
Wi-Fi is a type of signal used at home, office and other workplaces, to provide access to the internet wirelessly and at high speeds in a completely secure way.
However, there are times when for some reason unknown devices are connected to our network, bringing with them different inconveniences and putting the security of all connected elements at risk.
For this and much more it is necessary to know how can you see the devices that are connected to a Wi-Fi network? In this tutorial we will explain what methods you can use to solve all these inconveniences.
Index:
Disadvantages of connecting to your WiFi to steal your internet
There are different disadvantages, inconveniences or dangers of unknown or foreign people connecting to your Wifi network and stealing the signal for your own use.
It should be clarified that by illegally using the service that another person is using and has acquired, adding that in turn only that person is paying, is a robbery. > If for some reason, the owner of the service has given his password to another person, only that person can connect.
Among the disadvantages of that strangers steal your Wi-Fi are:
Slow internet speed
This is the most common disadvantage, and is the main symptom that others are connected to your network without your permission. Although it may not seem so, this can cause many inconveniences and great inconvenience to the person affected.
For example, if you are the type of person who likes to watch your series or movies in top quality, play online, perform multiple downloads, work remotely and online, upload images or videos in your work media, etc. .
Being slow in your browsing speed can worsen your feeling on the platform where you watch your movies, even affect your experience or game level. In the worst case, it can generate failures or noncompliance in your work, since it was uploaded and delivered later than requested.
Insecure WiFi networks
This happens when unknown people have access to your Wi-Fi network, this allows them to observe a wide variety of personal information, browsing data or clone web pages like your bank’s, to subtract money from your accounts or change their password.
Illegal activities
In addition to being a victim of information theft, the person who is stealing your wifi may be performing different illegal tasks that can be very serious, such as cloning credit cards, illegal downloads, selling Child pornography, generating phishing, and a long etc in digital crimes.
The worst thing about this case is that when it is done under your Internet connection, when these crimes are discovered, the main suspect will be you. This is because the access point is from your Wi-Fi network and directly from your network connection.
Steps to detect and check who has connected to your Wi-Fi network -Fi
There are different methods that can be used to see when other people are connecting to your Wi-Fi network illegally or without your permission, these range from observing the behavior of your router to entering the options of your router and display the number of devices connected to it.
Thanks to this, it is possible to know when unknown individuals are stealing your connection and in turn take actions to remove it:
Look at your router
If you suspect that someone outside is connecting to your Wi-Fi network, the first thing you should do is observe how your router behaves in the hours where nobody in your house is using it, or even You can ask these users to disconnect from the network temporarily and see if the device lights are blinking as a sign that there is activity on the network.
If the test is positive, there are indeed other people connecting to your Wi-Fi network without your consent.
Another option, although previously mentioned, is that your Internet is slow to navigate and download, in this case the main thing is to make sure that it is not a fault by the company. If it perform the necessary tests and it turns out that the speed is correct, because there are other people connected to it.
Using your computer
This verification method is quite extensive and in turn is the most important at the moment you want to eliminate the intruders from your network and prevent your connection from being stolen.
The first thing you should know is your IP address and in this way you can enter the router from your browser. Here you can make changes to the configuration of your Wi-Fi device and observe the devices that are making use of your connection.
In Windows 10
You just need to click on the “Internet connection” icon:
- Then you must click on the tab that says «Network», and finally choose the option of subsequentlyRed.
- A new window will open, in this you will see all the information of your connection, the one that interests you is that of your gateway or DNS servers, which is commonly 192 . 168.0.1.

In Windows 8 and 7
The procedure is a bit longer, but just as simple:
- To do this you will have to enter “Control Panel” and then select “Networks and Internet”.

- Now you will choose «Network and Sharing Center».

- You will click on the «Network» option. A new window will open, in this you will click on fullyDetails frequently.
- Look at the information in the “Default gateway” section.

MacOS
Here it is quite simple to know your ip address you will only have to follow the following procedures:
- Select the connection that you are using, this can be done from the side panel, there you will see a new window called «Network» and in this you can see your ip address.

Now you just have to enter the router to see who or what are the devices that are connected:
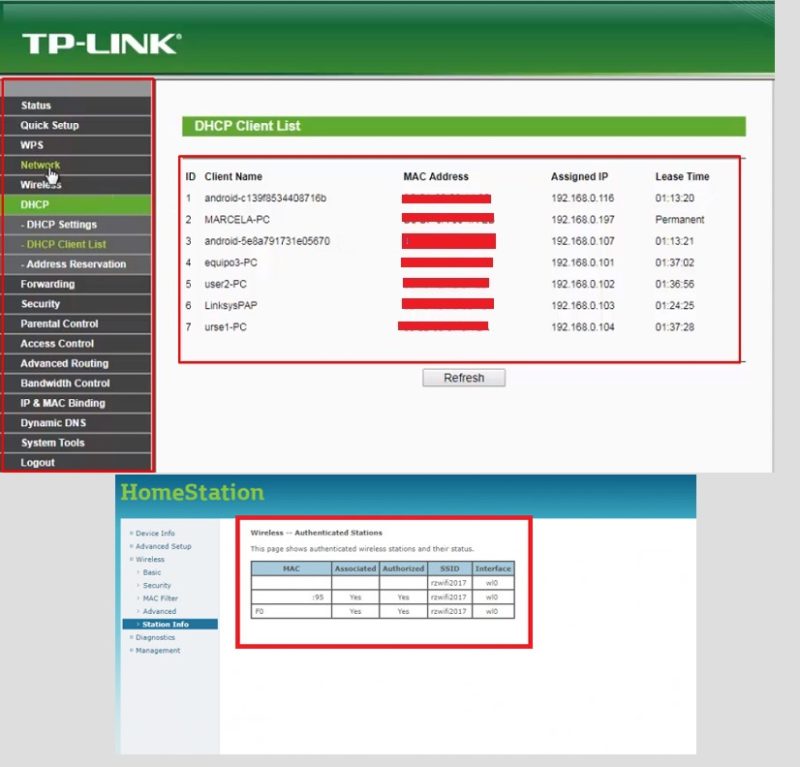
- Enter the “Wireless” option and then select the “Client list or station info” option, this alternative can be changed according to the brand and model of your router.
- You will see a list where you can see who connects to your network.
How to block and eject it to you Wi-Fi and make your internet connection worse?
It is important to know the methods and alternatives that exist to remove and prevent access to those who try to enter illegally and without your permission to your wireless Internet network.
Since although you know how to recognize when these individuals access, if you do not know how to remove them you will not be able to solve the problems that this causes:
Change your router’s key
It is the easiest method there is to expel all intruders from your network and regain controlled access to it. In addition, it is very important to have your own password and not a generic one, because this facilitates access to strangers.
Enter your router and change the password of access to your network, to do this:
- Go to the accounted forWireless permitted.
- Now choose “Wireless security” and locate the “WPA / WPA2-Personal (recommended) ».
- Select ” Password “ and enter the new password.
The name of this option may vary depending on the brand and model of your device, but mainly this has to do with security or access control. Browse between the different functions that your router has until you get the one that allows you to modify the device password.
Limit the access of equipment with MAC filtering span>
This is the best way to prevent access to unwanted users within your network, the only negative point is that depending on how you configure your MAC filtering, it will be necessary to constantly update the access data on your router.
This is because if a visitor arrives to whom you want to give access to your network or you get to buy a new device and want to connect it, you must first give it access by entering the configuration of the device.
The other way not recommended to use this method is creating a blacklist or blocked access, for this you must recognize the MAC and IP address of the device that you are not interested in connecting.
The negative of this method is that if the person changes the device, and knows ways to steal your Wi-Fi, they can always enter from any device making it null and useless to block it.
>
How to configure filtering by MAC? span >
Before starting the configuration to filter the connected devices using their MAC address it is necessary to know it, for this you just have to enter your router and look for the option that says «Wireless Statistics» to observe each one of the devices that appear and write down their addresses, which is formed by a series of numbers and letters.
You can verify the MAC address of your Android or iOS device by entering as follows:
- Open “Settings” , go to the section that says “About the phone” .
- Finally go to «Status» and copy the information that says «Wi-Fi MAC Address».
On iOS devices the process is very similar on Android.
Once you verify the addresses of all your devices, surely you can find that of that unknown element.
You can see MAC filtering in different ways, for example: MAC Filter, Wireless MAC Filtering, among other options. But will always be the word MAC associated with this function, so check carefully and mainly in the “ Wireless ” section of your router until you get it.
Now you just have to configure those devices to which you will allow access to your Wi-Fi network:
- In the “Filtering Rules” section you will choose “Allow”.
- Now you will click on «Add new» , you will add the Mac address to a short description for it, and notice that the tab is located in legallyEnanbled respectively.
- Only left press “Save”.
- Repeat this procedure as many times as necessary.
- Finally, you see that the “Wireless MAC Filtering option » is in « Enanbled » , if not, change it to activate filtering by MAC address.
Tips to prevent third parties from connecting to your WiFi without your permission span>
There are certain things that should be avoided or done periodically, to reduce irrigation or prevent others from entering your network without your consent.
Since it is important to keep your security and your personal information safe, apart from Wi-Fi theft is a somewhat embarrassing crime, and maybe you want to avoid that penalty to your neighbor for performing this activity: