
Index:
UPDATED ✅ Do you want to configure your Windows PC to make it more secure in every way? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
Currently attacks on operating systems Specially to Windows are becoming more constant so most users want to search alternatives that allow you to get a increased security and protection in all the data that is in the computer.
And it is that one of the most worrying aspects when using a windows computer is the privacy and securitythus preventing the user information may be in danger, especially personal data and bank accounts. It is because of that Microsoft’s own operating system allows you to configure it to increase protection and avoid any kind of information leakage or access of malicious code to the system.
Therefore, the objective of all this is to be able to increase the maximum possible privacy when using the PC, especially in those moments where you are browsing the internet. That is why here we are going to explain which are the main problems affecting the Microsoft OS Y how you can start configuring it to make it much more secureto do this, follow in detail everything that we will teach you next in the post.
What are the main Windows security problems?
Keep in mind that this operating system usually have some problems in your system that can reach affect user safetyespecially when your computer is constantly connected to the Internetas this can cause unauthorized third parties enter the computer system to extract any type of information or to leave any virus or malware there.
However, the best way to be able to fight the enemy is to know him, which is why here we are going to show you what the main Windows security problems are:
Crypto API 32
Crypto API 32 has become one of the main problems for windows users, and it is that this File Type belongs to Dynamic Link Library Win32 DLL, where on your list records can be found the Crypt32.dll. It is worth mentioning that this is housed in the hard drive, from there he takes care of perform different types of operations.
However, all this was violated by some attackers so they can install some malicious software therethey had the ability to impersonate legal software. This has allowed many people dedicated to this especially those more advanced can enter the system through this security error which has undoubtedly affected many users in different ways.
Microsoft Office 2016
Although many of users are unaware of this type of errorthrough the creating a program that is inserted into an HTML so that it can be executed in the browser via a Word filemany attackers can reach activate and execute different malicious codes to be able to carry out DDOS attacks on the computer.
Cortana
Cortana is known as the virtual voice assistant offered by the Windows operating system to its users, it allows different commands to be indicated through the voice. Nevertheless, Cortana has become a Microsoft OS vulnerability
through the voice assistant attackers can access documents that are stored on computers even though it is blocked. This means that any person dedicated to this could access through this medium and extract the personal and private data of users.
file manager
the file manager has become other problems for microsoftand it is that through a external memory such as USB an attacker or intruder may have access to personal foldersas well as to carry out downloading viruses and malwares to the system. All of this can greatly affect user privacy placing in endanger the security of the system itself.
internet explorer
It is no secret to anyone that internet explorer It is no longer used by most users, it should also be mentioned that it no longer comes default on windowsthis is also due to the appearance of Edge. However, it is considered that browsing through this browser may become dangerous for the user.
And it is that it has been proven that through it many attackers may be able to access the virtual memory of the operating system and cause serious damage to itthese attacks are carried out through a flaw that is known as Double Kill. In these cases it is recommended to use web browsers such as Google Chrome and Mozilla Firefox.
adobe-flash
Finally we must mention the failure of the system through adobe-flashEast type of vulnerability is related to a manipulation of an unknown input That runs on Microsoft OS. This is done through adobe-flashso a expert with the necessary knowledge can execute different commands on the computer and in this way to have a full machine control in order to access sensitive data that are stored there.
Learn step by step how to configure Windows to make it more secure
Windows offers its users the opportunity to configure the system To try to thereby increasing security and privacy, preventing that information stored on users’ computers may be affected at any time by any irregular situation in the OS. It is also important to mention that when some aspects are modified in settings to increase computer protectionit is possible that some of system functions or services stop working.
Bearing all this in mind, then we are going to explain how you can start configuring Windows quickly and easily:
Learn to control the data you send in your diagnoses
Windows operating system It is mainly characterized by collecting a large amount of data, This is used in such a case to be able to perform a diagnosis of the problems that you may have. However, on many occasions a lot of data is collected that they can reach offer information the rest.
That is why you have the opportunity to eliminate all this data collection, To do this, you simply have to enter the “Windows Settings”, you do this through the button “Start” and then click on the wheel symbol “Setting”. When you have entered “Setting” you must access the category of “Privacy”.
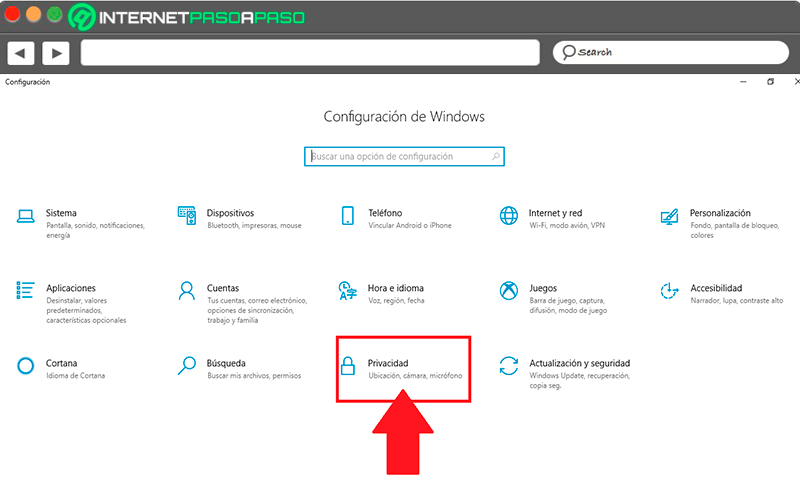
Within the privacy menu you must select the option “Diagnostics and comments” it is located in the panel menu on the left of your screen.
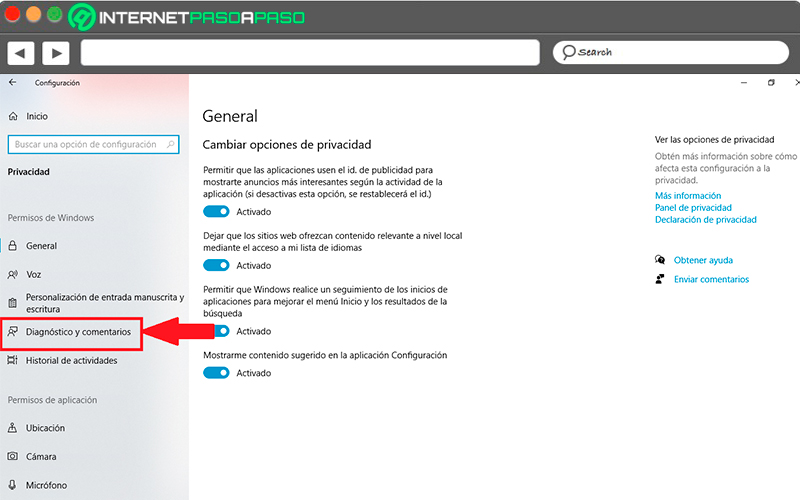
Once you have entered this section, on the right side of your screen you will find diagnostic data sectionhere you can choose what types of data you want sent to Microsoftwhether if only required or optional data. Depending on those you want, you must select that box.
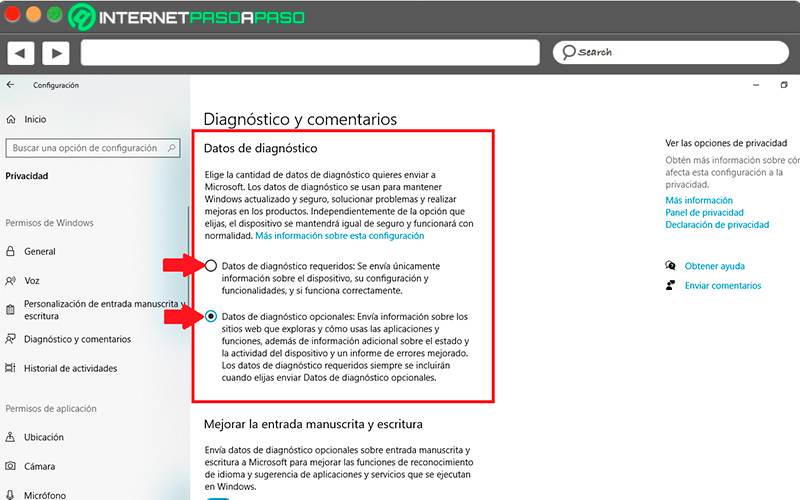
Turn off personalized experiences
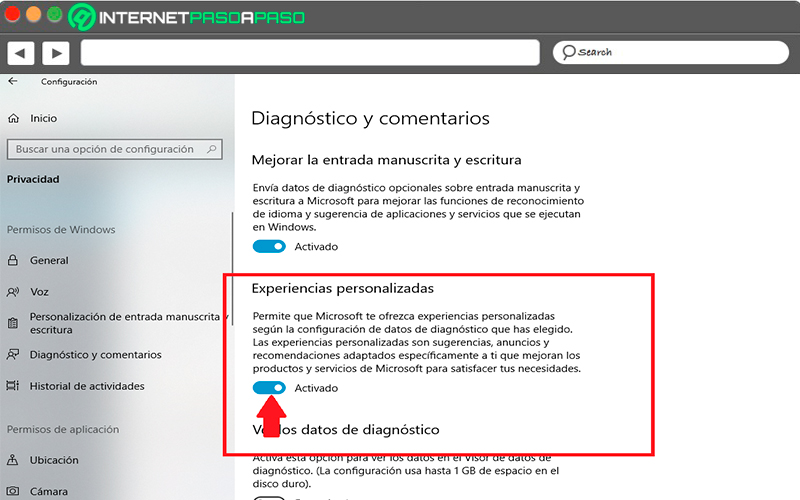
Within the same window Diagnosis and comments you can disable the option “Personalized experiences”, this section is used by Microsoft to collect your data and so after power suggest some personalized apps or ads to you according to your activities on the computer. The most recommended is disable this featurenote that here you can keep track of each of your activitiesso they can be used by third parties for malicious purposes.
Turn off diagnostic data
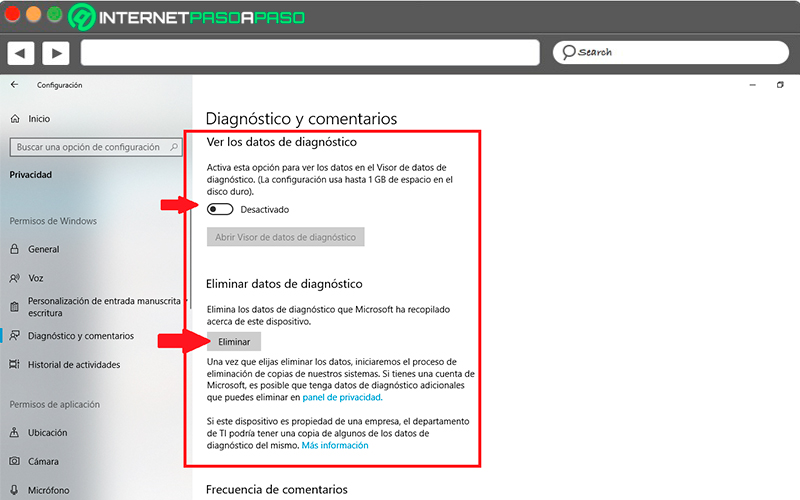
Continuing in the same window “Diagnostics and comments” You can also activate the section of “View diagnostic data”with this option you will be able to see what data has been sent to Microsoft about your activities in Windows. At the bottom you will also find the section of “Delete diagnostic data” with this button you will have the opportunity to delete all data of Microsoft servers.
Turn off voice recognition
Keep in mind that every time you use Cortana on Windowsthe system takes care of store each data what do you say to voice assistant, this with the aim of facilitating these tasks in the future.
Everything that collects Microsoft about what you say is sent to the servers, one way to avoid all this is to disable speech recognition online. Keep in mind that atdeactivate this function said recordings will no longer be collected, but the voice assistant will be deactivated so it cannot be used.
To carry out this procedure you need to follow these steps:
- The first thing will be to enter back to the section “Privacy” from the window of “Settings”.
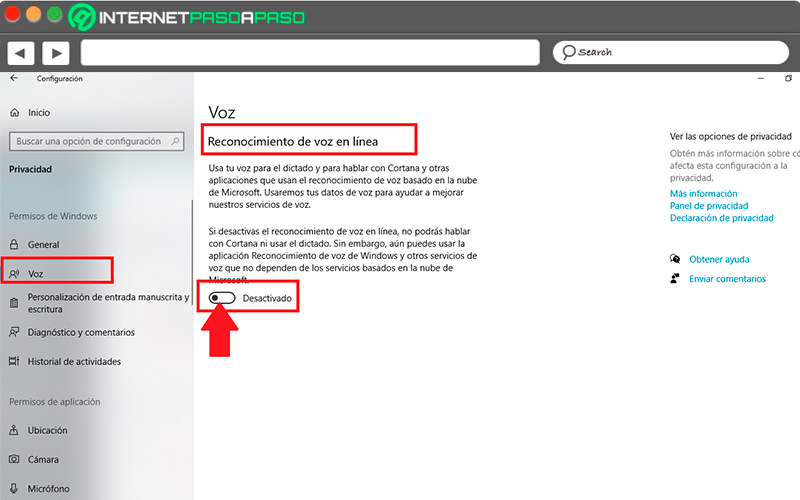
- Now on the menu that appears on the left of your screen, you must select the section of “Voice”, usually appears second below “General”.
- Once the command has been selected “Voice”, On the right side of your screen you will find the “Online Speech Recognition”, here you simply have to deactivate this function by clicking on the corresponding button.
Disable the “Inking and typing customization” option
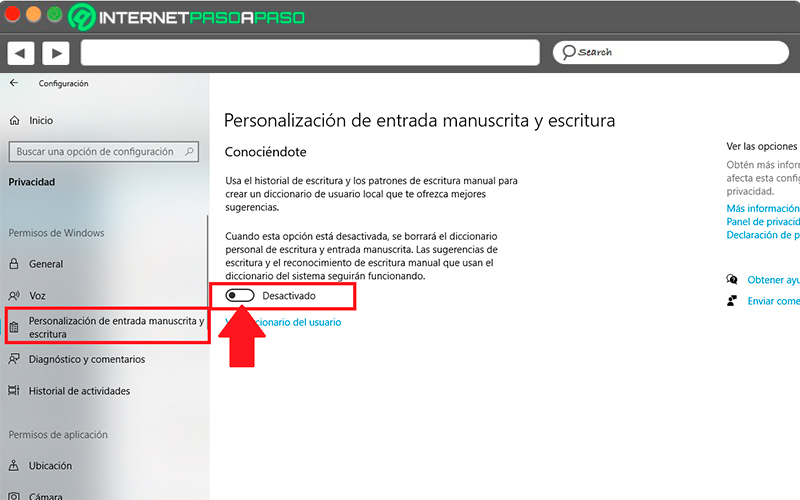
Although many users do not know,Windows is responsible for collecting everything you write with both your keyboard and a digital penit does this for the purpose of collect words used by the user to then complete a dictionary and provide these words at the appropriate times.
This can certainly be considered as a great advantage when carrying out certain types of activities in the teambut can also be dangerous, in case you don’t want to risk then you can disable this function.
To do this you need to follow these steps:
- In section “Privacy” You must select the option “Inking and typing customization”, it is found in the menu on the left of your screen.
- Once selected, on the right side of your screen you will find a button, you must disable to prevent Windows from saving the words that you write with your keyboard or digital pen.
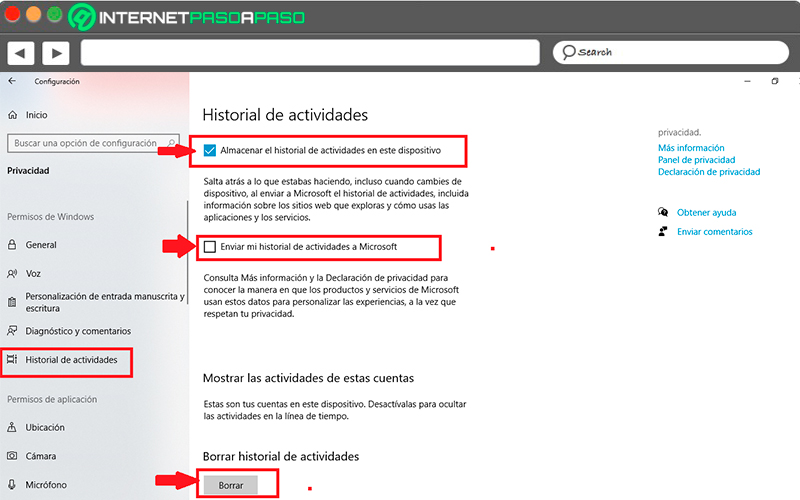
Turn off activity history
The Windows 10 operating system takes care of store a history of all the activities you do on it, this allows you in a certain way to be able to continue everything that you have been doing on one device on another.
Nevertheless, There are two ways to disable this feature.as Windows stores the history of the device on the computer and also sends all this data to Microsoft. We can say that device history is not so necessary turn it off since it is considered that this will not generate any danger, but turn off data sent to Microsoft if recommended.
To carry out these changes you need to follow each of these steps:
- Again from the section “Privacy” you are going to select the option “Activity History” it is located in the menu on the left of your screen.
- Once selected, everything related to that section will appear on the right side of your screen. As you can see, the box appears “Store activity history on this device” Y “Send my activity history to Microsoft.”
- Here you can activate both boxes, deactivate them or simply activate and deactivate one of them.
- At the bottom of the window you will also find the button “Erase” this in case you want to delete your activity history.
Control the browser and search history
In the case of Windows 10 users can count on a search engine that allows them to search for information on the internet and in the computer faster and easier.
But for greater privacy for the user, it can be controlled in two ways, either controlling the online content accessed and the historyand the second way is controlling the local files that are started. By controlling these details the same will not appear in the resultsthis allows your searches are much more indiscreet.
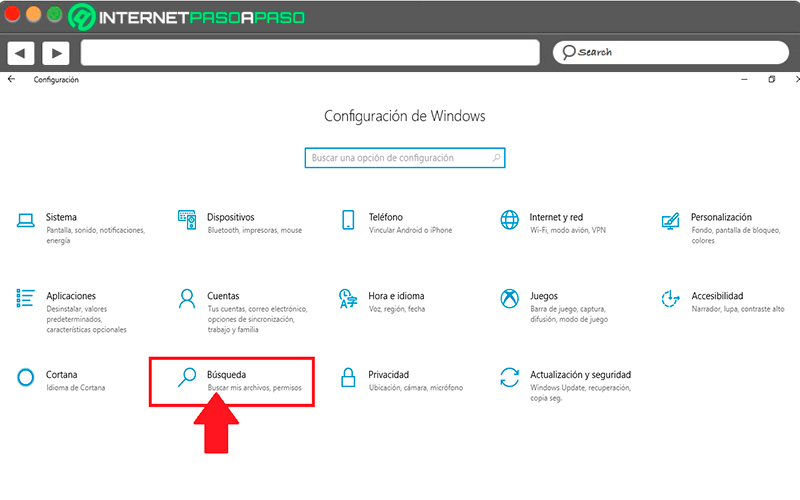
To start this procedure it is necessary to follow each of these steps:
- The first thing will be to enter “Windows Settings” and there select the category of “Search”.
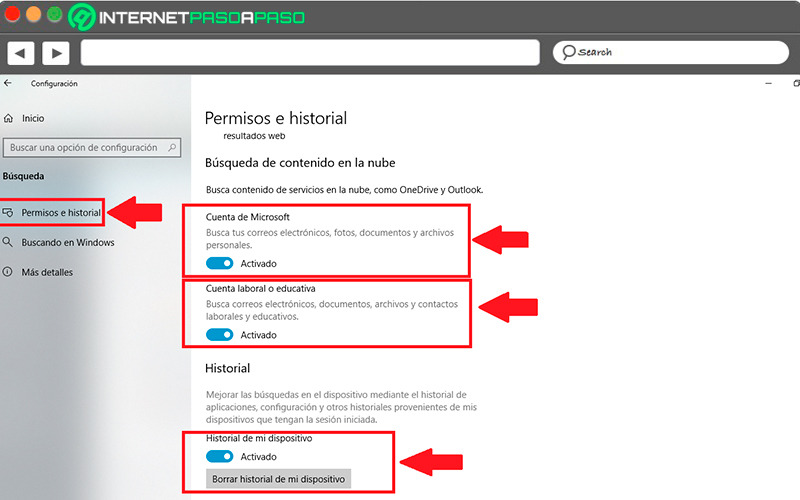
- Inside the section of “Search” You must select the item “Permissions and history” located in the menu on the left of your screen.
- On the right side of your screen you will find several options, the first of which is Microsoft Account, allows you to search your emails, photos, personal files and documents. you will also find bill work or educationalthis allows you to search emails, work and personal documents and finally your device history. Here you simply have to deactivate or activate these boxes according to your own considerations.
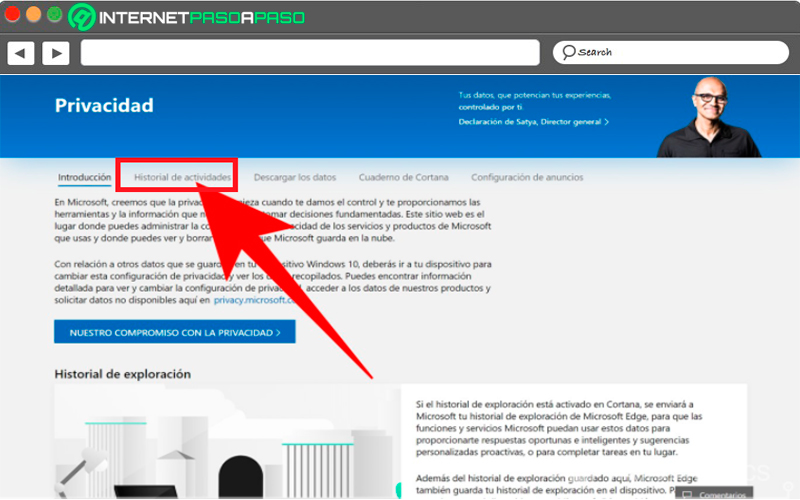
Delete the information that Microsoft has about you
most of windows users they do not know that Microsoft stores pretty much as much information as possible about them. This is how the company has a web page where you can see all the data that has been stored about you, this according to the rights of the users. Therefore, on said website you will have the opportunity to view such content and delete it if you so wish.
All these data is collected from your computer, mobile devices with their services, the Bing search engine or from the Edge Explorer. when you have entered your data and you are on that website, you will find an index where they will teach you all the types of data they collect about you and why they are doing it. The next thing will be to click on the tab of “Activity history”. Each of the tables with the types of data stored has a link to activity history.
Once you are in the section of “Activity History” you will find a page where you can explore all the data. In the left column you can see the different types of data that are stored. By default they will all appear but you can select one by one through the menu. Under each box you will find the button “Erase” you just have to click on it to delete all entry. You must repeat this procedure with each of the sections you want to delete.
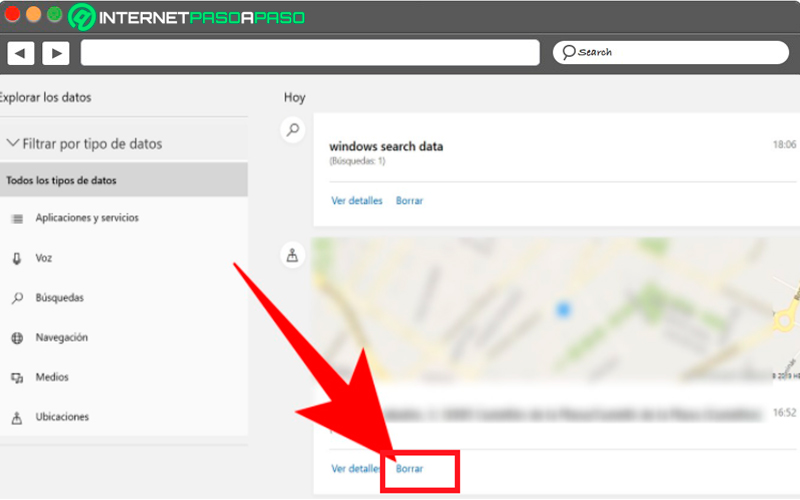
Now in case you are in a hurry and do not have time to go through each of the categories of stored datathen you can enter a specific category and there select the button “Delete activity” located at the top, with this action you can delete all the data that appears in the list without having to go one by one.
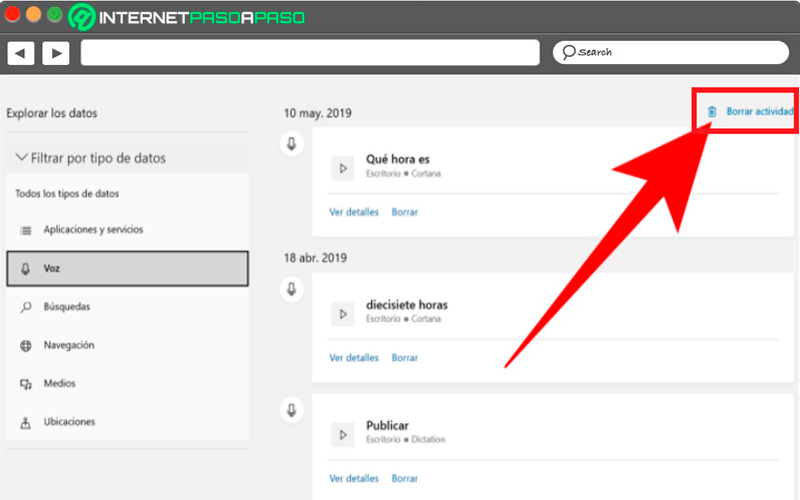
Control what applications access
If what you are looking for is to take care computer securitythen it is very important to control what access each of the system applicationsthis procedure is carried out from the category of “Privacy”, therefore, the first thing will be to enter it again. Once you have accessed the window “Privacy” In the left menu at the bottom you will find the option to “Application permission”.
In this section you can manage the following permissions for applications:
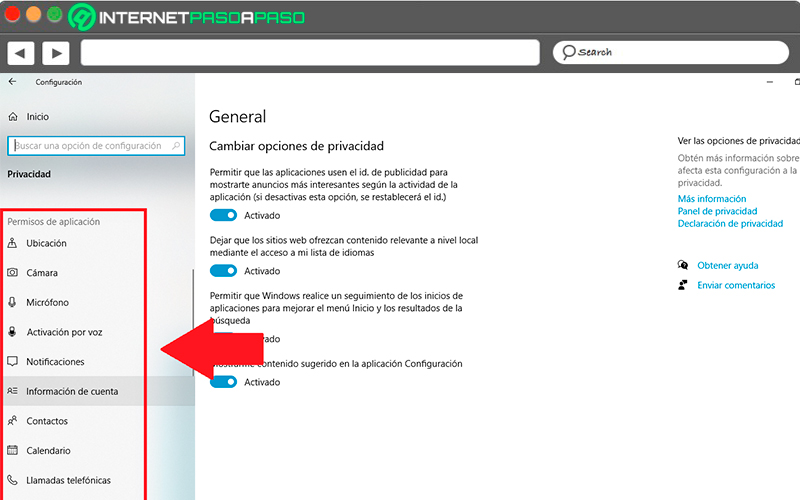
- Camera: In this option you can grant the permissions so that the app can access the camera that is connected in your computer, tablet or laptop.
- Voice activation: Allows applications to listen for a keyword. To activate this option the microphone must be activated.
- Microphone: Allows applications on the device to access the microphone.
- Notifications: Grants the authorization to enter the notifications of Windows users.
- Contacts: It allows entering the contacts that are configured in Windows, in the application of “Contacts” linked to your account
- Account info: Used to enter your account detailssuch as your image, name and other related information.
These are just some of the activities that can be controlled there for applications. By selecting any of these permissions you will enter a new page in which each of them will have the same options. One of them is that of disable access to your computer to this type of information. This option is usually activated by default, to deactivate it you must click on the button “Change”.
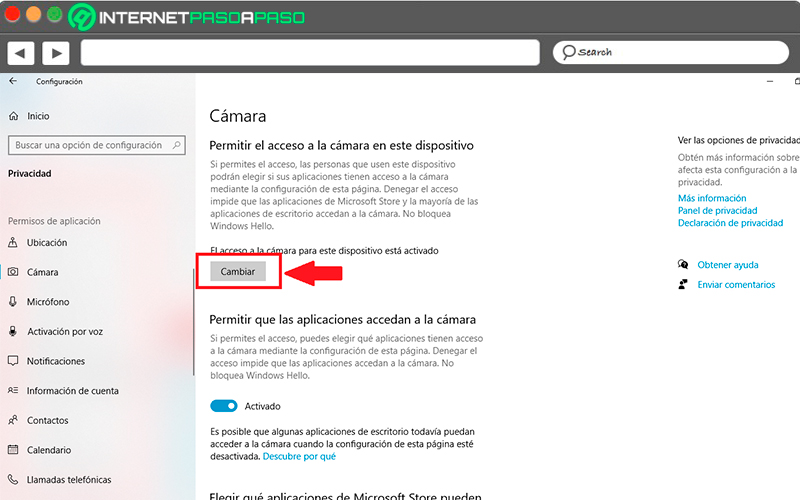
In this way you can access each one of them.the permissions that are there available and activate or deactivate them according to what you think is the right thing to do and the most appropriate for your safety.
Set up a proxy
If the main objective is to be able to achieve a privacy when connecting to the Internet, then there are two ways to achieve it, one of them is using a proxy. In the case of these networks they will help you hide your real IP address every time you access the internet, you can even pretend you’re online from another place or country. In the case of the proxies, these usually receive access requests to your PC and the same are camouflaged to later be sent to a server.
This will make the web page you visited I can’t know your moves, the IP is also camouflaged. If the configuration is to be local level you should not do it from the browserbut simply from the windows settingsfor this you must access the category of “Internet and network”. When you have entered this section, you should look in the menu on the left for the option of “VPN”, it is mostly found in the middle of the menu.
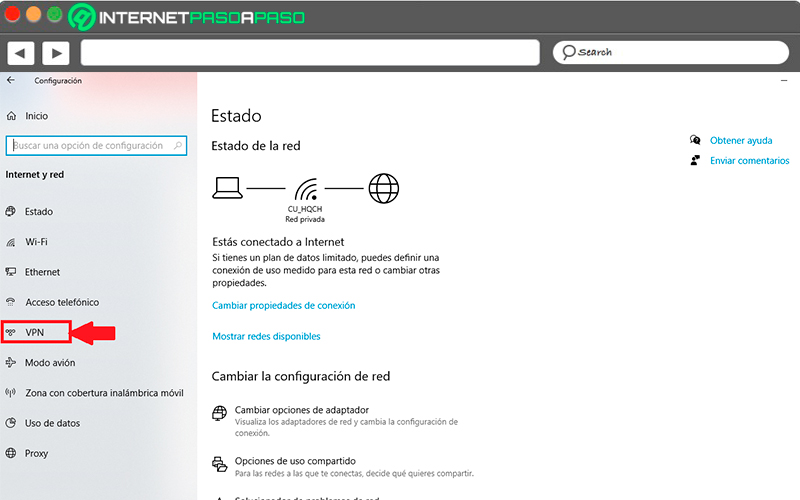
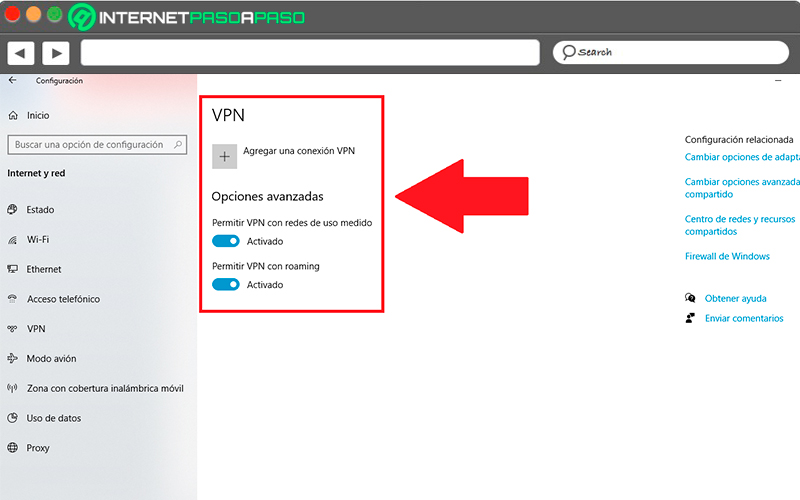
Once found you must click on it. From there you can add a VPN and grant the permissions you think necessary.
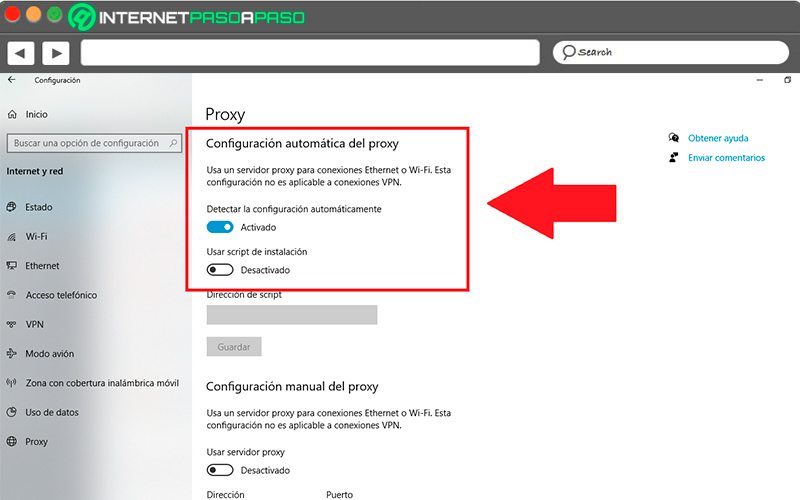
From the same menu on the left of your screen you can access the section of “Proxies”, here you will find two types of settingsone of them will allow you automatic proxy detectionwhile the other is for that you configure it manually.
Computing