
Index:
UPDATED ✅ Need to know more about what a backdoor virus is and how to eradicate it? ⭐ ENTER HERE ⭐ and discover everything about it ✅ EASY and FAST ✅
Backdoors is an English term that refers to the different attacks of cybercriminals to different computersthis is also known as back door in spanish. All of this refers to a security hole which enables the entry of viruses into the computer system without them being detected.
These types of viruses are usually entirely malicious and which enter computers with the aim of steal any type of private information stored there and even cause serious equipment damage. One of the great specialties of the backdoors is that they can enter a server, local or corporate network, web page without being detected.
These types of cyber criminal attacks has the advantage that they can do pretty much anything they want once they’ve logged into the computer of a user. That is why here we are going to explain what are these types of attacks and how can you eliminate them.
What is a Backdoors or backdoor and what is it for in computing?
a backdoor it’s a malicious program which is responsible for infiltrate computers secretlythat is, the user will not know that he has this type of virus on your computer. It is used to provide the attacker with a remote control of the machine where he has infiltrated achieving attack all vulnerabilities present in the system.
That is how The back door It usually works through a background what makes it possible hide from the user and not be easily detected. All this has led it to be considered one of the most dangerous malware of all, as it allows the person behind it to execute any kind of action on the infected machine.
These types of programs are used to spy on users, be able to manage their files, steal information, private files, financial data, install malicious programs on the machine, attack other people and even be able to manage the entire PC system completely. This is how the back door has the ability to destroy any type of machine with great ease.
These malicious programs are usually installed on the computer in different ways to start doing damage, although many of them No require an installation. These might be trojans, spyware, malwares, viruses, keyloggers, among others but they have much more advanced and dangerous functions, so they are considered as very powerful malware.
What are the main characteristics of a backdoor virus?
As mentioned before, all of this is a malicious program or malware which is entered by a hacker illegally on computers with the aim that they can act freely on it without any restrictions. All of this is done for the purpose of infect the computer for later subtract all the necessary information and data from itcan even reach completely destroy the machine.
According to all this, here we are going to teach you what are the main characteristics that backdoor viruses have inside a computer:
- They are intended to achieve create an entire network of infected computers in the best zombie style, which is also known as botnets.
- It has the ability to hack into a computer and allow the cybercriminals carry out their criminal acts via malware without the computer being aware of itthat is, the person will never know that they are stealing your private information and causing damage to your computer.
- These types of hackers they can reach involve the affected person in scams and other cybercrimessince by having full access to your system they can perform various operations through the data of the affected person.
- Once they enter the machine are capable of carrying out all kinds of activity without the person notice something strange on the computer. usually these cybercriminals are in charge of looking for the private, personal, financial data of the owner of the PC. This will allow them to be able to hack your different accounts, social networks, access to web pages, among others.
- Are able to destroy the hard drive memory of the infected PCwhich could cause its damage.
Backdoor Risks What can happen to my computer if it gets infected by one?
As we have mentioned before, these types of viruses are usually considered one of the most powerfulsince by going unnoticed it prevents the user from taking any measure against it, either to eliminate it or control it. This allows you to carry out different malicious acts on the PC without being detected.
In the event that your machine is affected by this malicious software, could be affected in the following ways:
- When this type of program insert into your pche is in charge of take remote control of the computerwhich will allow the cybercriminals to be able to do whatever they want on itEither from send, receive, share, delete, create files of all kinds.
- It not only aims infect your computerbut these trojans they have as mission create a network of infected computers so that they will use your machine to try to infect other computers.
- They can install malicious software on your PC without your authorization.
- Are able to steal your account data, such as usernames, passwords, among others.
- they can you steal personal photos and videos stored there.
- You can use your computer to carry out illicit acts such as fraud, internet theft, among others. Even all this can be carried out using your personal data.
- Are able to destroy the hard drive of the machine.
- They can carry out the destruction of your PC once they have obtained all the required information.
- They can control all hardware, get to modify PC settings, restart or shutdown anytime, create new passwords, user accountsamong other.
How did Backdoors get into my computer? Main causes
surely you are wondering how your computer can be infected with a backdoor or trojan, In these cases, the presence of these malicious software It can be due to many reasons, either because the user has installed it through some program, website or it has simply been installed when Did you receive any file by email or any other web route?.
The truth of all this is that everyones PCs are completely vulnerable to these types of attacks, especially The back door that are almost impossible to detect due to all their abilities to stay hidden from the system.
This is how we teach you below The main reasons why your machine may be infected:
through emails
this is maybe the most common and effective way to transmit a backdoor to a computer. These are usually added to a file that is attached to the messagein this case the person you make the mistake of opening such a file so that you end up automatically installing malware on your computer, thus allowing the intruder to start manage your team to your liking.
The best thing to do in these cases is ignore all those emails from unknown sources or unreliable websitesas the e-mails have become the main means of virus spread all types.
Using a LAN or storage device
other forms most common way to spread these viruses are through the same local Internet network or through an external storage device as a flash drive or external hard drive. Therefore, it is important to be very careful when use any external devicesince if this is used in many computers increases the risk of being able to infect yours.
web browsers
Many times web browsers also become an important factor for the spread of malicious softwarehence the importance of using browsers that are highly reliable and secure. In this case, it is best to use a browser like Google Chrome, Opera or Mozilla Firefoxalthough it is also important to mention that safety in this kind of case It will depend mainly on the websites that are visited.
Installation of fake programs
One of the things most dangerous currently on the Internet is to install free softwaremany of them usually be completely false so what you’re really going to end up installing is a malware on your PCin this case it can be simply a virus, spyware, malware or Trojan horse. Some being easier to detect than others.
According to this, it should be noted that websites are used to download programs from the web. Even though these free software are a excellent alternative to install all kinds of programson many occasions it is preferable to pay for them, but take care of the security of the orderr at all times.
Through Internet services (HTTP, Chat, Instant Messaging, ICQ, FTP)
It is possible that while you are visiting a web page if you are simultaneously installing some kind of malicious software without you realizing it, this is because many online platforms count on Trojan that are installed automatically when you enter the site. This is the same thing that happens with FTP servers.
Regarding the use of instant messaging Something very similar happens, since by means of chats can be sent any type of viruseither through a image, document, videoamong others.
Steps to remove Backdoors from my computer and be protected
If you suspect that your computer is infected with a Backdoors and you want delete itso here we are going to explain how can you do it. For this case we are going to recommend the tool malwarebytes which you can download completely free to your computer. It stands out for being a very simple tool to use that will allow you to keep protected from viruses, trojans, spywares, malware, rootkitsamong others.
Bearing this in mind, here we are going to show you how you can use this tool step by step, To do this, follow these instructions:
- the first thing will be download free software from Malwarebytes (you have the link below).
- Once downloaded, the following will be to execute it, for this a window of “Welcome” where you should press the option “Following”.
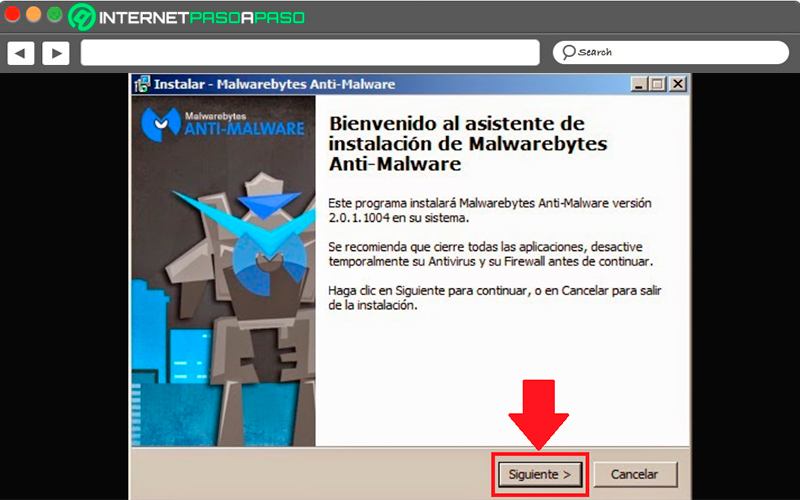
- To install the program it is important to follow each of the steps that are shown on the screen without changing any parameters of those already established. One time finish this installation it is important to verify that the option “Enable Malwarebytes Free Trial” is marked as “Run Malwarebytes Antimalware.” Once all this has been checked, the next thing to do is click on “To finalize”.
- When you have started the software a check will be carried out database and updates to detect if any update available.
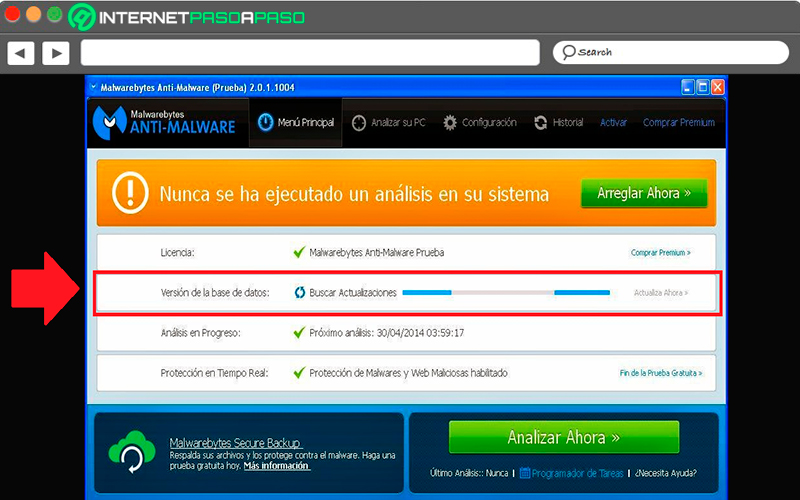
- When the previous step is finished, a system analysis to try to find possible existing threatsfor this you must click on “Fix Now” either “Scan now” for the analysis to start.
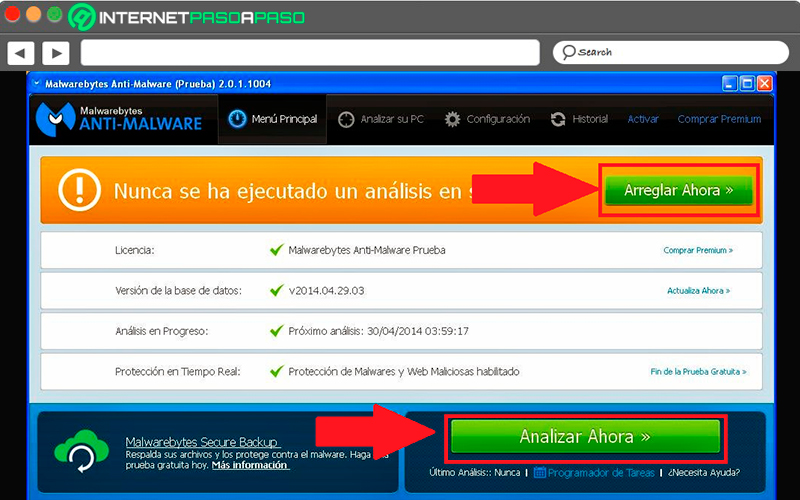
- Another way to start this system analysis is by selecting the option “Scan your PC” which is located at the top of the window. When you enter this option you will find a window where it will show you the option to “Complete analisis” which you are going to select and finally click on “Analyze now”.
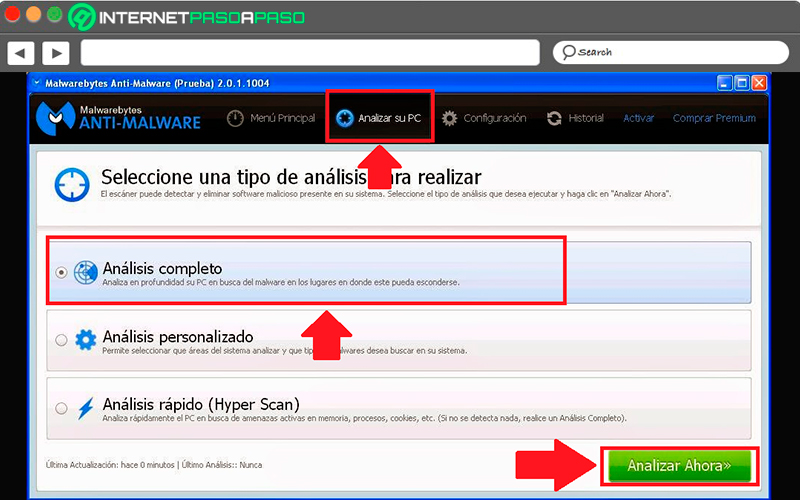
- Here you will have the opportunity to update databasefor this you must click on “Update now” in case it is out of date, if it is already updated you just have to skip this step.
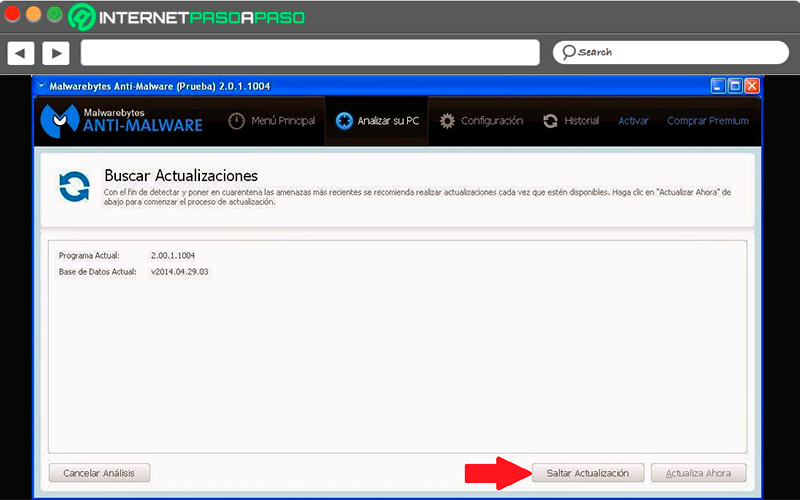
- It will automatically start the “Scanning” of the team, here you must wait a few minutes that this is completed, during its process they will leave detecting some of the threats present there.
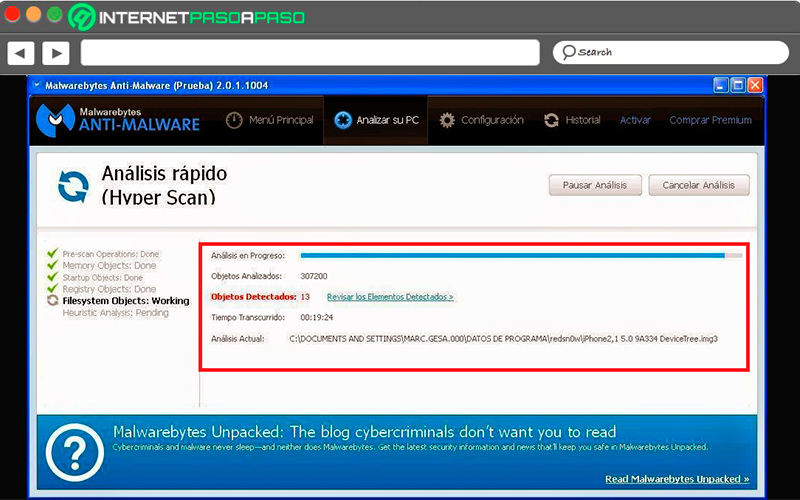
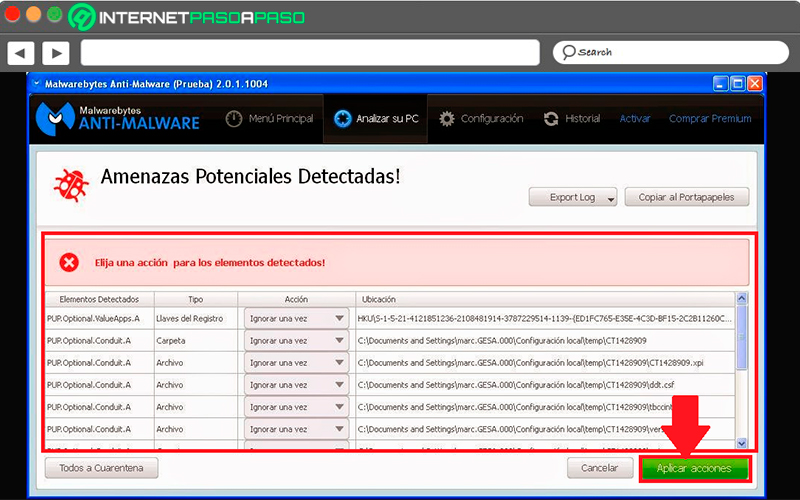
- When this procedure is finished, you will be shown the threats that were detected. In order to permanently eliminate them, it is important that you select the option to “Everyone in quarantine” and then in “Apply action”. This will allow all those malicious software go to quarantine.
- Once they are in quarantine, you can access it and delete them all.
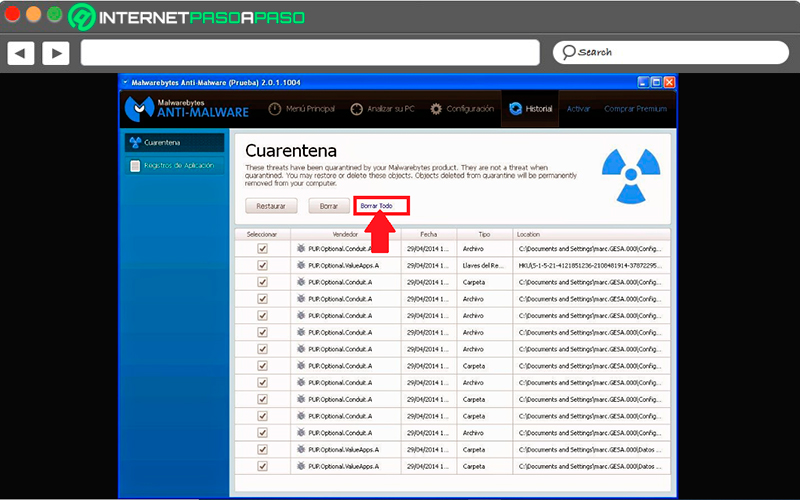
- When you’ve done this, Malwarebytes will ask you to restart your computer for all to be done changes made to the computer.
Download Malwarebytes Antivirus Windows
Download Malwarebytes Antivirus macOS
Examples of Backdoors What have been the most famous viruses of this family?
Currently there are many backdoor virus, which can be found of all kinds. Nevertheless, there are three of them that have been the most famous of this familythat is, they are the most common to appear in computers and computer networks.
Therefore, here we are going to introduce you the three most famous and dangerous backdoors you can find today:
tixanbot
Currently considered one of the more dangerous today, the same gives the attacker full access to the computer that has been infectedso that the cyber criminal You can access all the resources of the team without any authorization. This will allow the intruder to handle all PC files, download and install apps freely without any restriction.
That is how titan box he is able to destroy all services related to system security, where is he in charge of block all spyware, malware removers and else existing viruses in order to prevent Some of them have limitations.
Another of his great specialties is that he is in charge of block access to those websites that have excellent security, in order not to be detected. This type of backdoor can be sent via email, link, or simply downloading them through a fake file.
FinSpy
FinSpy has become another Today’s Deadliest Backdoor Viruses, it’s like this malicious software is capable of allowing its owner to download and install programs from the Internet on the infected machine. In order to attack with greater freedom the team of the person is responsible for lowering the security in the default configuration of the Windows firewallthis will allow you to act more freely.
Furthermore, it is one of the hardest to spotsince constantly change their names so it is easier to hide. FinSpy runs every time Windows starts, where its owner can take advantage to commit criminal acts you want.
Briba
Finally, we find Briba, another of the most powerful Backdoor of today and which allows a complete management of the hacker who created it, so you will have the opportunity to manage the entire system of the infected computer to your taste. In this way it can be used for download files, upload files and run other malicious software.
Briba runs from a FTP server that is hidden in the system, it is takes advantage of system instability to infiltrate the machine. His specialty is violating user privacy as well as causing poor PC performance.
Tips to be protected from backdoor viruses on my computer
Considering all the damage they can do cause these malware, it is extremely important to have basic knowledge to be able to avoid them and so on protect the computer and all private data stored on the computer.
That is why here we are going to teach you some of the tips so that you can be protected at all times from backdoor viruses, To do this, follow each of the tips that we will indicate below:
Use an antivirus
The first point to keep in mind is to use an antivirus that is really reliable and safe. Currently there are millions of such programsbut not all of them offer you the appropriate and necessary tools to attack these types of malicious software that they can reach damage your pc and even steal your private information.
According to this, the first step you should take to avoid the presence of backdoors on your computer is install a reliable and reputable antivirus, this will help you do analysis at all times and thus ensure that there is no virus present on your computer.
Install a strong firewall
As we have mentioned before, these types of viruses are responsible for exploiting weak firewalls, what forces you to install one that is really strong and ensure you one protection at all timessince from this you can ensure the security of your PC.
In the case of having a weak firewall, your system will be much more vulnerable, so it will be much easier for hackers can get into it. There are currently millions of firewall available in online marketso you can search for whatever really strong and secure and install it for So increase protection at all times.
Keep software up to date
One of the most guaranteed to keep computers safe is keeping all updated software and hardwaresince these will have most up-to-date security measures that will guarantee you a greater security in the system and less vulnerability.
Use password and rare users
One of the most common mistakes of all users today is choose username and password that are directly related to their name and other personal data. This usually becomes a very common and repetitive error and which is used by most of hackers. In this case, it is best to use both users and weird passwords and that they are from high security, since it will help to stop the different cyber attacks.
Other details to take into account
It is also important that, despite having the points already mentioned above into account, also consider these other aspects that will help you increase the security of your computer and thus avoid so much the performance of your PC as all your data stored on it is compromised:
- Make sure to set Internet zones and URL filtering.
- hold activated the firewall in order to get a greater filtering and protection in communications.
- Use a control policy and management of shared folders very strict, as this can become an easy means for such propagation.
- Avoid installing programs that are of strange origin. Please note that most of files downloaded from the internet They usually have viruses and other malicious elements contained in them.
- Make use of accounts users with limited privileges.
List of the best programs that you must have on your computer to remove backdoor viruses
Nowadays you can find a lot of available software that will help you protect your computer against these types of viruseseither by preventing these from reaching infect your computer Or simply removing them when detected. Many programs can be found on the market today, some of them free and other paid but despite this not all of them are really reliable and safe.
This is how we are going to show a list with the best applications you must install on your computer So you can remove backdoor viruses, to do this follow this list:
Panda
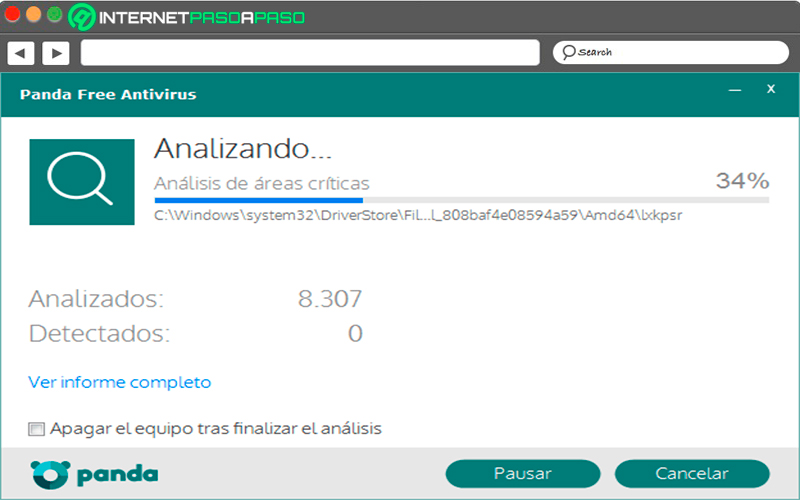
Panda is known to all for his excellent performance and analysis capabilities allowing them detect all kinds of virusesthis is how it also has the necessary tools to detection and removal of backdoors. Considering that these viruses have very high destructive capabilities that could cause the ultimate loss of a computer.
Bearing this in mind, Panda has specialized in offering very deep and advanced analysis capable of detecting them and thus be able to proceed to your elimination. Preventing the attacker from taking over the infected machine with the objective of stealing any type of data or information from itand even preventing them from being carried out scams with the personal data of the team owner.
Download Panda Antivirus Windows
ESET

ESET is currently another the most reliable large computer and smartphone protection companies on the market. they are in charge of offering all the necessary elements and tools to guarantee its users a complete protection 24 hours a day in all your information and private datapreventing them from be harmed by any type of virusincluding that of back door.
The Blackdoors are a type of virus that means quite a risk for userssince it has a huge potential to break any kind of security. It is because of that ESET has all this in mind and its researchers have been responsible for create all the necessary conditions In order to expose these malicious elements that are installed on the PC. All this has led him to become a excellent alternative to maintain equipment protected at all times.
Download ESET Antivirus Windows
Reimage

Reimage has become another of the most ideal tools to carry out any type of PC repairso it has become an ideal application for improve the functionalities of the equipment in various ways. This is how it handles protect your computer from cybercriminal attacks, removes all kinds of viruses, repairs the damage caused to Windows and helps improve the performance and stability of the PC.
In order to achieve all this, it has a very advanced technology where you have over 25,000,000 essential components which are used to help maintain the security of the Windows operating system at all times. In addition, it has a Avira AntiVir engine which makes it be able to remove any type of threat, including trojans, spyware, malware, adware, wormsamong others.
Download Reimage Repair Windows
spyhunter
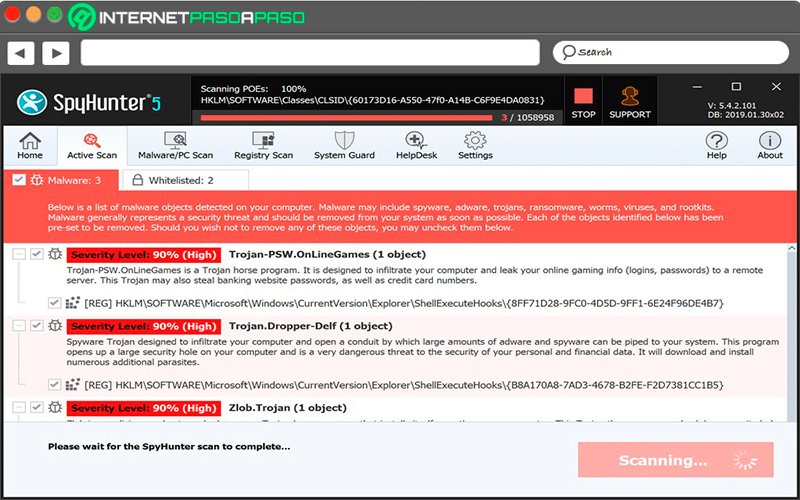
spyhunter is another of himThe most reliable protection software to deal with backdoorsconsidering that not all protection programs are able to counteract these types of silent and lethal attacks. This is how it is considered today as one of the most effective antimalware on the market, where you use a unique technology for detection of all kinds of viruses.
In this way, SpyHunter has become an excellent option to stop Trojan attacks, adware, ransomware, spyware and any other attack run by hackers what do they want violate the privacy of your computer. In this way, with this program you can ensure maximum security at all times, thanks to the fact that it has one of the more advanced analysis from the actuality.
Download SpyHunter Windows
Total VA
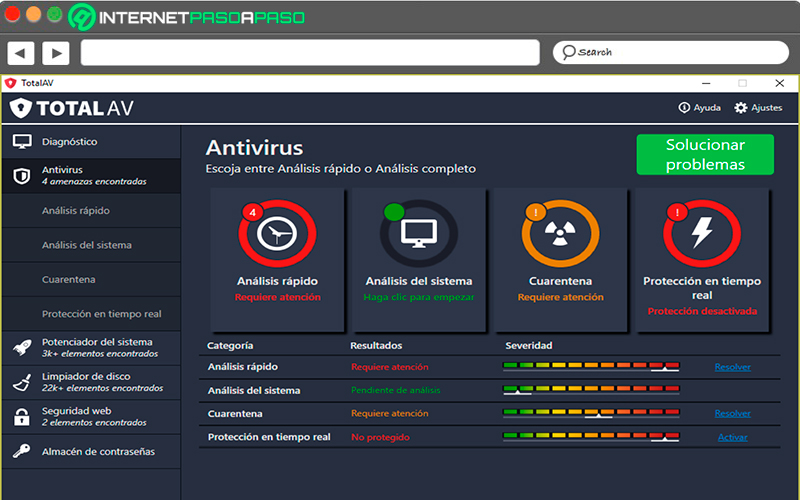
Finally, we present Total VAone of the latest antivirus on the market and which has managed to position itself among the first positions, managing to be located above others Programs of longer protection in the market. it’s like that even though Total VA It has only been working for a short time and has managed to become one of the best tools for what it is. virus detection and other software malicious programs that affect computers.
In this way, Total VA you can download completely free to your computer, it will offer you a large number of special functions that will help you to your PC functions at a higher speed and free from any kind of danger. It also offers a easy and quick installation, it has a very well designed interface so its use will be very simple and, finally, it offers a powerful protection accompanied by a very light solution.
Download Total AV Windows
Computing