
Index:
UPDATED ✅ Do you want to know what a network topology is and which are the most used? ⭐ ENTER HERE ⭐ and Learn all about it ✅ EASY and FAST ✅
When we want to design a computer network to be able to connect different teams or work units, prior planning is necessary to know what resources or elements we are going to need when it comes to being able to interconnect each of the technological nodes.
A network topology is a mapping that is used to know how a computer network is designed and what structure it has. (this is for the case of those in which we need to carry out a computer audit). With this tool we will detect weak points to increase security, and thus generate an optimal result so that people or programs that we do not want do not enter.
When you finish reading this article you will be able to identify the different types of networks that exist todaywhich are appropriate for different situations and above all you will not spend money on equipment that is not necessary with your needs.
What is a network topology and what are they for in computing?
This tool is used to be able to analyze the weak points that it may have, study the changes and their consequences if one element is changed for anothercheck if the previously designed security schemes work well and verify the correct operation of each node.
We say that in order to see the layout of the computer network or technological elements, including the lines and nodes used in it, a network topology is the appropriate tool to carry out the aforementioned analysis.
There are two ways to view a topology: one from the point of hardware and the other is to study the signal that exists between work units.
What are the main types of network topologies that currently exist
Types of computer network topology, they are classified according to their location with respect to a server.
The main types recommended by network administrators are the ones detailed below:
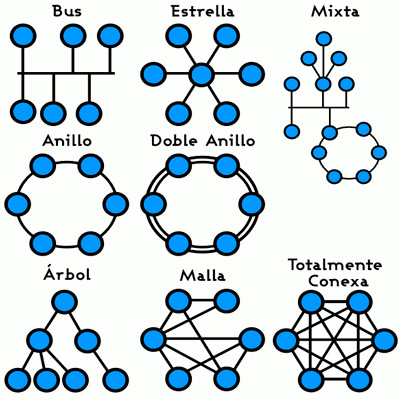
Point-to-point network topology
Also called PtP (point to point) either P2P (peer-to-peer). His analysis is characterized by simply studying two computers connected to each other. It does not present major complications since the level of interference is practically zero. It is ideal for small places where greater security controls are not needed..
linear topology
We can also find it in some places as “bus network topology”. It is defined this way because it is a common conductor that moves all the other nodes, graphically it would be a straight line which connects each of the computer terminals.
Circular computing topology
This type of computer network graph is also called a “ring” graph, and can be found in those designs in which each of the components are connected in a circular fashion, we can also locate a “double ring” version. This type varies because the interconnection is round trip.
star topology
We are going to find this kind of computer networks in those locations where all computing elements are directly connected to a central server. Its main axis is the server that has the action protocols for the different nodes.
Mesh network topology
Its name is due to the graph that results when a server has two or more connections, the difference that exists with a star or ring is that some elements or computers are not connected to each otherbut they are connected to other computers.
Fully connected topology
As its name clearly indicates, the main characteristic of this topology is that all work units are connected to each other, generating a great advantage when it comes to being able to quickly access information that they have at different link points. The main problem is precisely that anyone can access any machine.
Tree network topology
This computer networking review class corresponds to its resemblance to a drawing of a tree. It has the main characteristic that a central computer provides all the protocols that the different computers that are connected to the network have to carry out.
The great advantage of this type of network is its high degree of trust for the protection of information.since not all computers have direct access to the central server.
hybrid topology
As its name reveals, this type of mapping of a computer network is the conjunction of two or more topology classes. Its main advantage is that it can acquire all the elements that generate a profit from each of the different topologies, and leave aside those weak points that they have.
daisy chain
This class of topology, also called daisy chain, has as its main characteristic that each device is attached to the one next to it, that is, element 1 is connected to element 2 and this element is connected to another element that we can call 3, but 1 will never be interacting with 3 in a direct way.
What is the best logical map according to the type of network that you want to create? Applications
The best logical map will depend on the type of network we want to create. For these cases, we must take into account what the connections we have are going to be, we will have to verify all the nodes or hardware that we are willing to handle.
For example, a switch or an integrated hub are very necessary pieces of equipment, but they have different technical capabilities when it comes to taking action.

Once all these factors that will help the communication protocol have been determined, we will be ready to decide what will be the type of computer network that we are going to design..
Many network administrators opt for the simplest ones to avoid conflicts between those elements that make up the interaction set, but many times you cannot choose the easiest one, rather you have to choose the most convenient according to our transfer tasks.
The most used, according to our analysis, is the network topology “bus” and also that of “mesh”.
bus network topology
This can be used in businesses that are not very big and also in home networks as it provides a quick solution when you want to expand the network.
Use of mesh network topology
While for the mesh topology it is used in the opposite case to the bus network, It is used for those large companies in which there are many nodes that need to communicate with each other. and they depend on different databases that need to be worked on by different users.
networks