
Index:
UPDATED ✅ Do you want to know more about the permissions that apps ask for and how to customize them? ⭐ ENTER HERE ⭐ and Learn How FROM ZERO!
Basically, mobile applications refer to a program that can be download and run directly from a mobile devicewhether it’s a phone or a tablet. These applications are designed to offer greater simplicity to users. by compressing a complete world of tools that will make your day to day easier.
Now, in order to operate correctly, these apps require certain authorizations that are known as “Application permissions”. Therefore, every time an application is installed on a mobile or tablet, the corresponding operating system proceeds to list a number of permissions from which the app can work.
However, despite the fact that they are so essential, in reality, there are still many users who do not know what app permissions are for, specifically. Therefore, through this post, we will explain What are these consents and what are they for?like, what are the risks that they normally reveal and how to configure them correctly.
What are app permissions and what are they for?
While it is true, app permissions consist of a security system present in each system operative that, essentially, are used to obtain an authorization on the part of the user at the time of access specific parts that store or generate sensitive data of a certain device. In other words, when installing an application, these permissions request access to certain computer resources, be it the camera, the contacts, the call log, the files, etc..
In this way, it can be highlighted that application permissions are used so that users can know what information or what data will be shared with the application in game, in order to guarantee the security of said data stored on the device. Since, only if people allow it, those installed apps will be able to read that information. On the contrary, your access will be denied.
For its part, we also highlight that these application permissions are necessary for those downloaded and installed utilities can work properly and carry out its different functionalities as efficiently as possible. Which is why practically users feel obligated to provide their data in exchange for the service provided by the application.
What are the most common app permissions that I can give up?
When granting certain permissions to the applications installed on your mobile device, it is essential that you take into account What are the authorizations that you are requesting?. Since, many malicious utilities take advantage of the innocence of users in these situations and they ask for permissions that have nothing to do with their activityso they are suspicious.
So, for example, when a camera app asks for your consent to make calls, it could be a malicious app that seeks to usurp your stored personal information for various illicit purposes.
Reason why, it is important that you know which are the most common app permissions that you can assign and here we present them to you:
Telephone
It refers to a permit that identifies when there is a call to be able to stop the operation of the application in question, basically. Likewise, by providing this consent, the app is authorized to call, view the log, read the status of the phone, know the number, add voice messages, redirect to another number, manage calls (hanging up or picking up), etc. .
Microphone
Just as its name allows us to discern it, it corresponds to an app permission with which full access to equipment microphone is provided. As a consequence, the application will have the possibility of listening to what is said, recording telephone conversations and even act as a spy microphone in any other situation.
contacts
Through this approval, the application is responsible for requesting the fact of being able to consult the list of contacts saved in the terminal. Therefore, the app in question will have complete access to the list of contacts and, apart from that, it will be able to add new ones and edit it freely. It even has the ability to enter the list of service accounts whose entry is enabled from the equipment.
memory or storage
By means of this permission, the application will have an open door to see what’s in your phone’s memory, including the external storage system (for example, an SD card). In this way, in addition to being able to read what said memory saves, you will also be able to store more files there automatically.
Camera
It is considered one of the most common mobile application permissions of all. Which, requests access to the camera app and can perform actions of this. Whether taking photos, recording videos, editing images, etc. As a consequence, also may be an assault on the privacy of the userif this consent falls into malicious hands.
Text or SMS messages
When granting this permission to a mobile application, you are provided with full access to the device’s message log, as well as messages as such. Therefore, it allows said app to send text messages (SMS, MMS and WAP Push type) and until it receives new messages and read the ones in storage.
Calendar
Automatically, based on this permission, the application that requests it will have access to the terminal’s calendar and its agenda. Therefore, it will acquire the power to read and edit calendar information, as well as create new events on it. In addition to this, you will be able to see the entries that are in it in real time.
Location
By default, it is a consent that you accept that the application can know where you are, at all timesthrough the function gps of the terminal or through the mobile antennas or the connection Wifi that you use Usually, navigation apps, maps and some gamesare the ones that require this kind of permission.
body sensors
Another of the most common application permissions that can be assigned is the body sensors. In this case, the app in play should be designed to measure your physical activity and/or provide personalized information in terms of health or sport. That is to say, they operate like the well-known activity bracelets, since the use of said devices is also linked.
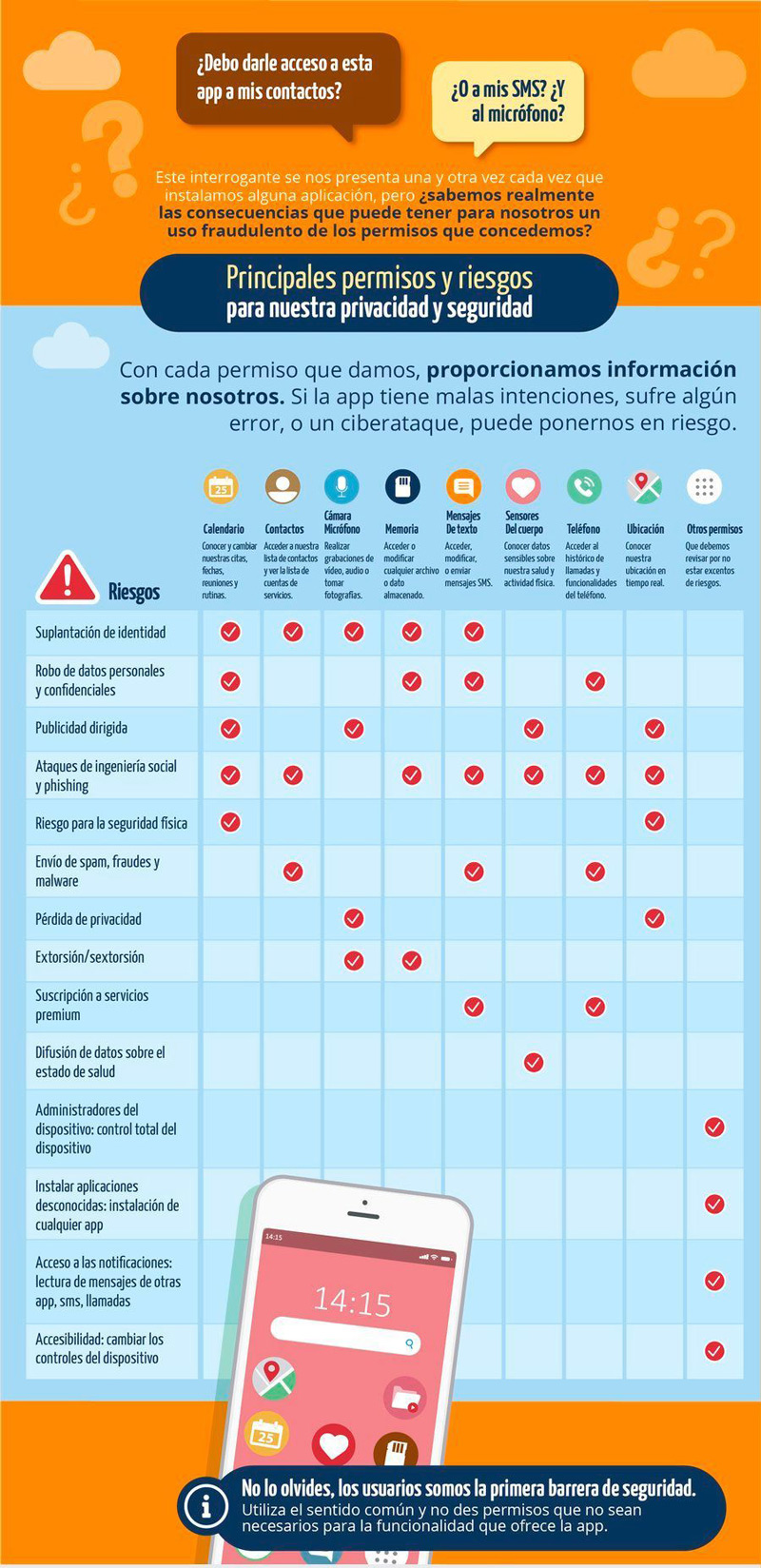
Infographic: Dangers and risks of granting permissions to APPs
Nowadays, security is one of the issues that most concerns developers when programming applications and, to the same extent, to the users of said mobile apps. Since most of them request so many permits, the latter do not know if they are putting their integrity at risk by authorizing them.
Therefore, in order to protect your data skilfully, it is valuable to know what are the main risks, dangers and threats revealed by giving permissions to mobile apps. Taking into account that, until now, few are the users who check these permissions when running new apps and with it, increase their vulnerability to possible prying eyes and actions illegitimate.
In this sense, we proceed to name, below, the greatest dangers evidenced by the granting of permissions to mobile applications of any operating system:
- Via permission based on camera accessusers could be victims of identity theft, loss of privacy, extortion (or extortion) and targeted advertising. Since, you will have the possibility to take photos and record videos secretly at any time.
- Notable risks are also evident from the permission of the calendar. Well, the app in play will know everything about your daily routine and will be able to share it with unreliable peopleespecially if you use your calendar actively. This facilitates attacks, theft of confidential data, different risks for physical security, etc.
- Once you allow access to your location through said permissionthe app that requests it will know where you are at any time and thus, you will lose your privacy completely. Furthermore, it is risky in terms of physical security and in terms of various social engineering attacks.
- Whether a given mobile app can freely enter the storage of your terminal or your external memory, will have the power to read, modify or delete any saved file. Which reveals a great danger to your integrity, because it simplifies identity theft, personal data theft and extortion.
- In case a malicious app requests the permission to the phone and it is granted by yourselfautomatically, this will achieve collect any action related to voice communications. With this, you can carry out social engineering attacks, steal sensitive information, send malware, secretly subscribe to services, etc.
- With the permission of the Contactsthere are also risks regarding phishing, attacks and spamming. In particular, this last danger, because it corresponds to a very attractive authorization for the famous spammers, since they will be able to have access to the list of all the accounts you use and your address book.
- Additionally, based in other permissions what the apps ask for, There are also threats such as: Installation of unknown applications, device administrators who have their full control, access to notifications, etc.
Learn step by step how to set app permissions
In view of the latent dangers exhibited by the authorization of mobile app permissions, it is important that users are aware of it and weigh every consent you provide to installed apps very carefullyin order to avoid vulnerabilities in terms of security.
Therefore, it is determining to know how to configure these permissions, in an optimal way and here, we show you several points of interest for that:
Choose which permissions to grant and which not
On operating systems like Android, for example, they give you the ability to manage app permissions custom mode. Thanks to this, when you install any app on your terminal, you can select those permissions that you want to provide and those that you don’t. Considering that, it will not be necessary to grant them all for the tool to work properly.
Therefore, while you are making this choice, you must check what permissions it asks for. Thus, depending on its nature, you will be able to intuit if the utility is requesting what is necessary or in reality it goes beyond what it really requires. Taking into account that, it would be suspicious that a photo editing tool or a simple game wants to access your current location. This being a regular permission for browser and map apps that need GPS.
Change any of the app permissions
It is also considered essential to check the list of permissions, in order to be able to modify any of the ones you have previously granted, If necessary. For this, from your phone, enter the Terminal Settings menu and enter the Applications section.
Next, it begins to verify in each one of the apps, which permissions they have enabled and thus, analyzes if it is necessary to provide it or not. Which, you can do it using the option “permissions” (this will depend on your OS and its version). In this case, if you notice that you have an authorization that is risky and suspicious, just remove it or change it.
Study the permissions requested by apps already installed
Malware-based apps also operate under a trick of installing a harmless app with light permissions, to then update it requesting new permissions, once it is installed. In this way, they manage to access the user’s location, the camera, his contact list, etc.
Therefore, another setting that is interesting to take into account is to use those applications that you have installed to check if it requires successive updates around its permissions. Taking into account that, if so, it is best to uninstall the tool as soon as possible. Since, in terms of security, permissions do not need to be re-accepted when such updates take place.
Privacy