
Index:
UPDATED ✅ Do you want to protect your personal information and improve your privacy on the Android Internet? ⭐ ENTER HERE ⭐ and discover how to do it ✅ EASY and FAST ✅
Privacy is currently a benefit. The times when it was a right seem to be in the past, since both advertising agencies and government entities are on the lookout for our data. They have no qualms about paying thousands of dollars to learn about our online habits.
Being mobile phones the devices that we use the most to do basically everything; from checking our social networks to buying with our credit cards, It is of the utmost importance that we begin to take their privacy more seriously..
In this article we are going to teach you how to make your Android mobile a real private fortress in which you will have total control over your data. We will teach you the main vulnerabilities of the system and also how to deal with them so that your mobile is a complete bunker.
Why is it important to maintain our privacy online?
Most people have the mistaken belief that “No one would be interested in my information”because they don’t believe enough “important” for someone to want to pay for it. There is nothing further from reality.
Little by little, the Internet has become one of the largest platforms for doing business in the world, moving an impressive amount of money. In today’s scenario, everything is valuable online; from the person who spends the most to the person who simply uses it to view their Instagram or Facebook profiles. This makes each and every one of us who connects “important”, much more so if we do it from an Android.
The reality is that in most cases, companies and government entities are not interested in our identities, that is a fact. However, our online habits are very interesting for them.
Have you ever thought about how interesting it is for a pharmaceutical company to know what diseases you have searched online to find out if you have them? either How interesting is the type of sneakers you are looking for for a clothing brand? All this can be very valuable to them because it is very important information to determine if you are a potential buyer for their products or not.
All this information you are knowing right now while reading this from your smartphone and there is nothing you can do to avoid it as long as you have that poor configuration and data protection on your device.
Identifying the problems What are the main privacy vulnerabilities in Android?
If you have already understood how important it is to have control over your data on your mobile device, we are going to mention all the each of the vulnerabilities of your Android operating system.
The operating system
The Android system is one of the most secure in mobile up to a certain point, but it has some problems. The first of them is that it basically comes configured to record each one of your movements while you use it. The applications to organize your routine leave a history of your activities that are recorded in an online database.
That is the main problem that you will have to deal with in your Google mobile operating system, so you will have to put your hands to work to solve it.
IP addresses
The Internet is wonderful, but we must not forget that it was a technology created by the military, so it has features that are still designed to track and monitor people. A clear example of this is the IP addresses.
An IP address is a number divided into octets that is used to identify a computer within a network. While this may seem harmless, the reality is that there is more risk than you think because anyone who has access to that address, has the ability to identify your computer and track it to know exactly where in the world you are connecting from.
IP addresses are visible to the portals you visit and also to anyone who has enough skill to intercept a communication between your computer and said website. The latter is unlikely, but we will give you an example that can compromise your privacy..
An internet domain costs less than €5, and a cheap hosting service can cost even less than €10. This means that anyone with less than €50 can create a website. ImmaImagine that a person with the intention of blackmailing others creates a website like sebumand when someone connects to it, they get your IP address, and therefore also your home address.
The address of your home and that of your loved ones (father, mother or children) will be available to a person who could threaten you, blackmail and put thousands of ideas in your head without even being really close to hurting you, but with the mere idea of it it can already scare you enough to take money from you.
The Navigator
The browser we use stores a lot of information about our online habits, so it is an important aspect that we must optimize to guarantee privacy in all senses. The The problem with most browsers is that they are very leaky and your browsing history is very easy to breach..
The cookies
Cookies are certainly not a big problem for the privacy of your data, but they can be used to create a history of your online browsing habits and later create a complete fingerprint to identify your device. Also, think about it Why would the portals warn of their use if they were so good? It is evident that there is a latent risk and therefore your authorization is needed to be able to install them on your computer.
the scripts
The scripts are a real problem as it is known that they can be used to track and identify your browsing habits. These in that sense resemble cookies but are much more powerful. The problem with them is that they are used by basically 80% of the portals on Internetso to do without them would be to stop viewing a large part of these websites.
the histories
Lastly, there are the histories. On Android, the vast majority of Google apps keep a complete history of your activities. All of them are very useful to improve your user experience, but some abuse this and can be a real problem for the privacy of your data.
The two histories that you should take care of the most are; the browsing history, in which each and every one of the portals you visit on the Internet are recorded, and the location history, that records all the places you go through your city in real time while you have the GPS of your computer activated.
Steps to increase our online privacy and protect our personal information on Android
Once all the vulnerabilities of your Android system have been detected, it’s time to teach you how to solve them all and even apply other configuration tips to make your device a real private fortress.
Operating system configuration
As we mentioned above, Google’s mobile system has certain vulnerabilities that we must face and solve. The good news is that you do not need to be an expert to apply them all and we are going to show you that next..
The screen lock method comes first. Fingerprint sensors are currently very fashionable, but they have their risks too. The main one of all is that once the mobile is unlocked, anyone can register her fingerprint on the device, and I can assure you because my girlfriend has one on mine.
In addition, another thing that is curious is that if you cannot enter with the sensor, it will be enough to enter a 4-digit code (security PIN) to unlock it. For this reason the best thing you can do is simply disable the fingerprint lock.
Which you can do as follows:
- Enter the configuration of your smartphone and position yourself in the section of “Privacy Y Location” and once there you must make touch in “Fingerprint”.
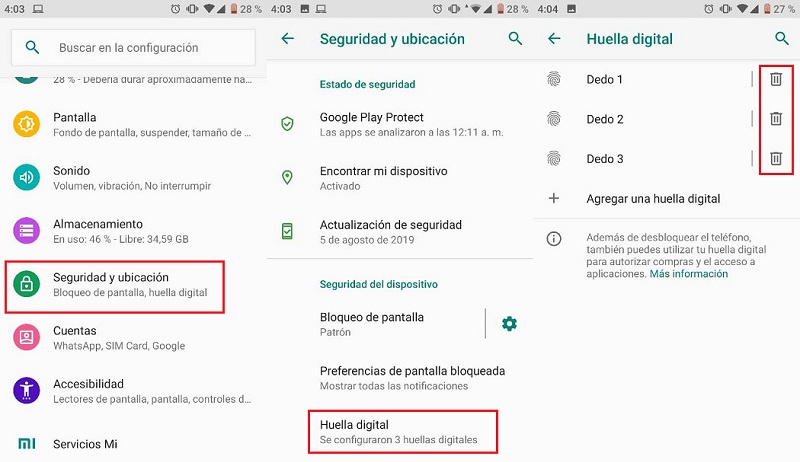
- In this section you will see all the fingerprints registered in the device, what you should do is simply touch the trash can to the right of each footprint to delete it and the job is done.
Now, what is the safest blocking method? Well, without a doubt, it’s a alphanumeric password that combines all kinds of characters to make it more difficult to crack.
The next step is to encrypt or verify that your phone is encrypted, so that communications on it are also encrypted.
To do this you simply have to follow these steps:
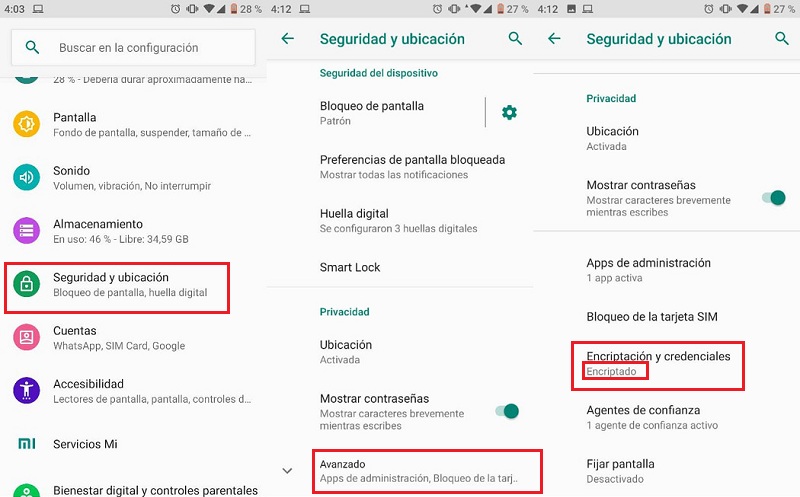
- Enter the configuration of your mobile and go to the section of “Privacy and location”. Once in it, go down to the end and touch the “Advanced”.
- After that you should look for the option “Encryption and Credentials”. If under it it says “Encrypted” It means that the mobile is encrypted. Otherwise you must enter it and make touch in “Encrypt” for the process to take place.
At this point you have already solved the most serious security problems of an Android, at the operating system level of course. But the mission is not over yet. The next thing is to get rid of Google’s activity control, which is a colossal data consumer and basically stores everything you do on your mobile.
Therefore you must go to Google’s MyActivity and disable it for all your devices:
- Enter this link from your mobile or computer.
- Go into “Activity controls of your account” and in this section you can disable all the trackers that Google has put on your device.
Encrypt the IP address
Now that you understand all the information that they can obtain through your IP address, you should proceed to take much more care of the portals you browse online from now on. In this step we are going to teach you how to encrypt your internet protocol address.
For this you will have to set up a VPN on your device. The first thing will obviously be to choose a good supplier. We choose VyprVPN which is one of the best, but in general you can choose any other provider of your choice. without further ado, what you must do to configure a virtual private network in Android is the following:
- Go to the settings of your Android and enter the section of “Internet and network” to then go down to the end and make touch in “Advanced”.
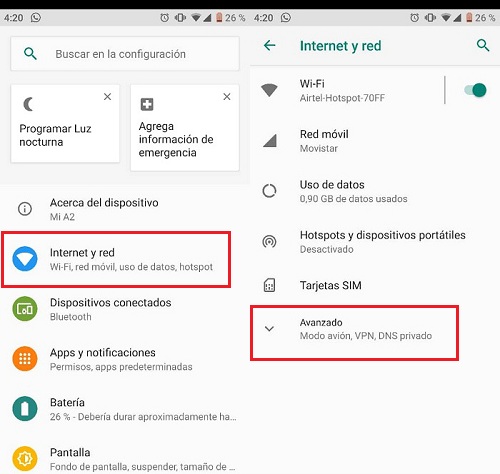
- At this point you should enter “VPN” and then touch the sign “+” which is in the upper right corner of the interface.
- A registration form will appear in which you must put the name, the server (below we leave you the complete list), the username and the password of your account. VyprVPN.
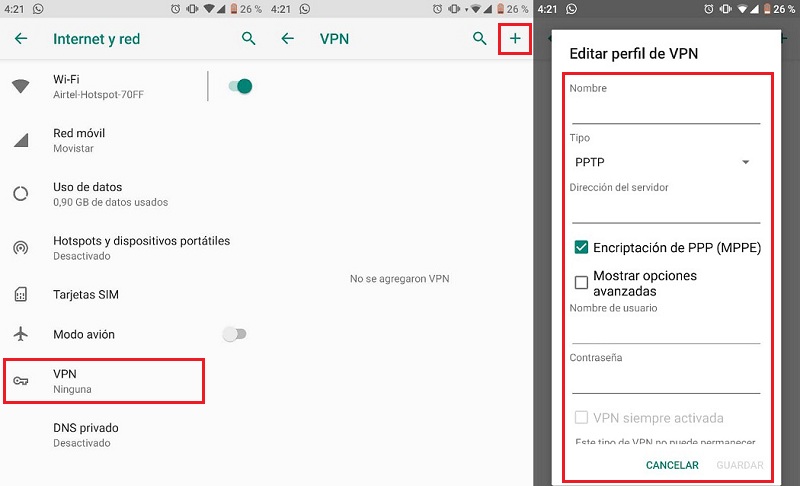
- After saving the new VPN simply activate it and all your communications will be encrypted online.
The VyprVPN service has multiple servers and You can choose the one you like from the following list that we share below:
| VyprVPN Server | hostname |
|---|---|
| Los Angeles, CA | us1.vpn.giganews.com |
| Washington, D.C. | us2.vpn.giganews.com |
| Austin, TX | us3.vpn.giganews.com |
| Miami, FL | us4.vpn.giganews.com |
| New York City, NY | us5.vpn.giganews.com |
| Chicago, IL | us6.vpn.giganews.com |
| San Francisco, CA | us7.vpn.giganews.com |
| Seattle, WA | us8.vpn.giganews.com |
| toronto | ca1.vpn.giganews.com |
| amsterdam | eu1.vpn.giganews.com |
| Stockholm | se1.vpn.giganews.com |
| Hong Kong | hk1.vpn.giganews.com |
| London | uk1.vpn.giganews.com |
| Paris | fr1.vpn.giganews.com |
| Frankfurt | de1.vpn.giganews.com |
| Copenhagen | dk1.vpn.giganews.com |
| Zürich | ch1.vpn.giganews.com |
| Moscow | ru1.vpn.giganews.com |
| Luxembourg | lu1.vpn.giganews.com |
| Bucharest | ro1.vpn.giganews.com |
| Singapore | sg1.vpn.giganews.com |
| Dublin | ie1.vpn.giganews.com |
| Kuala Lumpur | my1.vpn.giganews.com |
| Rome | it1.vpn.giganews.com |
| Madrid | en1.vpn.giganews.com |
| tokyo | jp1.vpn.giganews.com |
| seoul | kr1.vpn.giganews.com |
| Oslo | no1.vpn.giganews.com |
| istanbul | tr1.vpn.giganews.com |
| Helsinki | fi1.vpn.giganews.com |
| warsaw | pl1.vpn.giganews.com |
| Lisbon | pt1.vpn.giganews.com |
| prague | cz1.vpn.giganews.com |
| Vienna | at1.vpn.giganews.com |
| Brussels | be1.vpn.giganews.com |
| Vilnius | lt1.vpn.giganews.com |
| sydney | au1.vpn.giganews.com |
| melbourne | au2.vpn.giganews.com |
| Perth | au3.vpn.giganews.com |
| Jakarta | id1.vpn.giganews.com |
| Auckland | nz1.vpn.giganews.com |
| Hanoi | vn1.vpn.giganews.com |
| bangkok | th1.vpn.giganews.com |
| Reykjavik | is1.vpn.giganews.com |
| Manila | ph1.vpn.giganews.com |
| Saint Paul | br1.vpn.giganews.com |
| Mexico City | mx1.vpn.giganews.com |
| Buenos Aires | ar1.vpn.giganews.com |
| Bogota | co1.vpn.giganews.com |
| Saint Joseph | cr1.vpn.giganews.com |
| City of Panama | pa1.vpn.giganews.com |
| Taipei | tw1.vpn.giganews.com |
| manama | bh1.vpn.giganews.com |
| Doha | qa1.vpn.giganews.com |
| Riyadh | sa1.vpn.giganews.com |
| mumbai | in1.vpn.giganews.com |
| Dubai | ae1.vpn.giganews.com |
| Tel Aviv | il1.vpn.giganews.com |
| Sofia | bg1.vpn.giganews.com |
| shaan | li1.vpn.giganews.com |
| Algiers | dz1.vpn.giganews.com |
| Cairo | eg1.vpn.giganews.com |
| San Salvador | sv1.vpn.giganews.com |
| Athens | gr1.vpn.giganews.com |
| Riga | lv1.vpn.giganews.com |
| Male | mv1.vpn.giganews.com |
| Majuro | mh1.vpn.giganews.com |
| Macau | mo1.vpn.giganews.com |
| karachi | pk1.vpn.giganews.com |
| Bratislava | sk1.vpn.giganews.com |
| Ljubljana | si1.vpn.giganews.com |
| Kyiv | ua1.vpn.giganews.com |
| Montevideo | uy1.vpn.giganews.com |
Choose a safe browser
The next mission is to get rid of your less secure browsers and start using one that really guarantees data encryption and does not have IP leaks. In this sense you have two options little known by most users. But ideally, you should use one of the following browsers:
- Tor Browser: The Tor project is one of the few that focuses on ensuring the security of user data and has an excellent browser that comes with a configuration that makes it a real safe. If you want to install it, you must download the Tor APK to Android and disable unknown sources on your mobile.
- brave: this is a new project that last year generated very good impressions for the speed of navigation, the level of privacy and the savings in data consumption obtained with a browser that blocks all ads. You can download it directly from the Google Play Store here.
Choosing one of these two browsers will have solved three other details such as cookies, third-party scripts and ads, which also represent a threat to your privacy.
Delete the histories
Finally, it is important that you get rid of the records that your mobile saves. Browsing history cannot be turned off, but it can be deleted regularly on all browsers. So this is a habit that you will have to take to do it yourself manually.
On the other hand, location history can be easily deleted and disabled. to deactivate it you must go to the section “Location History” from your Google account. Once there, you simply have to deactivate the option on the relevant switch and that’s it.
List of the best applications to keep our privacy to the maximum on Android
By following the steps that we have taught you, you can increase the privacy of your Android device to the maximum. Now, to make your life easier in this regard, We present a list of applications that will help you increase the security of your smartphone:
LastPass
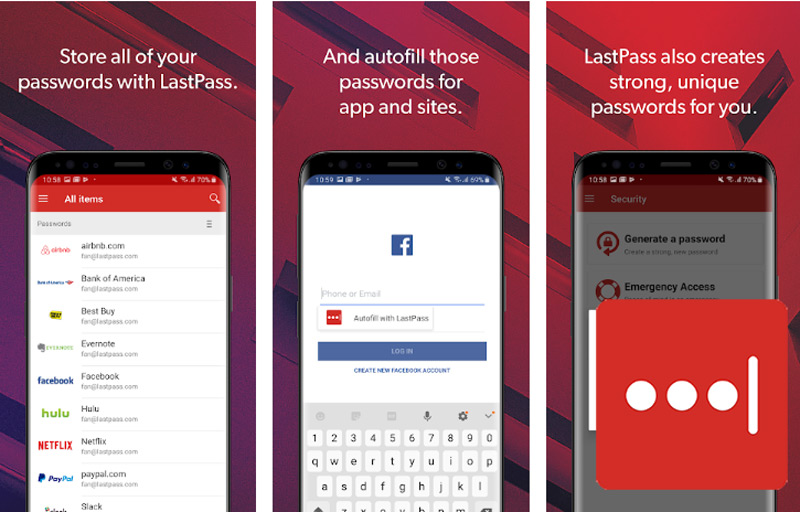
A password manager like no other you’ve seen so far. It is multiplatform (it works for mobile and desktop), which means that you can manage from it each and every one of the access codes to all your accounts. With a very sober design and pleasant interface, this app will undoubtedly become your best ally.
authy

This is an excellent option to manage your accounts with two-factor authentication. You can link to it services such as UpHold or PayPal digital wallets, investment brokers or cryptocurrencies and other digital services in which you have money invested or very important data. Also, all access codes will be encrypted with high-level techniques and you can protect them with a fingerprint or password.
CM Security
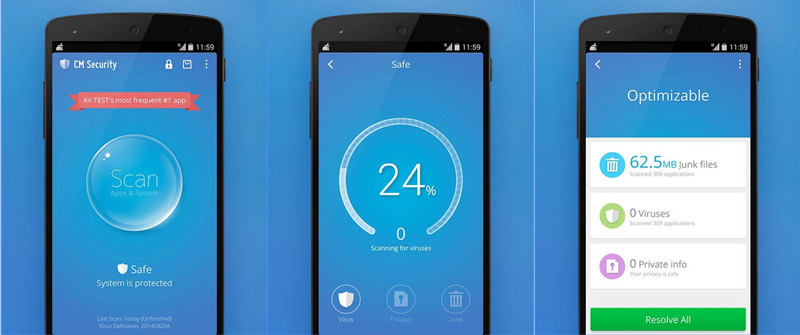
This is one of the most powerful applications when it comes to security. It’s a real Swiss army knife from which you’ll be able to block applications with a secret code, manage your passwords and optimize your mobile’s performance and battery life. Easy to use and officially available on the Google Play Store.
Inside
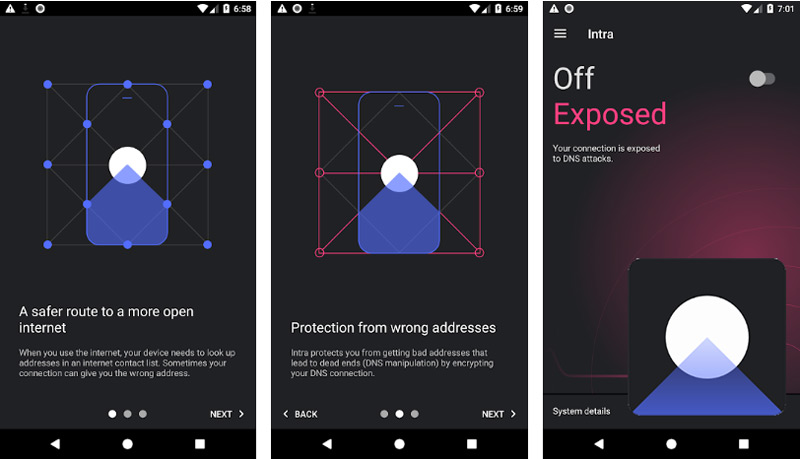
This is an application that many require to be factory installed on all Android devices since its developers are in a way closely related to Google. This is a simple switch that you activate to prevent government institutions from manipulating your server’s DNS to track you and obtain information about your online consumption habits.
Outline
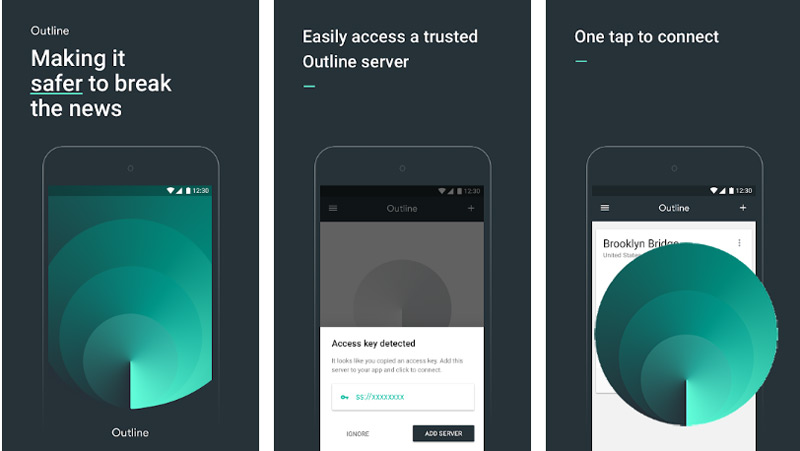
This is a sister application to the previous one, which also offers effective data protection and digital security solutions. To start, with it you can browse the internet and your browsing data will never be recorded in any virtual memory. Added to this, we can be sure of its high-level data encryption techniques.
With these apps and following the tips mentioned throughout the article, you can turn your Android smartphone into a secure ecosystem for your data.
Privacy