
Index:
UPDATED ✅ Do you need to KNOW what the Deep Internet is and how to enter it? ⭐ ENTER HERE ⭐ and discover what levels exist and the entrance doors ✅ EASY and FAST ✅
All Internet users in their idle aspect have heard, and increasingly, about the Deep Web and who more and who less, we get a slight idea of what it is or, at least, of what we find in it.
However, there are still many questions that most people have about it and it will be in this space that we will explicitly reveal what it is, what you will find in it, how it works and because this part of the internet is hidden.
Next you have the Greater user guide to access the deep web and answers to questions such as its estimated size and its compared to the dark web or “normal” internet, how to access it safely, what can we find there and some famous links in this dark area, do you still want to move on? so let’s go!.
What is the Deep Web or deep Internet? Definition

There are many ways in which the deep web is known. We talk about deep internet as the literal concept when translated from english, hidden internet or invisible internet. In any case, all these concepts come to mean the same thing.
It’s about a content that is found on the internet but has not been indexed by the usual search engines that we use, either the big google or many others like Yahoo!, Bing, Ask, Ecosia and many others. It’s a public or private online content that has not been tracked and cannot be found on a regular basis.
Thus, when we use any of them, this information will never appear in the search results, it is not accessible to the naked eye.
The reasons why any search engine does not crawl some pages are:
- hidden information: There is some information posted on an indexed site but it is not, so it is hidden.
- Contextual web: They are sites that will be modified depending on the context that occurs.
- Restricted access: Accessing the sites requires an action that solves the access protection.
- Dynamic content: Dynamic sites created as a response to certain parameters.
- Non-HTML content: Although it is common to use this language, we can also not do it, creating textual content in different extensions.
- Required software: There is some content that is intentionally hidden and requires specific programs (or other protocols).
- Unlinked pages: Any site of which a search engine is not aware of its existence in relation to the linked system. That is, that it has not carried out external or internal link building work.
How big is the Deep Web believed to be?
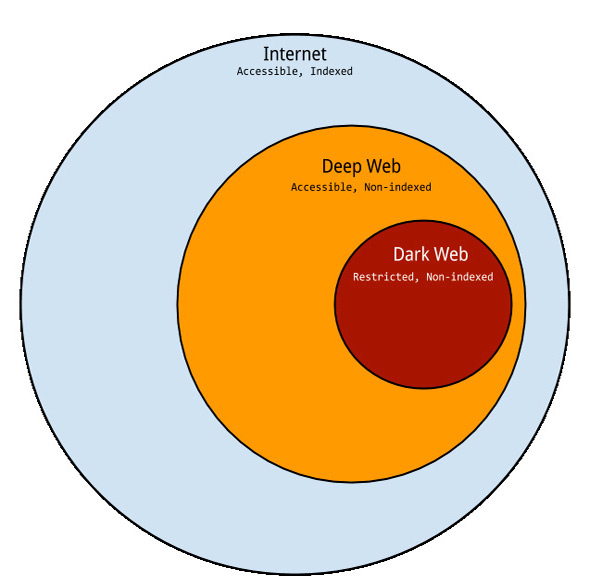
In the invisible internet we find all the content that, for any of these reasons, has not been indexed. Although the concept is used to refer to everything that is hidden with a malicious intention, the truth is that the hidden internet is really considered to be all the information that is not indexednot only intentionally because it is part of a crime but because we want to preserve the privacy of our creations or simply because we forget to do the indexing work.
It is about disseminated information, files or text pages is a specific place on the internet that is accessed in a special way. There is an estimate from the beginning of the decade that tells us of a size of over 200,000 sites and 91,000 terabytes of information.
Its most distinctive feature is the lack of registration by search engines, of course. However, there are also some others, being the most important, and in which criminals hide, anonymity. The activity in this hidden space is not associated with any person or machine. Established contacts are not monitored, we are not observed there and transfers are virtually untraceable.
On the other hand, we have the superficial internet, which is what we all habitually explore.; me to write this text and you to read it, to enter social networks, to find your dentist’s phone number, to buy jeans in a fashion company’s ecommerce, to write an email to your boss…
What is the origin and how was the deep web created?
Its origin is given, in fact, with the appearance of the Internet since it is precisely the first sites that used the network that were least interested in being indexed. In fact, the first web software was used without even talking about a registry, or engines, anything.
The Internet literally emerged from being invisible. It was later that, with the search engines, we began to talk about indexed and non-indexed content.
Are there levels of depth in the Deep Web? What are we going to find in them?
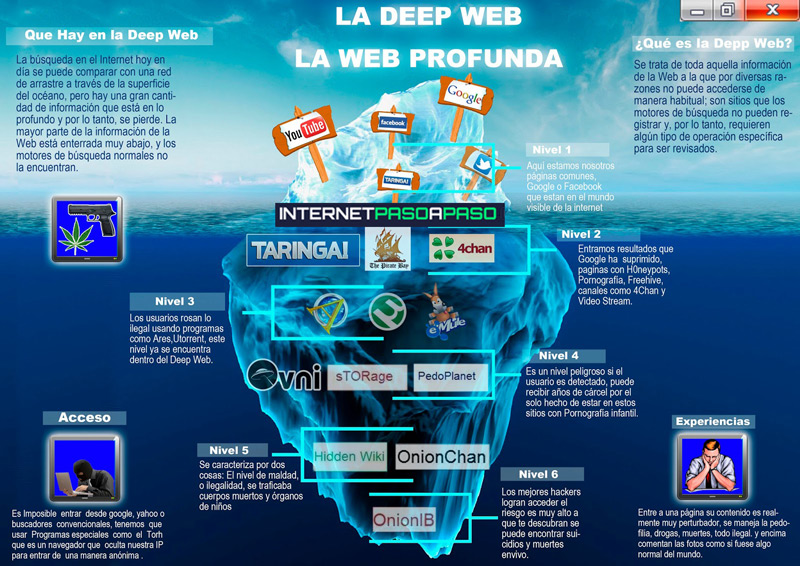
Indeed, the internet has several levels or strata. So much so that what remains in view of all is estimated to be only about 5% of the total content of information that exists on the internet.
- level 0: This would be the clearnet, the superficial web, the conventional one, to which we all access when we start our browser and type anything. All this content is indexed and initially legal (at least until it is discovered and studied).
- Level 1: This combines content that is indexed but more difficult to access and other content that is not indexed but of a legal nature and whose use occurs in the previous level, by common users. They can be databases in MySQL, certain communities and social networks, network services or web hosting.
- Level 2 or Bergie Web: Still easily accessible we have clandestine content that may or may not be indexed but that, as we say, due to its knowledge and use, is accessible. We could talk about the results that Google blocks, about the enormous 4chan communitytrap systems, Jailbait, FTP servers… Between this and the previous one we barely came across 5% of all the information posted.
- Level 3: This is the first level that requires a special access method such as an anonymous network or a proxy, which we would already consider the Deep Web as such. Here we would find pornographic videos, hacking information, celebrity scandals, gore videos, snuff, animal abuse, computer security, virus information…
- Level 4 or Charter Web: Its content is divided into two parts. One of them is easily accessible from Tor and includes material on a diverse subject, all of it quite questionable, of course. Banned videos, books and movies are at your disposal and the black market is taking place with drug trade, illegal games. sale of animals of exotic species, hiring hitmen, human trafficking… The second requires access with a closed shell system and in it is the content related to pseudoscience, conspiracies and ufology or UFO phenomenon. You will also be able to find information on artificial intelligence, experimental hardware, supercomputing, experimental plans of personalities from history… Until here we would find 20% of the total content of the network.
- Level 5 or Mariana network: In honor of the depth of the homonymous grave. It is not known for sure what this level contains, speculation being common to the point that reality has been mixed with what is imagined or invented. It is theorized, by default, with here it is classified information and other secret documentation of the different governments.
- Level 6: In theory, it is a mere intermediary element.
- Level 7, Virus Soup or The Fog: It’s a hotbed of malicious code designed to prevent anyone from going further while trying to detect the IP of the users. It requires quantum computing for access.
- Level 8 or The Primarch System: Of impossible direct access, this is a system that controls the entire internet and is out of reach of any organization. This is an anomaly that causes unalterable commands to be sent to the network, doing this randomly. It has been determined that there is a quantum function protection that no one has tampered with yet.
Although, as we have seen, the content of the different levels seems to be illegal both to consume and to even access it, the truth is that all kinds of information is also disseminated that is not illegal nor does it propose or suppose an illegality, but is simply hidden or not wanted to be easily accessible because it is not intended for consumption by the user.
The clearest example is that of the Academic Invisible Weba set of networks of scientific institutions where previous publications and all kinds of academic material can be found.
Other content would be that which we create uniquely and privatelythat we want or have to have posted but that we do not want to be accessible, for example, the development of inventions or elements of interest that do not yet have a patent.
Infographic: Tiers of the Deep Web
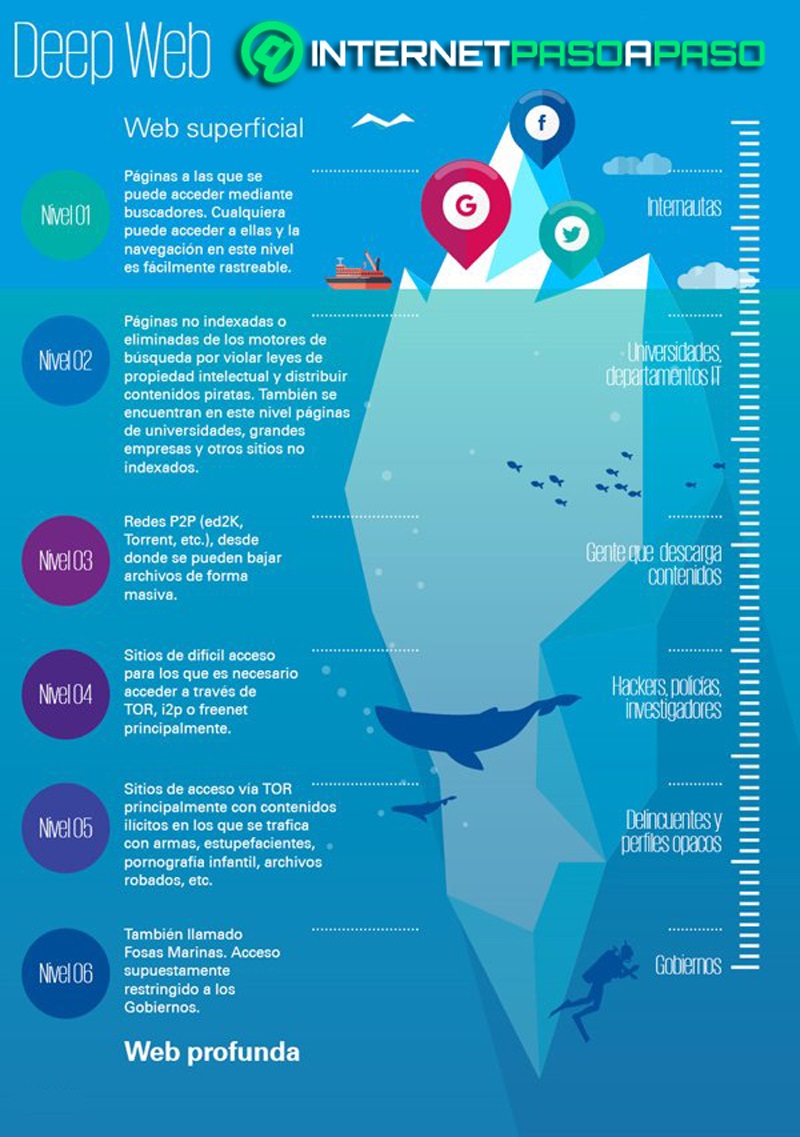
Search Engine Indexed Deep Web Content
In recent years, and coinciding with the knowledge that the user is having about this hidden content, they have begun to search more and more, out of mere curiosity. So much has been so it is already possible that certain search engines index part of this.
The way commercial search engines are getting it is through use a Site protocol that Google developed in 2005 and the OAI protocol, from the National Science Foundation. These work on web servers, allowing them to advertise, through the use of three algorithms, automatically detected URLs as they are, precisely, resources not linked to the surface web.
The content that is found, yes, corresponds to the first level considered invisible, that is, those less sensitive points within that enormous unknown sea.
How does the hidden internet work?
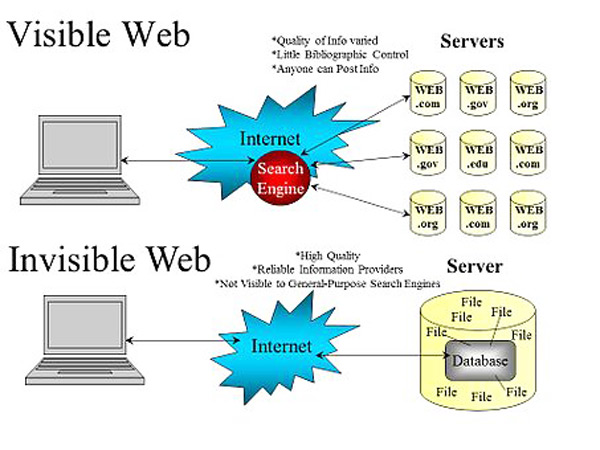
Access to this place requires prior knowledge of what you want to find and where to do it Well, unlike what happens with the superficial internet, in the deep web everything is much more complicated, there are no agility links for searches.
This is so because, as we have seen, sites are not indexed, according to a simple NO INDEX request by the webmaster, which ensures that the crawlers (web search spiders that work on the surface layer of the network) do not go through them.
domains
Onion is the domain extension that is used in these first levels of the Deep Web. You will see it ending all the URLs, as it would happen with the .com, the .es, the .org, etc.
East is precededinstead of a domain usually composed of the name of the site or one of its keywords, by an alphanumeric string including even decimals.
encyclopedias
What is used to start sailing in this sea is what is known as Hidden Wiki, a kind of Wikipedia that contains information about what we can find, working as an index of sites whose domain is .onion.
The encyclopedia is structured in categoriesmaking it easier for the user to find what they are looking for quickly and easily because, as we say, since it does not work with names but with numbers, it is impossible to carry out a search that returns results based on the words that we have entered.
It is essential to know that the url of this changes quite oftenso it is possible that when you go to use the most current one that you found a few days ago, it is no longer useful and you need to search for it again right at the moment of navigation.
It is also necessary to mention that although here you will find an extensive index, not everything you see is accessible to everyone. Many of these sites will not allow you access because they require a username and password (only possible after receiving an invitation) or simply because they require a more specific navigation method.
On the other hand, the existence of this place and these contents being more and more accepted, there are several websites with links to deep sites that you will find on the surface internet, so it will not be difficult for you to know which sites exist without need to enter. So we can have easy access to the Hidden Wiki URL and from other encyclopedias by doing a simple search.
Search engines
Although they are not usually used due to their primitive nature and the scarce and unwise results, yes there are some search engines on the deep web. Some of them are DuckDuck Go, Ahmia, Deep Search or The Abyss.
Their links are also easily found on the surface web, however, you will see that if you access them, you will not find much; a wiki is much faster and more complete.
cryptocurrencies
An important part of this world is based on the purchase of all kinds of things, from databases to weapons, through drugs or even organs. For this to be possible and there is no trace of the transactions, cryptocurrencies are used in the hidden network, which are digital currencies that are impossible to trace and that, even so, remain outside the jurisprudence we have, regardless of the country.
Invitations
The greater knowledge of these sites has forced their creators to protect them better, so that, at present, many of them require specific access that you will not have unless an invitation has been issued to you. This means that it is very possible that you will not find what you are looking for if you are just gossiping.
invalid links
Finding that a link does not work is very common. As is the case with the HiddenWikithe illegality of these spaces means that they constantly have to change domains and servers.
For this reason, although there are many spaces that give you information about links, it is best that you do the queries at the time of access, making sure that the links are not down.
How to enter the Deep Web safely? Is it illegal to do it?

It is important to know, first of all, that entering here is not illegal, it is not prohibited and, as we have already seen, you can find more than those related to illegal acts. what yes we warn is that the content that you can find will surely turn out unpleasant. In addition, it can also be dangerous.
Think that by accessing these places you have the risk that:
- Malicious hackers could target you, attacking you to steal your information.
- Your emotional stability could be violated due to the nature of many of the contents that, curiously, turn out to be the most accessible: videos of murders, real stories very explicit, in the first person, of crimes, animal abuse, explicit images of corpses…
- you could be scammed. No transaction you make here is regulated, among other things because surely what you have bought is not legal.
- Harassment and threats. Although at first your identity should be anonymous, the truth is that, in addition to other criminals, there are also cybercriminals specialized in hacking equipment, tracking movements and, with it, ending up finding you.
- Catchment. It is possible that, based on persuasion or simple deception, you are convinced to be part of communities with illegal interests or, at least, sinister ones, from which it is very difficult to leave.
- Finally, keep in mind that, although it is not a place with eyes, sometimes they can be therefor whatever reason, being able to accuse you of being an accomplice in any crime, whether for sharing illegal content, making a purchase, hiring a service…
Entering the deep web: step by step
Now that you are aware of what it is, what you are going to find and what can happen, all that remains is to show you how you can access those first levels of the deep web (remember that, after a certain point, to go deeper you have to go one by one).
Download TOR browser for Windows
Download TOR browser for Mac
Download TOR browser for Linux
- Download the TOR Project softwareThe Onion Router, a browser designed by the US Navy with the ability to encrypt communication while hiding your IP by constantly changing it through the use of proxies. It is credited with access to over 6,000 hidden sites.
- install it on your computer by launching its executable.
- set it up according to your intentions considering security and anonymity.
- When you want to start browsing the invisible internet open it as you normally would with any other. know that this it works through a P2P protocol that makes the trace end up being lost; that is, your computer will act as client and server at the same time, like the rest, becoming a network node. Your team’s information will have been encrypted in layers and this information will be sent to others.
- As we have seen, you will have to enter a specific link, the one from the Hidden Wiki, the one from another encyclopedia or, if you already know the one from somewhere, then that same one (without the need to resort to indexes). Remember that these must end in .onion.
- If you don’t know any space, enter the Hidden Wiki or in the directory you have chosen. You just have to copy the corresponding link and paste it in the bar of the tor browser. This way you will access URLs of all kinds of sites.
- Search for those addresses that are of interest to you and to enter you just have to paste them back into the TOR bar.
Tips to stay safe
Finally, we want to comment on some points that can be used to increase your security:
- When configuring the TOR browser, disable any plugin or script, as these store and give away personal information. Of course, perform the configuration only if you are sure of what you are doing; In general, this is already prepared to offer anonymity and security, because that is what this browser exists for.
- Have your Firewall and antivirus activated and updated.
- Also update the browser.
- Browse with the extension HTTPS activated.
- Although it is common to use Tor, there are other options more secure. If you work on Linux, it would be a better option to choose Linux Tails, a distribution of a bootable OS that leaves no trace.
- The safest operating systems are Linux and Mac OS.
- Do not access beyond the second level invisible. If you are here browsing, surely that will not happen, because if you have the necessary knowledge you would not need to read these words.
- Use a VPN connection located in another country, to be able to be in those in which the legislation is more favorable, by what can happen. In this way, our service provider will not be able to know that we have accessed the TOR network.
- don’t download anything. These places, as well as offering morbid content, also fill you with malware without you being able to complain or do anything. Furthermore, you could also be committing a crime by downloading certain types of content. Finally, there are files that have embedded network resources that allow us to reveal the real IP of our computer.
- Do not use TOR to download torrents. Curiously, in this case your IP ends up being known and you will be browsing very slowly for nothing while saturating the network.
- You can connect to Bridge Tor if you are looking for more privacyleaving aside the public TOR network, which is the one we access conventionally.
- Never access any personal profile of yours, neither by mail nor on social platforms nor in any place where personal information is available. You’ll have time to do it when you stop sailing these seas.
20 Best “Safe” .onion Pages and Entry Points to Access the Deep Web

All the links listed here redirect directly to the Deep Webso to be able to enter you will have to access directly from the aforementioned Tor browser, since if you enter from a “common” browser they will give an error. Enjoy the trip!
Internet