
UPDATED ✅ Do you need to know how many devices are connected to my router equipment and you don’t know how to disconnect them? ⭐ ENTER HERE ⭐ and discover how it’s done ✅ EASY and FAST ✅
Surely you have begun to notice something strange in your Internet connection, maybe it starts to be a little slower, or new devices connected to it start to appear and you don’t know who they are. Keep in mind that it is very possible that there are other people stealing your WiFi network.
Currently there are many WiFi theftseither through applications or hacker, which has made all these much more susceptible wireless networks. One of the ways to detect if there are intruders in your internet network is if your connection becomes intermittent or begins to constantly lose speed. Other reasons to discover if your Internet is being stolen is if your connection starts to be fast early in the day and during the course of the day. day the signal decreases, Sometimes even non-existent.
In this way, here we will teach you how detect possible intruders in your WiFi network and how to disconnect them from it either from the mobile phone or computer, thus avoiding that steal your WiFi signal and slow down your connection speed.
Steps to detect and check who has connected to your Wi-Fi network
Being able to know if your connection is being stolen is something possible today. This has become a great tool since it allows us to have greater security against potential intruders or cybercriminals. In this way, here we show you some of the ways to be able to verify that people have entered your wireless network without your permission, to do so follow the methods below.
On your Windows computer
It is important to mention that this type of topic covers a great content, that is why here we will try to be as specific as possible so that they can get good results and prevent them from continuing stealing your connection.
To do this, if you have a Windows computer, perform the following steps:
- To start with all this it will be necessary to enter the configuration of our network adapter, this in order to check the gateway. For this, we are going to “Control Panel” and then “Network and Internet”.
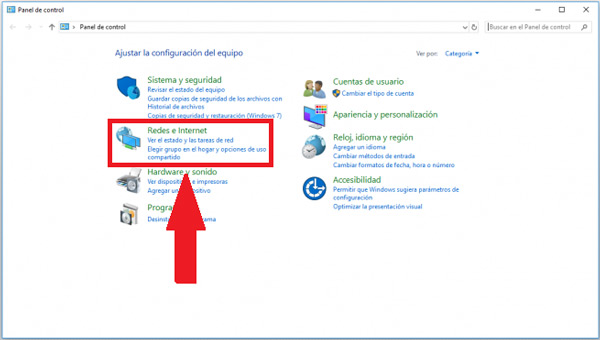
- Now four options will appear on the screen, there we click on “Center network and sharing”.
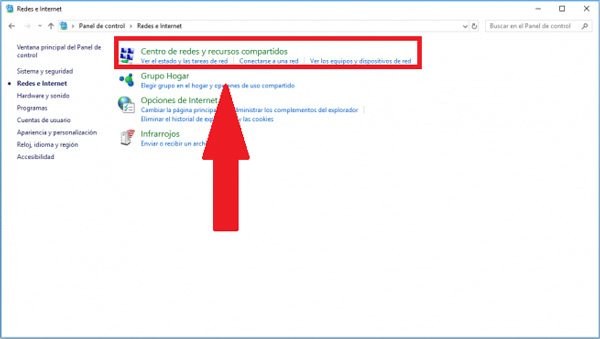
- In the new window that appears on the screen, we select the network that offers us the connection, in this case, it is a wired connection.
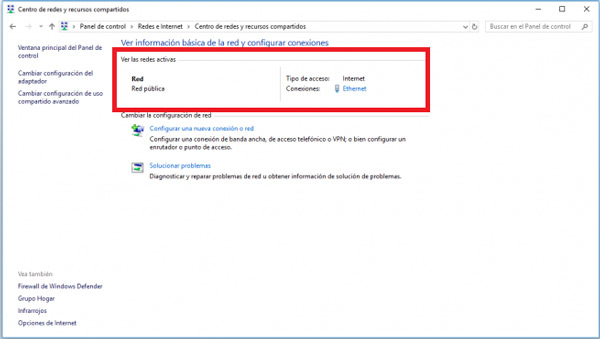
- When we select the network option, a new window opens, there we select “Details”.
- Here will appear the gateway that we will have to use to access the “Router Configuration”.
- Now with the command that appears in the option “Gateway” we use it to continue with the process. Possibly different paths may exist, that is why we must choose the IP address more similar to ours.
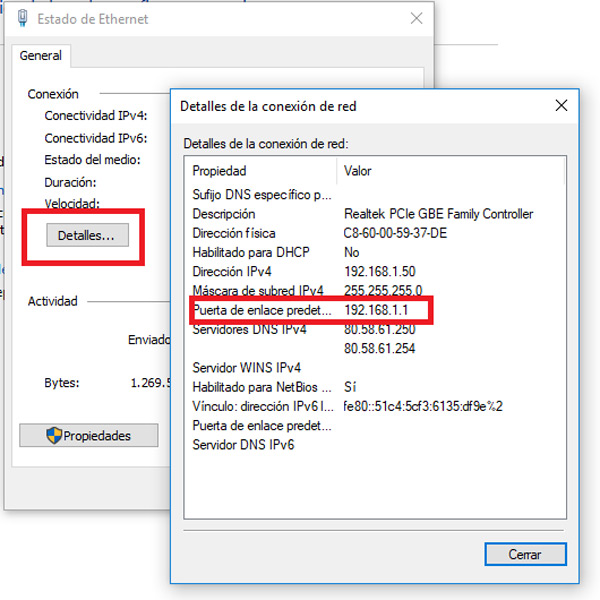
- Once we have the IP address It only remains to enter the browser of your choice and in the web address bar we copy the IP and press “Enter”. Guide to enter the router here.
- This will send us to configuration menu of your router. Keep in mind that this will vary depending on the equipment we use.
- Here you will access the settings menu of your device.
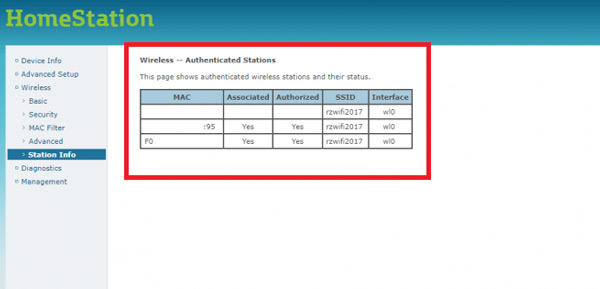
- Once inside the “Setting” from the team we went to the wireless section, “Wireless or Wi-Fi” This will basically depend on the equipment we use. Here different options will appear, in this case it is used “Station info”, can also appear as “Client List” or names similar to these two.
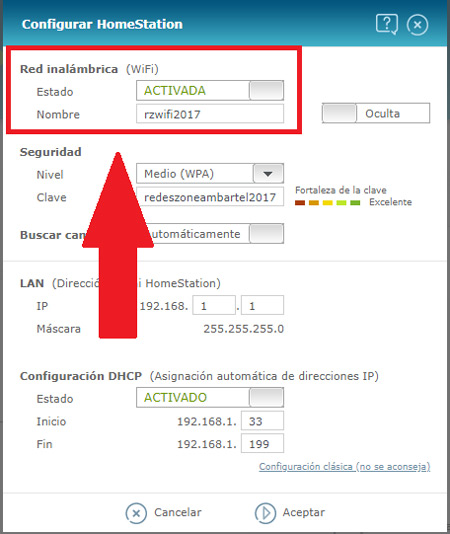
- Now a new window will appear with a box, there it will appear who or who is accessing without your consent and is stealing the wifi.
Keep in mind that once all this is done, and having verified that there are other users stealing your wireless connection, It will be necessary to find a solution to stop this. In this case what can be done is change the password of the same or in that case create one if you do not have it. In this way you can prevent other people from continuing to benefit from your services for free and lowering your connection features.
for macOS
In the case of macOS you can also detect that intruders are using your Wi-Fi network and therefore it has started to work more slowly or the connection drops from time to time, thus causing poor service and an inconvenience when using the connection.
It is important that whenever there is a wireless connection the greatest possible security is taken into account, since anyone with a little computer knowledge could violate the access to your network and start stealing it from you. For this, here we explain how you can detect potential intruders on your Internet.
To do this it is possible to use different programs that we find in the market, one of the most recommended is Wireless Network Watcher, To use it follow these steps:
Download Wireless Network Watcher
- Begins downloading said program to your computer and then it you install. Keep in mind that you can download in a ZIP file with all the program information.
- next thing will be unzip said ZIP file and then we run the program exe.
- Once executed and after a few seconds the program will automatically start to show you a list with all the devices that are connected at that moment in your Wi-Fi network.
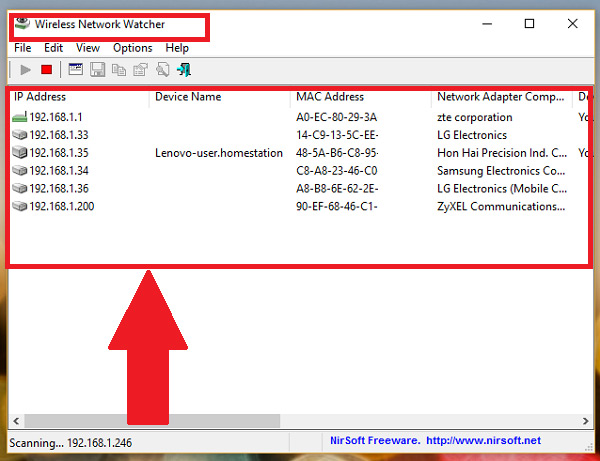
- In the event that it does not recognize the devices that appear in said list, you can select each one of them by right clicking on the device. there you can see the specifications of each one as well as the MAC address of the same. In this way you will be able to realize that computers are connected to your wireless Internet without your authorization.
- In this case, it is recommended change wifi password, that way all teams will be expelled from the connection and you only reconnect the equipment that is authorized by you.
From your Android or iPhone mobile
In the event that you are using the WiFi network of your mobile device, be it Android or iPhone, and you have doubts that there are other people stealing your Internet, you can start using some mobile applications that will help you discover this type of thing.
In this case we will use the app “Fing Network Scanner”. You can get this tool available for both android devices like in iOS. It is completely free and you will get it at Google Play or the App Store. In addition, it is very light and easy to use.
- The first thing you will have to do is download the application on your terminal.
- Once installed you will have to start “Fing Network Scanner”.
- When the application starts, the first thing it will do is show on the screen how many and which devices are connected to your WiFi.
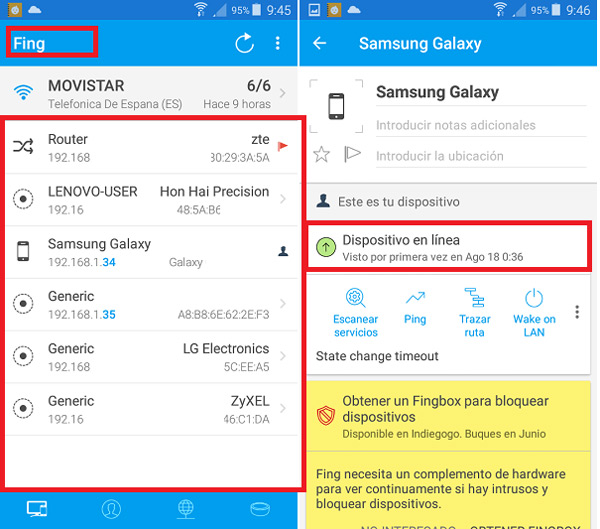
- One of the main advantages of this program is its speed in detecting the computers linked to the Wi-Fi network. So much so, that even his own router where does the wireless connection will appear on the screen.
- Now you have to identify each of the computers that appear in that list, there you will be able to see which computers use your network. In the event that only those that you know or authorizes it will mean that you do not have any intruders. However, this action it is recommended to do it every so oftenor, because these intruders can enter at times other than those you check. Therefore, you must be lucky to notice who else is using your wireless connection.
- In the event that a team appears that you do not recognize, you can click on it. In this way you will access its specifications, such as brand, model, mac address, among other features that will help you to know whether or not you remove the device from your network.
It is important to mention that it is recommended to carry out this process when your Internet goes from a good operation to a bad operation, that is, from working quickly and evenly, to lower your speed and fail the same connection simultaneously. Usually this happens when you start to steal your WiFi.
without using programs
One of the best ways to avoid intruders in your WiFi network is using the MAC filters. This consists of creating either a blacklist or a whitelist, the latter being the easiest to use. Here it is about creating a list of the devices that cannot access your network or just make a list with the MAC of the computers that can access the network.
That is, only those devices that appear on that list will be able to enjoy your Wi-Fi. To do this, just follow the instructions below.
- The first thing to do is introduce your IP address on the address bar of your favorite browser. Note that you must have both the user as the password of your router.
- Once you have entered its menu, you will have to look for the “Administration panel”.
- Next you look for the “MAC Filters”. In the event that you have already detected the intruder and have his MAC address you can copy it and enter it in the blacklist to block its access to the network.
- Another way to avoid these intruders is filtering only the MAC addresses that you want to connect to your WiFi network. To do this you just have to create a white list with the MAC address of the equipment that will allow you to use your wireless connection. This is considered the best option to control this, since only you decide who uses and who your Internet.
How to block and expel intruders and thus prevent them from stealing your Wi-Fi signal? List of security measures
Having your Wi-Fi stolen every day and at any time can be something that ends up making you very angry, since a stranger is benefiting from your services without any cost and permission and, in addition, they may be damaging your signal. In such a way, that you want to take quick and effective solutions to be able to block Wi-Fi signal and expel the intruders that steal your signal.
Best of all, there is a way to definitively expel these intruders, pFor this, it will be necessary to carry out the steps that we explain below:
- the first thing will be use the IP address of the router, which we are going to copy in the browser search bar. To be able to enter the configuration of the equipment you must know both the user as the password.
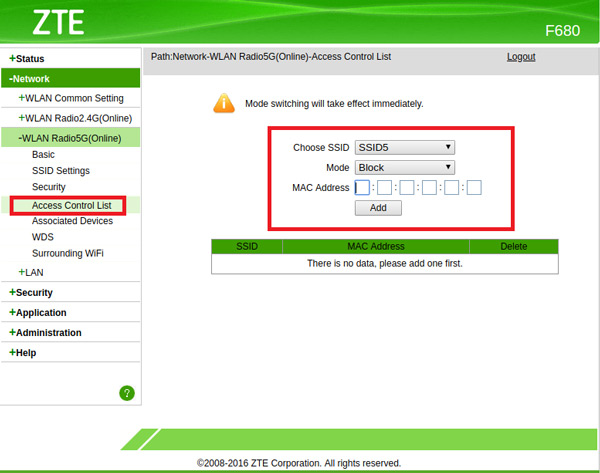
- Once entered the menu, you will find an option called “Access Control”, “MAC Filtering”, “MAC Filtering” or other similar names, keep in mind that this will depend on the brand of the router that you are using.
- In this section you will have to add the MAC address that you don’t want to reconnect on your wireless network.
- Here you only have to select the option of “Block mode” and copy the MAC address of the device that is stealing your Internet. Once it is included and save this person will not be able to access the network anymore.
Another way to avoid possible intruders in your wireless network is taking a series of security measures that will help you to have a greater protection in your connection.
Among them we can apply the following:
- constantly change your router password, this is a measure that we must apply every week or every fortnight at least. This will help eliminate all those people who for some reason have taken your password or have been discovered.
- If you have noticed a new device connected to your WiFi network, you can change so much the name as the password of it immediately.
- Choose a password with a WPA2 encryption for added security. All routers offer different security options for the wireless connection. The most recommended is bypass WEP passwords and use the wpa2 encryption, as they offer greater security.
Best programs and applications to know who is connected to your wi-fi network and is stealing your bandwidth
Today there is a large number of programs and applications that allow you to discover who is connected to your Wi-Fi network. In this way, you will be able to realize if there is an intruder who is stealing your connection.
Especially if you have doubts about this or your Internet has started to slow down or even have connection drops simultaneously.
Thus, here we present some programs that you can get for free and that will help you discover that mobile devices or computers are connected to your network.
Microsoft Message Analyzer

We start the list with this program microsoft, a very up-to-date tool that is capable of capturing and analyzing all the system traffic. In addition, it has a system tracking that will allow you to analyze each of the log files.
This program has been improved and updated with the aim of becoming the successor of Microsoft NetworkMonitorand that will help you to be able to detect which people are violating your security and thus stealing your Internet connection. To do this, it performs data visualizations of trace, record and other system message data. It also uses an online viewer and graphs to be able to obtain all the possible statistics of the system.
SoftPerfect Wi-Fi Guard
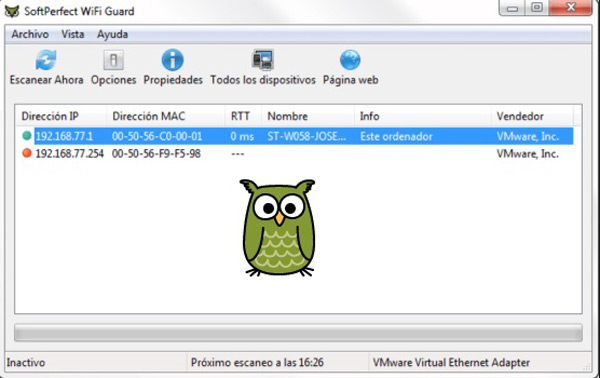
If you are one of the users who have small wireless networks and you want to keep it safe from any possible intruder you can use SoftPerfect, which becomes one of your best options.
It is noteworthy that today wireless networks have been improving their system security, where have they gone from WEP passwords to WPA2 ciphers thus offering a best security system. However, we are in a world where everything advances and the weaknesses become more and more noticeable. This is how these networks today are not saved from being attacked and their security is constantly being violated.
Wireless Network Watcher
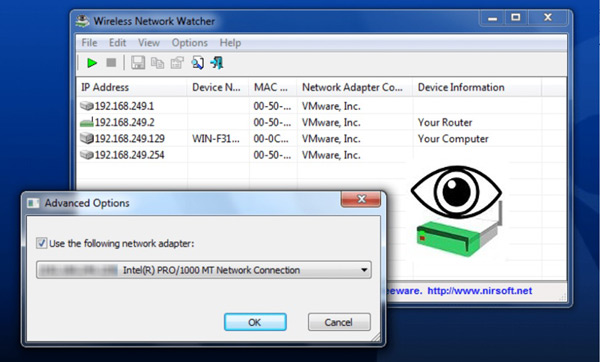
You can get this program available for windows computers and is responsible for teaching through an analysis all computers and mobile devices connected to your Wi-Fi network. This way you can have a record of who access your connectionas well as discovering those intruders to later be able to block them.
Each of the devices shown in the list provided by Wireless Network They carry the following data: IP address, MAC address, company and device name.
Angry IP Scanner
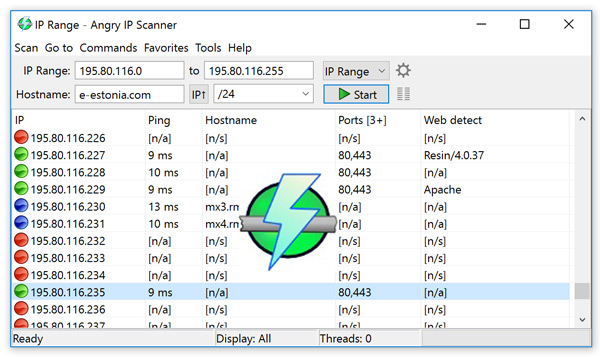
One of the lightest applications on the market, in addition, does not need any type of installation, allowing you to use anywhere. Its main function is find ip addresses in any range. Thus offering a record of all those devices that are connected to your WiFi network.
Among their main features is that they offer the name of the equipment, its MAC address, it scans ports, among others. A very useful tool to be informed of any possible intruder on the network.
WireShark
This analyzer program is currently the most widely used worldwideand among its main characteristics we can find that it allows see which devices are connected at any given time to your wireless network. Wireshark It is used by many companies and large-scale businesses and best of all, you can buy it totally free which gives it a touch of greater credibility.
networks