
Index:
UPDATED ✅ Do you want to know what OSINT is and how this open intelligent research system works? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
At present, it is likely that more than once you have come across the acronym “OSINT” on the Internet and, of course, you will wonder what it is. which basically is a term related to research and is widely used among military groups, government intelligence personnel, and law enforcement.
In this sense, it consists of a very useful system for obtain data or perform some type of inquiry. Therefore, it facilitates the collection and analysis of information publicly exposed on the netto carry out a certain study associated with actionable intelligence.
Then for learn more about this innovative intelligent research system and know what it is forWe invite you to read this post. In which, in addition, we will highlight its advantages and disadvantages, all its phases, its main uses and the best osint tools what’s up.
What is OSINT and what is this intelligent research system for?
Although it is true, the OSINT refers to the acronym for “Open Source Intelligence” which, in Spanish, means “Open Source Intelligence” and is defined as a methodology that consists of taking advantage of the large amount of information available to all public with the aim of transforming it into actionable intelligence. Therefore, it is a deep investigation system developed by the main security and intelligence services. Worldwide.
It is because of that, it is a term associated with knowledge gathered through publicly accessible sources. In this way, it emerges as a solution that offers the possibility of optimizing the decision-making process through the efficient exploitation of numerous information resources. Thus, while increasing the quality of the information, the decisions will be more accurate and will provide better results.
On the other hand, the open sources that are indicated through the OSINT, are defined as any means from which information is obtained that is public and accessible, that is, that it is in the public domain and not encrypted, regardless of whether it is free or has a cost. For what they can be: databases, public libraries on the Internet, traditional search engines, social networks, blogs, forums, newspapers, magazines, etc.
Which are used for the following:
- get documented about a certain topic.
- Speed up the process of an investigation.
- get answers through any search engine like Google or Yahoo, for example.
- Optimize cybersecurity in general terms.
- find an individual specific.
- Follow the trail of operations of a company.
In such a way, if the correct information is achieved, it will be possible to perform a better investigation and draw more accurate conclusions that will influence any decision making. Well, the system OSINT It will allow taking advantage of the enormous flow of information available in open sources, to select those of greatest interest and thus, process or analyze them in order to obtain truly accurate conclusions.
What is open or free source?

An open source is flow of information that is available and everyone has access. Namely, OSINT works based on online posts, chats, blogs, social networks and streaming platforms. But this is not all, open source intelligence also considers printed media such as magazines, newspapers, professional research papers, business data, telephone directories, and any other reports that may be useful in extracting data on people or topics of interest.
What are the advantages and disadvantages of researching on the Internet with this system?
Due to the optimal functioning of this system, it is evident that it supposes different advantages for its users. However, aside from its benefits, this research system also reveals certain drawbacks It is important to keep in mind when using this methodology.
In that sense, first of all, we proceed to specify its most interesting advantages or pros, so far:
- Is about a very useful system for any type of inquirysince it manages to speed up the investigation process remarkably, regardless of its objective.
- reveals remarkable comfort and ease of accesssince the information comes from open sources that can be collected from anywhere.
- It is characterized by being a very profitable methodology, given that it is possible to acquire such information for free, in the vast majority of cases. Which represents an effective cost saving.
- As long as users choose to employ this research system, may have constantly updated data or information. In this way, your conclusions will be more accurate.
- It is a system that involves fewer risks, because it is not necessary for you to carry out field work or travel to another place. Well, it is possible to gather all the data from home, office or office.
- It helps security professionals, notably. Thus allowing them to anticipate conflicts and events in order to design an efficient action plan.
However, just as it guarantees benefits of great interest, the OSINT either “Open Source Intelligence” it also manifests some cons or drawbacks that should not be overlooked.
Next, we mention the most substantial of all:
- In view of the amount of information found on the internet it’s overwhelming, the selection and filtering process may be greatly slowed down. Which will also cause inconveniences to rank the data.
- The fact of gather information on a large scale And power analyze them either visualize them efficiently, may require the use of software licenses or subscriptions that translates into a higher budget. Therefore, the OSINT It will not be completely free in many cases.
- Because it is a methodology based on open sources, this could cast doubt on the reliability of the information collected from there. Since they are sources that accumulate a large amount of untrue information and thus, it will be decisive to learn to distinguish between true and falseas well as knowing how to locate the correct sources.
Phases of the OSINT investigation process How does this open system work?
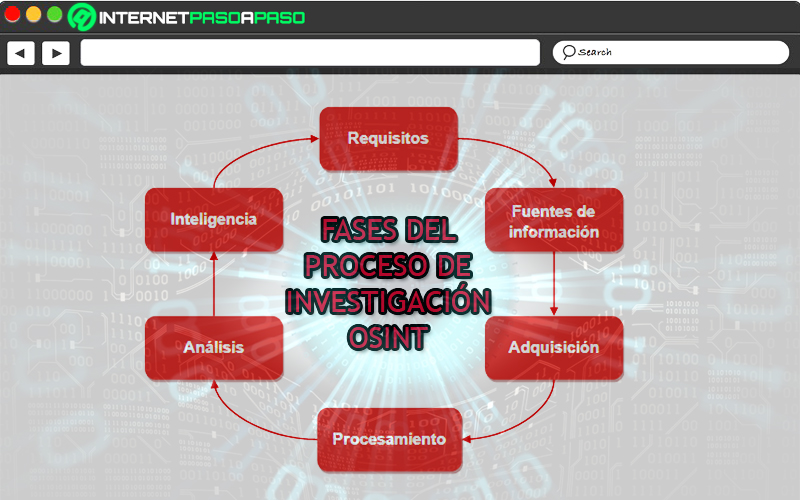
Ultimately, the OSINT refers to a research methodology based on searching for information in open sources that, in general, are hosted on the Internet. But, although it is presumed that all people know how to investigate the network, the truth is that few netizens manage to do it professionally. That is why, to comply with this open investigation system, it is not enough to carry out an inquiry process.
Since, beyond that, it is essential to comply with a series of steps, stages or phases that simplify this process and allow quality results. For this reason, the course of the OSINT investigation It has been structured through a clear and concise procedure that is based on a total of six phases and, once each one of them is applied correctly, the research work will be greatly accelerated.
Next, we will explain each of these phases:
Set goals and set requirements
It is the first stage of the research process, which is based on define all the requirements that must be met throughout the exploration. Therefore, you must establish each of the conditions that have to be satisfied to meet the goal or solve the problem at hand, as well as Specify what the information to be found is going to be used for and what type it will be.
Identify the most important sources of information
Next, you will have to carry out a study based on each and every one of the open sources of information that can provide more data or information for your investigation. In this way, you must specify the sources of interest that will be collected, through the requirements established at the outset. This, will help simplify and streamline the procurement process.
Acquisition of the information to study
It’s about the third phase of the OSINT investigation process, in which the information will be gathered through the indicated sources. Therefore, it is defined as one of the most important pillars of the entire procedure, since you must collect and study those web pages, newspapers, magazines, books or documents located during the second stage.
Processing of collected data
Once all the raw information is collected, it is time to start the fourth phase of the procedure, which is based on processing each of the data collected. This basically It consists of formatting the information collected so that it can later enter the analysis period..
Analysis of processed information
After processing all the collected data, it is time to start the fifth phase of the process. which is the one in which intelligence is generated through the information collected and processed. Thus, its main objective is to relate or link information from various sources to look for patterns that allow to obtain some relevant conclusion. Thus, this analysis offers the possibility of prioritize the levels of importance of the information acquired.
intelligence presentation
Finally, it is opportune to start the presentation phase that consists of teaching the collected information in a potentially useful and understandable way so that it can be exploited in the most optimal way. This means that, it will be decisive to give a format to the information investigated so that it is interpretable and practical to conclude the investigation and obtain timely conclusions.
Uses of OSINT What applications can be given to this technology?

It is no secret to anyone that the new technology OSINT It is ideal to carry out any investigation more efficiently, quickly and concisely. But, even so, it is still not totally clear what applications can be given to this methodology today and that is why we clarify that refers to a system that has a great relationship with several sectors, such as: security, marketing and journalism, mainly.
However, to point out its applications more specifically, below we mention the main uses of “Open Source Intelligence”:
- Identify, study and prevent the possible threats that exist in the military field or with respect to the national security of any country.
- Perform a search or follow to a certain individual who is responsible for certain irregular actions.
- Evaluate the level of privacy and security of a company or organization, since it allows audits to be carried out in these environments.
- Do analysis before launching a marketing campaign.
- Study market trends in terms of marketing or commerce.
- Know the online reputation of a company, brand or user.
- Make an appropriate one journalistic documentation.
- carry out studies psychological, sociological and linguistic.
- in a negative wayis also used to launch APT and Phishing attacksby cyber criminals.
List of the best OSINT investigation tools you should know about
Given that the flow of information obtained during the OSINT investigation process can be extremely large, it is necessary that the users of this methodology choose to rely on certain tools or services that are useful when implementing a system of this type. Otherwise, the difficulty to execute and finish it will be much greater.
That is why, in order to provide you with much more utility and offer you excellent solutions to carry out an OSINT investigation at a professional level, here we present some of the best tools that are recommended to be implemented during said processes:
Study keywords with “Newspaper Map”
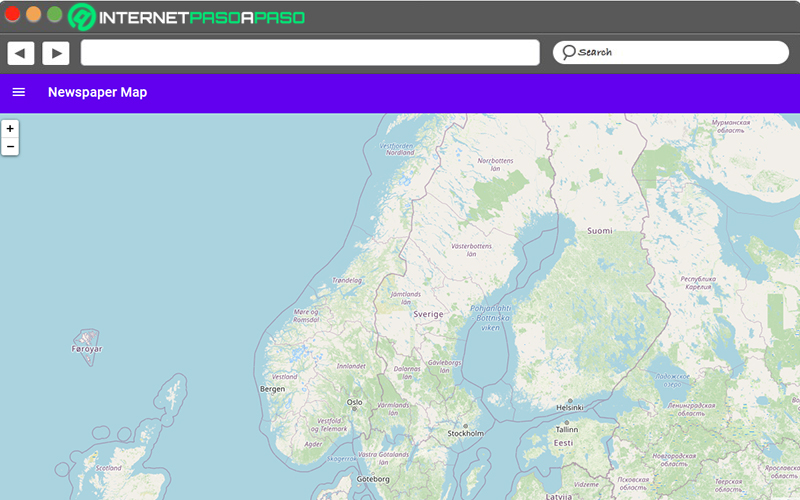
A very helpful object to collect information about a specific inquiry, is to make use of certain keywords. But for this you need know the language and lunfardo specificallybecause many words change depending on the region.
In that sense, it is recommended to use a website called “Newspaper Map” Newspapermap.com which consists of a page that hosts the local newspapers of different cities and/or regions around the world. which can be quite useful for define keywords through news in local newspapers.
Generate identities with “Fake Name Generator”
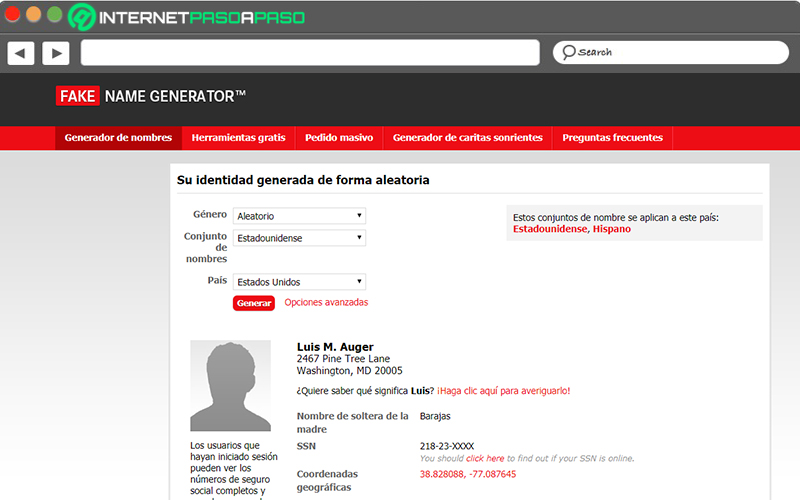
Although it is true, when conducting a thorough investigation, it is recommended make use of a false identity so as not to have future problems (of any kind) because of it and, of course, to protect your real name. But, for this, it is not necessary to use the real data of another person, since it would be indicated as a crime of identity theft.
In this sense, to protect your identity without damaging the name of another individual and still carry out an exhaustive investigation, it is advisable to use an online application such as “Fake Name Generator” es.fakenamegenerator.com which enables create the data of a fake individual, for free and easily. Also, to use a photo of someone who doesn’t exist, we recommend using the app “This person does not exist” It works with artificial intelligence.
Search posts by location with “Geo Social Footprint”
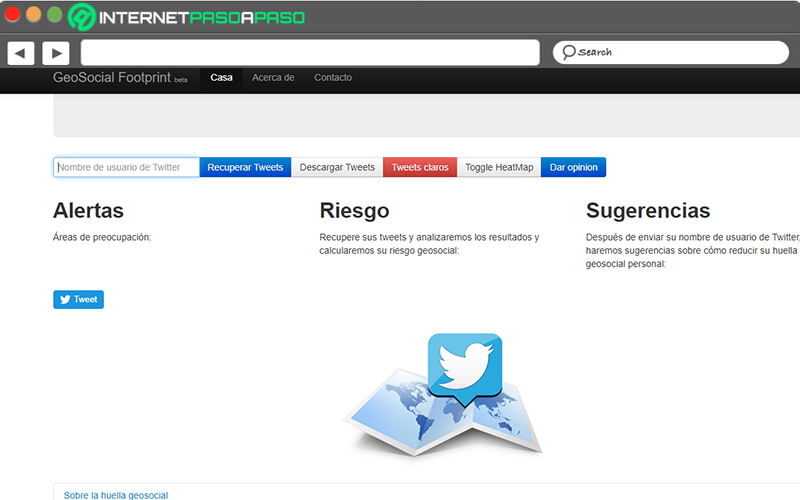
If you need to focus your research on social networks or, specifically on Twitter, we recommend you to use this tool. which is known as “GeoSocial Footprint” and facilitates the search for news or posts on Twitter from a certain location. In this way, it is a very useful tool that, luckily, it is free and reliable. Taking into account that, supports the location that all those posts or comments that are uploaded to the Internet and that, by default, keep georeferenced.
Use additional search engines like “Shodan”
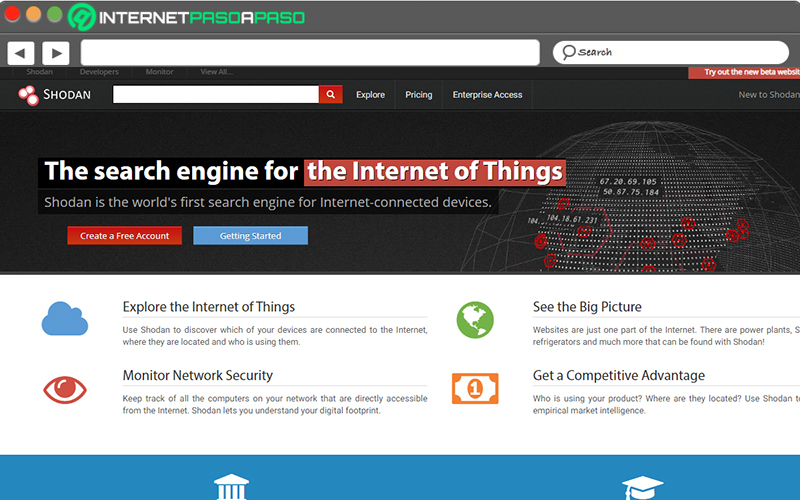
It is no secret to anyone that one of the main open sources of information refer to internet search engines. Since, by its very nature, These systems host all the information that is handled on the network. and thus, it facilitates the search of various data.
But, beyond the recognized Internet search engines, such as the Google search engine, yahoo either bing, There are other solutions of interest. In this case, It’s about “Shodan” shodan.io which is cataloged as an ideal tool for search for ports or services published to the Internet, including those that are geolocated.
Use virtual machines with own OSINT tools such as “Intel Techniques”
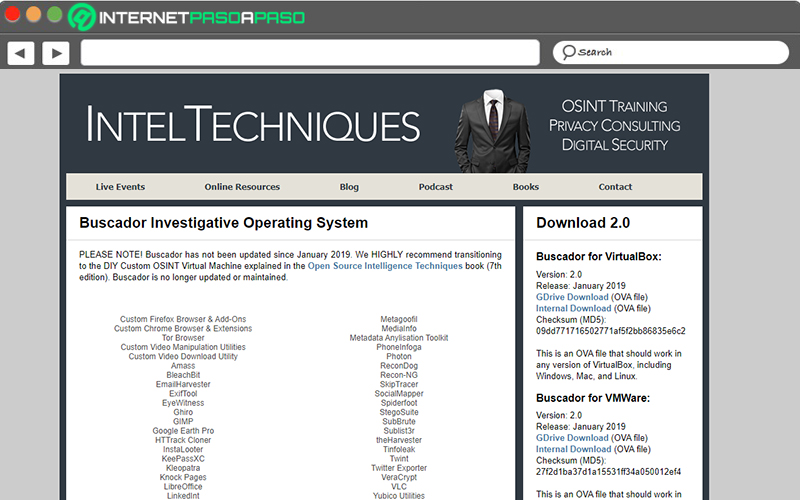
Today, there are several solutions that have various tools to carry out investigation processes of the type OSINT easily and so obtain conclusions of high quality and reliability to make truly optimal decision making. One of the most famous machines of this type, this is kali linux.
However, there are other virtual machines that host different security tools. OSINT and one of the best out there is known as “Intel Techniques” inteltechniques.com which is defined as a Linux preconfigured and virtualized contains more than 25 tools ideal for running searches and intelligence on open sourcesas well as to conduct research in general terms.
Specify identity documents or employment data on government websites
Despite the fact that many people, until now, do not have bank accounts, credit cards or profiles on the different social portals, the truth is that some relevant information can be found about them By other means. In this sense, it is recommended access government web pages from where they can be easily located.
In this way, depending on the country or region where the investigation is being carried out, you can choose to access a platform of this type to locate certain people through their identity document, social security, utility bills, tax registrations or even traffic violations.
Legal Framework Can we use OSINT to work with justice?
You must keep in mind that OSINT is different from the evidence that you can present in court. As intelligence cannot be offered as a type of evidence because it is not considered evidence in the Procedural Code.
Therefore, for what OSINT is taken into account will have to submit to forensic standards to be admitted, which does not happen very often. But this does not imply that you cannot use OSINT to work with justice and so you achieve obtain evidence that evidences some act which will then be subjected to technical expertise.
Informatic security