
Index:
UPDATED ✅ Do you want to learn how to browse the Internet safely from Windows 10? ⭐ ENTER HERE ⭐ and Discover All FROM ZERO!
While it is true, Windows 10 It is the latest version released on the market around the Microsoft operating system. Which, with only 5 years of experience, has managed to ponder as one of the best OS that exist in the whole world. Taking into account that, by default, it is a light system that reveals little consumption of resourcesprovides a better experience thanks to Cortana Y supports virtual desktops.
In addition to this, W10 also stands out from the rest for its remarkable safety and reliability, given that it has higher levels of encryption, a powerful password manager and seamless source code. However, when browsing the Internet, users are not exempt from presenting certain vulnerabilities which is appropriate to consider.
Therefore, due to the latent dangers in the online world, it is essential that users know What are the biggest dangers?. Like, how you can browse safely from your Windows 10 PC and some tips that will help you acquire much more privacy. Which, We will explain it throughout this post..
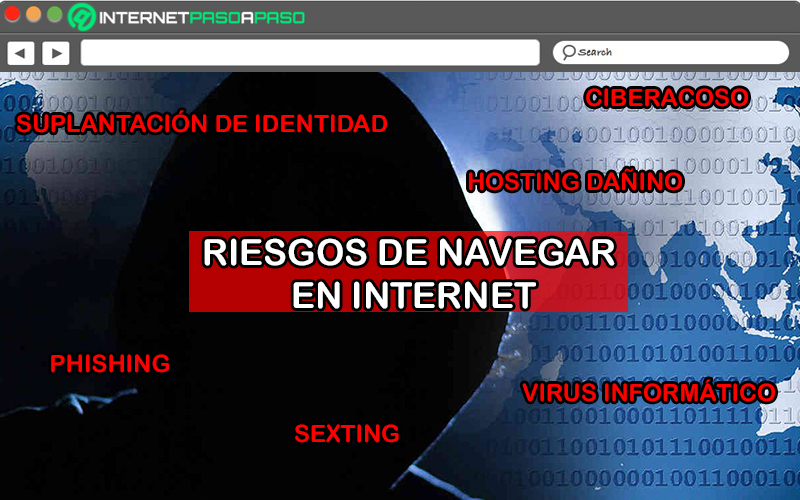
What are the main risks to which we expose ourselves when browsing the Internet?
It is no secret to anyone that the Internet has been an excellent tool for humanity and thanks to its different assets, has made life easier for peoplein addition to speed up the flow of information exponentially.
However, despite simplifying numerous human activities and contributing to the personal development of Internet users, the truth is that these advantages also reveal some cons. In that sense, today a large number of risks are distinguished to which Internet users are exposed when browsing in this environment.
Thus, the main disadvantages that produce vulnerabilities and can have serious consequencesin case of not taking the pertinent actions to protect you and increase your privacy on the internet. Therefore, to reduce these vulnerabilities and be aware of what is happening in this world, it is valuable to know the main risks you expose yourself to when browsing online.
Therefore, here we will introduce you to the most relevant of all:
Identity fraud
This is a problem that Internet users are facing more and more. Which, basically, is a malicious action by an individual who decides to do it for another person for malicious purposes (obtain data illegally, commit some type of fraud, etc.). That is to say, once upon a time some wicked person misappropriates another digital identity.
In this way, it acts under your name and apart from acquiring confidential information, it is also possible that it may be used to publish it. in order to blackmail, extort or discredit the victim online. Even on the Internet, identity theft is also generated when a person creates a profile with the data of another user and acts on their behalf.
That is why, when creating an attack of this type, the victim in question will have consequences such as: threats, insults, ridicule, a distorted image of oneself on the Internet and even economic losses. Taking into account that the most pertinent solution in such cases consists of denounce the perpetrator by all possible means.
phishing
In recent years, this has been one of the most used methods by unreliable Internet users to obtain confidential user information fraudulently, especially, those data based on your bank accounts, credit cards and/or account passwords. Thus, it consists of a type of online scam that uses deception to generate the illicit acquisition of funds.
For its part, this term comes from the words “password harvesting fishing” which, in Spanish, means “harvesting and password fishing”. Among other details, phishers use social engineering techniques to obtain the information they need. For this, generally they pretend to be a reputable company through SMS/MMS systems, telephone calls, instant messaging, emails and social networks.
In this way, they cause the economic loss of the victim. from your bank accounts or credit cards. Therefore, to avoid it, it is best to stop delivering confidential data via email, verify the veracity of the company in question, do not click on any links received by strangers, stop responding to messages that seem suspicious, etc.
Cyber bullying
Also know as “cyber bullying”cyberbullying is defined as a risk present in the digital world that produces psychological abuse of minors and is caused by another minor making use of technologies such as the Internet, mobile devices, social networks and video games.
In general, perpetrators focus on threaten, harass, humiliate, torment and annoy other minors (or even adults). Therefore, cyberbullying is characterized by post or share hurtful, negative and cruel content about another person. Appreciating that, in many cases, it can include private information to cause embarrassment and humiliation before other Internet users.
reason why, this qualifies as criminal behavior on the Internet. Thus, cyberbullying generates serious consequences that cause a great impact, reaching produce until the death of the victim. Thus, a more serious risk than bullying because its spread is faster and it has more coverage, apart from the fact that it can include attack by more malicious people.
Computer viruses
It is also very common to find computer viruses when browsing the Internet. These are defined as digital threats that have the ability to hijack computer resources used with the aim of spreading and carrying out Illegitimate and harmful actions for the user.
Viruses of this class can usually be contracted via email opening attachments (executable program files or macro files) that appear harmless, but are not. Furthermore, these threats are also distributed through instant messaging platforms to spread faster just by getting more contacts to click on some added link.
Similarly, there are software download viruses which are one of the most common to infect computers, in view of which, illegitimate Internet users resort to advertisements or pop-ups to increase their chances of infecting others while browsing the Internet. In other words, these threats can be attached to a file or document, as well as to a link or a program.
sexting
Corresponds to a practice that describes the sending of sexual, erotic or pornographic content through the Internet, based on suggestive texts, images and videos. Which, in most cases, are created by the user himself. sender. Being this, a threat carried out by adolescents who they usually send such content as proof of affection to someone, on their own initiative.
In this way, the perpetrators take advantage of the victims to use those images or videos with the aim of blackmailing and extorting them to obtain as a result, what they want (almost always, it’s money). Because of this, sexting is also known as “sextortion” on the internet and till now, it has affected millions of netizens all over the world. Which, without a doubt, marks the victims for life and significantly damage your reputation.
As a consequence, erotic content may be distributed worldwide, with no apparent control. With that, the perpetrators achieve their mission, by making the affected people feel humiliated. Which can end with loss of self-esteem, depression, anxiety problems, psychological trauma, exclusion from society and, sadly, it can even lead to suicide.
harmful hosting
Another of the greatest dangers of the Internet is harmful hosting. which basically it is the one that exhibits negative particularities in the browsing experience of Internet users, such as: information theft, infected servers, adult-themed website hosting, poor quality support, and SQL injections. In that sense, this type of problem leaves aside the protection of user data, given that are not treated properly.
It is likely that malicious third parties may store this information for use it for malicious purposes in order to achieve their goals. Which, mainly, ends in unwanted advertising and even identity theft. Therefore, in terms of security, malicious hosting reveals notable loopholes for users. Taking into account that, reliability is completely zero in these environments and as a consequence, there is no privacy at all. It is a practice that even leads to legal consequences and penalties.
Learn step by step how to browse the Internet from your Windows 10 PC
Fortunately, to browse the Internet safely in Windows 10, users have several solutions that allow them to acquire a higher level of privacy in the face of so many vulnerabilities and prying eyes. Which means that this operating system allows you to implement several alternatives to be able to have more security on the Internet, from a PC with W10.
Below, we detail these solutions:
install browser

To enjoy an optimal Internet browsing experience, it is essential make use of a web browser that has the relevant features to ensure this. Therefore, in Windows 10, it is recommended install a browser that allows you to access all the information on websites securely and privately. In this sense, when choosing your ideal browser, it is best that you value its level of security, checking if it can identify fraudulent websites through certain filters.
For example; or if it exists some risk of identity theftlike the presence of a computer virus. Also, look at the privacy that it allows to obtain, either browsing incognito or avoiding tracking by web pages. Additionally, we advise you to check the speed it delivers, its compatibility, its functionality and its design.
Thus, under all these features, it is appropriate to install some of the following web browsers in Windows 10:
- Google Chrome: At the security level, it is highly competitive. Since it is free of threats, it allows browsing in incognito mode, its updates are automatic and it adds extra protection with a sandboxing function.
- MozillaFirefox: By nature, this web browser has optimized security features, among which Linux Sandboxing stands out. In addition to that, it has an improved control center and provides tracking protection.
- Microsoft Edge: It is characterized by offering private and secure browsing in a pertinent way. Assuming that, it is capable of detecting malicious web pages and has no economic income from selling advertisements to third parties.
- Opera: Luckily, it has a built-in ad blocker that increases users’ privacy. Apart from that, it offers a high-quality VPN at no cost.
- Thor: Without a doubt, it is another of the most secure and private web browsers that exist so far. Since it allows users to remain anonymous while browsing the Internet and thus does not put their identity at risk.
On the other hand, if you want to download any of these solutions on your computer, the best thing to do is to proceed to download the installation file to your PC via the official website. Then click on “Run” in order to start the installation and once the process is finished, you can proceed to establish it as default browser.
Install VPN
Another element of great relevance to acquire greater protection in Windows 10 refers to the VPN. Which are defined as a service that is responsible for protect the data of its users online, before unreliable Internet users and even government surveillance. So mainly they manage to hide your online identity and encrypt your traffic in order that your fingerprints cannot be traced on the network, thanks to the fact that do not show the IP address of the users.
Apart from that, VPN services take care of secure your online connections so they can’t strip your data based on bank accounts, credit cards and login credentials. Likewise, they can bypass firewalls and offer secure torrenting. Luckily, from your Windows 10 computer, it is possible to connect to a Virtual Private Network (VPN) for freeeither for personal use or for work purposes.
For which, you will need to create your VPN profile correctly and proceed to connect to one of them, as follows:
Create VPN profile on W10
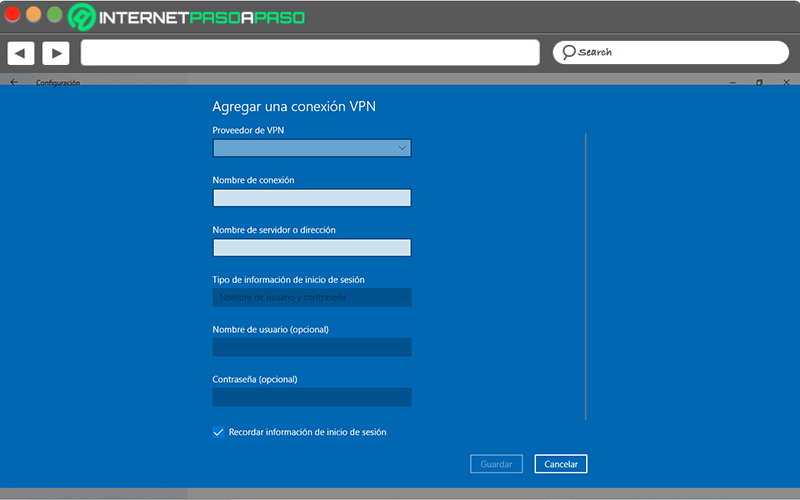
- Choose the Start button and click on “Settings” (the gear icon located on the left side).
- Then select the option “Internet and network”where you will find the option to “VPN” in the left sidebar.
- Next, Click on “Add a VPN connection” to start by selecting “Windows (built-in)” in the VPN Provider part.
- After that, in Connection Name, enter a name that you can easily recognize. Which will be the identification of your VPN connection when you connect to it.
- Then, proceed to write the address of the VPN server, through the box “Server name or address”.
- In “VPN type”, you have to choose the kind of VPN connection you want to create. For this, it is valuable that I investigate what type of VPN connection you need to use personally or in your company.
- Now, it’s time to select the type of login information or credentials you prefer to use. This, via “Type of login information”.
- Done all of the above, you can click “Save”.
Connect to a VPN
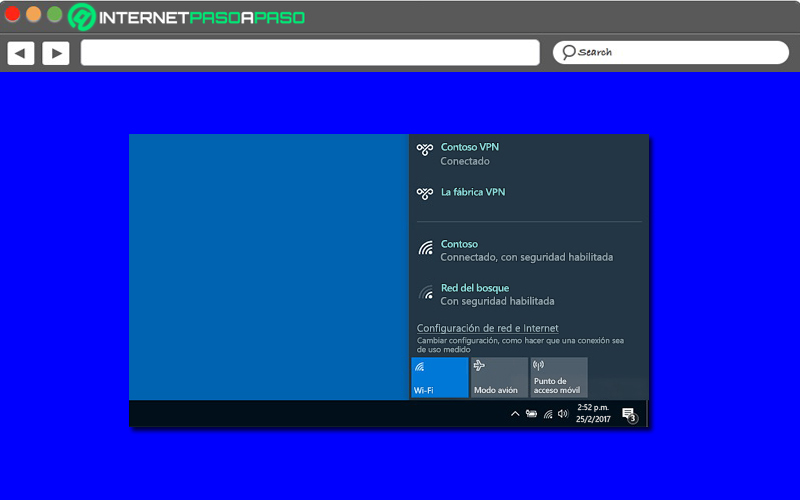
- After you have your VPN profile, go to the taskbar and click on the Network icon.
- Second, proceed to choose VPN connection that you want to use.
- Then if the button Connect is at the bottom of the VPN in question, just click on it.
- In case the VPN section in configuration opens, you just have to select said VPN and then click on “Connect”.
- On the other hand, if instead of the above you are asked for the login username and password, you must enter that data.
- When you perform any of the actions mentioned above, the VPN will show in “Connected” status And so, it only remains to start using it.
open website
After installing your preferred secure web browser and activating a VPN on Windows 10, it’s time to proceed to open the websites you need to start your browsing experience.
Which, thanks to the tools detailed above, it will be much safer and it will avoid endangering your integrity in the face of the different vulnerabilities that are known. In this case, said operating system offers you the possibility of schedule the opening of your website automaticallyin order to acquire the highest possible productivity.
If you want to make use of this functionality, it is best to proceed through the famous Windows 10 Task Scheduler and here, we show you how:
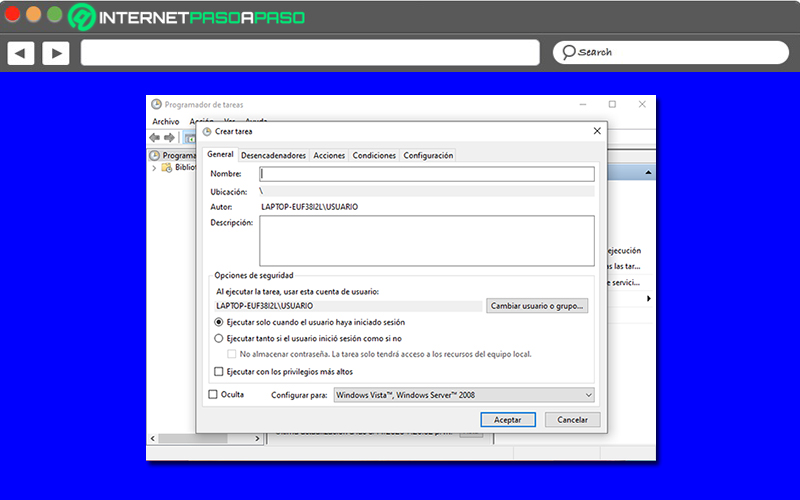
- First of all, from the OS browser, type “Task Scheduler” and enter this application where you will find several options.
- After that, in the application window, go to the section that says “Actions” and in the menu it contains, click on “Create task…”.
- Third, from the next window, you have to define several parameters like: Name and description of the task to schedule, security options to set the time to run the task, and compatibility settings.
- Now, Click on the “Triggers” tab and choose the button “New” to set how often you want to run the action. So, click OK.
- Next, click on the “Actions” tab. There, press on “New” and choose “Start a program” to enter the path of the browser to run in the field “Program or script”. To click OK.
- in the tab “Conditions”, you have the possibility to define parameters linked to the state of the computer. That way, you can customize the task.
- Then from the tab “Setting”proceeds to adjust values associated with the action to execute.
- Finally, click “OK” to apply and save all changes made. Thus, it is time to check its correct operation and open the website.
download content

Finally, in case you need to download content through a website, you can do it freely as long as you use your trusted web browser and have activated the VPN you set up on your PC, before this. Taking into account that, with both elements, you will be able to get an extra layer of security to avoid contracting viruses or computer threats when downloading any content (images, videos, documents, applications, etc.).
At this point, it is recommended to use a web browser that has the ability to verify whether the download in question is based on malicious software or indeed will be harmful to both the PC and the user. Taking into account that, most of the browsers recommended above, achieve identify any suspicious downloads to warn the user with notifications.
Tips for browsing the Internet safely and taking care of your privacy
Apart from implementing the solutions that Windows 10 supports, it is also valuable to put into practice other recommendations that will help you get much more security, privacy and confidentiality on the Internet when browsing the online environment.
These recommendations are explained below, as advice:
Use strong passwords
With the purpose of prevent phishing or any phishing-based threatsis essential create strong passwords and take care of them at all times. Since, during the online experience, one of the most vulnerable points of all consists of passwords and, therefore, experts recommend make use of keys with an optimal level of encryption.
To do this, choose to create a unique and complex password at the same time. Considering that, it is recommended enter 15 characters in it (at least) and that includes both letters and numbers, as well as special symbols. In this way, your online accounts will acquire greater security and it will be more difficult for them to be violated by malicious third parties.
Install a powerful antivirus
It is also appropriate that download and install a good antivirus for PC. Given that, through these tools, you will be able to increase the protection of your computer and your integrity because they are designed to prevent vulnerabilities and suppress any threats contracted.
For example, on W10, you can use the following programs: Microsoft Defender, Avast Free Antivirus, Bitdefender Internet Security, AVG Internet Security, among others. But apart from installing an antivirus, keep in mind that, you must keep it updated so that there are no security gaps in the operating system. Taking into consideration that by installing all relevant updates, the software will remain capable of detect and remove virusesin order to protect you from all the risks present on the network.
Value the importance of the famous “https”
Although the true “https” refers to an Internet communication protocol that guarantees remarkable data protection and confidentiality sent by users once they enter any website. Therefore, all web pages that contain said element in their URL address, are appropriate for conducting private and secure communications.
Therefore, when you browse the Internet and access the websites you need, it is essential that verify that said site operates under this protocol because with this, you can ensure that your information will be protected through the TLS protocol at all times. To check it out, simply view its URL at the top and confirms the existence of “https” at the beginning of it.
For its part, if the website does not use this protocol, it is likely that eavesdropping by intruders throughout your experience on that website. Therefore, they will be able to carry out their illegitimate actions in order to acquire your data and obtain relevant information about you. for so, Generate your different threats (phishing, identity theft, cyberbullying, etc.).
Use the firewall or firewalls
Another effective recommendation consists of implement the use of firewalls to navigate the network. Luckily, Windows 10 has a built-in firewall that you can configure in a custom way, according to your requirements. Whereas, these with appropriate for add an extra layer of protection to the operating systemthanks to the fact that it blocks malware, delivers optimal performance and manages bandwidth.
On the other hand, if you want to activate the firewall available in Microsoft Defender for W10you will only have to access the Settings menu to choose the option “Update and security”. Afterwards, press on “Windows Security” and proceed to click “Firewall and network protection” from protection areas. Now, select a network profile and change the value to “Active” in Microsoft Defender Firewall.
Avoid suspicious links
Apart from everything, we also advise you prevent access to suspicious links and prevent the execution of attachments of dubious origin. Because, one of the most used means to direct Internet users to malicious sites, consists of links or hyperlinks, as well as executable files. For by means of them, they can carry out phishing actions and achieve the spread of computer viruses.
Therefore, when detecting the presence of these elements that are suspicious, it is best to prevent access to them so that, reduce vulnerability to the dangers they exhibit. Considering that, usually, they are risks present in emails, messages on social networks, chat windows and even advertisements on the Internet.
Computing