
How many times have we not heard that any company, web platform or team has been attacked by cybercriminals? Surely a lot. This is because an attacker managed to violate the system and steal his data. Commonly the possibilities they have to carry out this crime is taking advantage of a weakness in it.
These criminals often find it very easy, because they use these small mistakes to infiltrate, the famous Exploits being their favorite tool. But what are they really? It’s basically a program or code that takes advantage of a security hole.
As you see this term is related to threats and attacks, reason why we should know very well the consequences that it can generate and how we can avoid them to protect our backs. In this article below we will give you all the details you need, since for us your security is important.
Index:
What are exploits and what do they do in computing?

This word has an English origin and means to exploit or exploit; in computer science it has a similar meaning, but nevertheless, we speak of a piece of software that uses an insufficiency to have unforeseen behavior within of an information system.
These tools, as we already mentioned, are very useful for cybercriminals, since they can use vulnerabilities in very popular programs. The same are able to obtain administrator permissions or be able to take control and evade security measures to generate an infection.
If we imagine this in another context, we could represent the system as the model of a lock, where if it has a flaw in its design it would allow us to create keys (exploits), to open it and therefore access what you are trying to protect.
The purpose of this is to destroy or disable the system to which the attack is made, when its measures to perform activities that are beneficial to third parties are violated.
How does an exploit work to detect vulnerabilities in our computer equipment?

Mainly we must keep in mind that this can reach our computers in different ways, because usually are not only actions generated by hackers, but also by security experts, reason why the one who knows very well what they do.
Sometimes this can come from its own consequences, being the fact that we open emails of suspicious origin, click on malicious links, enter dangerous websites, etc. Other times you may arrive with an ad harmless thrown on a page.
As software is created and developed by us humans, it is very common that they may have errors in the codes; These are usually called bugs. That is why when a mistake or vulnerability is found in an email software, when making a request to the server for example, a hacker could create a file to exploit the error and access user information with ease.
Exploits and malwares How are both terms related?
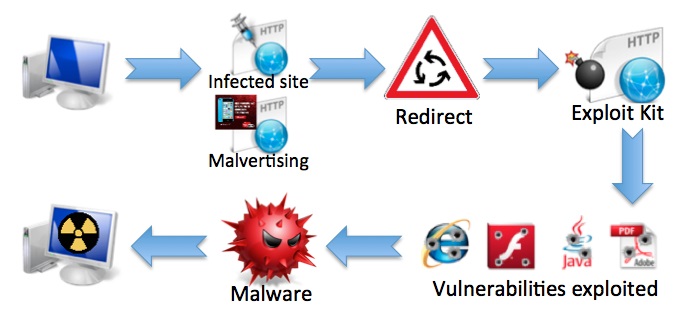
When we talk about viruses, we associate it directly with all kinds of malicious software, but we must know that today these are little dangerous pieces within the threats that can be found on the network.
Currently we can find different terms that seem to be familiar, such as exploits and malwares, but we must be clear that these expressions have different functions.
A malware is malicious code, which can generate any kind of problem on our computers to cause damage and take control of its operations. It is made up of Trojans, ransomware or worms. Although it is not intended to damage the hardware of the equipment, if it steals, deletes and encrypts your data.
On the other hand, exploits are programs that have the purpose of exploiting the errors that exist; as we have said, they take advantage of the errors of design or programming of a certain system to enter the .
As we can see, there are differences between one and the other, although both can be used to commit any kind of inappropriate act. The exploits by itself is not malicious, criminals use it as an extra component within their malicious code to obtain illegal entry. Likewise, many malwares use exploits to achieve their goal and take control of the system.
What are the types of exploits that exist and how do they differ?
There are several types of exploits, each of them is important that you know them, since these are based on the different forms of access that are achieved and according to the objective of the attacker.
The following are distinguished within them:
- Remote Exploit: It is one where it is not necessary for the attacker to be physically in front of the computer that wants to do the damage. Which means that you can run it from any type of local network where you are connected, you can even do it from an Internet connection.
- Local Exploit: It is done when The attacker is in front of the computer he wants to attack. Although it does not need to be physically present, it can also be done remotely.
- Exploit client: In this, the attacker must be in front of the computer physically . It is currently one of the most common, because an email can send a malicious attachment, and once it is downloaded it can be executed.
Tips to protect you from exploits and prevent computer attacks
Once explained what this program means, what are its types and how they work, you can then apply certain options and tips to prevent it from affecting the development of your operating system.
It should be noted that installing a tool that tells you when there is any type of threat is very important, as this will help keep the equipment in perfect condition.
Take note of these tips we offer you:
Keep all our applications and systems updated
As we have said, these take advantage of the security holes of our computer, that is why we must close them immediately. For this reason keep our entire system and what it contains updated to the latest versions are helpful, this to prevent it from being exploited by attackers.
The updates not only incorporate improvements in functionality but also include corrections that serve to close possible holes.
To make sure they are up to date and not miss an update, we can use an administrator to keep our security safe while making automatic adjustments.
Decrease any type of exploit effect that can be executed without our permission
Sometimes those who create the applications do not make updates to solve any type of problem, reason why they can use different types of instruments to avoid any type of virus that could damage the operating system and thus get an appropriate response.
Having a solution at hand is essential to achieve and block any type of threat that does not allow any vulnerability in a file.
Install an antivirus
Nowadays it is essential to install a good antivirus that is constantly and automatically updated, with the intention that your computer has the security it needs. Keep in mind that you must use one that is capable of detecting and blocking exploits; on our part we recommend ESET Smart Security, but if you want to see other options you can go to the following link to know the best antivirus .
Install backup measures
You should always install programs that provide the necessary security to your computer, because hackers can use these expiations in order to enter your computer whenever they want.
Be careful of the attached files
Every time you enter your email and need to open an attachment it is essential that you verify that it does not come from any source with risk. This is because you can unconsciously install any type of file malicious that may harm your computer.