
Index:
UPDATED ✅ Malware is any malicious program or file that tries to violate the security and privacy of your computer ⭐ ENTER HERE ⭐ and Learn more
The Internet and computing in general have endowed us with multiple benefits from its inception until now, and each time it seems that they will be more and better. However, not everything is rosy, and just as there are many good things, there are also others that are not so good..
In this sense, no doubt computer viruses are one of the biggest problems of the modern Internet, that no matter how many advances it makes, cybercriminals find ways to create programs that take advantage of vulnerabilities in our systems.
Malware is one of the most problematic computer viruses and in this article we are going to teach you everything you need to know about themso you can learn to identify them and remove them from your computers to keep your data always 100% protected.
What is malware and how does it work in computing?

A malware is a computer term used to identify programs, files and documents that contain malicious data that seek to enter our computers to steal user information. Their name is an acronym for malicious software, and although they are not always complete programs as such, they can cause a lot of havoc.
Although when a person contracts any virus, their body begins to give clear signals that things are not right in the body, with a computer it is different. Many malware work in the background and are almost unnoticeable, since the operation of the computer generally continues normally..
When a hardware or system begins to fail due to malware, it is more than likely too late and the malware has already served its purpose. Thus, the best weapon against them will always be prevention and a correct configuration of the equipment to avoid getting infected.
What are the objectives of malware in our operating system?

The goals of a malware are quite basic. In general, what is sought is to obtain information, rarely does a file with these characteristics have the direct intention of damaging hardware or softwaredespite the fact that many times the methods they use to steal data can cause system-level damage.
Now, why would someone want information about me? That is a question that many ask themselves with more innocence than they should.
The Internet is a gold mine, but also a nest of snakes. A person does not need your bank details to get money from youit is enough to discover a personal secret strong enough to blackmail with it.
Also, you will be surprised to realize how strange some hackers are. This server, for example, fell victim to spyware trying to obtain my account login details for a popular MMORPG gamein such a way that I could enter it and steal all the items and other accessories that I worked so hard to obtain.
A game is an innocent thing, I just had to create a new user account and start from scratch. It was annoying but my life remained completely the same. Very different thing to what it would have been if that malware instead of getting my Metin2 accountI would have discovered some compromising secret (which I don’t have).
Types of malware How are these computer viruses classified?
To say malware is to enter into the more general term of what computer viruses are. There are many of them, so the need arose to segment and classify them according to their size and nature.. Here we present the most important ones.
infectious
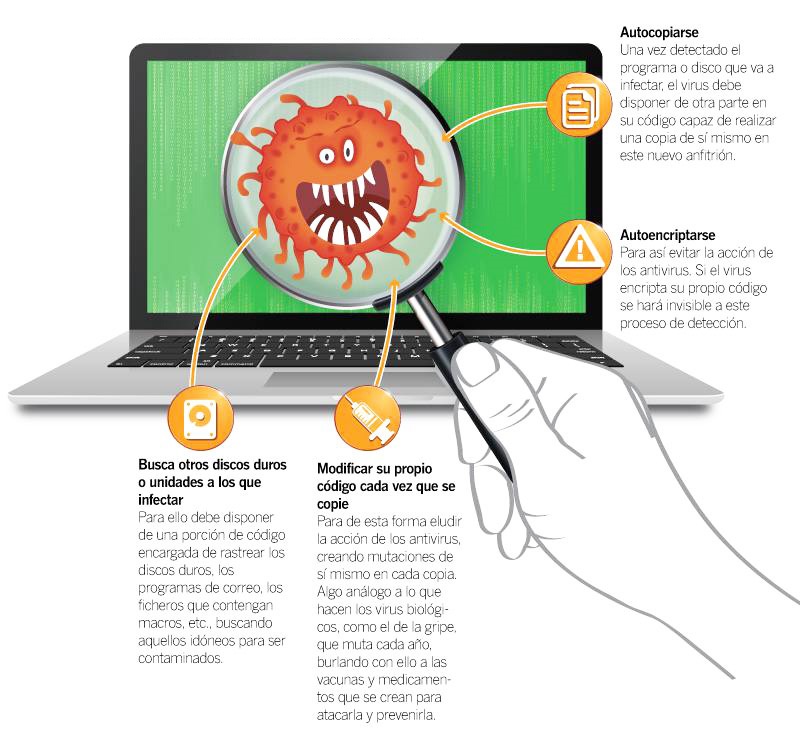
Those programs that have the ability to replicate and infect another program within the same device are classified as infectious malware. These are by far the most risky and powerful as they can undermine the entire system from multiple repeated files and terminal causing logical failure. that even ends up affecting the hardware.
Among the different types of infectious computer viruses, the computer worm is undoubtedly one of the most dangerous. These have the ability to enter our computer through system vulnerabilities, to later multiply and infect the entire system.
The Morris worm is possibly the most remembered computer virus in this category, since in the late 1980s it turned the Internet upside down, spreading throughout almost the entire network and affecting millions of users. The source code of said worm is in a museum.
Hidden
On the other hand, there are hidden malware, which are those that try to enter our system in the most cautious way possible.. These generally detect security vulnerabilities, then sneak in and start making their own.
Although these viruses are easier to control, their risk is much lower than the previous ones. They continue to represent a real threat to the security of users.
In this category we can highlight malware such as:
- Trojan: The Trojan is a malicious program that masquerades as a legitimate one, deceiving our system just as the Trojan horse in Greece did in its time, a story that in turn gives rise to its name.
- Back door: backdoors are malicious programs that seek to enter our system and then create a hidden access door that allows the hacker to remotely access the affected device and monitor it to steal important information.
- Self-downloads: These are viruses that we find on some websites. What these do is that when entering a portal, an unauthorized download is automatically started, which contains spyware.
- Root kit: this is a technique used to hide other malware. What it does is modify the operating system so that it does not show any signs that it is infected and so the virus can continue doing its job without interruption.
for profit
Another category of computer viruses are those that seek to profit from the user they attack, or at least corruptly automate processes to monetize a portal.
In this sense, the most popular are:
- Advertising: These viruses are among the most harmless, since they generally search for less personal data in our system, such as Internet consumption habits or the user’s favorite websites, in order to later sell that information to advertising agencies. Among them we have spyware, adware or hijacking.
- Passwords and important data: In this category we essentially have keylogers, which are malicious programs that can steal information and access credentials to platforms that can range from a video game or social networks, to bank details and the like.
- Dialers: these are programs that use the connection of our internet provider or mobile network to make calls in the background, leaving the line open. Generally, the number they call makes a profit from the call, while the owner of the equipment will unknowingly have to pay the full cost of the call.
- Botnet: A botnet is a synchronized network of computers that is infected with a virus and is used to send massive spam to other users to infect them and expand the network, or simply to carry out more powerful attacks.
- rogueware: These are nothing more than viruses that make the user believe that their computer has a serious virus that can only be removed by a program. But the reality is that this information is false and users end up paying for a program that they did not really need.
Grayware
This is a classification that is given to various computer programs or mobile applications that have the ability to camouflage in the operating system of the day, to later download a series of spyware and other malware in the background.
Who creates these malicious programs? Computer virus writers
Yes, it is a bit difficult to imagine who would be able to invest so much time in the development of a computer program. And the answer is not very difficult. The reality is that there is a guild of people out there who like to make a living as easy as possible..
The development of computer viruses is a very lucrative sector, since the amount of money that can be made in it is quite considerable. Also, with a little imagination you can come up with many ways to make money by stealing private information.
That is why thieves, fraudsters and all kinds of cybercriminals spend months of their lives developing programs that can circumvent the defenses of the most widely used operating systems today (which is not impossible, far from it), to blackmail and sell the data of affected users.
Is there any penalty for them in Spain?
In our country, this decade the penalties against those who use illegal software to enrich themselves have been considerably toughened, sentencing them to prison for several years with high bail to obtain parole. This is happening not only here but throughout the EU, and especially in the United States of America..
The case with LATAM is different and there are not many countries with a clearly determined legal framework against this type of criminal.
How do I know if I have been infected with computer malware? Main signs

Although the most powerful malwares are also the most silent, you can always recognize some signs that one of them is doing something mischievous.
Next, we present the clearest signs that you have to identify if there is indeed one on your computer:
- The computer will go slower. If for some time you have noticed that your hardware is not performing as usual, it is possible that there is some malware in the background taking up too much processing. However, this is usually a bit ambiguous since a virus is not the only reason that can slow down your computer.
- hardware failures. You will find them at first as subtle faults, which will seem to have repaired themselves but over time they will become more recurrent. If the keyboard does not press some keys despite being in good condition, or the mouse pointer is inaccurate, there is possibly a virus that is affecting a driver.
- software bugs. Which can be much more aggressive than the previous point, since they could range from causing unexpected application closures to complete failures of the operating system.
- Unauthorized actions. Windows and tabs open in your browser that you have not authorized or if something hinders your user experience while playing a video game. It is also possible that the home page of the browser changes without you having done so.
- little storage available. You unjustifiably notice that more space on your hard drive is occupied than you remember, because software hosted on your drive has replicated itself too much or is leaving too many residual files.
- screen of death. In Windows, if the system damage is too great, you may start to see the so-called “blue screen of death” very often, which will force you to restart the computer and you will lose everything you are doing at that moment.
- Corrupted antivirus. The clearest sign that you have a malicious program is that the protection against them is deactivated and becomes obsolete, without even being able to update it, which allows the virus to act at will within the OS.
While these symptoms are pretty obvious, just because you don’t have any doesn’t mean you’re clean. There are malware that are very silent, and their goal is simply to collect your data without taking up a lot of storage space or affecting your computer’s performance. Yet they are there, knowing us and hoping to find private information to use against us.
What are the main vulnerabilities used by malware to attack our devices?
Malicious programs by themselves do not have the ability to affect us, so they need to take advantage of some vulnerability in our OS in order to launch their attacks.
In this sense, the vulnerabilities that most enhance malware are:
- Software homogeneity: This refers to the fact that an operating system is used by multiple computers on a network. In this way, if the hacker manages to understand said OS, he will be able to create malware that attacks any computer that contains it.
- software bugs: These are more common than we think, especially when you have outdated programs. A simple bug in one of the files can be exploited by malware to enter it and begin to affect its operation.
- Over-privileged code: All operating systems usually give certain privileges to some programs, allowing them to perform certain tasks without even requiring permission from the user, such as a request to a server. In fact, malware works under this principle, and is programmed as software with more privileges than the rest, meaning that once it enters the system, it can live there freely.
Tips to protect your computer from any computer malware and be sure to be infected
Fortunately for everyone on the internet, computer security has also come a long way, and it is becoming increasingly difficult to develop malicious programs that really represent a threat to the integrity of your computer or information.
Of course, for this you will have to follow the advice that we give you below:
Keep system and software updated
The teams that develop software and operating systems work around the clock to find vulnerabilities before hackers do, so they can fix them before hackers take advantage of them.
For this reason, it is necessary that you always update each and every one of your programs, especially the operating system. Because in these packages is where you will get the most secure version of the software to date.
antivirus and firewall
The antivirus and firewall keep inside a database of all the viruses that exist, so that when one of these enters your system, it is immediately detected and subsequently blocked. This is your computer’s first line of defense, so it’s important to have one installed and updated.
Antiviruses can protect you from all kinds of threats, and although they have many detractors, it is undeniable that they are necessary to keep your system safe.
Avoid making illegal downloads
Yes, we all love free, whether video games, series, movies, and more, but these methods are not always safe, so it is best to always avoid them. Digital hacking is one of the biggest forms of cybercrime that exist, so it is more than likely that those behind these projects have more than one bad habit.
P2P download portals usually contain virus-mined files, since many of these are not verified as there is no quality control on the content, but rather the intention is solely and exclusively to obtain traffic.
ad blockers
Ads and pop-ups from unorthodox websites can be a real threat, as many of them often direct you to download files without your permission or install a plug-in on your browser that further hinders your user experience using it.
Fortunately, you can install an extension on your browser that blocks all ads and any other form of invasive advertising. The best known is Adblock.
Do not install programs of unknown origin
It does not matter if it is on your computer or on your mobile, be very careful with the programs that you install outside of recognized stores such as the Google Play Store, Apple Store or similar, since these may have been modified to hide malicious programs that make yours without even realizing it.
Computing