
Index:
UPDATED ✅ Do you want to know the reasons why you should take care of your data on the Internet? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
It is no secret to anyone that the Internet has become the right hand of the human being, especially since in it you can look for any type of information and always get an answer for it. All this has made it become a very essential tool for any human beingEither for carry out student research, for the workplace, to carry out banking operations among many others.
However, perform daily online activities can reach disclose your personal information, allowing that unknown people can invade your privacy. And it is that internet privacy it’s the only way they have users to be able to control where their personal data goesboth to personal and work level, so security in these cases is very important.
You should keep in mind that when you do Internet use to carry out all or almost all your activitieseverybody your data is in dangerincluding bank details, confidential, email, physical address, among many others. That is why it is extremely important to be able to protect your privacy online, To learn correctly how to do it, simply follow in detail everything that we will teach you below.
What are the main risks of not protecting our online privacy?
Being able to surf the Internet will give you a large number of options on what to see, what to download, what websites to visit, what social networks to useamong many other activities that can be carried out.
But the truth of all this is that in most cases they end entering personal data Either for access a banking website, register on a platform, open one of your social networks, among other. As you can see, basically all movements made from the network have their dangers in terms of security and privacy.
Therefore, not taking the necessary measures to protect yourself can cause you different types of risks, such as the ones we are going to show you below:
Identity theft or impersonation
Without a doubt, this is one of the aspects that most concern most usersespecially since this type of action has become very common on the network, especially nowadays when practically everything in Internet forces users to have to leave certain personal dataEither for access a website, to enter social networks, to register on a web page, among many more
All this has made people engaged in committing criminal acts can take advantage of it, since with manage to extract a few pieces of data from a person they can begin to impersonate them. All of this is known as identity fraud and is currently used for defraud and steal from other users through the network.
no doubt this violates user privacyso it is recommended avoid giving personal data and information publicly. In the event that you get to be affected, the most recommended is make it known on the platform where you are being affected, this will help you cover your back.
Spam and data to third parties
spam every time it’s done more present in usersand this has become a way of manage to scam users either through the emails or social networksthese being the most common means where are these made types of activities.
In this case users receive an advertising message or email that invites them to access a website and register through very tempting promotions. But the truth of all this is that these platforms end being false and their goal is to make the person enter your personal data for later extract them and use all that personal information to carry out each their illicit activities.
get a virus
not count on no protection while browsing can cause you different security issuesone of them is the get a virus on your computer. Please note that these malicious software they can be in the websites, in some file you download from the webin an email or in any message you receive from a social network.
One way to try to prevent these software types is having the ideal tools for it, in these cases it is about antivirus or antimalware programs that constantly they will analyze the websites you visitas well as the different files you download from the web. This will help you have your computer completely clean and out of danger at all times. Note that viruses can cause serious or irreparable damage to your machine.
Social networks

From the birth of social networks user security problems increased considerably, and it is that despite the fact that these platforms have become a essential site for most people, they place mostly users’ personal data as easy prey for online criminals.
That is why in these cases they are the same users who must place the limits. Fortunately, each of them decide what to post and what not to postso all must be taken into account the risks that are run when uploading personal information to these platforms.
Many people are constantly publishing their vacations, photos of their children, where they study, their daily routines, among many others private data what can be used by third parties. Thanks to this type of action, what is it sexting or cyberbullyingwhich is why it is very important to be able to control and limit everything that posted on social media.
Phishing attacks
phishing attacks have become one of the biggest problems for most users, and it has become the main technique used by people to carry out non-legal acts in order to extract personal data, credentials, passwordsamong many other important data.
These types of attacks can be carried out in different ways, but the most common is through the e-mailsin these cases they are usually send messages purportedly from well-known websites or platforms such as Instagram, Facebook or Twitter, where it tells them that they should update your password or your personal data for security. To try to make this quick, They force the user to respond to said email within 24 hours.
However, the point of all this is to make you believe the individual that there is a problem with their account so you should immediately access the link that has been left there. That way the individual agrees and enter all the necessary data to update your personal and work information. But the problem is that all these data goes directly to criminalswho take advantage of this technique to extract all the private data and access credentials to carry out their different illegal activities.
child pornography
This point is addressed directly to all children’s social media accounts that currently existit must be taken into account that children today do not measure the danger that can exist on the Internet, so they usually upload a lot of content on your social networks to share with friends and non-friends that they have there among their contacts.
But the truth of all this is that there are many people dedicated to taking photos of minors to be published on pornographic websitesso the photographs of all these children can reach in danger. In these cases, the most recommended is that parents manage such accountsthis will not only let them know who is in communication with youbut they can also see what types of people follow them on each of their profiles.
Should I really worry if companies know my online consumption habits?
Keep in mind that online consumption habits are the actions they take users repeatedly on the weball this is very valuable in the world of marketing for companiesas it has become a form of power meet customers, find out what they like, what their favorite activities are, among many other data they can collect.
However, all these habits are taken into account from the beginning. consumer point of view and refers directly to the behavior and custom of that person. In the case of companies their success depends largely on the success of their marketing strategy, and it will depend on what whether or not your analysis of the consumption habits of your potential customers is correct.
Therefore, it is considered that the habit of consumption does not turn out to be so dangerous for users, since this has been taken as a measure by the companies to try to know their public and to be able to reach them in a way more direct and easy. Nevertheless, There is a risk that all this data could be taken by a malicious individual with the aim of taking advantage of all this information.
Despite this, the collection of data from companies regarding the consumption habits of users has not become a biggest problem for consumers so you could say that this is not really worrying as long as highly confidential information is not being provided What passwords, bank details, physical addressesamong others.
How does the NSA brazenly spy on everyone? Snowden case
If you still don’t know, it is presumed that the NSA started some time ago espionage around the world in a brazen wayall this has come to light thanks to the revelations made by a former CIA employee Edward Snowden, all this left in shock to the entire international community. This is how this young American has tried to traitor to the National Security Agency (NSA), everything led him to be cataloged as a hero by the international community.
But in his country he has been considered a traitor to the countryso today Edward Snowden lives in asylum in Moscow. In the same way, Edward Snowden has pointed out that USA has a running espionage plan not only in your country, but all over the worldwhere he even points out that he performs a spying on several European leaders through their mobile phones.
Some of the ways the NSA conducts this type of espionage include the following:
Gaining access to company data on the Internet
According to some Leaked documents have revealed that the NSA had one back door in order to get a access to most of the data of companies in the world. Said leaked document showed that the agency entered servers of large Internet technology companies as they were Google, Microsoft, Facebook and Yahoo companiesall this with the purpose of being able to spy on communications through the Internet, all this was carried out through a surveillance program called Prism.
Thus, it was noted that Prism gave you access to the NSA ya your british counterpart, the Government Communication Headquarters. All this allowed him to have a access to emails, information from social networks, chats, voice traffic, file transfers, stored data, among many others. Despite all these revealed documents, the security company Prism strongly denied to have provided all access to their servers.
Through phone calls
In October 2013 the German media reported that the United States had intercepted the mobile phone of Chancellor Angela Merkel, for more than a decade and that this espionage had been completed only a few months ago. To all this it was necessary to add the documents provided by the American Snowden, where it is claimed that The NSA had been spying on Merkel since 2002.
according to different documents cited They pointed out that this practice of listen phone calls was not only being practiced in Germanybut also in 80 other countries around the world. which indicated that the NSA was getting a lot of information from people, businesses, and citizens around the world. In the case of the chancellor Angela Merkel it was found that they were affected two of your phones, one of them was used to obtain details of your party.
While the other was the one he used to all the themes government related. According to experts standard encryption may be vulnerable to coding systemso it is separate from the program that is used for create the message. All this allows the spy can place itself between the program that created the message and what it is going to encrypt.
This way you can see the information before it is be decrypted or encrypted. In addition, there are also many indications that the NSA has been monitoring millions of calls from German citizens, French citizens and even the phone calls of the presidents of Brazil and Mexico at the time. In the same way it is presumed that they have achieved spy on the phones of at least 35 presidents from around the world.
Through the fiber optic cables
In June 2013 it was discovered thanks to the documents leaked by the young American who the NSA also carried out espionage through fiber optics, that’s how he UK was able to intercept fiber optic cables with global communications where all this information went directly to the United States National Security Agency.
According to the documents that came to light, they indicate that they had access to 200 wireswith which they were able to monitor around 600 million communications a day. Both the information obtained through the Internet browsing and phone use was stored on their servers for up to 30 days so that it could be properly analyzed.
In everything related to this The Government Communications Headquarters by its initials GCHQ refused to do any comment type. But time later the italian weekly L’Espresso made known to the international community how much the NSA as GCHQ they had counted with three submarine cables terminated in Italy, managing to intercept data both military and commercial. the wires in Sicily were called SeaMeWe 3, SeaMeWe 4 and Flag Europe-Asia.
Through targeted espionage
Another of the complaints that came to light was that of the NSA spying on the offices of the European Union in the United States and Europe. All this thanks to the documents provided by Edward Snowden who managed to prove that USA had one computer network of the European Union in Washington and in the offices of the United Nations bloc (New York).
These same documents also state that the National Security Agency also made espionage operations in Brussels buildings, there you find the main offices of the institutions of the European Union. In the same way, it was found that least 38 embassies had also been targets of this espionage, among some of the affected countries were Greece, Italy, France, Japan, India and South Korea.
And it is that not only a espionage outside the United Statesbut also the embassies and diplomatic buildings of New York and Washington they were being watched. For all this it was pointed out that they were used extraordinary ranks to intercept telephone messages, recordings and specialized antennas.
Social networks as our digital personalities How much information does your profile contain about you?
It is no secret to anyone that social networks have become a part of life for many people, where many have cataloged it as a open diary of each of the people, and is that the vast majority of users he usually publishes everything or almost everything related to his life, such as his personal life, work, friends, family, hobby, partner, among much other information.
This is how on many occasions and without thinking about it, users end up showing all their information through their profiles, which is why the question of How much information does your profile contain about you? And the reality of all this is that anyone could deduce your lifestyle simply by checking your social media profilethese types of data can be used for malicious purposes without you realizing it.
Among some of the private details that can be obtained through profiles on social networks are the following:
The personality of the person
through thes publications made on this platform, of the comments made and of all the interactions that take place thereyou can easily manifest the way in which select friends, type of family, job, among many other aspects that help define the user’s personality type.
In this case you can get two types of personalities:
- Exhibitionist Personality: It is usually said like this to those people who constantly accept any friend invitation without knowing who it is, because in the minds of these people it is understood that The more audience you have on your social network, the better it will be.. Furthermore, they are constantly updating your profile just to be noticed but without interact a lot with others.
- Exploitative or aggressive personalities: This type of person also seeks get a large audience and that they are also heard and answered. This personality type is usually aggressive when people do not reply to their statuses or interact with them.
It has been proven that this type of behavior may be due to celebrity syndromethese are people who want to have a large audience and always be the center of attention, where everyone or the vast majority always has to do with them.
They are a window to your real self
Although many users do not realizesocial network profiles have become a window into your real life, Well there you can basically see people’s behaviorwhether the same he spends his time traveling, partying, he is a professional, he is studying, among many other details.
It is worth mentioning that in social networks all people show a lot of personality more open to who they really are, this is because many Users can easily express themselves and interact through a computer or mobile than doing it in person.
The famous bermuda triangle
Perhaps many do not know what it is the bermuda triangle in social networks, but it is called if relationship or coherence what should exist between the photo, the name and the biography of the user. Taking into account that these three things influence a lot to know the type of person behind that profile.
If it’s a person enterprising or of a lot of work possibly your profile picture is related to your workalso through this photo and biography you can get to know the level of status of the person. All this will allow you to know if you can find it well economically or not.
The truth of all this is that social networks end up providing more information about you than you can imagine, thanks to them many people without even meeting you in person they can know what you like, who your closest circle of friends is, what you do, your family, among many other aspects. Due to all this, it is best to be very careful with the type of personal content that is uploaded to them.
Learn step by step how to configure the privacy of your social networks from scratch
Considering all private information that can reveal the different social networks today, it is very important to know how to set up your privacy from scratch. That is why here we are going to teach you to how to carry out this procedure in each of the most important social networks of today.
To do this, follow in detail everything that we will teach you below:
On Facebook
power to control privacy in each of your social networks is very important, in the case of Facebook It should be mentioned that it is one of the platforms with more registered usersso there you have the opportunity to get people from all over the worldthis means that the chances that personal information can reach the hands of strangers increase.
In order to configure and increase your privacy within Facebook, you will need to follow each of the following tips that we are going to give you:
Choose who can see your photos
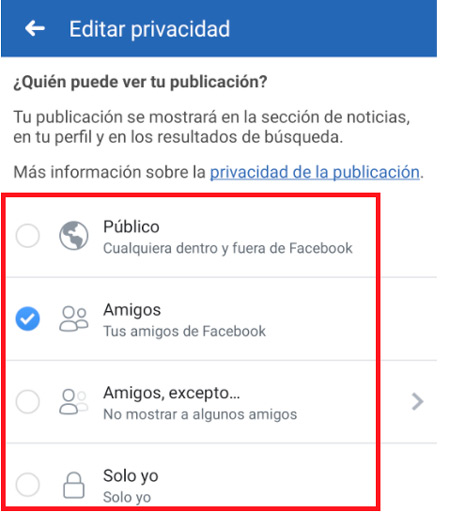
Every time you do a Facebook post this can be seen by all people, that is, by those you have in your list of friends and for those who are not. A form of increase your privacy is by making said content uploaded can only be seen by the people you wantin this case your list of closest friends and family.
For this you can configure this from the right panel of your own appin the list of options that appear there you simply have to select the one that interests you the most, either if you want your post is public, that only your friend list sees it, some specific friends or it is only available to you.
Decide who can see your comments or activity
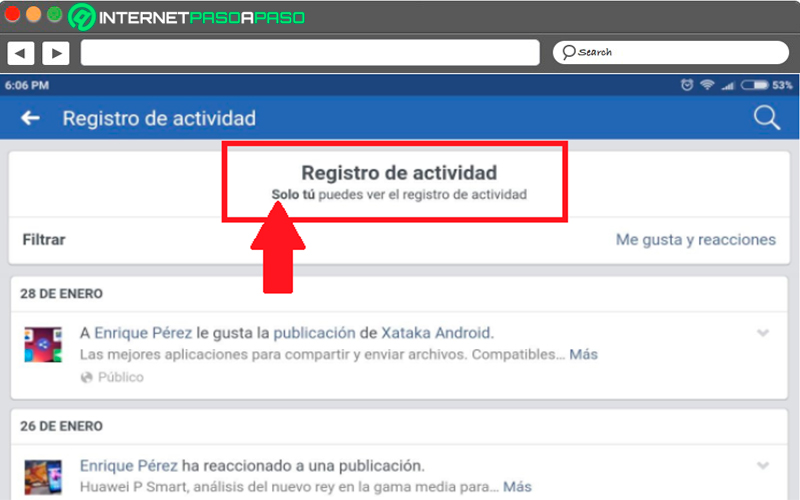
Another way to keep your account private is deciding that people can see your activity and commentsfor this you must enter the “Activity Register” from the “Account settings”, here you can see all your activities within the platform, at the top you can see marked that users can see your activityhere you can select if only your friends, only you or all.
Choose who can send you friend requests
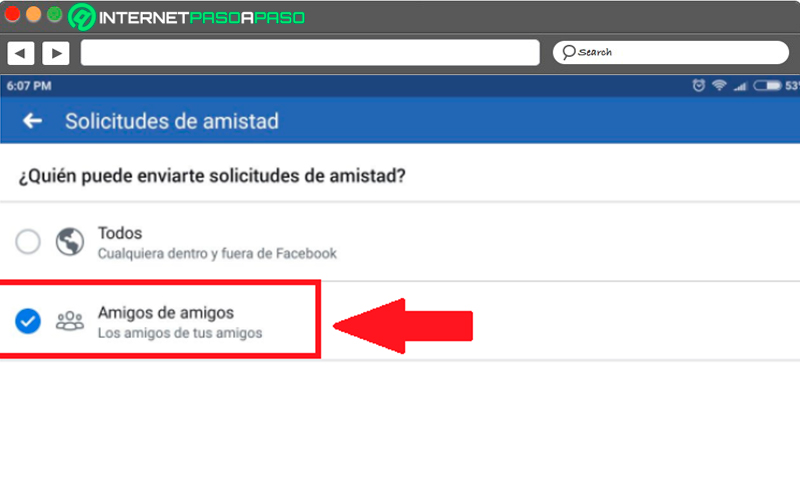
Most people tend to constantly receive friend invitations from strangers, which can be quite tedious for most. In order to avoid this, you need to go to the bio just below your profile picture, there you go find three buttonswhen you select it, a drop-down menu will appear where you must select “View privacy shortcuts.”
When you are in this section you should look for the option “Who can send you a friend request”, this will prevent people unknown to you from sending you such a request, here you must select the checkbox “Friends of friends”.
Configure who can see your tagged photos
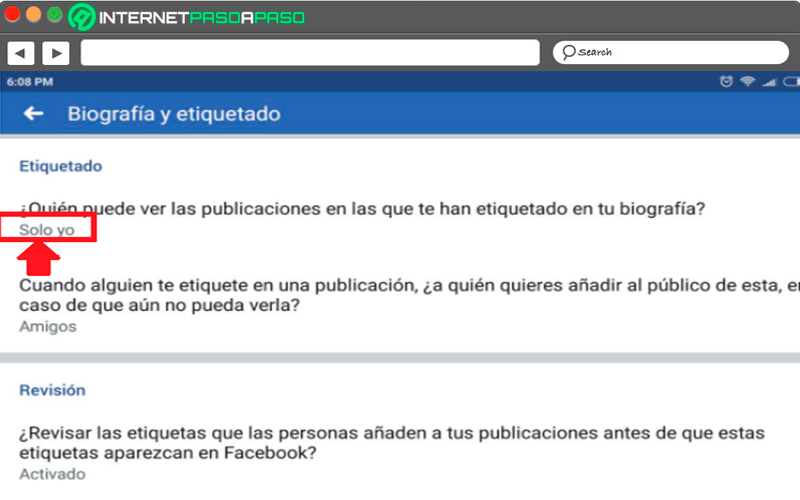
On many occasions it ends up being tagged in photos you don’t want anyone else to see, to maintain this privacy and be yourself who decides that this photo appears or not, then you can configure this section, for this you must go to the “Biography and Labeling” from there you will be able to establish a option series that will allow you to define who can see the photos where you are tagged.
Not being able to handle the tags personally, as any friend can upload an image and tag yourself in it, the only way to do it is by applying this type of options. To do this in the labels section in the option Who can see posts you’ve been tagged in? You just have to select “Just me”.
On Instagram
Instagram is currently the most popular social networkit is used almost all over the world, so it has a large number of Active users. It should be mentioned that this platform is fully photographicso your users can upload photos or videos and thus share them with your friends and followers. However, being able to keep privacy in your account is very important, for this we teach you here how to make your Instagram profile much more secure at all times.
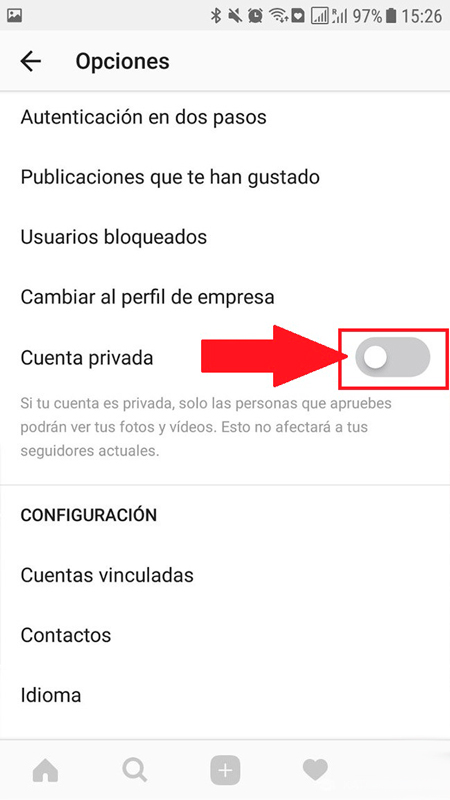
Set up your private account
This social network, like most, allows its users to decide whether to have a public profile or only privatein the case of public profiles any user can access regardless of whether they are your friend or not, he will be able to see all the content you have in your feedin the case of private accounts only your posts will be available to your followers.
In the case that a user wants to be your follower, then you must approve said request first, this will allow you to decide who can see your photos and who doesn’t. To make your profile private You need to go to the section “Profile” and there click on the three vertical dots at the top right of your screen.
In the drop-down menu that appears there you must select the option of “private account” and do what the switch is set to green. In this way no user who does not be your follower will be able to access your posts on Instagram.
Block those users who annoy you
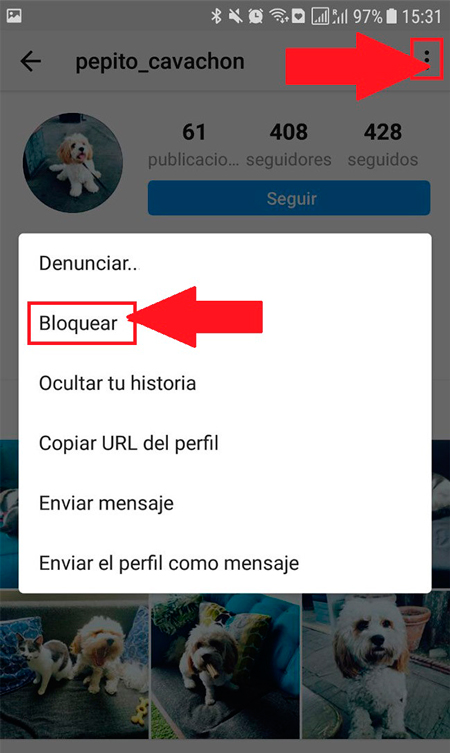
On many occasions you usually have unknown people added in your account that are constantly bothering you either sending messages or commenting on your posts. A form of fix this is by blocking that contact.
By blocking it, said person will not be able to access more to your profilewill not be able view your content or comment on your photos regardless of whether your account is public or No. To be able to block a user you simply have to go to that person’s profile, there you click on the three vertical dots that appear at the top of your screen and in the options menu that appears you select the option “Block”, Automatically that person will no longer be your friend and will not be able to know anything about you again.
Hide the posts where you are tagged
Can control photos that your friends upload where you go out is practically impossible, but one way to Preventing these photos from being seen by your followers is by hiding these publications from your profile.. Luckily, Instagram allows you to have all the necessary control in your feedthis will allow you to decide what is going to be shown in it and what is not.
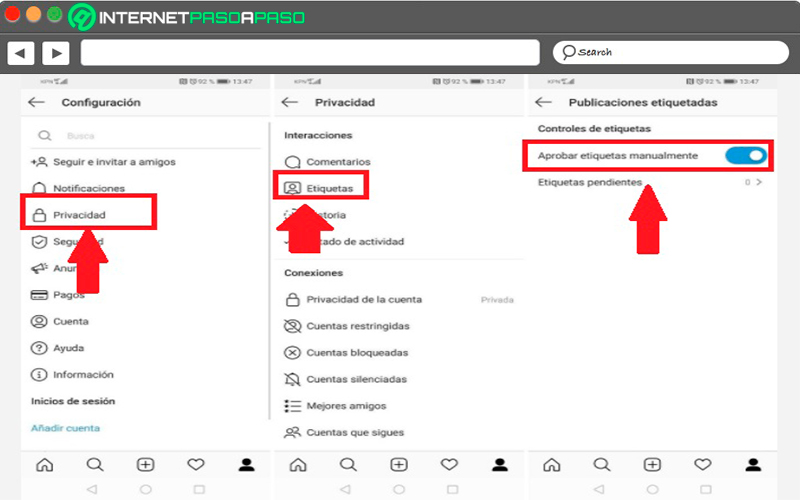
In order to hide these publications, you need to follow each of these steps:
- The first thing will be to enter to your profile section,
- Then access the menu setting up your account.
- There you must select the option “Privacy”.
- Then click on the option “Labels”.
- Now you owe toActivate the option that appears there to approve the labels manually. This way every time someone tags you in a photography or video first you must approve if you want this to be reflected in your profile.
Control the comments they make to you
Another advantage offered Instagram regarding your privacy is that it allows you manage the comments they make on your posts. In this case you can restrict who comments on youalso has filters that allow you to detect certain words in them and automatically block those comments so that they do not appear. This is a very good way to prevent them from being make some kind of unpleasant comments.
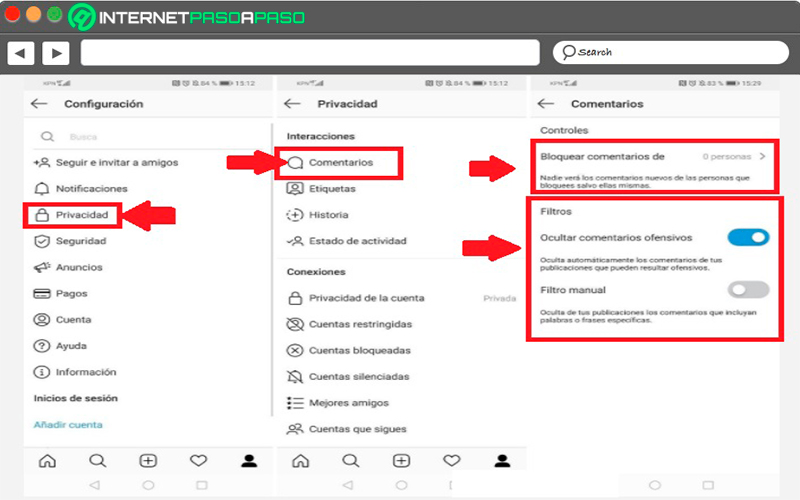
In order to manage these comments, you simply have to follow these steps:
- Here you must access the menu of “Settings” from your profile.
- There you must enter the section of “Privacy”.
- Then click on the item “Comments”.
- Now you have to activate the option hide offensive comments.
- In case you want a particular user cannot comment, then you must enter their name in the comments section. “Block comment from”.
This way you can prevent some people comment on your posts and in turn prevent them from having offensive or rude messages by other users.
on WhatsApp
WhatsApp It is one of messaging applications most important in the whole world, although it may seem a lot safer than any other social network, the truth is that this application comes by default with a configuration that could harm your privacy, that is why here we are going to teach you how you can improve privacy in it and prevent your contacts from knowing a lot of information about you.
To be able to enter the WhatsApp settings you will be able to do it through the following route, this will depend on which smartphone you have, Android or iPhone:
- Android: “WhatsApp” > “More options” > “Settings” > “Account” > “Privacy”.
- iPhone: “WhatsApp” > “Settings” > “Account” > “Privacy”.
Considering what is the path to access the privacy of your application, here we show you what aspects you can improve security.
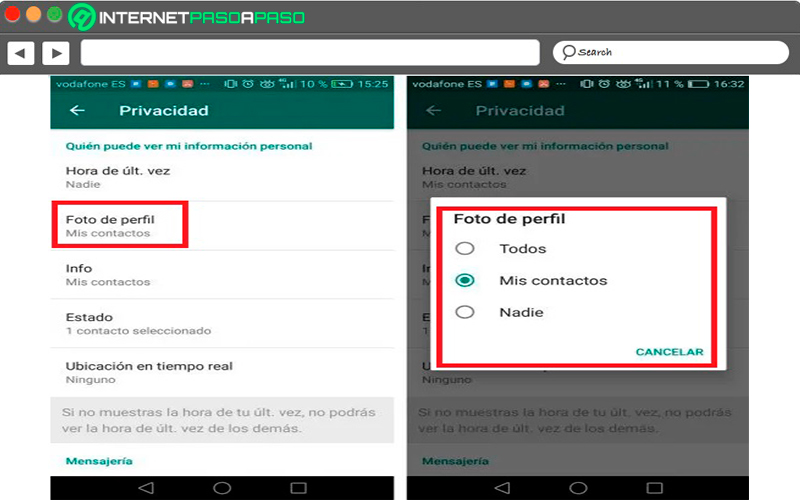
Profile picture
The app settings It is programmed so that by default your profile picture can be seen by any user who adds your phone number. However, this can be change so that your photo can only be seen by those users that you also have added. For this you can decide if you want your profile image to see it “All WhatsApp users”, “Only your contacts” or “No one”.
Decide who to show your status to
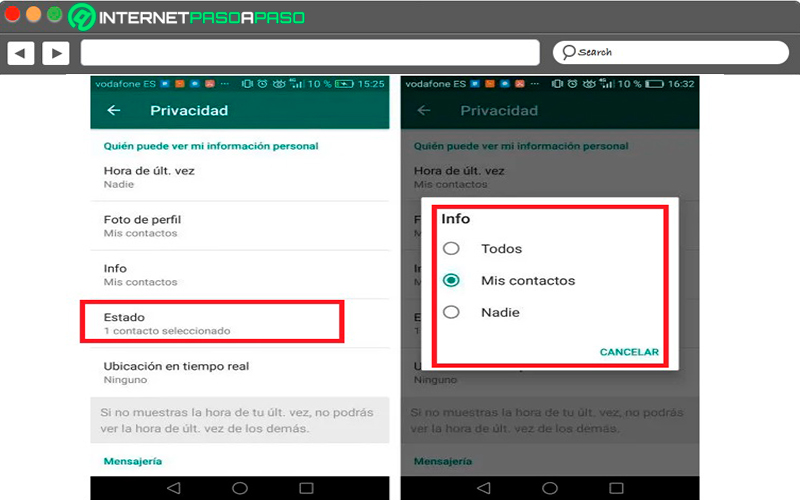
With whatsapp status the same thing happens with profile picture, every time you upload a status it comes configured by default to be shown to all the people who have your number stored no matter if you have them. Luckily all this can be configured from Privacyin this case you have to select the option “Condition” and from there select any of these options “Everyone”, “My contacts” either “No one”.
Connection time and online
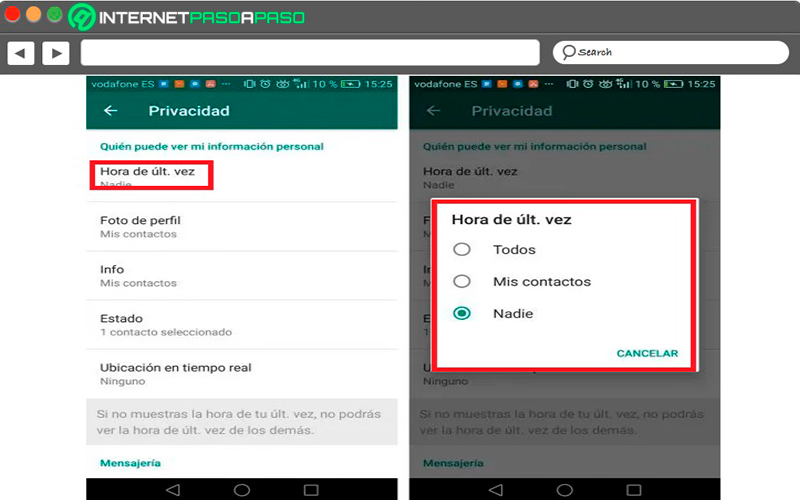
It can be said that this is one of The aspects that most violate the privacy of users in WhatsApp and it is thanks to connection time other users can know when it was the last time you entered the messengerthe same happens with onlinethis allows other users to see when you are using said application. WhatsApp It allows configure these aspects.
This is how you can decide if you want it to be shown your connection time or notin the case of online status if you will not be able to hide just like typing. You should also keep in mind that when deactivating your last connection timeyou can’t either see the last hour of your contacts. However, since messaging privacy and from the section “Time for last time” you can select if you want that option to be seen only your contacts, anyone from courier or nobody.
Turn off read confirmation
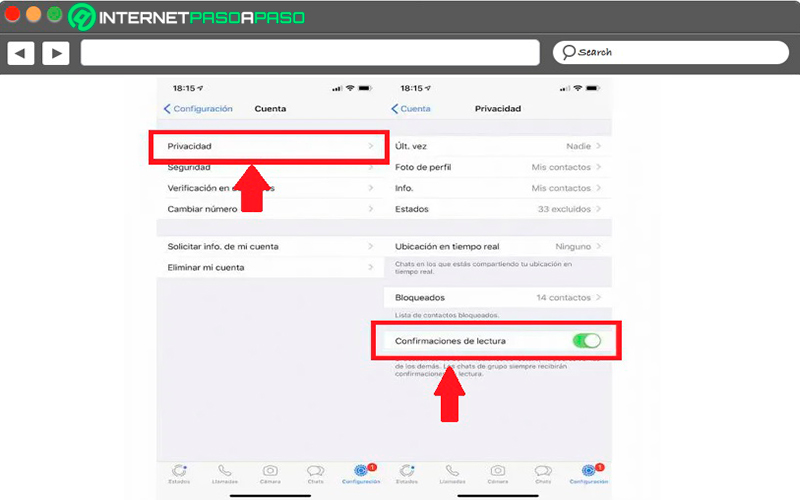
The old versions of instant messaging they did not apply what is the read receipt, This is the famous blue Check which has become so popular in said application. Its function is to indicate the person if their message has been sent, if the user has already received it and if it has already been read.
It is defined according to the following:
- A single gray Check it means that the message has already been sent successfully.
- Double check gray it means that your message has already been delivered to the recipient’s device.
- Blue Double Check means the recipient has already read your message.
A large part of users do not like to reveal this type of information, especially because it is feel compelled to respond once they have read it. Luckily this is something that can be changed from the “Privacy”, here simply you must disable this optionbut note that this is not disabled for group chats and voicemail playbacks.
block contacts
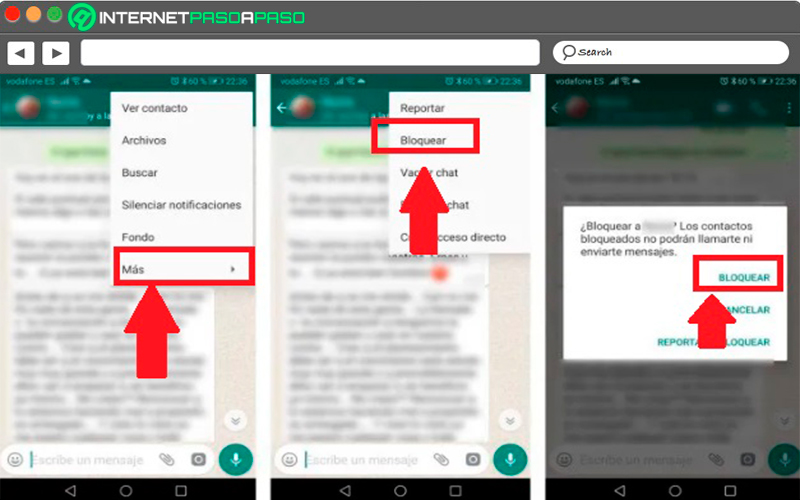
How many times have you had an argument with someone? your contacts in messaging and for some reason you don’t want that person to keep you on their list. One way to fix this is “Blocking” you can do this directly from the person’s chat by clicking on the three points located at the top right and in the options menu by clicking on the item “Plus” and in the new menu select “Block”.
Another way of add users to your block list It’s from the options “Privacy” right at the bottom of the menu you will find the option to “Blocked Users” from there you can add those contacts with whom you do not want to have any type of communication via instant messaging.
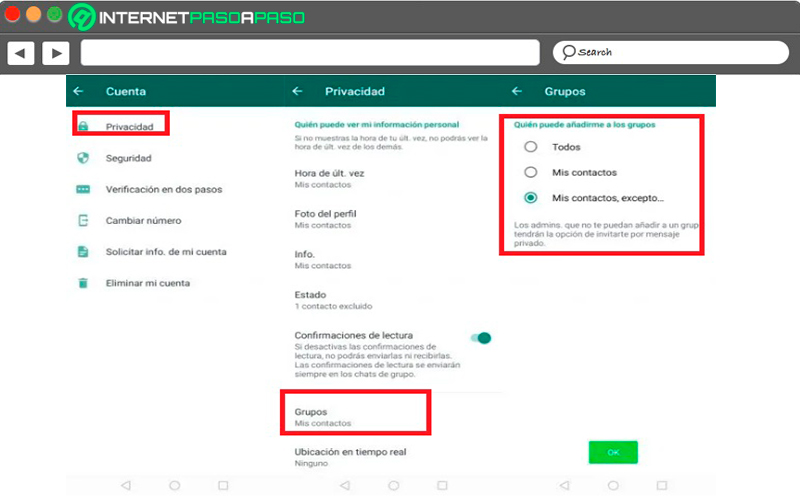
Avoid being added to WhatsApp groups without your authorization
Surely at some point you have added to a WhatsApp group without first consulting it and in which you do not want to beso your only option is leave him. But luckily for the vast majority all this has changed and you can choose which people can invite you to join a group. Here you can choose between “All”, “My contacts” or “My contacts except…”.
On twitter
Twitter is another of the most used social networks in the worldit consists of a public platform by which any user can access it. However, for all your data and information are saferthis platform offers you some tools that will help you mainly with its privacy.
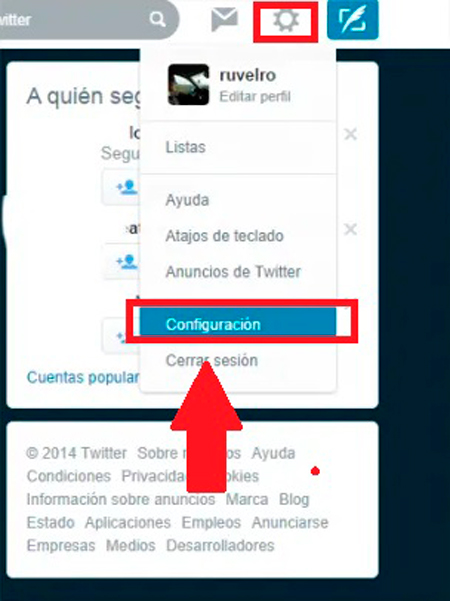
In order to configure the privacy options on this platform, you need to access to the settings menuto do this you must select the option of the wheel located at the top of your screen, there a drop-down menu will appear where you can select the item of “Setting”.
Now in the menu on the left side of the section “Setting” You must choose the section “Security and privacy”, from said menu you will be able to configure some aspects related to the security of your account and privacy.
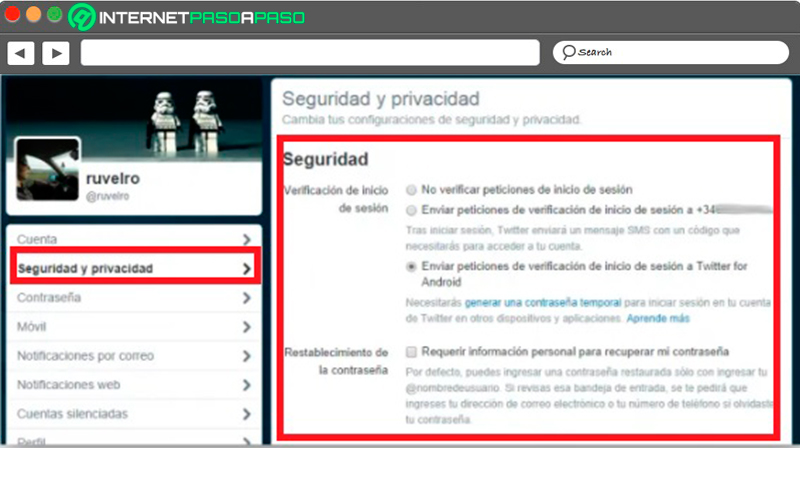
As can be seen in this section there are different security options, all or most of them directly related to the loginthis in order to prevent unauthorized third parties can enter your account. One way to improve this is by activating 2 step authentication, this will offer you extra security when logging in. You can also request that the system asks you some personal questions every time you log in.
Now in the Privacy section you will find the following options that you can configure:
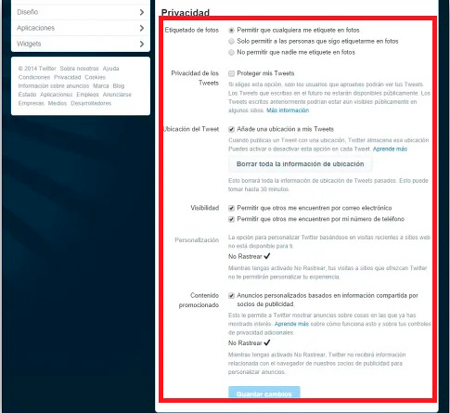
- Protect tweets: With this option you will have the opportunity to close the account to all those unauthorized persons. This allows anyone who wants follow you and see your posts first he will have to send you a tracking requestonly if you accept it, said person will be able to access your content.
- Tag in photos: In case you want to control the publications in which you are taggedthen with this option you can choose which users can tag you in the photos that are uploaded to the social networkhere you can select if anyone can do it user, your friends or just nobody.
- Visibility: It is done with the aim of knowing if you want other members of the platform to be able to locate through your email or phone number when they want to meet you there.
- Tweet location: This function allows you to choose if you want each of the your tweets will have the address added as metadata or no GPS data will be sent. You can also choose to delete all the GPS data of all the tweets you have previously published.
- Promoted content: Through this option, the social network will place your timeline promoted ads of their sponsors Depending on the type of content you post.
Being able to configure all this correctly will undoubtedly help you improve your privacy and security at all times. This allows you to have a greater control of your activities and movement on Twitter.
on Telegram
Finally we teach you how configure privacy in your Telegram messaging application, It should be mentioned that this app does not have the same whatsapp popularity but as for their operation are basically the same, so despite being a chat appthere are many details that can reveal some aspects of your privacyTo avoid this, you need to modify the following aspects:
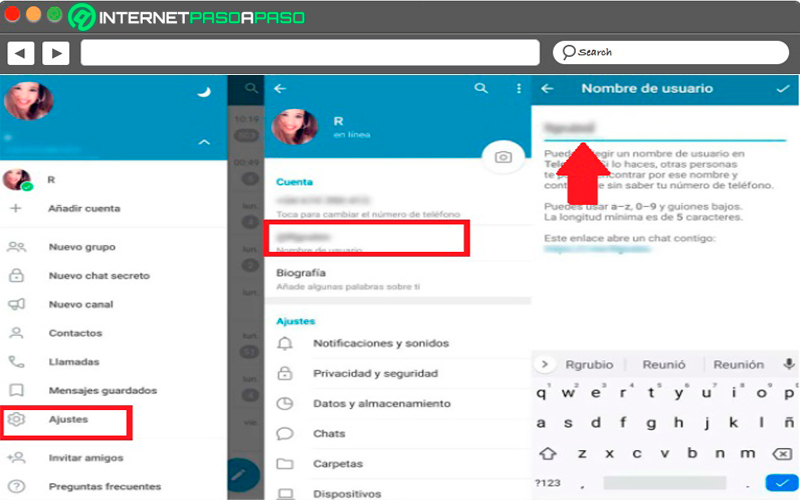
Username
Unlike WhatsApp not here you need to give your number so they can add you to their contact list, in this case it is a Username what to have but what it is not mandatory eitherit must be taken into account that this is done so that other users can search for you and write to you through messaging. In case you don’t want to have a Usernamethen you can simply use your phone number for it.
With the alias or username the other users of the platform will be able to search for you and get in touch with youbut at no time will you have to give your numberso that improve your privacy. Therefore, it is most recommended use an alias and thus avoid giving your personal data. Also, in case someone you don’t know adds you you can easily delete or block it, this will prevent that person from being able to contact you again.
In order to choose a username and thus avoid giving out your phone number, you need to follow these steps:
- Once you are inside the Telegram app you should go to the three lines located at the top left of your screen.
- In the menu that appears there, select the item of “Settings”.
- Now you will see the section “bill” and in it the option of “Username”.
- Here you must click on that option and write the alias with the one you want me to other users get you.
- When it’s done, just click “Confirm and Save”.
last time and online
In this instant messaging app you will also have a last time and an online, But as same as WhatsApp allows its users to hide this and that way improve your privacy. This will prevent your contacts know when was the last time you accessed the messaging.
To modify these parameters you must follow these steps:
- The first thing will be to enter the “Settings” of the application.
- Then you must access the section of “Privacy & Security”.
- There you will find different options available, in this case you must select “Last time and online”.
- There you will find three options, in this case you must select “All” if you want all the people of Telegram see your last time, if you just want that your contacts see it either just “nobody” if you want no one can see this detail about you. By applying this function you will not be able to see the last connection time of your contacts.
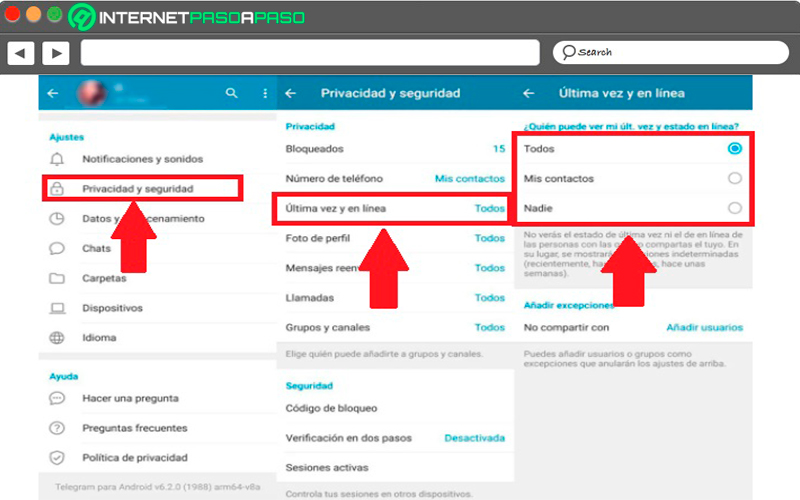
In the event that you do not want to share these details of your privacy with only some of your specific contactsthen you can go to the section of “Add exceptions” and there you select the option “Do not share with”, there you just have to add users they don’t want them to see your connection time. This is done from the same section of “Last time and online”.
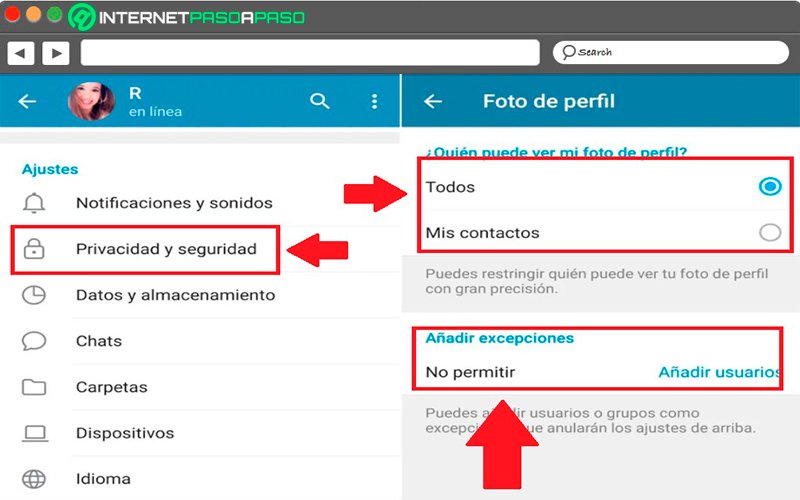
Choose who can see your profile picture
You also have the opportunity to select which users can view your profile picture, this will allow you avoid strangers can see the picture you have there.
For this you need to follow these instructions:
- The first thing will be to enter the “Settings” of the app.
- Then go to “Privacy & Security”.
- From there you must press “Profile picture”.
- At this point you must select one of these two options “All” either “My contacts”. In the case that you do not want it to appear to some specific users, then you can select “Add exceptions” and there “Add contacts”. From your agenda you must choose the people you want.
Metadata How much information can they contain and what are the risks?
The metadata means “Data about data” this refers specifically to information about a documentas can be the creation or publication date, modification date, author, publisher program among many others.
It can be said that these data are considered of great help when having to manage documents and their preparation processes. It is important to mention that the metadata can be found specifically in office programsthat is why every time you work in programs like Microsoft Word you will be generating metadatanamely, data on data.
An example of this so that you can understand all this better is the following:
- Naps creating a word document or with any another tool you are going to be writing a lot of information in it, but at the same time the application it will generate a series of metadata for said file.
- In these cases, it is responsible for collect details as it is the date the document was created, the name of the app you are using, the date it was last modified, among some other details.
Having the definition of this tool a little clearer, then here we show you what types of content can be collected in office documents:
- The document properties: Here it collects information about the author, title, number of pages, words, editing time, date of creation, time of last modification, among some others.
- Technical properties: Physical or virtual printer, the editor application and the version.
- Edition revisions: It will also show the history of previous versions.
It is important to mention that apart from the office documentscan also be collect metadata from other types of files as are the images.
Among the main metadata collected from images are the following:
- Image properties: Artist, description, title, geolocation, orientation, date of creation, date of last modification, its resolution.
- Technical properties: The brand and model of the photographic device, the editor application and version.
Taking into account all the data that many users collect, they will wonder Can metadata be an information leak? But the truth of all this is that this tool of data collection is considered as a information security measure, so it should be assumed that does not generate any type of risk for users.
Although it is true, at storing all these types of data can suffer some type of vulnerability, but it can be taken into account that the risk that this represents can be considered quite low, bearing in mind that the types of data they store can be considered to be of little relevance..
However, the level of risk that this represents will depend on the following factors:
- The criticality of information that has been provided about the environmental vulnerabilities.
- The amount of available metadata.
- The grade of relationship between each of the data collected.
Considering all this, it can be given as an example that there is a metadata where you have the Author and the Editor Application along with their version of the same document. In the case of author will provide us with information about the existence of a user in the environmentwhile the publisher application and version provides information about the existence of a software that belongs to the environment.
Based on all this, it can be said that the metadata they only take care of provide information that is related to the environment and not to the content of the document, so it could be considered that the metadata does not represent a leak of information for the user, but it allows to know a little about the environment of each document or file.
Learn how to delete your metadata to prevent anyone else from accessing it
The procedure for deleting this metadata from Windows 10 is very simple to do, For this, the first thing you should do is access said data, for that you must look for the file that has the metadata you want to delete and right click on it. In the options menu that appears there you must select the option “Properties”.
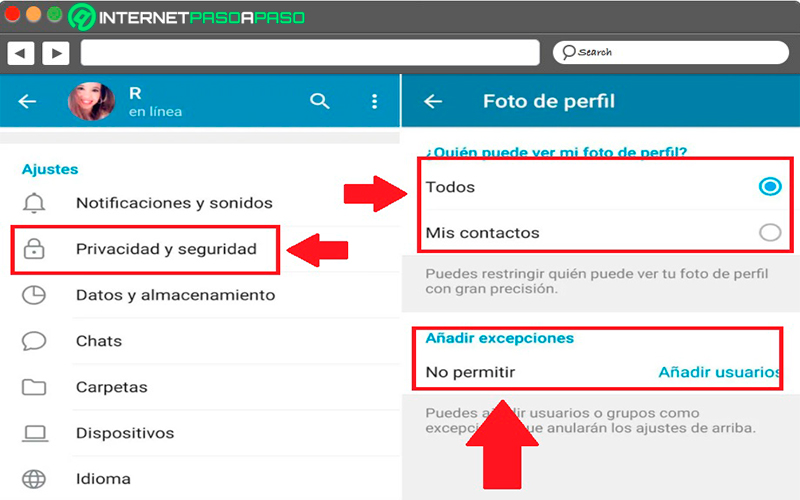
When the properties window has started on your screen you must click on the tab of “Details”, this will allow you display the basic metadata of the file. Here you must select the option “Remove property and personal information” this is in the bottom of the properties window.
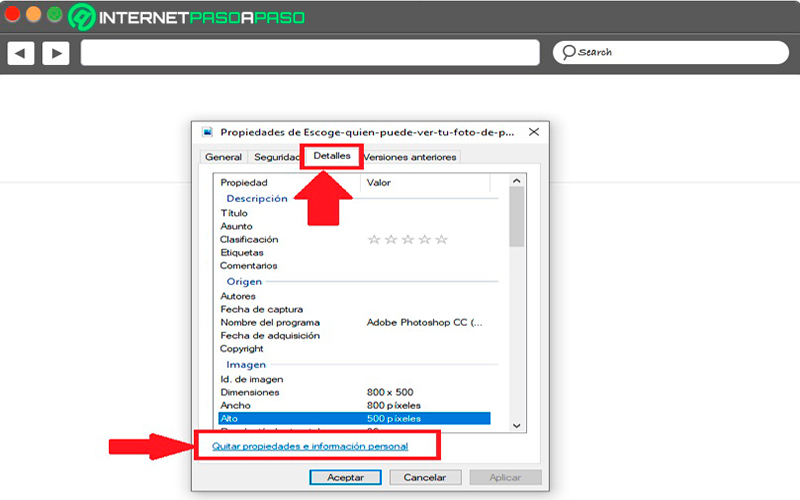
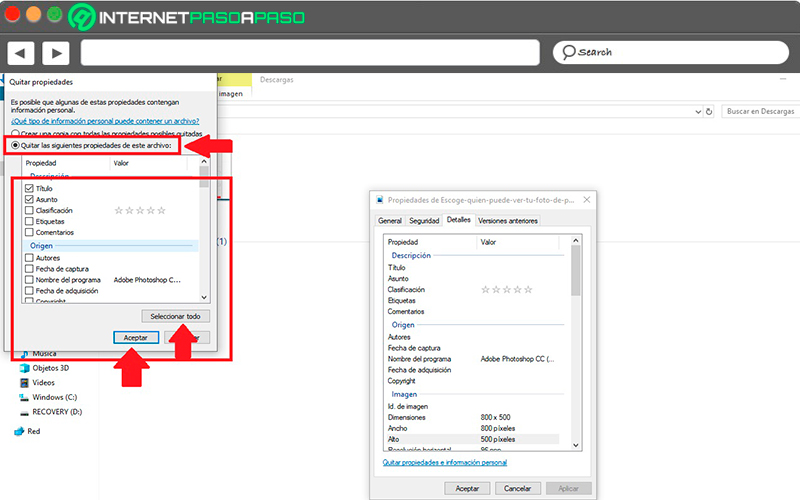
Clicking there will open a new window called “remove properties” in this case you must select the checkbox “Remove the following properties from this file”, here you can start to select each of the metadata you want to delete, you can also choose the button “Select all” and finally click on “To accept” for the changes to take effect.
List of the best tools to protect your privacy online that you should know
web security is one of the most important factors to take into account today, especially since every time security and privacy issues while browsing the Internet are greater. Whether when it’s done use of a social network, accessing a website, downloading files onlineamong many others types of activities that can be carried out on the network.
To try to curb the risks a little and increase your online privacy, here we show you the best tools for it, in this case follow the list that we will show you below:
Privacy Badger

Privacy Badger It is a google chrome extension that you can install completely freeit has the function of helping you to have a completely safe browsing at all times taking care mainly your privacy.
For this, it has a automatic function allowing them block invisible trackers, so once the tracker appears in three different web pages this prevents its passage. It is important to know that this type of tool will help you block any type of advertisement or threat that is presented on the network, so it is highly recommended to use it. In case you use as default browser Mozilla Firefox or Opera you can also use Privacy Badger.
desire.me
This is another one of online tools that you can currently find on the net, it stands out for its excellent performance and for its great utilityit performs functions of scan your email inboxis even able to analyze your oldest emails.
In the event that you receive any spam email then it will automatically detect it and it will send you an alarm about it. For a larger window it can be used without the need to have a network connection, so that your data will not be shared with anyonethus ensuring a maximum privacy and data protection at all times. So if you’re looking for a way to protect you then desire.me It is a very good alternative for you.
Cookie AutoDelete
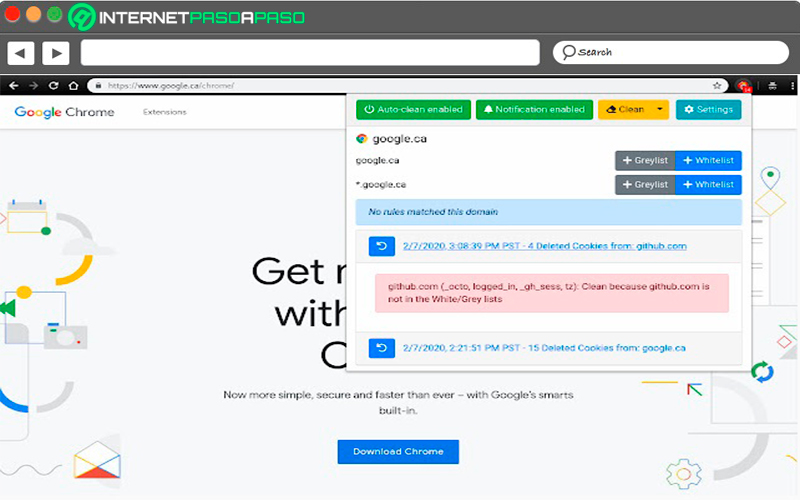
This is another extension that you will find available for both Mozilla Firefox browser What for Google Chrome, Its objective is to carry out the deletion of unused cookies each time the browser tab is closedso it will prevent any scans from being run on you.
So you can have more control over these elements through the settings you can choose which ones you want keep and which ones you want to deleteso you can deletedelete all cookies especially from those sites you don’t trust. Therefore, the main function of this extension is to prevent direct tracking on web pages.
DuckDuckGo.com

Finally we present this web browser, which is one of the most sought after and interesting when wanting browse with complete privacy, he himself takes care of block all kinds of trackers on web pages, preventing the user from being affected by any kind of tracking. Also offers ratings on the protection offered by the website you are visiting and in the same way use encrypted connections at all times.
Privacy