
UPDATED ✅ Do you need to NAVIGATE the Deep Web or the Internet anonymously and don’t know how to do it? ⭐ ENTER HERE ⭐ and discover how to do it step by step with this TUTORIAL ✅ EASY and FAST ✅
There are many rumors and myths about the anonymous browser Tor. That it is illegal, that it is not safe, that it incriminates you… The truth is that, although it is not the most effective in all aspects, it is very interesting in certain circumstances, such as, for example, for enter the deep webwhich is the way in which almost all of us have known it.
TOR is a not too long-lived browser that promises us anonymity and securitywhich is why it is used more and more for all kinds of queries, in part, avoiding the aggressive data collection that is done through other browsers and networks.
If you want to keep your data safe and browse in peace, the best thing you can do is cLearn everything about TOR: what is this search engine, how does it work, what does it offer you, what is it for and how can we access it. We see all of this below.
What is it, what is the Tor browser for and what advantages does it have?

Bull The Onion Router is a Mozilla based web browser but that, obviously, differs from this in many things, mainly in terms of the management of our data. We are talking about an anonymous browser that is part of a project to develop a low-latency communication network that is superimposed on the Internet.
The most remarkable feature of this project is that the exchange of messages between users does not reveal their identity, maintaining the integrity and secrecy of the information. To do this, create this free softwareThe Onion Router, which is flexible and resistant to many attacks, although improvable.
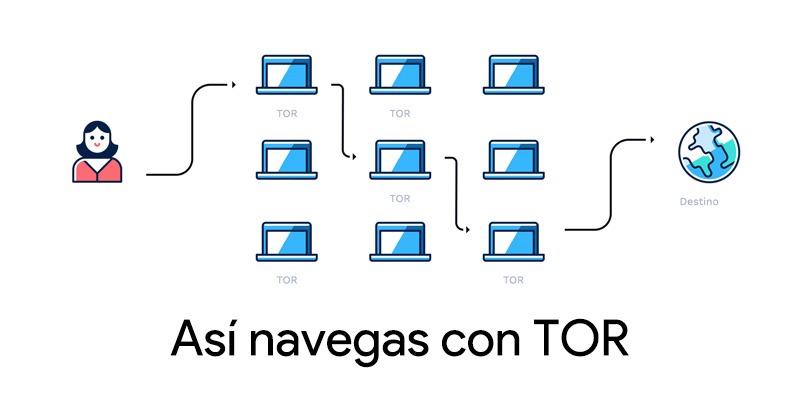
Browsing with this is done by connecting to three layers of encryptionalways seeking the non-compromise of the user’s data. The connection will be transmitted to three different servers located throughout the planet, looking for the anonymity of those who browse to be a guarantee. A) Yes, none of the sites you visit will know where you are doing it from. This action is called Circuit.
In other words, the information sent by our team, data by data, bounces randomly through the connected nodes, in addition to being encrypted. Each node only knows which node it will bounce to next, but it is impossible for it to decipher the information. The exception is given by the last of these, who, if desired, can obtain the information, but will not know the origin.
Browsing is done by connecting to the Tor network. Be careful because the network and the browser are not the same thing at all. It is maintained by volunteers who donate their bandwidth and has no point of failure or centralized entity, as is the case with VPNs. It is, in fact, a kind of peer to peer network, although, in addition to nodes, it also has traffic routers. For know more about a VPN enter here.
East will isolate cookies and erase your history navigation after each session to protect both security and privacy. These benefits have some consequences, for example, a longer loading time or elements that do not work.
It is also important to note that, with time of observation, we can end up discoveringalthough that is something that would require the attention of someone who wanted to identify us, something that will not be common if we do not do anything remarkable.
Steps to download and install Tor Browser on your computer
If you want to download Tor anonymous browser, don’t worry because it’s not complicated at all. We teach you how to do it from the three main operating systems: Windows, Mac and Linux.
for Windows
Using Tor on Windows requires:
- Download TOR for Windows on the official website of TORProject. Click on the version of your choice.
- This will make you have a file called “Start TOR Browser” which you will have to run to start the “facility“, which is nothing more than the choice of browser hosting.
- You will have to choose the route of your interest, that is, the place where you want it to stay.
- When you want to start using the browser, you just have to double click.
- The opening of the browser will take a few seconds, which are the ones needed to make the connection to the TOR network. Therefore, a status box will appear that will quickly disappear.
- When the time comes, the browser will run and you can use it. Of course, the best thing is that you take a look at its configuration and modify it to your liking considering the ISP, firewall or proxy.
- Currently do you have a tutorial offered by its own TORProject within the browser itself, on the main page that appears as soon as you open it. This is located at the top left; you just have to click on the globe icon and it will start.
for mac
- Download TOR for MAC on the official website of TORProject. Choose the version you prefer.
- Depending on the browser you are using at the time, you will be asked if you want to save the file or open it or, directly, it will be downloaded in the predestined folder for it. If you have the possibility, always choose to save the file instead of opening it directly.
- If you do not have the third-party download option enabled, you will have to do it by entering the “Configuration and security” and whom “Privacy”.
- When you want to continue, you just have to go to the download folder where the file has been saved and double click about him.
- Verification will be carried out by the team to ensure that there is no manipulation of the file and the installation will begin, which will be carried out, by default, in the folder “Applications“.
- You may run it both from this folder and from your launchpad.
- The result will be a source warning box. Click on “Open“.
- On this first occasion we will be given the option to make some modifications. You can now make the configuration according to your preferences or click directly on “Connect“.
- When you connect, a process window will open indicating that the connection to the network is being made.
- you only have left start the tutorial by clicking on the globe icon in the upper left corner of its main page.
for linux
- Download TOR for Linux on the official website of TORProject. You have different options so you only have to choose the most convenient for you.
- You will be asked if you want save the installer. Do it. This will start your download. A few moments later you will have it in your default download folder.
- now you have to open terminal work, either from the desktop or from the dock or simply with the commands Alt+Ctrl+T.
- You have to go to the folder “downloads“including the command”CD Downloads” and pressing “Enter“. If the download has been done elsewhere, you will simply have to command to that location.
- It is time to extract the contents of the installer with the command “tar – xvJf full file name“.
- You will find the folder that contains the browser. You have to open it by commanding “cd folder name” (for example, tor-browser_en).
- Now you have to run the browser with the command “./start-tor-browser.desktop“.
- The browser window will now open. Click on “Connect” either “Connect” to start using it.
- You also have the option to configure certain aspects, which you can do now or later.
- When you connect you will have the option to start use the browser through a tutorial with which you will learn how to use it quite simply.
How to configure Tor Anonymous Browser correctly to browse the deep web safely?

We have already seen that one of the main reasons why many people use this browser is because of the curiosity of access the deep websomething impossible to do from conventional browsers such as Mozilla, Chrome, Safari, etc.
Nevertheless, accessing this type of content can be very insecurewhich is why we advise you to make some settings to browse the deep web safely.
In any case, our advice is that you do the following checks even if you do not enter the deep web; The configuration of a browser is very important, it does not matter if it is Tor or any other.
Security settings
For it:
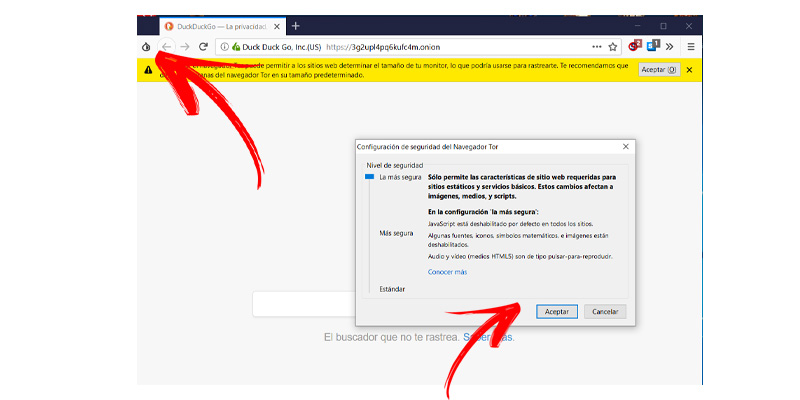
- Click on it onion icon that you will find at the beginning of the top bar.
- Now click on “Security settings“.
- A new window will open allowing you to choose between three levels of security:
- “Standard”
- “Safer”
- “The safest”
- according to the selections you will see the aspects that include each of them. Choose the one of your choice.
- Click on “To accept“.
TOR Anonymous Browser Network Configuration
Now we will do the same with the network:
- go to the onion again.
- This time you will have to click on “Tor Network Configuration“.
-
Here you will find three options that you can check:
- “Tor is censored in my country.“. Find out about it and, if so, check.
- This being the case, you will have the options to choose a bridge, request it or provide it.
- “I use a proxy to connect to the Internet“. No problem with that, if this is your case, check the box.
- In this case, a form will appear to indicate the type of proxy you use, its address, the port and the option to set a username and password.
- “This computer goes through a firewall that only allows connections to certain ports“. This will depend on the configuration you have in your firewall.
- If you enable it, you will have to indicate which ports are allowed.
- “Tor is censored in my country.“. Find out about it and, if so, check.
- Once you have checked the corresponding boxes, click on “To accept“.
To update
It is essential to always keep the browser updated. Our advice is to do it daily.
- Click on the icon of the onion.
- Now in “Check Tor Browser Update“.
- A window will appear that tells you if there is an update or not and, if so, you will be allowed to do so.
Privacy & Security
- Click on the icon three barsup to the right.
- Now go to “Options“.
- From the three tabs on the left click on “Privacy & Security“.
- Various options will appear in relation to forms and passwords, history, cookies, the address bar, protection against tracking, permissions, data use, security and certificates. choose wisely what you want to give and receive from the browser and the browsing experience.
How to use Tor Browser?
Once you have made the corresponding configuration, let’s see how to start using the TOR browser. To do this, we are going to see all the points that we can treat from this software.
Onion icon or TORButton
We have already seen three of the four options for this icon. The last, which in turn is the first offered to us, is “new identity“. If we press it, a window will open alerting us that the windows and tabs will be closed and asking us if it is what we want. We are also given the option of not receiving the notice again.
the new identity means to restore everything, that is, to eliminate all traces of what happened in that session, clearing history, closing sites, etc.
planet icon
East takes you to a simple tutorial.
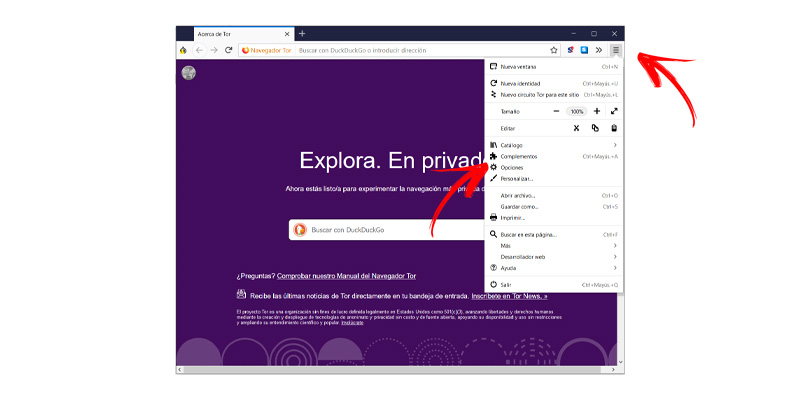
Option menu
The icon with three horizontal bars It takes us, as with any other browser, to a series of options:
- New window. Open another browser window.
- new identity. Ditto if we do it from the onion icon.
- New TOR circuit for this site. The browsing data is restarted but keeping us on the web where we are.
- Catalogue. It allows us to access the options of our bookmarks, downloads and history.
- Accessories. It takes us to a panel of extensions, themes, plugins and language for us to install and configure. Note that all these elements reduce the level of privacy. From here we can decide if we carry out automatic updates, which we always recommend.
-
Options. Here’s a misc that includes the tabs:
- General. Spell check, download options, application management, actions related to Firefox…
- Search. Options about the search bar, the default search engine and alternative search engines.
- Privacy & Security. We have already seen it in the previous point about configuration: history, cookies, certificates, etc.
- Personalize. The amount of elements available is immense, from changing sizes to sending links, flexible spaces and much more. All these options can be placed in the overflow menu (which we will see next).
- Plus. Here you enable character encoding and offline work.
- developer. A compendium of shortcuts and other tools to make browsing more comfortable and faster.
- Aid. A help center for various aspects, has no further explanation.
overflow menu
It is created to the right of the address bar (trailing quotes icon) including all the aspects that we have chosen from “Options” > “Customize“. This is a marker that allows us to have access to these functionalities without having to access the corresponding menus where they are.
onion services
These are sites that have added protections, being contrary to censorship and allowing us to share content completely anonymously. are services whose access is made exclusively through the TOR network, that is, they do not exist anywhere else. Of these we can say that:
- IP address and location of these are hiddenso that it is difficult to detect and censor and, of course, the identification of the operators.
- The traffic of these services is encrypted end to end.
- Each service has a automatically generated address consisting of a set of 16 letters and digits with a .onion extension.
There are all of sites encrypted in this way but, unfortunately, they are not found in the search engine. You must know the URL to be able to enter, something that is not difficult either, since there are even encyclopedias (the most famous is HiddenWiki) where addresses are continuously added. In case you’re wondering, yes. These are the contents of the first level of the deep web.
No script
This pre-activated extension is a blocker that is responsible for alerting us of different situations and from which we can make some decisions. It is a lot like AdBlock.
You’re told what type of page you’re on, whether it’s trustworthy or not, it filters sites based on it, you’re given the option to temporarily pause alerts on the site or in general, and a few other little things. plus.
Main window
In it you will find a search bar to enter what you want to search for. Is corresponds to the search engine you have as default or the one you have put, to your liking, if you have already changed it.
Tor anonymous browser address bar
in her too you can do a conventional search, which will be done with the search engine you have. However, what is interesting is that you can write an address with .onion domainthat is, onion services.
When you use one of these services, the bar changes to show you, to the left of the URL, an icon of a green onion, which indicates that the connection is totally secure and that, in addition, an onion service is being used. Yes, besides, you access a site that is HTTPSYou will also find a padlock.
Circuit
We have already talked about the reset of a circuit but… what is it? Where is it? This is accessed clicking to the left of the URL. By doing so you will see the IPs that have been used while browsing what you have done and are doing Also from here you can choose to create a new circuit for the site you are on.
Is it possible to use Tor Anonymous Browser on Android or iPhone mobile phones?

The diverse use that has been given to it over the years and the growing use of the Internet to do absolutely anything has meant that, of course, the demand for the browser and the network that we are analyzing has also grown on mobile devices.
A) Yes, The mobile version of Tor has already been released, available for Android, in no more and no less than 29 languages. This is available, of course, on the TOR Project website, being, so far, yes, an experimental alpha version. We also found it in the store google apps; you just have to search for it by “The Onion Router“, from the developer”The Tor Project“.
This does not yet have all the active functionalities, so it will be more complete than what you initially see when you download it. The stable version, ready to simply be updated, is expected to be released during the first months of 2019. However, you can already start using it for the basics, which, after all, is what most of us are looking for when using TOR. : an improvement of our privacy.
Know that in order to use TOR on mobilein addition to downloading the corresponding software, You will also have to download the “Orbot” app. This acts as a proxy server, so that it enables the connection between your mobile version of Tor with the general network that the browser works with. For the rest, you will see that its configuration and start-up is as simple as if you were doing it on your computer.
In the case of iPhone phonesknow that the app is available “vpn-browser” as well as “Red Onions” as the most used and complete (there are several others). These they are not official applications from The TOR Project but from other developers. In any case, they are used to connect to the Tor network but they are NOT the Tor anonymous browser.
Computing