
Index:
UPDATED ✅ Do you want to learn about internet privacy for journalists and protect your investigative work? ⭐ ENTER HERE ⭐ and Learn it ✅ EASY and FAST ✅
Online privacy has become a state issue for regular Internet users for several years. Protecting our personal information is very importantespecially when among it are crucial data of our work.
In the case of journalists, the case is much more delicate and the protection of information is of life or death importance. Not only because it can reveal controversial information about a news event, but also because ongoing threats to press freedom today.
If you are a journalist, you must take your task of spreading the truth more seriously, and more importantly, protect it above all else. That is why today we will teach you everything you need to know about Internet privacy for journalism professionals worldwide.
Press vs Institutions; a war for free speech

Throughout history, journalism has been seen as a direct enemy of politics and institutions. For most of the last century, journalists faced censorship, at a time when dictatorships put gags on freedom of expression.
With the arrival of the 21st century it was believed that this would change, but beyond that what it did was evolve. Although there are no longer so many dictatorships, we see how government cabinets in the United States prohibit access to press conferences that were always freeor as government agencies in Venezuela even refuse to provide real data on the situation in the country.
This also makes it clear to us that, regardless of ideology, politicians will always be “enemies” journalists, since both in the United States and in Venezuela, perhaps the most representative countries of the capitalist and communist ideologies of the West, indistinctly apply measures to torpedo journalistic work and distort the truth.
Victimization is not a solution either, since these measures have been supported by certain punctual failures of journalists who precisely did not know how to protect their data, and leaks of crucial information occurred for very delicate cases. It is because of that the best weapon in this scenario is to be as professional as possiblesomething in which the privacy of our professional information plays a transcendental role.
Privacy of journalistic information. Why is it so important?

We are normally very jealous of our right to privacy, but in the professional realm this takes on a much more serious tonesince the information handled by a journalist not only affects his life, but precisely the privacy of another person or persons.
Putting together a journalistic investigation case is a multi-stage task, which is developed slowly and during which evidence and important data are collected until the complete case is completed. If in this time some type of information leaks, the whole process would collapseespecially if it has not been confirmed and turns out to be false.
Although every journalist has the right to give his/her erratum, the image of a professional whose name is involved in a slander case is usually very tarnishedand not only his own but that of the entire media outlet for which he works and even reaches the entire guild.
According to the Spanish Penal Code, for a journalist who incurs in these irregular behaviors, a heavy sentence could even be awarded, including jail time, as long as it is shown that he or she was aware of the falsity of the data, and not that he was manipulated by his source to give false news.
In any case, all these problems can be easily avoided. if the professional has strong security habits that guarantee data protection that it collects in each of its cases. Thus giving crucial importance to privacy for journalists, especially when it is online.
What are the most important aspects of a journalist’s privacy?
While the Internet has completely changed the way journalists around the world do their jobs, making it easier in some ways, privacy priorities for a journalist remain the same as they have always beenwith the difference that now you will have to apply new methods to guarantee it.
source protection

The protection of the source is undoubtedly one of the main concerns of any journalist, as this could make or break your work. A person who provides us with important information in a case must have all the guarantees that his identity will be completely anonymous and that his life will not be affected by the information he is providing.
This is especially important in cases of corruption, drug trafficking or organized crime, where revealing the name of the source could directly compromise your life and that of your relatives.
Data verification

We journalists run into more than one obstacle to carry out our work. The world is full of cases of “fake sources” working to create disinformation and offer misinformation to sabotage high-profile cases. This not only happens in politics, but also in almost all sectors.
No matter how many years and how reliable a source is, a journalist must always verify each and every one of the data that comes into her hands through whoever. In this way you protect your work and you guarantee that everything you have done well will not fall apart because of an injurious fact..
Information coding

Previously, journalists used notebooks to make notes and these were generally made in code, so that no one other than the journalist could understand them if they fell into the wrong hands. In fact, even today the journalists of the “Old School” these mechanisms continue to apply.
Nowadays, with the advent of smart devices and cloud storage solutions and other technologiesnew ways of encoding information are created so that no one other than ourselves can even get to visualize it.
Work tools
The Internet offers journalists a wide range of tools to facilitate their work. In these tools there is usually a lot of data about our workincluding contact information with sources or clues about new cases to be developed.
Therefore, when choosing online applications and programs to carry out our work, it is important to use those that offer us the highest level of privacy possible, guaranteeing that no third party can enter them or violate their security in any way.
Anonymity

Being 100% anonymous on the Internet is almost utopian, practically impossible, but at least we can reach a point where to be discovered we must be tracked by a true computer genius. For this reason, everything that helps maintain our anonymity online is a plus that we are obliged to do..
VPNs can assure us that our IP address cannot be discovered, in such a way that it is not known in which web portals we have recently navigated. In addition, it is also important to constantly delete our browsing history, as well as use a browser like Tor that gives us greater guarantees than Google Chrome or Mozilla.
Information storage

Analog recorders and notes are a thing of the past and it is a fact that more than 80% of the world’s journalists’ guild use technology to store their information. In that sense, there are multiple methods a press officer can apply to protect their investigation.
There are essentially three methods of storing information today, and all have their strengths. For a journalist it is important to consider all three:
- local storage: This method is the most used by all Internet users, and is made up of the physical disks of your main work computer. In it will always be the most important data of the investigation so that you can constantly access it without much inconvenience.
- external drives: external storage systems consist of a physical disk in which the information is saved as a backup to recover it in case it is lost from the main disk. Removable USB sticks and similar devices are often used for this.
- Servers or the cloud: cloud storage is one of the safest since there is no physical way to access the information, and it is stored on digital servers. It is an efficient way to make backup copies and, above all, to be able to access data from any device.
Tips to protect the identity of your most important sources
Source protection is every journalist’s top priority. This is a complex process that begins long before you even determine who your informant will be, since you must put together certain mechanisms so that it contacts you with the guarantees that your anonymity will remain intact.
Devise safe channels to establish contact
In a highly controversial case, don’t expect the answers to come to you by themselves. You must follow your nose and scrutinize until things come to light, that’s how this job works. Once you uncover enough pots, there will be people interested in hiring their version of the story and for that you must leave them a safe way to contact you without being discovered.
Telegram is one of the most secure messaging applications out there, with complex encryption methods to protect the privacy of its users. In fact, they have confronted US entities for not disclosing their information and have won.
Another safe way is to use temporary emails, since these are deleted after certain days and everything that is spoken through them in that time will also disappear.
journalistic professional secrecy
Professional secrecy is a right to privacy and protection of information and the way in which it is obtained, that a journalist has about his work. No one, absolutely no one in the world can require you to openly reveal the personal data of your informantseven if it is implied that the information they reveal to you is false.
This right is not exclusive to journalists, it also occurs with psychologists, who cannot reveal the confessions of their patients either, even if they claim to have committed a crime, as well as in Catholic priests and bishops.
Interpret information impartially
A mistake that many journalists make is that when they receive crucial information from a source about a case, they focus only on seeing the points that favor their investigation. It is important to always remain lucid and analyze what each data means and how it affects the general interpretation of everything.
An error of interpretation is serious, since it could also be argued as insult, which would bring all the work down and make all the risk your source took to inform you of the topic lost.
Choose the communication medium well
Yesteryear, a media outlet was responsible for ensuring full protection of the data provided by its journalists in an investigative case. However, the role of newspapers has been considerably distorted. The Internet has made it possible for anyone with a computer at home to start a “Digital Diary”.
Many of these digital newspapers are seen more as a business model than as a true channel to defend the truth and make it known to the public, so they don’t understand the true meaning of protecting a sourcesince their goal is to make money and sell advertising, and if for that they have to sell their soul to the devil, then they’re delighted.
This puts journalists in a real minefield where one mistake could spill all the secrets of their work. Thus, When making a complaint, journalists use their independent media or social network accounts to make the truth known.instead of entrusting the information to any modern means of communication.
Secure your mobile phone

Edward Snowden is a name you will read a lot about in this article. He is a former NSA employee who developed a device for iPhones that detects any vulnerabilities and information leaks from them. The name of this is Introspection Engine. The announcement of this open source hardware was announced in 2017, and it is expected to be ready in early 2020.
What this tool does is that it performs a thorough scan of the entire system and detects if any application is running that transmits data via GPS, Bluetooth and other functions that may pose a risk to mobile data.
Methods to verify crucial data and rule out slander and “fake news”
By now you know how to manage to get a source and guarantee your anonymity butWhat guarantees do you have that the information they are providing you is true? This is when the real challenge of a research work begins, especially when it is one of scope and a lot of controversy.
Analyze well the intentions of your source
The main thing when you have a source is to assess their intentions, and especially to interpret the information they are providing you to confirm that they are not including personal judgments but rather raw information. It is normal to meet characters who try to use journalists by providing false information to control public opinion like this, so you should always protect yourself from this.
Compare the information
You won’t be able to make a case with just one source, you’ll need multiple sources to create a solid, well-supported explanation of the facts as they are. Contrasting the information of one and the other is important to find inconsistencies in the version of any of them. The golden rule in the media of yesteryear was that no information would be considered true without first being confirmed by two or more compelling sources.
This should not only be done with a research paper, but with any news event or information that you want to inform the public. So whether you’re investigating embezzlement in your local governmentor doing a report on breast cancer, Contrasting all the information that comes into your hands is important.
Interpretation of the data and the rumor theory
Allport and Postman are two of the most important communicators in our history. Both developed what is now known as rumor theory. This introduces us in the idea that more than 50% of the topics of conversation that we handle are unconfirmed data that he called rumors.
Both make it clear to us and show that people tend to share a lot of information without even verifying it, and what is worse, we tend to add a personal touch when spreading it. However, despite the fact that the vast majority of rumors are lies, they also make us understand that many of them are true, and that is where the journalist’s work begins.
Allport and Postman also give us a series of characteristics that the rumor must fulfill in order to become a social truth despite the fact that it is actually a lie. but they also leave us a guide to rule out rumors and verify the truth:
- What facts surround the rumour? It is important to ask yourself that, since every action has a reaction, so if something is happening, it is possible that the consequences of those acts are already beginning. For example, if you hear in your neighborhood that your neighbors are thinking of separating, a rumor starts, then If when you visit them you notice that they are happy and everything is going well, possibly the rumor is just gossip. On the other hand, if on the contrary you feel tension between them and have witnessed some strong arguments, this rumor may be true. This is a vague example but it perfectly explains what we mean at this point.
- How volatile is it? One of the characteristics of the rumor is that it is very changeable, since each of those who transmit it tend to add their own criteria, which means that in the end different versions of the same event are created. This is a key to know when a rumor is an absolute truth, since when it is so, a solid version of the story tends to be maintained.
Steps to be anonymous and leave no trace in our journalistic investigative work on the Internet
Privacy on the Internet is a topic that constantly generates debate in today’s society, and seeing how companies like Google collect information from each and every one of its users, it is increasingly important to protect it. For an investigative journalist, the issue becomes even more relevant.
Being able to be completely anonymous on the Internet is impossible for many, but there are different methods to maintain anonymity to a certain extent.
I2P
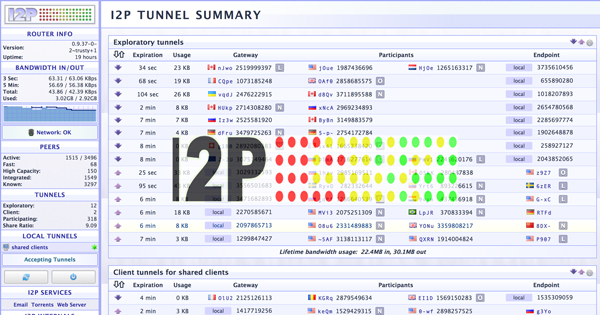
I2P or Invisible Internet Project, is an emerging technology launched to the public in 2014 that consists of a network that guarantees complete anonymity. It is well known for being a reliable alternative to Tor, another project that we will talk about later.
I2P consists of a software that creates a tunnel in all the communications of your computer with the Internet, similar to what a VPN does, but with notable differences.
When you install the program you begin to be part of the network and when you make a request to a server, it forwards the request to a node, which is identified as “Input node A”and this in turn redirects it to another “Exit Node B”which is the one that finally makes the request to the DNS server on duty.
This makes it impossible to know the origin of the request, since each and every one of the network nodes would have to be verified, and even if found, the IP address of this will be encrypted and cannot be known even by the same members of the network.
The latter makes it a better alternative than Tor Browser, which also uses a layered system but in which the IP address of the nodes can be known by the other members and even tracked. For this reason, we have decided to mention I2P before this one.
If you want to join the Invisible Internet project, you simply have to download its program, install it on your computer and activate it. It is light and will not affect the speed of your Internet.
Download I2P Windows
Download I2P macOS
Thor
We cannot fail to mention the Tor network. This is a technology that creates a network of layers to keep the user’s IP anonymous when connected to the Internet. What it does is similar to the abovewith the difference that it is much more difficult to even trace the origin node, since the request bounces off hundreds and thousands of them.
The latter makes it detrimental to your Internet speed, which will be affected, but it is much more reliable when it comes to efficiency. The only inconvenience that its detractors see is the fact that the members of the network can know the IP of the others.
Nevertheless, this problem is solved with the fact that nothing guarantees that the IP from which your node receives the information is the original. That is, this could be one of the many that bounced before reaching you, and you will not be able to know anything about said request other than the node from which it was sent to you and the node to which you sent it.
Edward Snowden used this network to communicate with the journalists to whom almost 6 years ago he shared a series of secrets from the NSA in which it was confirmed that the US National Security Agency spied on everyone using smartphones and certain mobile applications.
To be in the Tor network you simply have to download and install the browser Tor Browserwhich has a very easy to understand interface.
Download Tor Windows
Download Tor macOS
Download Tor Linux
Click on the link and you simply have to choose the operating system corresponding to your computer, and then install the program without problems.
Snowden Project

Snowden’s name is deeply tied to digital privacy for journalists. This former NSA official got fed up with watching the US National Security Agency blatantly spy on everyone right under his nose, violating your innate right to privacy. So I leak all this information to the press.
From that day on he became one of the main enemies of the United States, but he is not daunted and whenever he can he brings out something interesting. In 2017, it announced that it was developing state-of-the-art tools to guarantee the privacy of the work of investigative journalists..
Among the various tools that Snowden has in mind we can identify Sunder, which allows encrypting important data whose key can be given to a group of people who will be the only ones who can access it. This is designed so that journalistic investigation teams can improve data security and share it with each other without fear.
In addition, he is also thinking of a new version of Jitsi that allows videoconferences to be held completely anonymously. Similarly, he mentioned SecureDrop, which is a browser specially developed for journalists and will be used initially by members of the WikiLeaks organization.
All these tools are completely free, and will be released to the public as soon as they are proven to be completely safe.
Tips to protect your storage devices
Storage devices are the daily bread of any storage journalist, and it is on them that you will store the most important data of your case. For this reason, certain security measures must be taken to achieve the goal of being 100% safe on the Internet:
Encrypt your hardware
Hardware encryption is the first line of defense between hackers and the most important information in a case. Currently, it is an issue that causes many headaches because the NSA has a whole division of professionals of the highest level finding ways to crack the most complex ciphers.
Snowden spoke in 2017 of a series of programs that he himself uses to keep himself hidden from the NSA. One of them is the Tor network that we already presented above., But it was not the only one. Among them he also mentioned powerful encryption software whose method was a real headache for the NSA itself.
The program mentioned by the computer genius is Truecrypt, open source and completely free. This has a simple operation, because what it does is establish a password to access the data on any SSD drive or USB flash drive.
However, it is important to keep other options in mind as TrueCrypt it stopped being updated in 2014, just after Snowden mentioned them in his papers. Currently, it continues to be the program with the best encryption, but since it is not updated, it is a matter of time before certain vulnerabilities arise.
Other options you have to encrypt your storage devices are BitLocker Y GNU Privacy Guardboth open source too and with a tremendously strong encryption method.
always back everything up
You must not only take care that the information is stolen, but also that it is damaged. Snowden denounced on multiple occasions that entities such as the NSA used different very powerful computer viruses that have the ability to damage any hardware. For this reason, never have important data in one place..
The safest place to store information today is the cloud. Also, Other options you have are USB flash drives and even CD Rom discs where you can save certain important data.. In this way you will have a whole secure network in which the most important information of your case is found.
encrypt email
You may not know it, but there is nothing more insecure and less private than an email. Currently, these are transmitted in clear text format, which means that there is no technology applied to them to hide their content.
This means that anyone with sufficient permissions, such as your email provider’s sysadmin, or skill enough to grant them to themselves, can read each and every letter you type in your email messages. This has always been the case and is one of Snowden’s biggest concerns..
Fortunately, there are methods that will allow us to encrypt our email communications. One of these is GNU Privacy Guardwhich creates a robust encryption tunnel that will allow us to be certain that no one but us and our recipient will read the emails we write.
Steganography
Steganography is a series of techniques used to encrypt messages within other messages. That is, it is writing a text that contains another message in its content. It is a very old technique that was used in the first wars in human history, and became popular during the cold war between the USA and the USSR.
Steganography is something that you will have to learn sooner or later in a world where nothing is safe anymore when it comes to the Internet. You must devise a method that only you and your work team know perfectly and that no one else can decipher.and taking extreme measures, it will be important that everything that is written about the case is with this technique before publication, maintaining the integrity of the most compromising evidence.
List of the best tools to improve the privacy of your data on the Internet recommended by Snowden
We close this mega guide for journalists with a list of tools recommended by Snowden himself than any investigative journalist you should start using for the benefit of your work and your own safety:
TailLinux

This is a distribution of the Linux operating system that you should start using right now on your work computers. This has been programmed in such a way that no one can hack it, identifying the most important system vulnerabilities and correcting them so that no malicious program takes advantage of them.
It’s completely free and open source, so if you have extensive computer skills you can even make your own tweaks to the OS.
SecureDrop
It is an application that allows secure communication between journalists thanks to the benefits of the Tor network. This is one of the first apps that make use of this technology to encrypt communications and Snowden highly recommends it over many other tools.
Download SecureDrop Windows
OTH
This is an instant messaging app like WhatsApp that allows communication between journalists through chats. It has very strong encryption and the NSA itself catalogs it as one of the technologies that gives it the most problems when attacking.
VeraCrypt
This is for users the best possible alternative to the TrueCrypt that Snowden recommended in 2014, which has a powerful encryption method to protect our storage devices, these being very difficult to decrypt to violate user privacy. It is also open source and completely free.
Download VeraCrypt Windows
Download VeraCrypt Linux
Privacy