
Index:
UPDATED ✅ A computer security vulnerability or hole is a security weakness of a computer that allows data theft ⭐ ENTER HERE ⭐ and Learn more
As there is a large consumption of technology in all the areas in which we move, the risk of computer vulnerability is constantly growing. This is nothing more than the probability that a hacker has of attacking information systems and at the same time our personal data.
It is because of that, it is necessary to be aware of all the risks to which we are exposed and that many times we are completely unaware of. In this article we will talk about what computer vulnerability is and we will analyze the different types that exist. We will also mention the consequences that these virtual attacks bring.
Don’t miss any detailsince you will be able to know how a hacker works and what is the best option to solve it.
What is a computer vulnerability?
It’s called computer vulnerability to the result of programming errors that exist in an information system. In this way, the availability of access, the confidentiality of the data and the programs that the user has installed on a given device are put at risk.
Due to this situation, a cyber attacker can take advantage of this “computer hole”, caused by a technological limitation, to remotely enter the user’s equipment and cause intentional damage. These can range from the copy of the buffer to the loss of the connection of different resources, both from hardware as economic.
What are the types of vulnerabilities that exist in computing and what causes them?
Due to the constant development of software, Computer weaknesses come in different types, which we will explain below:
low gravity
It is the vulnerability that least affects the information system of our computer or mobile. The way to solve it is very simple and we will have no problem reducing the risk, is the situation that a hacker can least take advantage of. These risks are usually caused by adware or spyware that collects information for advertisements or simple things.
Medium risk
It is also generated by files that are stored in cache memory and that produce a risk that is slightly more important than the previous one. Since these manage to reduce some of the configurations presented by the user’s equipment. The solution will be given with an audit, since with it the danger can be eliminated without major complications.
Critical vulnerability
At this point we are talking about a risk aimed especially at the integrity of the user’s information and data, since it produces the loss of confidentiality. To eliminate the risk, the work should be much more precise and in some cases all computer systems will have to be reinstalled.
Critical vulnerability rating
If we have this classification is because our equipment and personal data is being handled by intruders without being able to control them. It usually spreads like a worm and attacks the entire computer environment as it is carried out automatically.
It can bring very negative consequences to the entire network. In these cases, it is necessary to format the computers, reinstall the operating systems and perform a deep audit again to verify that the risks of attacks have been eliminated.
Risks of vulnerabilities How dangerous are they for users?
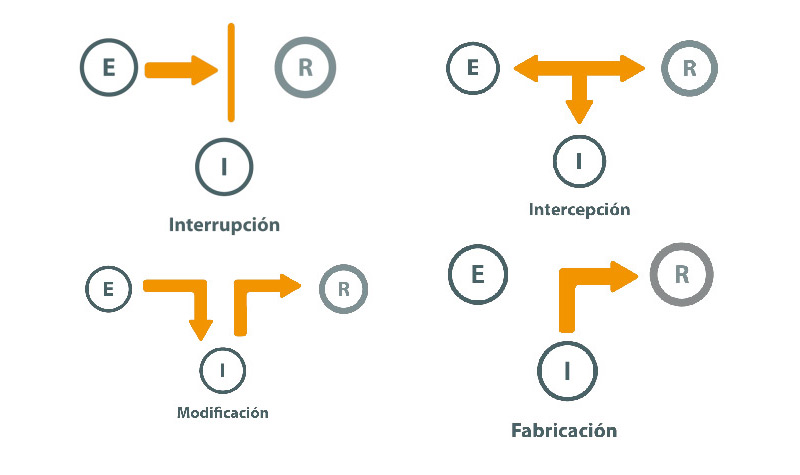
As we have seen so far, computer vulnerability is caused by the holes that exist in the development of software. This is used by attackers who manage to enter systems to perform different actions, which will vary with respect to the danger they generate on the user’s computer.
In this way we can say that there are different types of attackswhich will be classified according to the role that the hacker has and how is the quality with which the information arrives (or not) to the receiver.
A risk of interruption It occurs when the data delivered by the sender to the receiver is interrupted by the intruder, but he does not modify them and they do not reach their destination. An example of this could be when applications are deleted from our computer or mobile without proper authorization.
A little more complex is when the interception of the information issued. That is to say, in the path of the data packets towards the receiver is the intruder who becomes aware of all the information sent. He does not modify it, so no one notices such a situation. It is one of the most difficult risks to detect.
When the hacker decides modify information sent to the receiver, it may cause the software to be altered or data deleted to work in a different way. Although it is true that the detection in this case is much simpler than others, it is also necessary to mention that it is more complex to be able to detect the place where the data flow is intercepted and modified.
Finally, there remains the most dangerous of risks. Occurs when the attacker impersonates or fabricates elements in an information system, such as an IP, email address or anything else that resembles official sites. In these cases, the user confidently receives completely false information.
Tips to prevent vulnerabilities in your computer system from being exploited and protect your data
As you may have already realized, it is inevitable that these computer vulnerabilities exist, because it exceeds the user’s control. This happens because these are generated in the development with errors of the software used in the devices.
So what we can do is reduce that “gateway” of hackers with actions that are within our reach. Due to this, we will show you how you will be able to prevent intruders from attacking your computer system. Let’s get started!
virus update
Many people think that just by downloading one of these programs they already have their computers controlled and away from any risk of cyber attack. Unfortunately, this is not the case, since viruses or malware are programs that are stored, especially in the temporary files folder, and new developments appear every month. Therefore, the companies that own these antiviruses are optimizing new protocols for detecting the most modern malicious files.
For all this, it is necessary to always have the latest update of an antivirus and “make it run” at least once a week or when we have entered pages or websites that may seem dangerous.
Updated operating system
As with antivirus, the operating system both Windows like the others, it has settings for defense against viruses and threats. In this way, it is necessary to activate the option “Real time protection” and also the “Cloud based protection”.
To do this we must go to the Windows menu and choose the second option called “Protection against viruses and threats”. It is important to keep this point in mind, since the operating system is one of the programs that presents the most computer vulnerabilities, so it is always necessary to obtain the “hotfixes” or patches designed by the engineers on our teams.
Email setup
This is another great gateway for hackers. Since one of the means by which intruders access our equipment is through deception or sending false emails, where they persuade us to click on certain links to access promises or unreal prizes. In this matter, we must be very careful and not open ads from people we do not know or who directly offer us an unclear message.
If we want to have an updated email, it is convenient to have the “most popular platforms”since these offer the possibility of dividing the mails into spam and malicious emails, which are really the important ones. They can do this work thanks to the large database they have and the notices made by users.
Internet browsing

We must be cautious with those web pages in which we browse. This is because cyber attackers are constantly looking to break into our computers. through unpopular websites either “similar to other originals” (for example, a bank or a recognized store) that hide certain information or where it is not clear.
To detect malicious sites many times we must read the security protocol they have in the URL. It is preferable to access all those that have a security certificate and have https. While this is not an absolute guarantee, it will help improve our protection.
Unknown file download
When you download applications or programs for your computer or mobile device, try to do so from sites recognized by many users and avoid accessing app stores other than Google or Apple.
Although it is true that files with format can be downloaded with peace of mind torrentit is necessary to be very careful when we drive in uTorrent or similar sites.
Since at “go down blind” and accept the download of a file only by its name, we do not know the content until we have it on our computer. To perform this task, it will be necessary for those users who have an advanced level.
Computing