
You may have seen some Youtuber uncovering mysterious “bought” boxes on the Dark web and you might think that the Deep web is as scary as this one. But you should keep in mind that they are two different terms, when we are faced with a link with the termination .onion it is about the Dark web , and it may “possibly” be loaded with negative content.
The Deep web for its part is only the top layer of this great cybernetic void. Particularly in this one are one of the largest cryptocurrency exchanges, and it is by far one of the sites for buy bitcoins at an excellent price or vice versa and change them to USD, It is also known for having the safest Wallets on the entire internet.
But if you know the existing risks and still require some service, then this section is for you. Here you will see how to navigate safely on both without spoiling your computer.
List of the 10 best browsers to enter the Deep Web and Dark Web without danger … or almost
In order to enjoy the services offered by the Deep web or the Dark web and not be discovered immediately, or that Your identity data is not disclosed, one of the first things you need is to have a browser that allows you to hide well. This step is of course after having a high quality VPN, that is why the first browser we have brought for you is:
Tor Browser

When it comes to entering the Deep web Tor browser project is considered a leader. It is a browser that is made under the code of Mozilla Firefox, but with some modifications that allow you to navigate without leaving a mark by deleting cookies and browsing history.
So companies that use personal information for data collection or simply to track will not have access to that information. Another point to note is that Tor Browser has its own proxy service, and with slight modification in HTTPS encryption, allowing encryption up to 3 times, thus avoiding all types of tracking.
This is highly recommended to also browse the Dark web and thus be able to access your information securely. But beware, it is not recommended to use it for a common navigation, because the Tor added to the VPN among other security measures will make your navigation a complete slowness, which contributes to a longer time in the network , which could leave some kind of trace. In our opinion it should only be used on specific and really necessary occasions.
Invisible internet Project

With all encrypted connections and an extensive network of its own, Invisible internet Project is considered by many to be the best browser to access the Deep web. It has very strong protocols that prevent the tracking of ips, which is excellent for protecting your identity when browsing in these environments. In addition, this has a super decentralized file storage to download without leaving a trace of ip.
It is definitely more advanced than the first of this list in some aspects, therefore its configuration and use are for more experienced users in the area. Another of the advantages is that it has its own network, and of course this makes the connections all encrypted.
This is achieved by skipping some nodes of the network entering and exiting through a kind of tunnels. This system is very different from Tor Browser , because the connections are faster and more private than in the previous one, thanks to the lower number of users.
Whonix

To explore the Deep web, Whonix is considered a bit limited and tedious , since it is not a browser as such. But if it is about safety when sailing it is excellent, and we tell you why. Whonix is a mini open source operating system derived from GNU / Linux and based on the same Tor browser source code.
This means that when browsing the Deep Internet with Whonix we will simply be running an operating system parallel to the main one, and browsing Tor as most people usually do What is the advantage of this? being another system, which is obviously developed to navigate with high levels of security, no malware, no matter how powerful, can access outside this system or our IP, so we will be browsing with full assurance that our data is protected.
Subgraph OS

We are facing another system distributed by GNU / Linux. This time it is a very complete operating system with a complex layer protection system, particularly based on Tor browser.
This is equipped to receive all kinds of malware attacks and has the peculiarity that all its applications are isolated in a sandbox, that basically keeps all applications separate and prevents them from having Internet connection access without authorization. This way no damaged file can spread the infection and all data is kept safe.
Another important feature of the Subgraph OS is that for an application to connect to the internet you need to first pass the firewall test and it also needs to be approved by us Fantastic!
Mozilla Firefox

We know that to navigate the darkest corners of the Internet, the best known and most mentioned method is to enter with Tor browser, and we know that most browsers with high security are derived from it. Although we must emphasize that Tor browser is a direct derivative of Mozilla Firefox, therefore we can also access the Dark web.
But before accessing this means we must comply with certain steps that activate the entry and protection of our integrity.
- Type “about: config” in the main navigation bar of the browser.
- Then type “network.dns.blockdotonion”.
- Change the preference from “true” to “false” by right clicking on it and then clicking on modify.
In addition to performing these steps it is advisable to install some Firefox plugins that increase security such as HTTPS Everywhere and Noscript.
It should be noted that if you do not know how to perform these procedures correctly or do not know how to move on the Dark web, we do not recommend this method, as it is a bit more advanced.
Epic privacy browser

This browser is based on Chromium , designed to navigate with high levels of privacy. It is excellent to go deep into the internet, because has an encryption layer system , which means that at the end of each session any trace or fingerprint is removed.
Navigation is done with a private proxy, so it is impossible for them to find our IP involved in the searches we perform. Although browsing through the proxy is a bit slower, it is the safest mode available to Epic privacy browser and therefore the most recommended.
Google Chrome

For us is the least recommended in this case because it is usually the browser we use for our daily searches, or even to enter our emails and social networks that can contain very valuable information For cyber criminals. But as it is an option, our task will be to expose the risks and share the method for you to decide.
The first thing you should do is enter and install the Deep web extension from this section of Chrome, this is developed by Tor2web . We also recommend to use a free or paid VPN for less risk. The advantage of entering with Chrome is that we will have exclusive access to some internet underworld search engines that might interest you.
Onion browser

This is the best browser to access the Dark web from your mobile, whether Android or iOS. It is very simple to use and is a browser that has all the aforementioned qualities. It is useful to hide, to avoid leaving a trace or leak of our IP and for the protection of our personal information.
Of course, and in all it is advisable to accompany its use with a good VPN that gives us that important security bonus when browsing the Deep web.
Tails

This is not exactly a browser, but an operating system, a Linux distribution to be more precise. It was developed thinking exclusively about user privacy, and therefore has tools to complement the Tor browser .
The most striking of all is its AppArmor, which is a kind of confinement to the browser that protects it from any attack that seeks to steal your data. While also limits the number of folders you can save from this , it’s a price worth paying to be 100% protected.
Qubes
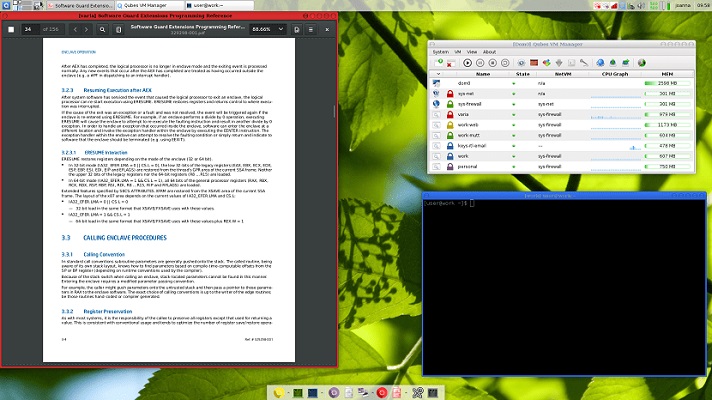
This is another operating system that will allow you to raise the security level of all browsers for desktop devices. Based on the Linux code , this is based on the isolation of the programs, to create a “jail” in which the information is as protected as possible, avoiding all kinds of attacks that attempt to steal it.
To achieve all this, it bases its architecture on four elements such as the network domain, the storage domain and the implementation of virtual machines to run each application in a dedicated environment .
>