
Index:
UPDATED ✅ Do you want to make your Android more private by encrypting all information on it? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
Globally, there are over 2.5 billion active Android devices. Reason why, this operating system is estimated as one of the most famous in the world and, mainly, is characterized by its fundamentals in Linux which is free and free OS kernel. Also, Android is distinguished by provide a high level of customization and different tools to provide the best user experience.
However, like all mobile devices, those that operate under Android also they present some security gaps that can endanger the privacy of their users. In particular, because these computers normally contain an extensive amount of personal information (accounts, messages, contacts, photos, etc.).
Due, it is vital to encrypt your Android mobile with the aim of adding an extra level of security that could make the difference between a massive embezzlement of identity or kidnapping and a much minor inconvenience. Therefore, in this post, we will let you know the benefits of encrypting your Android and how you can do it step by step.
What are the most serious security and privacy risks on Android?
Before knowing what the main advantages of encrypting and/or encrypting a mobile device Android, it is essential to know the biggest security and privacy risks that this renowned operating system has revealed over the years. Since, in this way, you will achieve create more awareness regarding the relevance of adjusting or optimizing this parameter.
In this sense, below, we mention and detail what these threats are on Android:
the bloatware
This is one of the biggest drawbacks exhibited by the OS platform. Which basically refers to all those PUAs that cannot be uninstalled Of the device. Because, it derives failures with respect to the memory load and the security of the terminals Android because many of them have data collection services that are not always duly informed to the user of the device. Thus, it is possible that they suffer from severe vulnerabilities due to malicious software.
Android Fragmentation
Another risk exhibited by the mobile operating system of Android, In terms of security, it is a substantial problem present in said platform that is known as “Android Fragmentation”.
Which, is that OS updates are retained by the manufacturers themselves of devices in order to prevent compatibility issues, but this prevent security fixes from reaching users. Therefore, depending on the version, there may be notable security flaws that minimize the level of privacy.
software vulnerabilities
One of the main vulnerabilities of Android as a secure operating system, lies in the OpenSSL flaw that affects it directly. Being this, a risk that can admit the access of strangers to the physical memory of the device and even, give administrator privileges on it. Taking into account that normally this depends on system versions.
But apart from the software’s own weaknesses, there are also vulnerabilities in applications installed on computers. Since, many of them are used to insert advertising in other apps and thus, facilitating unwanted actions. Such as, for example, providing access to sensitive user information to malicious people.
Applications in third-party repositories
Although it is true, one of the main advantages of Android This is the number of applications developed exclusively for this platform that allows to have new functionalities in the device and optimize the user experience. However, by acquiring a better level of customization and effectiveness, many people are at significant risk.
Well, with the idea of getting a paid app for free, they choose to enter unofficial sites or third-party repositories to download said app. Considering that, for malicious purposes, many of them can be modified to carry out unreliable actions that range from scams to identity theft.
Custom operating system that generates security holes
By default, users of Android they can personalize their experience to the highest level, but this also presents a security risk in the OS. Since, when it comes to modifying the system to add more layers of customization or launchers, they get remarkable flexibility, but also produce security breaches. Given that the modifications made can facilitate various attacks that have been designed to access via android settings to affect users.
For example, some time ago, several researchers discovered that modifying the icons on the main screen through a launcher, apart from changing the appearance of the device, also stopped registering apps that redirected the user to a malicious web page. As well as this type of attack, there are many more than they vilely take advantage of the customization capacity that Android has.
Why should you encrypt your smartphone and its files? Advantages for your privacy
As we mentioned before, in a usual way, users often save their personal information on the mobile device for greater comfort and effectiveness when managing it. This means that the vast majority of Android devices contain a large amount of personal data of its userswhether your data, accounts emailsocial network accounts, messages, photos, contacts, etc.
Therefore, if optimal privacy is not set in order to encrypt a smartphone, it is possible that all this information fall into the hands of malicious people who wish to carry out their illegal actions. Whereas currently there are different kinds of attacks of which you can be a victimif you do not protect your mobile properly.
In this sense, the fact of encrypting your smartphone, your files and all the information you handle through the terminal, it is completely essential. Well, in this way, you will prevent any prying eyes from stalking you in view of your vulnerability and commit a crime that affects your integrity. Now, beyond understanding the importance of encrypting a mobile Android Due to the risks involved, it is valuable to know what are each and every one of the advantages that this fact facilitates people.
Which we name here:
- Of course, you acquire a higher level of security. Since, when encrypting your mobile Android, you will be building a wall that will prevent other people from accessing the content you save on your smartphone.
- In case of loss or theft, all the information you store on your computer will be kept safe. Since, if you use an encryption key, it will be impossible for a third party to decrypt it to enter the memory of the telephone and see what it contains.
- Encrypt your smartphone and its files, allows you have full control over who can view what’s inside it. With which, you will optimize your user experience.
- Thanks to the fact that it offers you the possibility of improving your user experienceOf course, it also means adding a higher level of customization. That is to say, encrypt your Android mobile it is essential to individualize the security parameters, according to your requirements.
Learn step by step how to encrypt an Android from scratch and make it more private
Before starting the encryption process in Android, It is important to take into account two main aspects. The first of them is based on it is necessary to have some screen lock passwordOtherwise, you will not be able to encrypt your Android. On the other hand, the other parameter It consists of charging the phone 100% to prevent data loss, in case the battery runs out.
That said, it is time to proceed to encrypt your Android smartphone from scratch in order to acquire a better user experience and protect your privacy in a powerful way:
Set your password (if you don’t already have one)
If you still don’t have one screen lock key, it is essential that you configure one, before encrypting your mobile device. For this, go to the Settings, select the “Lock screen” option and through “screen lock type”, proceed to choose the one you prefer to set and save it. In order to encrypt the mobile phone, it is recommended to use a PIN or password as a screen lock. Since, in this case, the lock pattern, facial recognition and swipe are not valid.
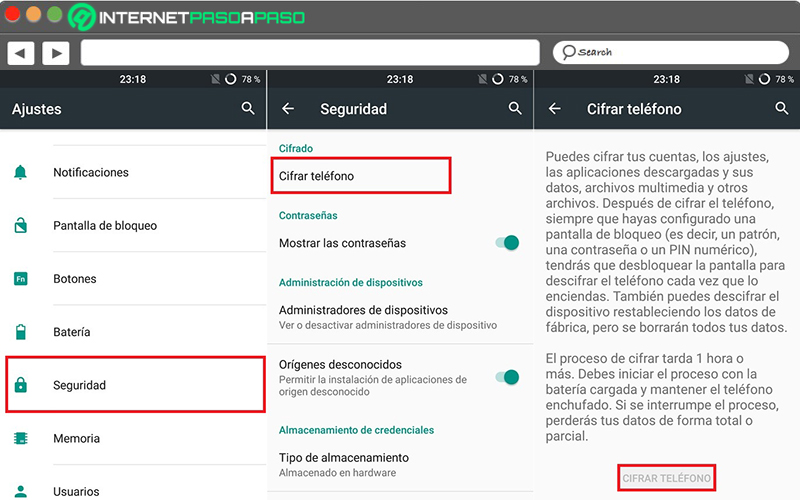
Access the device settings
After having a PIN, To start, you have to enter the application of Settings from your mobile phone or tablet Android. To do this, simply locate the app icon in the general menu of the device and click on it.
Click on the “Security” option
Once you enter the menu Settings of your device Android, it’s necessary that look for the section that says “Security” to be able to locate the available options of Code either Encrypt. Taking into account that, according to the terminal manufacturer, these names may vary.
Select “Encrypt phone”
Next, in the section called “Encryption”, you will find the option required to encrypt your computer. so you have to press “Encrypt phone” to be able to start this process, confirming the action by clicking again on the button that says “Encrypt phone”.
Once the above is done, it only remains wait for the encryption process to finish. which, generally, takes one hour and cannot be interrupted in any way, otherwise it will have to be started again. For this reason, it is important that you have the mobile or tablet fully charged or even, connect the terminal to the current while data encryption is performed.
List of the best apps to improve your privacy on Android and protect your data
Apart from adjusting the settings of your mobile Android in terms of data encryption, you can also make use of some applications compatible with said operating system to optimize your privacy and acquire a maximum level of security.
As a consequence, below, we present three of the best applications for it:
1Password
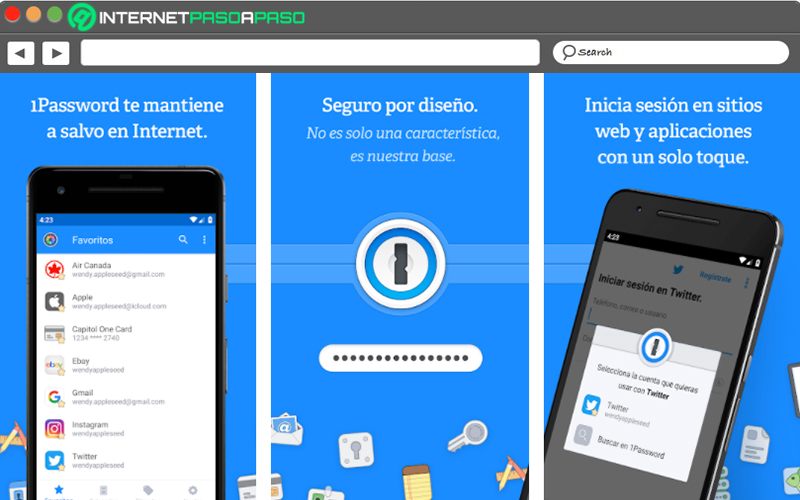
It is a mobile application available on the Play Store characterized by its effectiveness in protect passwords securely and control their privacy through your Android device. Since, it is a tool that uses a 256-bit AES military encryption system to ensure the greatest protection possible.
For its part, it also allows you to block the app automatically in order to safeguard your information and make sure it is fully protected, in case of theft or loss. Additionally, it is capable of create unique and strong passwords for all your accountsallows you to have access to your personal data on all your computers reliably and organize your information in different vaults to protect different areas of your life separately.
Signal
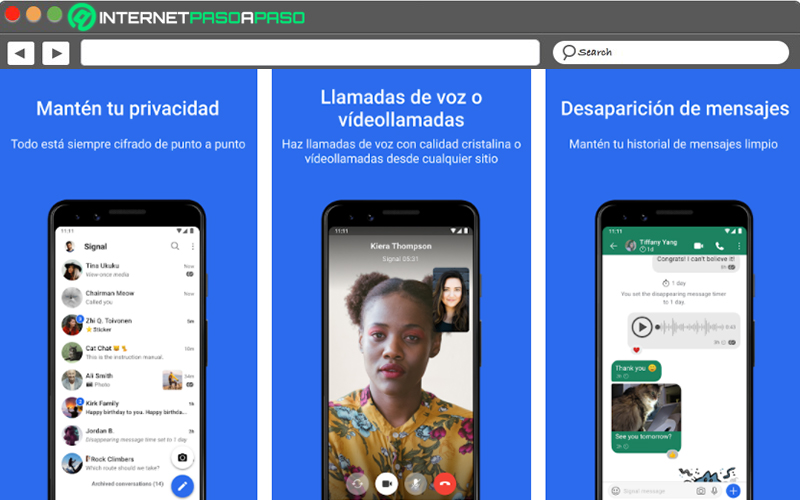
If you wish encrypt your communications by text and voice calls, it is recommended that you download and install this application on your mobile device. Well, it consists of an ideal tool to communicate instantly every day, send and receive confidential messages, as well as participate in high-definition voice and video calls, as safely as possible. Thanks to the fact that the technology of this mobile app has the ability to keep the privacy of conversations as high as possible.
So, for free, you can communicate what you want without the fear that some unwanted third party is aware of it. Taking into account that, Signal uses an advanced open source protocol with end-to-end encryption to guarantee your privacy. Also, characterized by its speedas messages are reliably and automatically delivered in the most restricted environment possible.
DuckDuckGo
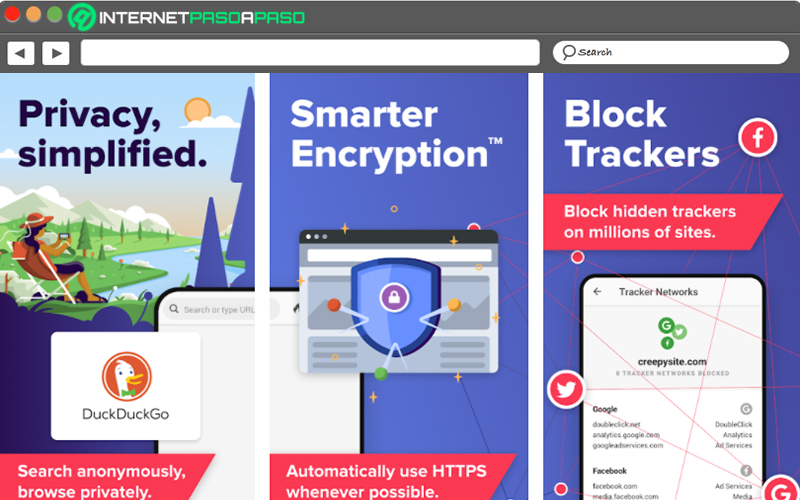
to navigate in Internet securely through your mobile or tablet Android and maximize your privacy in this environment, we advise you download and use the DuckDuckGo mobile app. Being this, a fundamental tool to preserve privacy and security when browsing the net. Considering that, by default, it is a browser that uses encrypted connections and blocks page crawlers.
In addition to that, so that users can feel safe, this well-known browser deals with showing an assessment about the Degree of Privacy that it obtains, every time you enter a website. With this, people will be able to know, for sure, what is your degree of internet protection. Even the Degree of Privacy manages to minimize hidden tracking networks and avoid practices against the privacy of each person.
Privacy