
Index:
UPDATED ✅ Do you want to know which are the best VPN servers to surf the Internet anonymously? ⭐ ENTER HERE ⭐ and discover the types ✅ EASY and FAST ✅
Security and anonymity are two highly desirable features in our connections. For this reason, the VPN or virtual private network is a service that is accessed more and more.
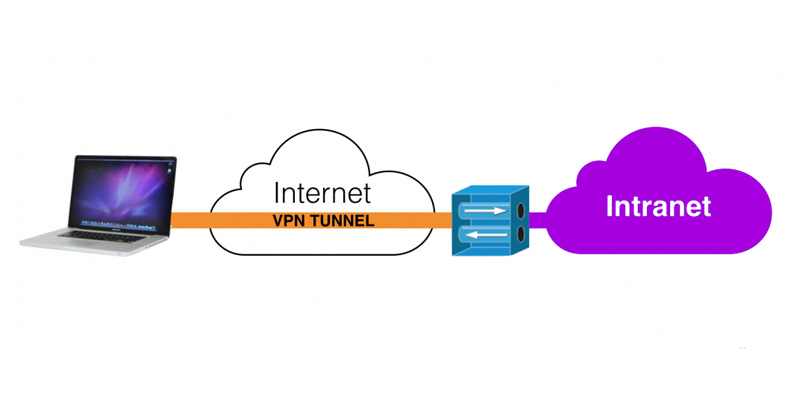
Is it is a network that masks our IP address while giving us great security through encryption of information, becoming a direct access tunnel to our destination.
Of course, in this post we are going to tell you in detail what does it consist of and how it works, as well as letting you know, of course, what are their advantages and disadvantages, the types that exist, the uses we can give them, we teach you how to configure your own network and, of course, we give you our recommendations so you can try some of these free services and get to know better, and in practice, what a virtual private network consists of.
What is a VPN network and how does it work?
vpn are the acronyms, in English, of the concept “virtual private network“. This refers to a computer network technology whose main characteristic is to serve as a secure extension to a LAN that is on another uncontrolled network.
In this way, a computer that is connected to this network will be able to send and receive information over other networks, whether public or shared, in the same way as if it were part of a private networkincluding its management policies, its security and its functionality.
For this to happen, you must make a virtual point-to-point connection using encryption and/or dedicated connections.
Of course we can get that Multiple devices connect to each other within the same network without the need for cables, which enables their communication and the exchange of information with security and privacy.
To be able to create, configure and use a VPN you need, at least, the following:
- Possibility of user verification. This prevents access to unauthorized persons. Thus, an unsuspecting user will not be able to enter a company virtual private network, someone who has not paid a fee will not be able to access a paid one, etc.
- Access control. Likewise, specific access to some or other places and data must be given.
- Activity Register. The network provider will have a record of the use of this by time, users and use of it.
- Data encryption method. There must be a way in which the information is encrypted to be transmitted with the certainty of not being able to be interpreted if intercepted. To do this, it works with certain encryption algorithms such as 3DES or AES. With them it is achieved that the data is only read by the final sender and receiver.
- Data Integration. We must make it possible for these not to be modified during their entire trip.
- Introduction of the SEAL security algorithm.
- Key update. The encryption must be updated continuously, and there is an efficient and gentle key management system.
- undeniable signature. The messages are signed and this fact cannot be denied.
The operation of this resource is quite simple. Conventionally, to access any page you contact your IPS, that is, with the internet provider with which you have the contracted connection. It is this one that, through its servers, attends to your demands and launches them where it corresponds. This assumes that, obviously, you are seen by him.
When you use a virtual private network, what happens is that ryou make a call to a VPN server, whose connection is encrypted. Thus, it is achieved that your ISP does not see the data that is sent by you; in their eyes, it is the VPN server that is asking for access to the sites, not you. It is something like a mask that we put on so that he can stand up for us.
Obviously, we must not forget that the masks are supported by thin rubber bands and, therefore, It is not that we are invisible or anonymouswe simply have one more layer to cover ourselves with.
Why use a VPN server and what advantages does it have?
A IP adress It is a number that is assigned to the devices that connect to a network in order to identify them. This feature makes them very dangerous, because anyone with access to that information could find out personal data from any of us.
For this reason, using a VPN should become a priority for any Internet user today, since the benefits they do not provide are obvious:
- you can evade the geographic internet censorshipsince we can choose a server hosted in the country we want.
- They hide your IP address in such a way that no one can decipher it to obtain information from it without your authorization.
- protects you from risks of using public WiFi networks since all the traffic that passes through your device will be secured.
- It will be easy for you to avoid bandwidth limitations that telephone companies use to insist you purchase more expensive plans.
- you avoid the firewall blocks or firewalls since being your encrypted IP these will not apply as easily.
- Tea protects from the risks of downloading content via P2Pespecially when it comes to pirated content as no one will be able to know your internet protocol address.
- Using a VPN can also improve your experience playing online since by circumventing geographic blocks you will be able to access exclusive content from certain countries.
What are the advantages and disadvantages of using a Virtual Private Network when browsing the Internet and changing your IP?
A priori, we see that this resource is very interesting. And, indeed, it is. However, before continuing, it would be better to know, point by point, its good things and its bad things, so that everything is very clear to us and we can consider hiring and using it without having any doubts about what we are going to obtain and what we expose ourselves Let’s see it.
Benefits and advantages
Of course, enjoying this service has many good things:
- Compatible with any application. All internet traffic is routed, which makes the VPN connection possible in any application.
- simple connection. You only have to set up the connection once, and after that, you can connect and disconnect at will without any difficulty. In addition, you can do it from different devices and from different places.
- More security. Security increases, allowing us to send information privately, hide our identification data (IP, location), not be so exposed when we connect to public networks, etc.
- location spoof. This allows, in addition to not being associated with a specific place, that we access places banned in the place we are or, simply, to resources available in other locations.
- Activity Hiding. With a VPN, the internet provider will no longer know what you do with their service. However, do not forget that the VPN manager does.
- Economic. Virtual private networks are cheaper than other resources that are used to satisfy some of the same needs that we work on in this case.
Risks and disadvantages
On the other hand, we also find some negative aspects that must be considered:
- User Tracking. There are services that track the user to obtain information to design their usage and browsing statistics; These are generally the free ones. watch this aspect if you do not want your activity to serve to make your consumption habits known on the network, although nobody is going to point it out to you directly, of course.
- connection slowdown. It is a direct consequence of data encryption.
- Misrepresentation of inappropriate information. The location cannot always be faked. This is much more difficult if you connect from your mobile phone, since it is on the move and connects to various networks, storing that information without you even knowing it.
- transferable security. We find one more layer of security, but it is not impenetrable.
What is a VPN network for and what uses does it really have?
We have already seen what it is for, at a general level. However, its operation can be useful in very different tasks, which makes this a resource used by users with very diverse needs. Let’s see the clearest utilities that are given.
Restricted content consumption
The VPN will serve you to consume all kinds of content that, in one way or another, you have been restricted. We talk about what is not available, for various reasons, in your countryas was Netflix years ago in Spain or as is the case with Facebook in China today.
In this way, if you cannot enjoy them in the place where you are, you falsify your address to make believe that you are in another place where you do have access to these.
I would also enter here I dodge the restrictions placed on us by special circumstanceseither the ISP itself or lower echelons (for example, library computers that do not allow access to video viewing websites so as not to consume all the bandwidth). With the VPN the data is encrypted, so it is not known which sites you are accessing.
Use of P2P networks
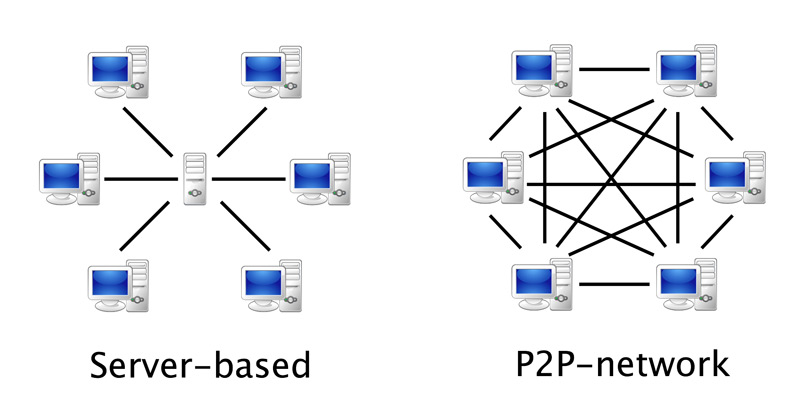
The P2P downloads They are not always simple, and that is due, in large part, to the boycott by Internet providers, which block or, at the very least, make it difficult for you to download content.
Why? Well, first of all, you are generating a lot of traffic, and although its limits are practically incalculable, the truth is that they multiply the bandwidth of thousands and thousands of clients, meaning that, in the end, this can be reduced.
On the other hand, there is, of course, the fact that any of your downloads is illegal. Nothing happens to anyone, it is assumed, but in case you were investigated for it, your supplier would be consequently harassed by the authorities.
For both reasons, what is done is block browsing certain sites, the download of torrents, their management software, etc. or slow down navigation and use so much that we ourselves are the ones who give up and stop downloading in the P2P networks.
Tasks with sensitive information
This is not always the case, but what is common and what is increasingly being offered to be competitive is data packet encryption. With this you can make use of sensitive informationsuch as your bank access data, from an unprotected network without these being exposed.
Telecommuting
telecommuting with unencrypted connections it is highly insecure; you would be connecting to the company network from an open network or, at most, a home network, easily hackable.
with this resource encrypt the connection and, at the same time, enjoy the same information that you have at your workplacein the work network.
Types of VPN networks that exist and how they differ
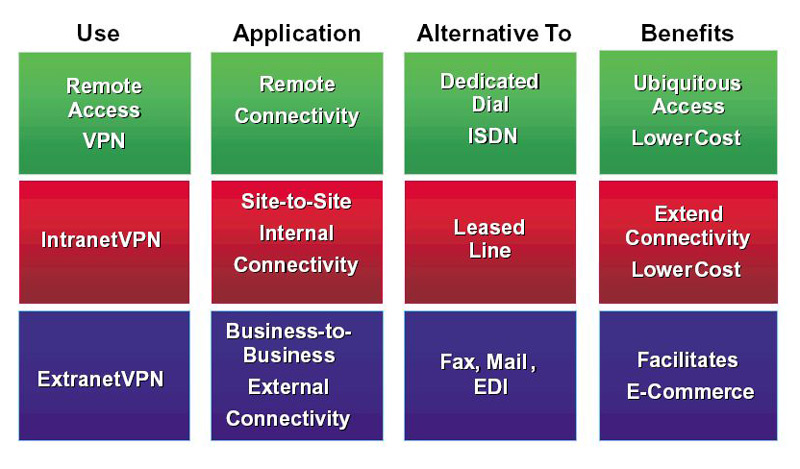
As you can imagine there are many types of VPN networks, this resource can be offered in multiple ways, although the essence is always the same. Thus, we can make different classifications of this depending on its base, its architecture or the connection used.
according to architecture
The VPN architectures that we can find in which a private connection is offered are the following:
remote access
The users authenticate to connect remotely where appropriate, accessing in a similar way to what would happen in the local network itself. With the remote access VPN dial-up infrastructures are replaced that have been used for so many years and that are based on telephone lines and modems.
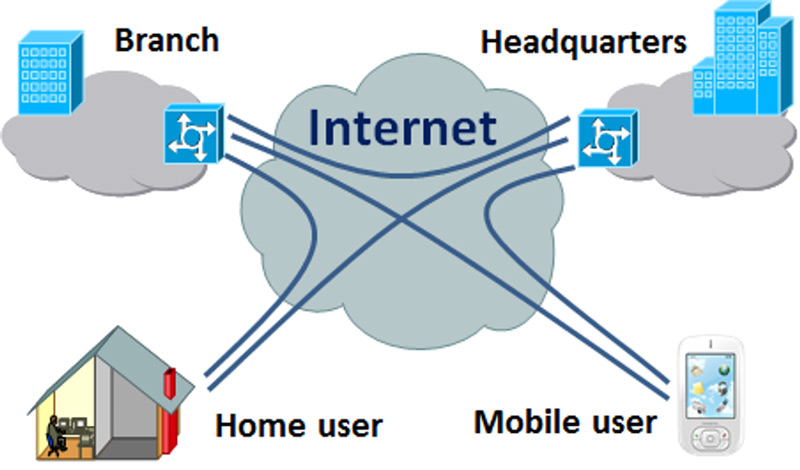
Point by point
The server is permanently linked to the internet, being able to accept connections remote offices coming from authorized sites (remote offices) to connect with a headquarters. Each branch server is connected through the services of a local internet providerso that the expense of traditional point-to-point wiring is reduced.
tunneling
with this technique network protocols are encapsulated over each other, creating what is defined as “network tunnel”, a tunnel appeared in a computer network. To do this, a protocol data unit or PDU is required to go inside another encapsulated PDU.
With this method we get a routing of the given data packets over a set of intermediate nodes, which cannot fully know the content of these. The tunnel created is defined by the two ends. The communication protocol used is SSH, which ensures the encryption of information.
Over-LAN
It is similar to VPN with remote access, with the exception of use the local nerve center network instead of the internet to make the connections. With the over LAN we can isolate both services and areas of the internal network, which represents an improvement in the security that we can offer with the use of wireless networks.
depending on what they are based on
On the other hand, it would not be superfluous to indicate that we can also make a classification according to what the VPSs are based on.
In this case we would find those that are based on the client and those that are based on the network:
Customer based
The user connects to a remote network using an application, requiring user information and password. A) Yes, a computer-network channel is created that will be encrypted and that will serve to perform a secure data exchange.
web based
one is allowed connection between different networks using the Internet.
Depending on your connection types
And since we are talking about connection, we cannot continue without mentioning the types that also exist in relation to this resource:
remote access
A user connects, with a computer, to a private network. The packets are originated by the remote access client, who must authenticate against the server dedicated to working for him in said network, and vice versa.
router to router
The connection is made by router and it is this element connecting to the private network. In this case, the connection is characterized by the packages that are sent are not going to originate in these devices; these are only authenticated when making and answering calls of connection.
firewall to firewall
A firewall establishes the connection and connects to a private network. The data packets that are sent can come given by any user who is using the Internet at that moment. Authentication occurs between a calling and responding firewall..
In mobile environments
It happens if the point at which the VPN should terminate is not fixed to a single IP addressbut it moves between several.
They are ideal when you want to keep the session, something that is increasingly in demand today, which means that you are working hard on this aspect to get a resource reliable.
How to create and configure your own VPN server? Quick connection guide
We have already seen that a VPN connection is a way to connect to a virtual private network, using the Internet for this, so that it is not necessary for the computers to be interconnected with each other. For this reason, many people decide to create own server with VPN.
This is not too complicated so, of course, next we are going to see a small tutorial to do it ourselves, yes, differentiating some operating systems from others.
On iPhone and iPad with iOS
If you are interested use a VPN on your own iPhone or iPad tablet. You will be able to connect to your work just by having a battery and a good connection. This will allow you to carry out small tasks without the need to use a computer, which is becoming more and more popular.
- For iPhones and iPads running iOS, VPN apps come with a configuration profile right out of the box. Therefore, just by entering the “System settings” a profile can be set up automatically.
- Once you are in the “Settings” section, go to the “General“.
- Inside it, access “vpn“.
- From this menu you will start create a new VPN connection by entering the data of the service provider and the type of access to said connection.
- When everything is complete, click on the “Save“.
- Test the operation of the connection, which, if everything went well, should be perfect.
On Android smartphone
In the case of devices that run the Android operating system, the procedure to follow is extremely simple, since the OS itself has its own VPN client for Android.
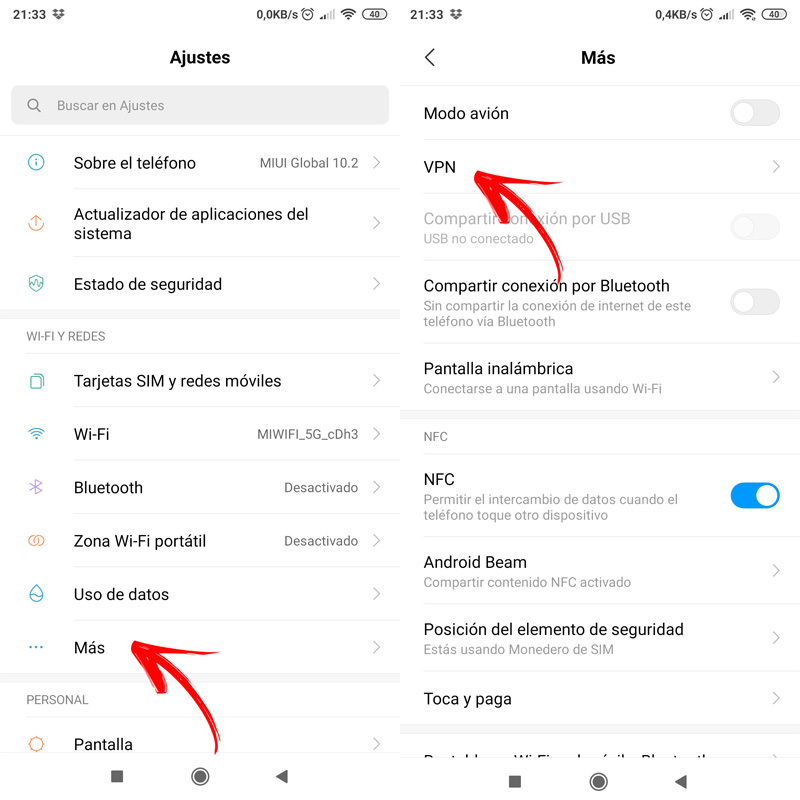
- You must enter “Settings“.
- Go to “Wireless and Networks“.
- Now to “Plus” or “Others“.
- Then click on “VPN“.
- Select the option “Add New VPN” or just “+”.
- fill on behalf of the connection and the type that interests you. My recommendation is that you put PPTP.
- Then fill in the details of the server host.
- Click on “Save“.
- Now you can try to access the VPN to check that it is correctly configured. This will appear along with the other WiFi networks you have listed.
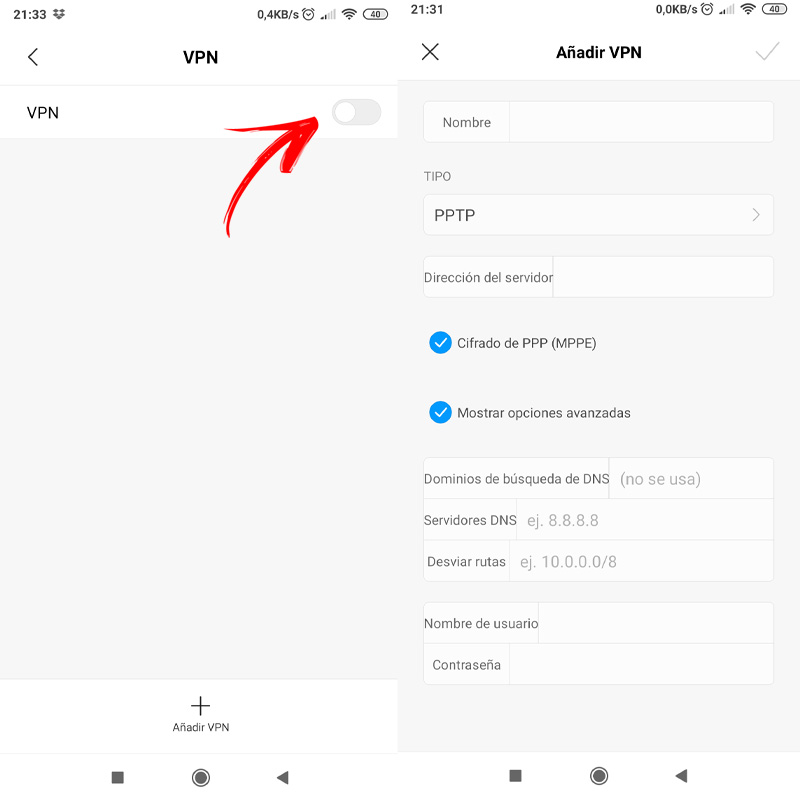
Another option is make use of a third-party applicationthat there are and that they have no more mystery than being downloaded from the Play Store, installed and configured.
On Windows 10
Windows 10 has made it easy to set up a VPN serverso that, following a few simple steps, it can be achieved without having great knowledge.
- Initially, we must know these dates:
- IP adress of the VPN server.
- Service provider VPN. We recommend using a free service before hiring a premium service, at least until you know how this resource works.
- Login name and username and passwordto of the VPN account.
- Then you must login with admin account on Windows 10.
- Go to section “Network and Internet“.
- Access the “System configuration“.
- Click on the button “Add a VPN connection“.
- Now is the time to enter all information that we have initially obtained: provider, name of the connection, IP address, type of VPN (we recommend selecting PPTP because it is the most used) and the type of login (the best option is to enter a username and password).
- With the connection created, you must access it to check that it has been done correctly and that it can be accessed easily through WiFi.
For Mac computers
set up a VPN network on a Mac computer if you are not used to handling it, it is not as intuitive as in the case of the Windows operating system. Therefore, our recommendation is to follow the steps below to do it correctly.
- First of all, you should go to the “Launch Pad”.
- From there, go to the “System preferences“.
- Within it, you must choose the category “Net“.
- Then a window opens with the parameters to fill for the VPN connection to become effective.
- Within this screen, we go to the bottom left and click on the “+“.
- In the new window that opens, we mark the option “vpn“.
- It is at that moment when We choose the type of VPN network that will be created.
- Next, data is filled initially provided to us.
- Once this is done, click on the “Connect“. If everything has gone well, the connection will be effective without any problem from that very moment.
on linux
Although we all believe that the Linux operating system is very complex, in this case we are facing a very simple connection tutorial. The steps below can be used for any OS distribution and the options will have the same meaning between them.
- First of all, open the terminal and execute the command “$ sudo apt-get install network-manager-vpnc“. In this way, we will get a necessary package.
- We open the menu “networks“.
- Within it, we choose “VPN connections“.
- Here, we give the option of “Set up a new VPN“.
- Click on the button “Add“, “Add” or “Import”.
- Next:
- Click on “Import saved VPN configuration“. Extract and import the file with your VPN information.
- Or, if you don’t have any yet, simply fill in the data after clicking on the “To create“.
- In the “Advanced Settings” tab, select “TTLS authentication“.
- Once the data is already registered, you must click on “okay” and a VPN connection could already be created.
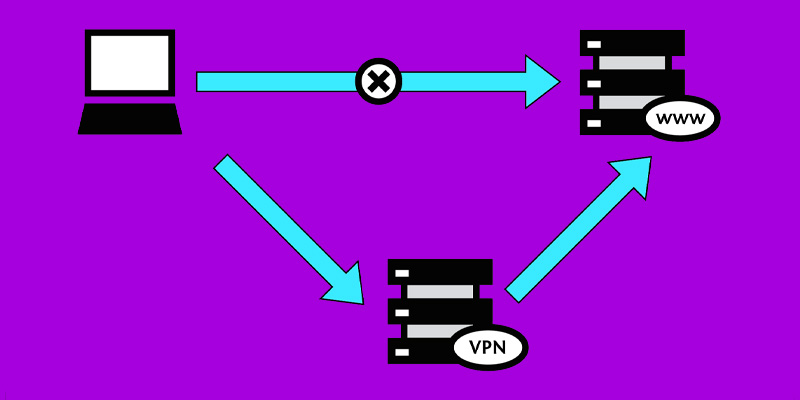
What are the differences between a VPN and a Proxy?

These terms are often confused because both can mask our IP. However, we have to say that this is the only function of the proxy; this, unlike the virtual private network, it does not encrypt the information or provide security of any kind, he only makes requests on our behalf.
It should also be noted that there is a big difference in terms of application compatibility. While the proxy would only be used in browsers and a few applications previously chosen capable of configuring an advanced connection, virtual private network offers compatibility with any type of software by being able to route all traffic.
What are the differences between APN and VPN networks?
Although the concept looks similar in its acronym, it has nothing to do with the one we are dealing with today. An APN is an access point (access pont name) used to be able to connect to a network in any operator. Typically, this point consists of a username and password that must be Introduce.
This point occurs between an existing interface between a particular networkfor example, a mobile network, and the general network from Internet. Its configuration usually occurs automatically, although, if not, the manual option may be required.
VPN we have already seen that it is a network mounted on another network. is not a point and its assembly occurs, generally, between device and server.
We can make a comparison to say that an APN is like a door and a VPN is like a corridor, but they are not related at all, one does not lead to the other. The only thing in common is that they require verification for the user in question to have access, but the resources themselves are two totally different things.
Characteristics that you should take into account before hiring or using a free or paid VPN
Of course, we have to take into account some aspects. Some will be decisive, others will simply add value. Be that as it may, we will have to consider them to choose the service that best suits what we need.
Let’s start by checking if the VPNs we are considering have a registry with which we relate an IP and an identifying mark of its users. It is necessary to see what is the exact information of which there is a record.
It is interesting, too, know the tools with which monitoring is carried out from service. In many cases, it may also be important relationship with external providers: If they work directly with some, with all of them, what is the process if a DMCA-type request is received…
For many stakeholders, exchanging files between servers is the main reason to get a VPN, so it is necessary to know what forms of file traffic exist.
If you make use of a payment service, surely you are also interested in knowing if, with the payment method, you can get to know the identity of the user.
List of the 5 best free VPN connection services to browse the WWW privately

Considering aspects such as whether data is recorded, how and for how long, monitoring tools, the use of external providers or the reaction of the VPN to certain circumstances, we have been able to create a top of best vpn connection services that are freeso that you can try them without having to marry anyone.
ProtonVPN
Some features:
- You can also get a version of 8 euros per month and another of 24.
Advantage:
- The entire system is internal, not having to use parts from anyone outside the corporation, which is a plus of security.
- There is P2P traffic without limitation.
- Its headquarters in Switzerland gives us extra security in terms of privacy.
drawbacks:
- There is a monitoring of the timestamp of the last successful connection attempt, although it is later overwritten.
- You can connect simultaneously on only 2 devices.
TunnelBear
Some features:
- Although it is free, there is a Premium version that costs 5 dollars (and up), with its corresponding improvements.
- It is compatible with Windows and macOS as well as Android and iOS.
Advantage:
- It can be used on up to 5 devices.
- It is very popular for its good speed, which, in the best case, reaches 12 MB per second.
- Vigilant Mode is ideal to be safe in our connections to public networks, as it blocks all kinds of suspicious content.
- It has a very simple installation, as well as its interface, so it is an ideal option for those who do not pilot much.
drawbacks:
- As a limitation, to consider, we have that their servers work only from Germany, Canada, the United States, France, Japan and the United Kingdom as well as from Australia with the paid version.
- The data limit is 500 MB, although you have the option to tweet about them to double this amount.
CyberGhost
Some features:
- It has a paid version of 5.99 per month for a one-year subscription, reduced to 3.5 euros if you pay for two years at once.
- It works on macOS and Windows.
Advantage:
- Privacy is such that your internet provider cannot recognize what you are visiting.
- There is no limitation of megabytes to consume in your browsing experience, hence it is the preferred option for those who consume a lot of streaming video.
- It is operational from Spain.
- You can connect from 5 devices.
drawbacks:
- It has an automatic disconnection after three hours, which means that you have to log in again.
- To use it on mobile devices we must get hold of its paid version.
- Ditto for high speed browsing.
- More ditto in the case of being interested in browsing sites that are blocked based on your location.
Hide.me
Some features:
- You can subscribe to a payment option of 4 euros or 8, depending on the Plus or Premium plans. In addition, you have a 45% discount for making an annual payment; very to consider.
- You have the option available for free from a device.
- We can use this free VPN on Android, iOS, Windows and macOS.
Advantage:
- You have access to sites that are blocked in your country.
- You have a more than interesting bandwidth, being ideal for the user who enjoys queries on several networks.
drawbacks:
- There is a data transfer limit, although this is quite generous compared to TunnelBear, since we managed 2 GB.
windscribe
Some features:
- You also have two payment options to choose from: 9 and 4 dollars.
Advantage:
- There is no limit to the number of devices a single account can be used on.
- It includes a firewall that helps us avoid malware and a blocker with which to say goodbye to invasive ads.
drawbacks:
- It only has 11 servers although, yes, each one from a different country.
- It has data limitation, although this is quite loose, of 10 GB per month.
Are Internet connections through a VPN 100% secure and private?
Encrypted connections using virtual private networks they are much more secure than most, but they still have their spots that need to be covered to achieve total perfection when it comes to communications security.
There are the DNS leak calls which can reveal a lot of user information. These are generated when certain data leaks out of the VPN network tunneland they are a recurring problem in all virtual private networks, especially free ones.
Free VPNs have also been accused of selling information from their clients to advertising companies, which is basically as if they are scamming you because they are selling the data they are supposedly encrypting. For this reason, it is always best to hire a paid license from any provider.
What dangers exist on public Wi-Fi networks and why should you always use a VPN server?
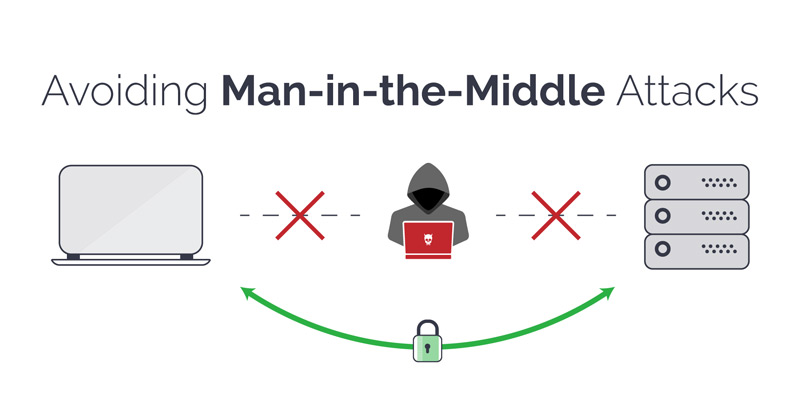
public wireless networks they are a real temptation for any user, especially for those who do not have much data in their monthly plan. However, these can be riskier than people think.
The first thing you should be clear about is that when a device connect to a Wi-Fi network, also communicates with the other devices on the network indirectly. A sufficiently skilled person can get between the router and one of the computers and access the data as it travels over the radio spectrum in what is known as an attack.”Man in the middle“.
This is one of the biggest incentives to use VPN networks since they encrypt all the traffic and when someone tries to interpret it they will not be able to because everything is perfectly encrypted.
|
USES AND TYPES |
||
| VPN for United States | VPN for Venezuela | VPN for China |
| VPN for Windows | VPN for macOS | VPN for Linux |
| vpn for android | VPN for iPhone | VPN for Ubuntu |
| VPN for Chrome | VPN for Mozilla Firefox | VPN for Netflix |
| VPN to play online | VPN to download Torrents | VPN for IPTV |
networks