
Index:
UPDATED ✅ Want to protect your privacy with encrypted calls from the Zoom app? ⭐ ENTER HERE ⭐ Learn How FROM ZERO! ⭐
End-to-end encryption is the act of apply an encryption to the issued information from a device so that the only one who can decrypt it is the recipient’s device.
In the case of Zoom has added a verification process for E2EE as “risk-based authentication” which is in charge of encrypting the videoconferences carried out to fight against abuse and guarantee the privacy of the users. Today, this feature is available for both free and premium users.
Indeed, it is suitable make end-to-end encrypted calls on Zoom and for this reason, in this post, we will teach you the steps to follow to get encrypted calls on Android, iOS, Windows and macOS.
Benefits of encrypted Zoom calls
While it is true, end-to-end encryption on Zoom video calls deals with providing additional protection for users. Thus, both senders and receivers can obtain the greatest possible security when transferring any type of data, so that no third party can read the messages exchanged.
Indeed, when end-to-end encrypted calls are used in Zoom, no one else will have the ability to monitor the network to see the content of your message, not even the communications company itself. Since, Zoom does not have the option to proactively monitor meeting content and it also does not share information with law enforcement.
Therefore, the benefits of encrypted Zoom calls can be summarized as follows:
- It is a utility that guarantees complete security and privacy of your communicationsas they are impossible to crack by third parties and intermediaries.
- Even if someone manages to hack into the system or steal the data, end-to-end encryption prevents me from reading them because it places an additional layer of encryption on the information.
- It allows obtain the greatest possible confidentialitygiven that no one will find a way to decipher your messages and thus you can deal with the topic you want freely.
- It is ideal for increase protection against certain types of cyberattacksespecially phishing scams and man-in-the-middle attacks.
Requirements to get Zoom end-to-end encrypted calls
To enable Zoom end-to-end encrypted callsit is important to comply with certain requirements or demands that the company itself has determined.
Next, we present the main ones:
- Users of Windows, Mac OS and Linux have to install the program Zoom Desktop Client with version 4.0 or later.
- To activate the function in the Zoom mobile appboth on Android and on iPhone and iPad, it is essential to have the version 4.0 or later of said application.
- who use Zoom Rooms for conference room on Windows, MacOS and Linux, they must use the version 2.2 or later this.
- Meeting hosts with free accounts can only enable end-to-end encryption after verify your phone number through a code obtained via SMS.
On the other hand, it is necessary to clarify that the fact of turn on the end-to-end encrypted video conference feature in Zoom from a version other than 5.5.0, means disabling some software features that do not support such encryption.
These functions include the following:
- Live broadcast.
- Cloud recording.
- Rooms for small groups.
- Access before the host.
- Private chats between two users.
- Live transcript.
- Reactions at the meeting.
- Take votes.
- ZoomApps.
Consequently, If you want to make use of these features and at the same time take advantage of the end-to-end encryption function in Zoom, you will have to install version 5.5.0 on your mobile, computer or Zoom Rooms. so that they are compatible with each other.
Learn how to verify your identity to make encrypted calls on Zoom
While paid Zoom accounts can be directly attached to the end-to-end encrypted meeting feature, free accounts they must verify their identity so you can make encrypted calls in the application or join one of them.
In fact, it is necessary to know each of the steps to follow to carry out this verification in a fast, practical and easy way through Android, iOS, Windows and MacOS:
On Android and iOS
To activate and use end-to-end encrypted meetings for your own use in Zoom through your Android smartphone or tablet, you must follow the following step-by-step:
- First of all, you have to log in to your user account via Zoom Web Portal. In other words, you must open Zoom from the web browser of your mobile, tablet, iPhone or iPad and enter.
- Once you access, tap on the “Schedule a meeting” button and at the top (where it says Meetings), hit the down arrow to there select “Setting”.
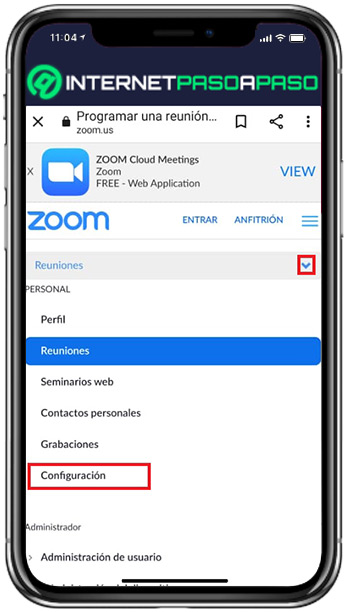
- After this, from the Meeting section, go to the Security section and through it, look for and activate the option that says “Allow the use of end-to-end encryption” moving the switch from left to right.
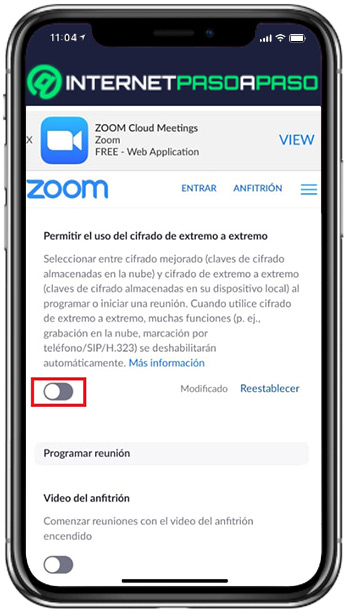
- Next, if you have not verified your identity, you must add your mobile phone number with its area code to receive a code via SMS and enter it in the corresponding field. In case you have already done it, just subtract choose the default Encryption Typeeither by checking the box “Enhanced Encryption” wave of “End-to-End Encryption”.

- In conclusion, press the “Save” button at the bottom of that section and that’s it.
On Windows and macOS
If you are one of those who chooses to manage your Zoom account from the comfort of your PC or Mac, in this case, you will have to complete the following procedure to encrypt your video calls end-to-end in the software:
- Using your trusted web browser, search for Zoom and access its website to log in to your account (with username and password, through Google or from Facebook).
- After entering, go to the left side and in the options bar, click on “Settings”.
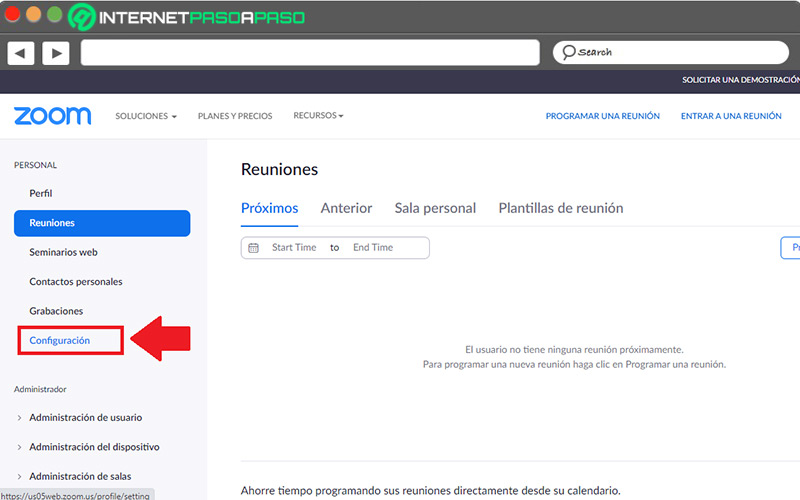
- Then choose the section “Meeting” at the top and through the left sidebar, Click on “Security”.
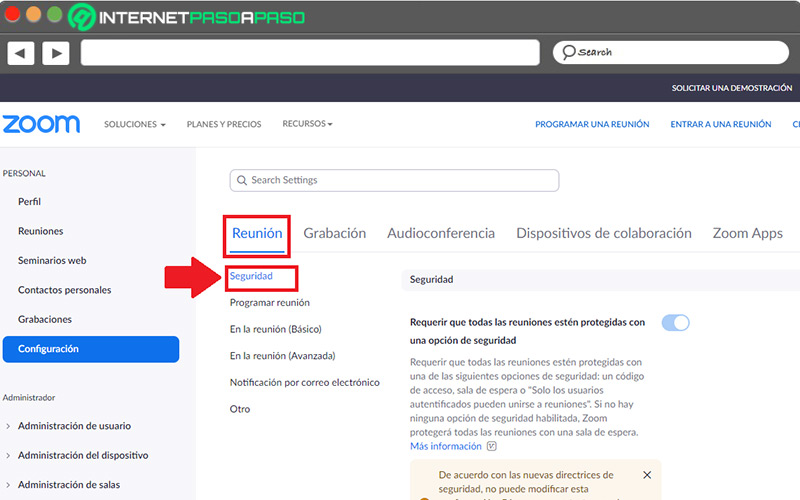
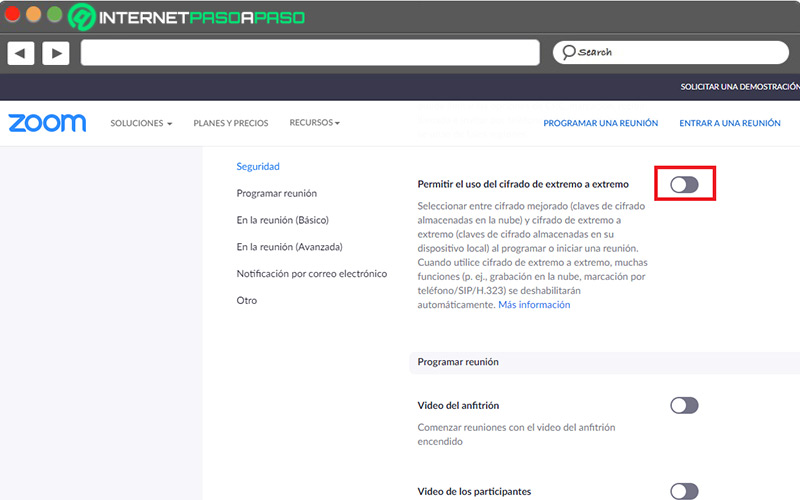
- Once the above is done, navigate through all the options available in the Security section until you find the one that says “Allow the use of end-to-end encryption” and enable it by moving the switch from left to right.
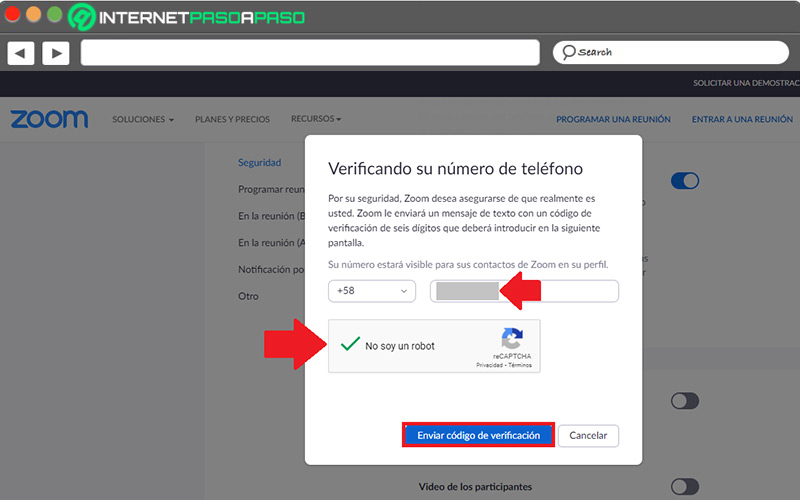
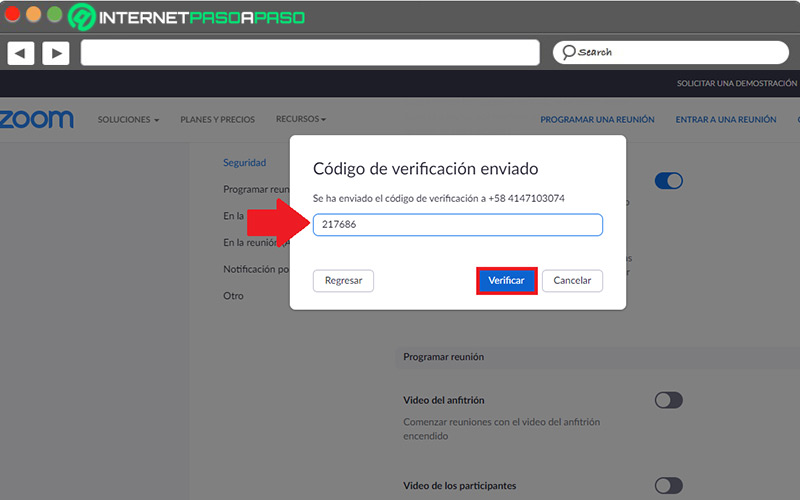
- Next, they will show you a pop-up window from which you must verify your identity. To do this, choose the area code and enter your mobile phone number in the indicated field. So, fill in the captcha and click the “Send verification code” button.
- Once you receive the verification code on your mobile device via SMS, you have to enter it in the field that says “Enter 6-digit code” and press the button “Verify”.
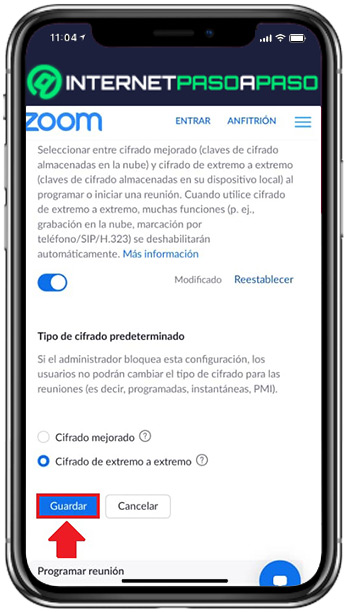
- Finally, the platform allows you to choose the default encryption type: Enhanced Encryption or End-to-End Encryption. So it only remains check the box you prefer and press “Save”.
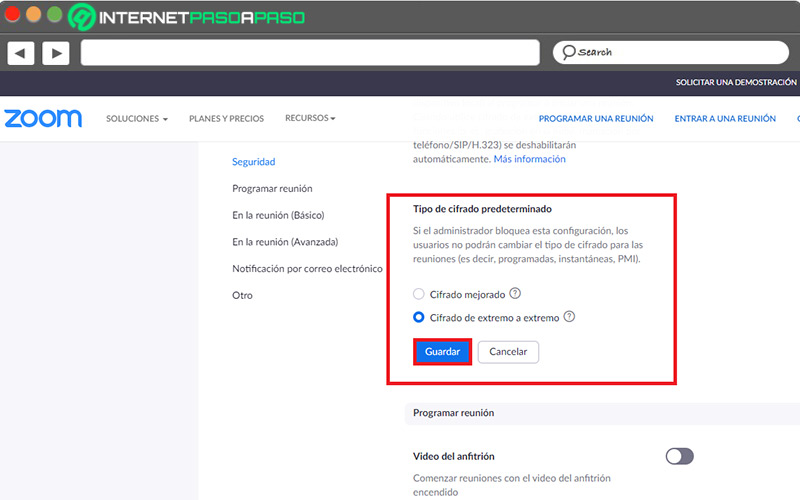
In general, it is recommended to select the “Enhanced Encryption” as the default encryption type, due to the limitations revealed by end-to-end encryption. The latter, it is recommended to activate it when certain meetings with an additional layer of protection are required.
Tips to improve the privacy of your Zoom account
Beyond enable end-to-end encrypted video calls in Zoomit is also valuable to consider other best practices for optimize the security and privacy of your Zoom accountin order to protect the information you exchange through the platform.
Consequently, if you want to further increase the confidentiality of the meetings you hold on Zoom and maintain an extra layer of protection, it is ideal to consider the following:
Use a password to protect each conference
One of the best measures to ensure that unwanted people do not access your Zoom meetings, is to protect each conference with a password. Which, of course, is a different password than the one you use to log into your account.
By default, these passwords are known as meeting id and they are predetermined by the platform itself. So, it is important share them only, exclusively and directly with the users you want to invite. Well, it is not ideal for them to appear on social networks or other public channels.
Use a two-factor authentication system
It is also advised to take advantage of Zoom’s support for two-factor authentication (2FA) which is a highly secure method of logging into a user account. Since, in addition to entering the email and password, another additional data is used to access the account.
With this extra layer of security, Zoom users will prevent anyone from logging in using a personal meeting ID they’re hosting. Thus preventing the interruption of intermediaries or unwanted third parties.
Activate the room wait zoom

To have much more control over your user account in terms of security, it is optimal make use of the “Waiting room” function which consists of a tool from which the host can give permission to the people who have joined the meeting.
In this way, it is much easier to detect the presence of intruders and rule them out before starting the videoconference. Taking into account that this function allows you to approve the entry of each participant one by one and, in addition, expel any unwanted personeasily.
Choose register with your work email on Zoom

Another of the most effective practices to increase the security of your Zoom account consists of sign up using your work email (or work). Since, this will help you prevent the company from sharing your contact information with third parties, assuming it is a domain of your workgroup.
Thus, Zoom will only be able to share your work contact information with your real colleagues and in effect, you can keep your personal email totally privateas well as your personal contact details.
Privacy