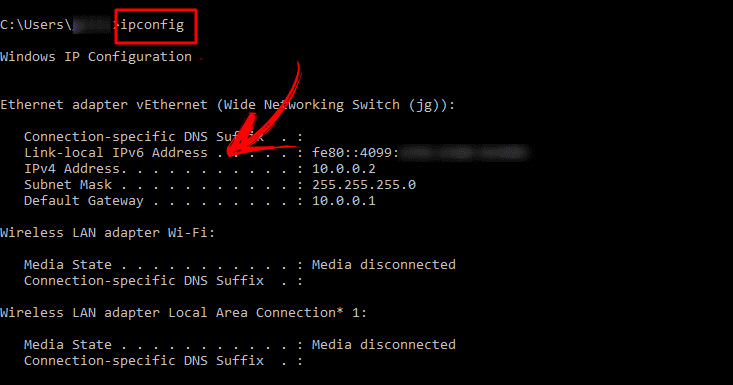
This data can be taken from the box where the router came or from some tag attached behind it. Another alternative is search on the Internet what is the default IP address that brings the brand of our router.
What we want to show you is not the previous alternatives, but through the use of a command that allows us to use Windows.
For that, we will do this guide:
- Press “Windows + R” .
- We type the command “cmd” and we give “Enter” .
- A black DOS window will appear.
- We will immediately type “ipconfig” and click on “Enter” .
- It will show us a series of data such as the subnet mask, the MAC address and the “Default gateway” .
- We copy the numbers of this last option and we will write it in the next step.
Enter the router interface
At this stage we will do this process:
- Once we have copied the Default Gateway we write it in the address bar.
- The configuration access window will appear in the browser of the router, so we will have to enter the username and password.
If we have never changed this data, according to each brand of the device, the username and password is “admin” for each of the fields.
Select the option “Wireless”
Once inside the control panel we will follow these instructions:
- We go to “Wireless” , in some other devices it can appear as Network or WiFi.
- We look for the option “SSID Broadcast” .
- We deactivate it.
- We click on participant accept.
Check the configuration
To verify that we have performed these processes well, we will have to enter with our mobile device and click on the WiFi icon , provided we have this option enabled.
At this moment we are going to get a list with all the wireless networks available around us, so ours should not appear on that list .
To enter we will do:
- Click on our mobile in “Add a network manually” .
- We manually write the name we put to the WiFi signal.
- We enter the password.
- We click on clearlyAccept / strong> .
If all the steps have been done correctly we should be within our network whose signal is invisible.
Will it affect the speed of my Internet to make the wireless network invisible?
The Internet connection speed is related in the first place, with the service we have contracted with our operator and secondly, due to the level of occupation that the channels of the frequency of our router .
Recall that a modern router device works with two frequencies, one of 2.4 GHz and the other of 5 Ghz . The first one has 13 channels while the highest frequency has 22 channels with a much wider band so the data travels more efficiently.
That is, with everything we’ve talked about, speed has nothing to do with the configuration of the SSID broadcast , but with the number of devices that transit through each of the channels of the respective frequency and the service provided by the operator.
Tips to configure your router and that nobody connects to your network and no one connects and improve your security

In addition to making the WiFi signal of our network invisible, we can perform other tasks that will allow us to be more efficient with respect to router security.
To shield our router and nobody connects, we need to take into account the following aspects:
Change the password encryption protocols
Encryption security protocols are those procedures or parameters that allow a more or less secure connection according to the integral parts that they have in the process of data connection and privacy.
In this way we recommend using passwords with WPA2 or WPA encryption , where the possibility of accessing the router by entering PINs, according to the MAC address, will be very difficult to succeed.
Perform filters by MAC address
This tool allows us to make a selection of the selected devices through the identification of the network card that the manufacturer introduced, that is, the MAC address.
In order to perform MAC filtering we will have to follow the following steps:
- We select the option accounWireless†.
- We go to “Filter by MAC” .
- We activate this option.
- We enter all the devices that will be authorized to enter the network.
- We click on “Add” .
- We press permittedAccept .
Decrease the signal range
We have the possibility of decreasing the signal range of our WiFi network, which will help to some extent reduce the possibility of intercepting the signal.
While it is true that this is not a concrete measure, but will benefit from using in conjunction with other aspects that we have mentioned.
To make this configuration we go to Windows:
- Control Panel
- Device Manager
- Network Adapters
- Advanced Options
- Transmit Power
- We choose the range
- Accept
Change factory password
A very simple and concrete security measure is to change the factory default password immediately when we receive the router device . This will prevent third parties from carrying out, through applications, attacks on the router and deciphering the password for entering the wireless network.
Perform audits with third-party app
Third-party applications will help us to control the entry of intruders because they will carry out work in a systematic and programmed way in their audit. There are different applications that we can install on our mobile device or computer.
We recommend “Who uses my Wifi? Network tool ”.
With this kind of tools we can immediately expel intruders . It also allows us to obtain a history of the connections of the different devices.