
Index:
UPDATED ✅ Do you want to prevent people from spying on you and stealing your information while you browse online? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
Currently Internet is surrounded by a danger series what can affect user privacyall this is due to internet surveillance that currently exists, where all online activities, online and offline data are being spied on and monitored by government agencies, ISPs and cybercriminals.
All this has made security while browsing the web more and more compromised, since it seems that more and more people have less confidence and security mainly in terms of your personal data and bank accounts. Although it has been found that in many countries the majority of Internet conversations are being spied on.
In this way, most users nowadays look for different methods and alternatives that allow them to slow down all this a little, with the aim of avoiding being monitored all the time and above all for protect your digital integrity. This is how here we are going to teach you a little more about what all this is about and how you can avoid it, for this, follow in detail everything that we are going to teach you next.
What is cyber surveillance and what risks does it represent for me on the Internet?
The cyber surveillance refers to monitoring the activities that users carry out on the Internet, as regards the online activity, online and offline data, and monitoring and logging of Internet trafficall this by government agencies and institutions for the purpose of protecting national security, although many of these cases can be used to carry out malicious purposes.
In this way it can be said that internet surveillance it is provoked by most governments and currently applied in many countries. Recently organizations like the United States National Security Agency (NSA) has been involved in all this, but even in other countries governments have also been involved in espionage activities on its citizens, all this is justified by alleged reasons of national security.
Some of the justifications for this type of surveillance is that it is used to collect data on terrorists and criminalsin order to prevent these people from carrying out their malicious activities. But the truth of all this is that these types of activities are currently being used to invade the privacy of users online, this is how all this can represent different risks to citizens.
Some of the risks are as follows:
- One of the most common in all this is the kidnapping of files on hard drives and mobile devices through the use of malware.
- You can also generate a identity fraud of the users.
- The phishing to usurp the digital identity of individuals and the theft of personal data.
- The lack of privacy for the user at the time of navigate in Internet.
- communications and personal data of users may be at risk when being spied on by private companies or institutionssince all this information can be used for malicious purposes.
Taking all this into account, here we are going to leave you some of the most famous Internet surveillance agencies in the world:
- Canadian Communications Security Establishment (CSEC).
- UK Government Communications Headquarters (GCHQ).
- Russian Federal Security Service (FSB).
- The Australian Directorate of Signals (ASD).
- New Zealand Government Communications Security Office (GCSB).
In this way, the different governments they use technology companies in order to facilitate your access to private information. In the event that these companies do not want disclose your customers’ private informationin many cases you have no choice, as agencies like the NSA you can force them to comply with your demands.
In this way, large technology companies such as Google or Facebook They may also be forced to share information with the government and that way reveal certain types of data for what is national security work.
Should I allow companies to know information about my online preferences?

Can allow or not espionage of certain companies about the different activities carried out on the web is somewhat complicated. It must be borne in mind that the Internet spying, identity theft, or theft of private information are a crime recognized and prosecuted by law, but in these cases these types of espionage are mostly made by companies government in order to provide greater national security and thus be able to detect any type of danger that may affect the nation.
In this way, even though users do not want to be monitored this will be impossible to controlthe only thing that can be done in these cases is to take some security measures that can reduce this type of risk. This is how many people try to get rid of this espionage by installing barriers of security or antivirus. However, it is very possible that despite these measures the Government wants to access your information.
In the case of USA Congress passed a Protection Act Law Y Sharing Cyber Intelligence (CISPA), a law that has also been known as big brotherwhere large American companies are forced to share data with the governmentamong some of the data that must be delivered are chat conversations, personal information, emails among many others.
All this has been classified as a government abuse of power to spy on citizens without their authorization. Therefore, no person should allow companies to know their online preference informationfor this you must take some necessary measures that we will teach you later and that may help you to protect your personal information a little.
What are the main methods used to do digital surveillance?
Currently the PRISM program is one of the most discussed since it allows theto NSA to be able to collect data from the servers of service providers of USA, where you can include large companies such as Microsoft, Facebook, Google, Yahoo, Appleamong many others.
Therefore, any information that is stored on someone’s servers is in danger of being stored and analyzed by third parties. There are also other programs like FAIRVIEW and STORMBERWboth take care of collect all the traffic which is directed through a gateway or router specific.
In any of the cases, a wide variety of information can be found that could be collected, such as the navigation data and recorduntil emails, videos, chats, photos and file transfers. In the case of XKEYSCORE is one of the most recent programs that have been included and that is sure to be in the list of nsa Surveillance, which is related to secure distributions of Linux or virtual private networks like the VPNs.
Keep in mind that this is not only applied by the United Kingdom and the United States, as there are many other countries that collect data from citizens around the world. In this case they may not read directly citizens’ e-mails, but it is possible that they track your browsing activity and habits in social networksthe apps they use, and possibly related information from their friends.
Keep in mind that all of these data is collected by private companies as well as through social networks, but that certainly all this data ends up in the hands of the government, either through programs such as PRISM or through the court orders for them to deliver the collected data. All this happens also for internet providers, who on many occasions must also provide the Government with all the data collected through their services.
Learn about the most controversial cases of online surveillance that have been uncovered
Several have now been discovered online surveillance cases who have placed more than one in a constant alertsince all this has exposed several types of spying on citizens around the worldwhich undoubtedly worries most people.
That is why we are going to show you some of the most controversial cases that have been found today:
Snowden and NSA
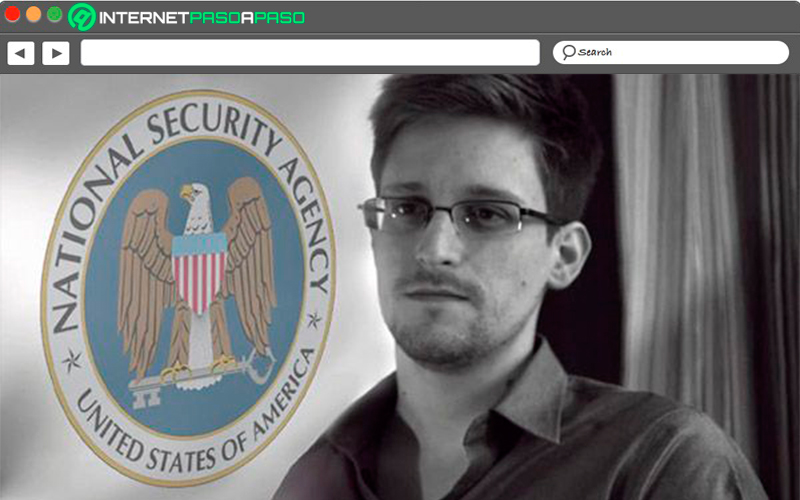
Edward Snowden went from being a United States spy agent to become one of the most wanted men in that country. And it is that the case that involves Snowden has become one of the most outstanding the history of mass espionage on the Internet. It’s like this American citizen and former CIA agent revealed methods of investigation and mass surveillance by the United States Government.
According to the revelations of former CIA agent, the Government He came to spy on heads of state and multinationals. But Who really is Snowden? He is a computer scientist from North Carolina who started out working as a security guard and ended up working on the premises. agency secrets NSA National Security, where he would later start working on the INC as an expert in computer security.
In 2009 he left the CIA and start working in a private consultancy within NSA facilities in a US military base in Japan. It’s like this US citizen revealed to washington post newspaper violations of security and privacy by his Government, based on “I cannot in good conscience allow the United States government to destroy the privacy and freedom of the Internet and the basic freedoms of people around the world.
I don’t want to live in a secret society where everything I do and say is recorded.” Snowden I travel to Hong Kong, It was there that he first leaked the documents where, according to the United States would have required the verizon company to deliver all telephone data to the FBI. In the same way, he granted an interview to The Guardian and Der Spiegel.
Where he stated that both Germany and Israel would also be involved in surveillance projects and even behind the creation of a cyber virus targeting suspicious computer systems to transmit information against these countries. After all these revelations and some other Snowden He has been considered by many as a hero who risks a lot to defend his convictions and protect physical and psychological harm that other people may suffer.
While for other people he is considered as a narcissist who intends to attract attention to himself. Since said revelations he has become a persecuted of the United States who have filed a lawsuit for treason against the country. This is how he since then he had to leave the North American territory to avoid being arrested.
Massive extraction of intimate photos of celebrities
Without a doubt, this was one of the cases that generated the most controversy regarding the online security and surveillance and it is that a large number of celebrities suffered a photo theft intimate that were later sold in an American forum known as 4Chanwhere the person or people who posted all this content wanted to change it to Bitcoin payments.
In this case the attacker posted several photos with a list of celebrities where he had his intimate photographs, and where he points out that in the coming days he will publish new images and even intimate videos of many of them. In this case, there was talk of up to a thousand actresses, models and singers whose photos had been stolen from their own online albums.
In in 2012 he was sentenced to 10 years in prison for the hacker who accessed the bills on-line of Mila Kunis and Scarlett Johanssonwhere he took intimate photographs of both and later they were published on the Internet. These have been some of the most relevant cases in terms of theft of intimate photographs of celebrities.
Adrian Lamo: The Nomad Hacker

Adrian Lamo has been known as the nomadic or vagabond hacker by many, since he himself had as a main activity visit different cyber cafes and places with public access to the Internet to carry out cyber attacks. It was like this young man Adrian Lamo carried out computer attacks through the vulnerabilities presented by the computer security of large companies such as Bank of America, Yahoo! Or Microsoft.
Thus, for the year 2012, Adrian Lamo He was sentenced to six months of house arrest and two months of probation for stealing the data of more than two thousand subscribers of the newspaper New York Times. Furthermore, he went on to become even more famous after ratting out the Private Bradley Manningwho would have leaked information from the army and Secretary of State of the United States to Wikileaks being sentenced to 35 years in prison.
Vladimir Levi known as “The hacker of St. Petersburg”
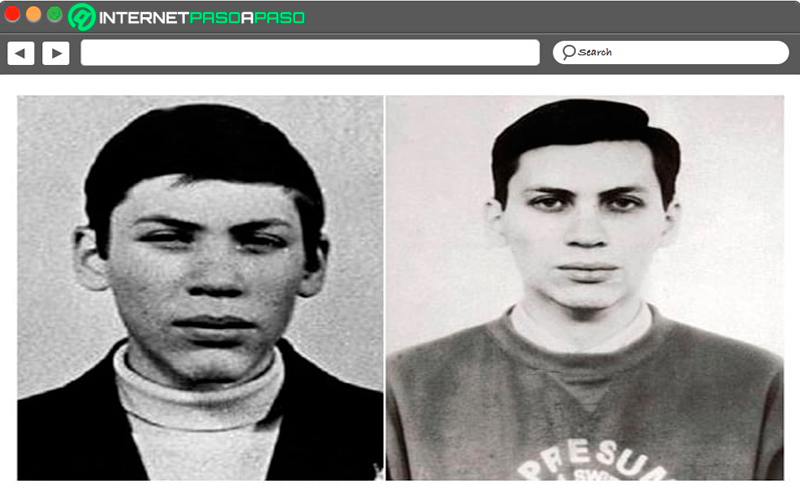
after finishing the Cold War, the City of St. Petersburg became one of the main points of hacking around the worldall this was very well used by Vladimir Levy to carry out a data mining and money from different bank accounts.
That was how for the year 1994, he managed to get more than 10 million dollars of customers Citybank. However, after this he was arrested by Interpol and the following year was sentenced to three years in prison and a fine of more than 240 thousand dollars. Furthermore, he was forced to pay back all the money he had taken from different clients of Citybank. So far it has been estimated that Levin could be linked to the Russian mafias.
Learn step by step how to protect yourself from cyber surveillance to protect your privacy
Taking into account that cyber surveillance can become a problem for you and for everyone, it is very important to be able to take some necessary measures that allow you to avoid all this, in this way you can take a little more care of your security and privacy. That is why here we are going to teach different methods that will help you protect yourself a little more from all of this.
To do this, follow the list that we will show you below:
Hide browsing history
You should keep in mind that each of your movements on the internet remains registered in your web browsereither from the pages you visit to the time you spend browsing each one of them, on many occasions the information you write in it and your password They are also stored by the browser, all this in order to provide you with a better experience the next time you use it and so you do not have to re-enter said data or information.
Without a doubt, if it is a personal computer all this can be very useful, since your experience can be much more effective. But everything changes if it comes to a public computer or that is shared with someone, since in this sense privacy is lost a bit. Therefore, an excellent option for this is hide the browsing history or web pages that are visited.
In fact most of web browsers today it has the resources necessary to allow users to easily access and manage all this to get a increased privacy. The reasons why you want deregister the pages accessed are manystarting with this will prevent third parties from seeing the trail you leave while you browse, which allows you to have greater privacy and security in your data.
encrypt email
Undoubtedly the e-mails have become the number one target of most malicious people who seek to extract different types of information and data through this medium. All this is due to the fact that today most communications on the Internet are carried out through emails, where millions of private data from both people and companies are shared daily.
All this becomes much more susceptible when it comes to confidential information such as passwords, bank details, contracts, among others. For this reason, today it is essential protect all this shared information by this means, either for the emails sent as received and the best way to do it is by encrypting emails.
Thus, information encryption thus becomes one of the most necessary processes to prevent unauthorized persons can read other people’s emails and even manipulate them to modify their content at your convenience or to extract some important data from there.
Encrypt chat conversations
Surely you have heard about what it is encryption, a term that is associated with various contexts, but mostly that refers to the mathematical process of rendering a message unreadable, except for those people who have the key to decipher it and thus make it readable. Therefore, it is a technology that allows to protect the information shared by chat of a lot of people.
Today, most instant messaging applications allow you to activate encryption in your conversations, as is the case with WhatsApp who offers what is end-to-end encryption. This means that every time you send a message to a contact in your address bookonly you and the recipient can access that conversation and all the files shared there such as images, videos, voice messages, documents, among others.
In this case not even the whatsapp developer will be able to see said content, this will allow each user to have greater control over their conversations, guaranteeing a 100% privacy. Encrypted messages will appear with a padlock logo and only the sender and the receiver will know the code to be able to decrypt the conversation. To ensure greater protection, each of the messages sent will have a different code from the rest.
Password your apps
Today users have the opportunity to encrypt all or at least almost all mobile applications on your smartphoneand it is that despite the fact that these technological devices are considered quite useful and necessary for the human being, they are also considered very insecureespecially because they can be easily within the reach of third parties and because, mostly, a lot of private and personal information such as conversations, photos, videos, among others.
On many occasions you have to leave the phone with other people to use it, but for some reason you don’t want these people to access it. certain applications and can see the content that is there, mostly it seeks to protect what is the gallery, text message and some other apps over there. Accordingly, a safe and effective method of avoiding this is by applying what is app encryption.
This will prevent third parties from accessing those applications without your authorization, unless these know the password. This method is considered to be much more effective than just lock home screen. In addition, this procedure can be carried out through many methods and in a very simple way.
Encrypt your galleries and media files
As mentioned in the previous section, most users look for protect certain applications specifically in their mobile devices and even laptops. One of the most necessary folders to protect to guarantee a increased privacy and prevent third parties from knowing private information is that of protect galleries and files multimedia.
Today most people decide capture through photographs all his best moments as well as in some cases the most moments intimate and private so all this is recorded in the galleries of the smartphones. In this way, there is a need to place extra protection and encrypt these apps in order to prevent third parties from accessing them without your prior authorization.
use faraday sheaths
Faraday sheaths have become a technological product capable of inhibiting electromagnetic waves, these can be backpacks, wallets or simply envelopes created with materials capable of preventing the passage of waves. This is how these products will help you make your devices invisible with wireless networks for anyone who wants to take advantage of it.
It is no secret to anyone that communications by electromagnetic waves It is comfortable, but it also avoids having to physically access a device to be able to read its content. Therefore, these covers have become an excellent option for most to hide their technological gadgets and thus make these overlook. These covers can be used with mobile devices, tablets, smart keys, among other.
Use a secure browser
This is another of the alternatives that can be carried out to try to improve Privacy and thus try to be less exposed to what is mass espionage. Currently there are many available web browsers in the market where many of them offer you excellent alternatives for browse safely. Despite not being such popular and common browsers, a very good option to start surf the web in a more discreet and secure way is through Tor Browser or Brave.
Both browsers stand out for offering high privacy in all user searches, something that may not be achieved in other web browsers such as Google Chrome or Mozilla Firefox. Therefore, if you are looking for a maximum security in this sense it is worth making use of these web or Opera browsers, this being another of the best cataloged browsers in this sense, in addition to offering an excellent navigation speed.
Keep social life private
It is important to use safe browsing and messaging techniques, since this will prevent most social media data that you drive end up falling into the hands of the government. However, it must be borne in mind that social networks They provide a lot of personal data, where possibly through them some experts can easily know everything related to your life.
Keep in mind that social networks like Facebookthey are doing many surveillance by themselvesthey may not be collecting data to see if you are a national security threat, as personal data may be used for many purposeseven to sell them to malicious people who can profit from them.
A A good alternative to avoid this is not publishing or offering much information and content through these platforms, something that might seem almost impossible today. However, keeping all this in mind can help you have a increased privacy and possibly not to be spied on by your government or by private businesses.
Update the operating system and applications
Surely you have already heard that updates go hand in hand with security, and it is that being able to have everything updated on your technological device will guarantee you a little more reliability and safety in all your data and information. Therefore, the constant updates in operating systems and applications they will provide you with much safer versions for both computers and mobile devices.
You must bear in mind that the older the versions you have installed on your devices, the higher they will be. programming and privacy failures that can be presented with respective versions. In addition, the old versions are easy targets for the cyber criminalssince through them it is much easier to infiltrate malicious programs known as malware.
Privacy