
Index:
UPDATED ✅ Do you want to know the tricks to get the most out of Tor Browser? ⭐ ENTER HERE ⭐ and find out what they are ✅ EASY and FAST ✅
Tor has become the emblem of browsers that can more efficiently keep our data hidden during the time we surf the Internet.
There is a lot of information (some true, some not so much) about this browserwhich is closely related to the deep web. If we need to stay hidden, we will have to meet certain requirements since the browser alone cannot do its job with 100% deficiency.
In this report we will bring you all the facts and truths you need to know about Tor, We will teach you the best tricks with which you can navigate without any inconvenience keeping you at all times hidden from others. We will also talk about Javascript and why we have to disable it.
Why doesn’t Tor Browser disable cookies? Does it affect my privacy?
Tor Browser only works with session cookiesand permanent cookies type “As far as I know” (AFAIK) they are considered session.
In principle, our security would not be so much in danger according to this system, but as there are other factors that also determine the level of privacy, not only, it is recommended delete cookies and verify that self-destructing cookies do not really exist at the time of closing a session.
If we want to remove session cookies before start again in Torwe will have to modify the configuration.
To do this, we are going to go to the drawing of the onion and select “new identity“, in this way we can access again as if it were the first time we entered.
How to disable JavaScript in Tor Browser for even more security?
In order to disable JavaScript, we will have to follow these steps:
- We start the software.
- In the address bar, select the icon “yes“, which corresponds to noscript
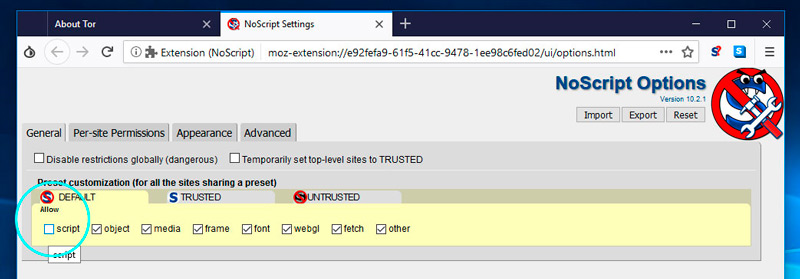
- We click on “Option“
- We seek “General“
- Click on “script“
- We choose “Predetermined“
There is another way which is to use the tool “javascript switcher” which we will add to the browser and will help us to enable or disable JavaScript.
We will do this procedure:
- We install “javascript switcher“
- We click on “Menu“
- We select “add-ons“
- We write in the search bar “javascript switcher“
- We choose the first option
- We click on “Add to Firefox“
- We select “Add“
There is a third way to disable javascript and it is through a manual procedure directly in Tor.
To be able to do this step we will perform the following procedure:
- In the address bar we write “about:config“
- We select “I accept the risk!”
- We write on the bar “enabled“
- And we activate through “Fake“
List of the best 15 tricks and tips to get the most out of Tor Browser

The following are the best tricks you can find about the browser, with them you will become an expert in hidden browsing:
Anonymity to browse
The main meaning, or rather, the essential characteristic that Tor Browser it is precisely not expose our data to the members of the Internet network through autonomy and security protocols.
For it, we will need to work with different data than what we frequently use on other Internet sites. We may use temporary emails and any aliases that we do not use on other sites. We also cannot use the alias we have on Tor in other non-secure browsers.
cryptocurrencies
It is advisable do not use real coins when you want to do operations but this kind of virtual currencies to maintain our anonymity.
Banks or financial entities
Something that is too logical, but necessary to recommend, is that if we want to continue browsing without knowing our data, we cannot interact with banks or any official body that has the same characteristics, since they will ask us to identify ourselves and it will lose meaning. to navigate in Tor.
Tor Security
It is said that this browser it is as secure as any VPNbut being a browser it also works with Script, that is, it makes it a reliable tool in terms of security, but with some limitations if we don’t pay attention to some details.
The problem arises when our operating system is not up to date, so it becomes vulnerable to the entry of intruders. When we navigate in a vulnerable operating system, Tor cannot fulfill the function that we ask of it, which is to maintain our 100% privacy.
Navigation time
Although when we access the browser, our IP change for one that is surely thousands of kilometers from our location, thus obtaining great peace of mind in not identifying our equipment, we should not abuse this situation.
It has been verified that when browsing from the same computer, to the same web pages, or close to the same location with the same device, they have been able to determine the real origin of the computer and the identity of the user.
Social networks
Justly the point of browsing through Tor is not to identify ourselvesif we need to enter one of our social networks, Tor cannot do its job because yes or yes we will have to register.
Use of browsers
Both the Deep Web and the traditional Internet provide us with different browsers that keep our real identification hidden. If we use a different kind of browser, whatever it is, for example, Chrome or Internet Explorer (and we have to redirect to another site)it will not make sense to browse Tor, because these browsers through their cookies can easily identify us.
Embed Raspberry Pi with Tor Browser
We can install a router, that is, at the Internet access door a “raspberry pi“, so that once we have downloaded Tor we can pass all the data packets through the Raspberry Pi and thus remain hidden.
To configure Raspberry Pi:
- We open the command line of Raspberry Pi
- We wrote
sudo apt-get update - To accept
- Then we write
sudo apt-get install iptables-persistent git - To accept
- We select “And it is“
- To accept
Once we have already configured Raspberry Pi, we would have to convert it into the access door, for this we will need this Script:
- We wrote
git clone https://github.com/unixabg/RPI-Wireless-Hotspot.git - To accept
- Later
sudo ./install - To accept
- We follow the configuration instructions
We already have Raspberry Pi configured as a. of access, what we need now is to install Tor.
We will do these steps:
- We wrote
sudo apt-get install tor - Play
sudo nano /etc/tor/torrc - And we select
Ctrl + X
Finally, we would have to tell the router what traffic we are going to send to the Internet through the Tor software
Update Tor Browser
It is necessary to have the browser permanently updated, since with this we will prevent our real IP from being detected through leaks that can often be caused by vulnerabilities in other computers.
Windows
We recommend not to use Tor with Windows operating systems, the weaknesses that the operating system presents in the library that is based on the templates to make C++ (TBB) have the highest points which can be hacked.
Remove JavaScript, Java and Flash
It is recommended to disable these programs, since they do not maintain a certain level of privacy that we are requiring. If any web page uses any of these programs, we recommend not opening its URL.
use linux
To increase the efficiency of Tor it is recommended to work through the Linux operating system, programming it in such a way that it is compatible with the latest versions of Tor. Also, we will have to take into account adding Privoxy which will work very well as a proxy and choose tails either Whonix.
Delete cookies
It is advisable to delete all cookies permanently, since there could be a gateway to the vulnerability of our computer through TBB or Tails (with which we recommend working). Included in these classes of cookies are not only self-destructive cookies but also session cookies.
Mobile phone
In order to maintain absolute privacy, we recommend not having our mobile phone in the same place that we are accessing through Tor, this simply means that, If we want not to be identified, many times they can identify us through our phone that have applications for this purpose.
storage units
So that Tor can do its job efficiently and thus be able to have our privacy highly guarded, we will also need the storage units to be encrypted by configuring them through Linux.
How can I download Tor?
We have already explained the different characteristics of the tor browserNow you just need to be able to download it. Through the following links, you can get it for Windows or MacOS, it depends on your operating system:
Download Tor Browser Windows
Download Tor Browser macOS
browsers