
Index:
UPDATED ✅ Do you want to configure any operating system to be more secure and private? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
At the moment there is no operating system that is not vulnerable to certain security issues. For this reason we will show you in this article how to configure your operating system to make it more secure and keep your data protected in a simple way.
we will teach you the vulnerabilities presented by Windows, MacOS, Android and iOSso you should be attentive to learn every detail according to the OS you have installed.
Also, you will know the step by step to configure each OS to make it more solid. Do not miss anything if you want keep your private information safe on any device.
What are the main vulnerabilities of modern operating systems?
The vulnerabilities of modern operating systems that you can find today are the ones detailed below:
Windows 10
on a computer with Windows 10 operating system you will find that the update code does not contemplate the protection of the files against a new malware. This is very common in almost all OS, but it is accentuated in the Microsoft. To solve this problem, it is necessary to periodically update the operating system.
You can do this by downloading so-called security patches, also known as Hotfixes. Cortana is another weak point that W10 has, since cyber attacks are known to have been carried out through this virtual assistant. The best way to avoid this is disable Cortana so that you do not have access to private information. Cross Site Scripting or also called script crossings are also points to consider in Windows security.
These programs are hosted on the computer through the browser and can work to spy on the information you carry on the Internet. Although browsers are not part of Windows, it can be taken as an operating system vulnerability that does not detect and eliminate cookies and the advertisement that can considerably impair security over the Internet.
macOS
macOS is a much less vulnerable OS than Windows, but this does not mean that it does not have weaknesses when it comes to cyber attacks. This is the case of the cookies, the scripts and the advertisements what the user has every time he surfs the Internet. For this reason, it is convenient to work with trusted browsers (especially Safari) and customize it to avoid this kind of checkout.
iOS

The vulnerabilities you will find in an iPhone are related to Internet browsingevery time you download applications you must do it in the app storewhich controls that all the apps that are uploaded to the platform are safe and comply with the terms of conditions and services of Manzana.
As with all operating systems, when you browse with your iOS mobile you will not be able to avoid being tracked. For this reason it is convenient to use vpn to encrypt the IP adress, become invisible and work with a different geolocation than the real one. In addition, cookies are installed on the phone, unless you customize it to the browser so that you are not monitored.
Android
While is true that Android offers users great security resources both to access the mobile and not to be located by means of the real location, it also has security vulnerabilities in its operating system. This is especially due to Internet browsing. As is the case with iOS, the OS cannot prevent the user from being tracked and that third parties do not know about the activity carried out on the web. This can be fixed by browser customization.
Learn step by step how to configure Windows to make it more secure
The step by step that you will have to do to configure Windows to make it more secure is the following:
Download all updates from Windows Update
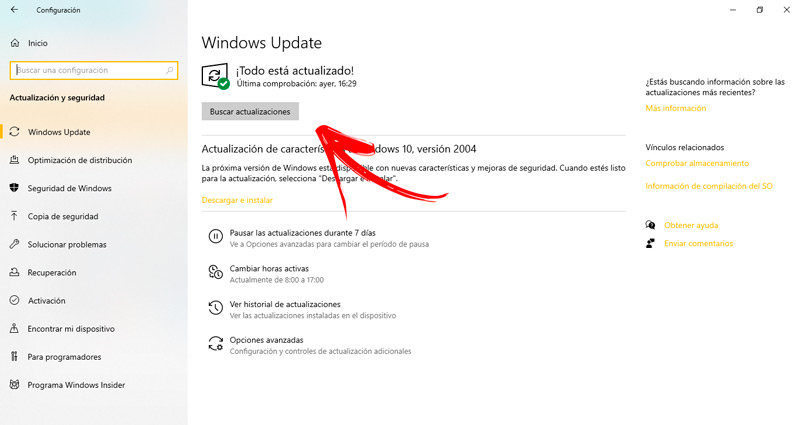
You must not forget that have the operating system updated reduces the risk that some malware join your team.
To know and update this part, you must do the following:
- enter a Setting from the button beginning.
- Choose the option Update and security.
- head over to the tool Windows Update.
- Check if there is any update that you have not installed yet by pressing the option Search for updates.
- In case there is any of these, click Download and install.
Disable Cortana
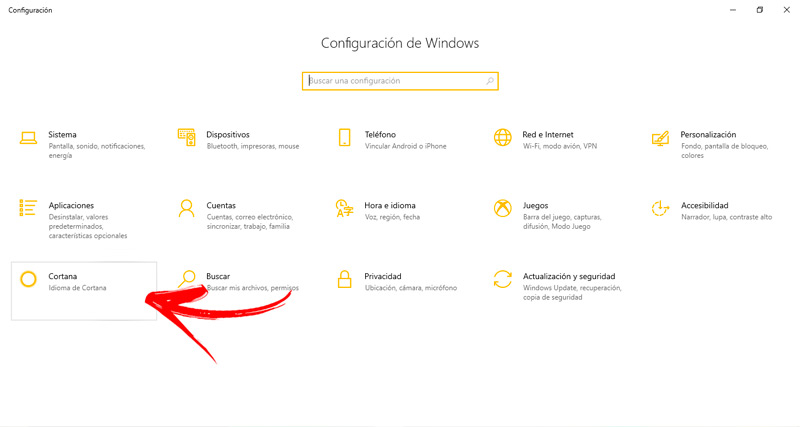
It has been found that the windows virtual assistant presents vulnerabilities that allow attackers to enter computers.
For this reason, it is convenient to disable this wizard by following this guide:
- head over to the button beginning and click on Setting.
- NextChoose Cortana.
- Press in Search and Cortana settings.
- Search the function Allow Cortana to respond when you say Hi Cortana Y turn it off.
- Also You will have to to disable field Let Cortana listen to my commands when I press Windows logo key + C.
- And finally, disable field Use Cortana even when the device is locked.
Configure diagnostic data
microsoft gathers information about the activity you do on your computer. This feature comes enabled by default, but you can disable it to strengthen your privacy.
You will have to do this step by step:
- enter a Setting and select Privacy.
- Next, choose Windows permissions.
- Press in Comments and diagnoses and check the box Required Diagnostic Data.
Customize activity history options
What you should do now is avoid sending your activity history to Microsoft.
To do this you will have to follow this guide:
- When you are in Windows settings go to the section Privacy.
- Choose the option activity history.
- deactivate the tool Send my activity history to Windows.
- It also removes activation Store my activity history in this device.
- And finally deactivate Show the activities of these accounts (of e-mail).
Remove permission for apps to access your location
You must go to Settings and follow this step by step:
- Choose the option Privacy and then choose Location.
- Then turn off the tool Allow apps to access your location.
- Also click on the tool for clear location history that you have saved on the device and if you prefer, choose what type of app they can know where you are.
Customize the microphone and camera
You should not forget that any unreliable user with a bit of computer knowledge can access the microphone and camera of your computer with operating system Windows.
To avoid this inconvenience, continue with these steps:
- Press in Start and select the option Setting.
- Choose the tool Privacy and look for the option Microphone Y disable field Allow apps to access the microphone.
- You will have to do the same with the camera accessing the function that bears this name and then disabling the tool Allow access to the camera on this device.
Configure your browser
You must not forget that there are browsers that are not secure, so they can be vulnerable to the intersection of the information between your computer and the hosting of the website you want to visit.
For this reason, we recommend that you use browsers recognized for their security, as is the case with Chrome, Mozilla Firefox, Tor and Opera. In this case we will show you how you can set up Chrome to strengthen your security. The first thing you should do is clear history what you have so far.
The steps are:
- Open the browser and go to the menu to select Record.
- Search the option Delete navigation data.
- click in Basic.
- Choose field Time interval and choose All.
what you should do now set up what for your activity is not saved at any time.
To do this you must follow this guide:
- head over to option Data and personalizationlocated in the menu.
- Press in activity controls.
- Choose the tool manage activity and choose Plus.
- Find Save activity for and click on it.
- choose the option Never and finally click on Following Y To finalize.
Next, you must block third-party cookies so that these programs do not affect your privacy.
You can do this by following this process:
- Search in Chrome the option Plus and click on it.
- Select Settings.
- Choose Advanced Settings.
- click in Privacy & Security and then in Content Settings.
- You will find a list where you will have to select the tool cookies.
- Choose to disable cookies.
- disable the box Allow sites to save and read cookie data.
Discover how to configure your MacOS to make it much more secure
As is the case with Windows you can also set up your mac to make it more secure.
You will have to do this step by step that we show you below:
Configure cookies
The first thing you will have to do is configure the cookies that are installed on your Mac so that they do not deliver information without your authorization to third parties.
What you should do is open the Safari browser and follow this guide:
- head over to option Menu and then select preferences.
- Next, look for the tool Security and click on it.
- Choose Show cookies.
- Press in delete all.
- To end the process, click To accept.
Block banner ads
Open Safari and follow this step-by-step to block pop-ups:
- Press in the menu of Safari.
- Select Preferences.
- click in function Security.
- Choose Block pop-ups and click on it.
Steps to configure your Android mobile and protect your personal data to the maximum
To configure your Android mobile and make it really secure you will have to follow these steps:
Set the blocking method
What you will need to do to hardening your android operating system is to modify the settings to access your phone when it is locked. You will need to use the method fingerprintas this mode is the safest.
You will need to perform these steps:
- head over to Android settings.
- Choose the option security and location.
- click in device security and look for the tool Fingerprint.
- If you have an engraved fingerprint To authorize purchases and access applications, it is ideal that you delete it by clicking on the trash can and then record it again by clicking on Add a fingerprint.
Perform credential encryption
This action will privacy increase for those card lock management apps they need a key or credential to access it. If you use this configuration mode, what you will do is encrypt the access method so that it is not decryptable with any attack method.
The steps you must follow to carry out the encryption of credentials are:
- Press in the tool security and locationwhich you will find in the menu of setting.
- Next, Choose Privacy and then choose Advanced.
- Search the tool Credential encryption and select the mode until it is on encrypted.
Improve Google activity control
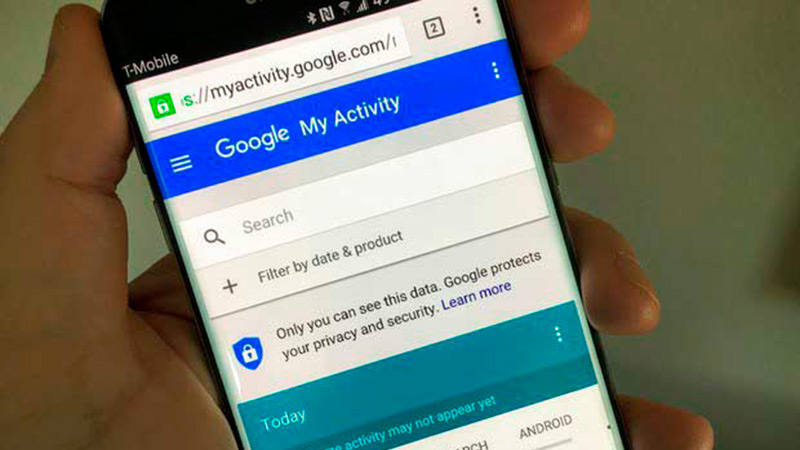
Few people know that in the tool Google My Activity all activities performed on the mobile device. In this function you can see a list chronological order in which you can see what type of applications were used, when the browser was accessed and what type of third-party apps were used. For this reason it is convenient to configure My Activity to improve privacy.
The steps you will do are:
- enter with your browser here
- click on Activity controls on your account Y deactivate this option for your device Android.
Set up a VPN server
When you use this class of computer tools, what you are doing is losing the geolocation of your device and remaining hidden when you browse the Internet. This will greatly improve the encryption of the IP address therefore, you will need to download a trusted application to carry out this task. As we told you in the previous paragraphs, it is convenient to choose a paid VPN or, at least, not to leave records of the activities you carry out on the web.
Customize your trusted browser
It is convenient for you to use Google Chrome as your trusted browser, if you prefer you can also use Firefox, Tor, Opera or Brave. But this is not all you have to do, since you will have to configure it to delete the histories and disable the cookies. In the case of Chrome, we already explained it to you with the Windows operating systemnow we will take as an example the browser Firefox.
The process you will have to do is:
- Select Menu.
- head over a Privacy & Security and select the option Record.
- Next, you will have to click on Use custom settings for history.
- Active the box Clear history when Firefox closes.
- Then you’ll have to take a step back and select again clear history when firefox it closes.
- Choose Preferences for history cleaning and set the parameter you need.
- click in To accept to finish the task.
Learn the steps to configure iOS and make your iPhone more secure
If what you are looking for is to strengthen the security of your iPhone or iPad, look at the steps that we show you below to be successful with your task:
Configure Safari
While it is true that you can use any trusted browser on your iPhone, we will show you below how you should customize Safari so that you strengthen your security when you browse. The first thing you should do is block cookies.
You can do this step in this way:
- Go to the menu of browser.
- Choose the option preferences.
- click in Security.
- Search the tool show cookies and click on it.
- Choose the option delete all.
- To end click To accept.
Now, you will have to clear the browsing history. You can do this by following this guide:
- on your mobile, go to the menu iPhone.
- click in Safari.
- Choose Delete history and browsing data.
- Press in delete history.
Restrict ad tracking

When you want to block ads on your iOS mobile you will have to do it with these steps:
- Access a Settings from your iPhone.
- Choose the option Privacy.
- Active the tool Limit tracking.
In this way you will have restricted the tracking of advertisements when you browseif you want to do it also with the Apple TV device you will have to choose the option Apple TV settingsclick on GeneralThen in Privacy and finally activate Limit tracking.
Incorporate a trusted firewall
The firewalls what it will do is strengthen security. you can use any app that is available on the App Store and in this way you will block the outgoing connections that have a protocol of type UDP or TCP.
Computing