
Index:
UPDATED ✅ Do you want to learn more about what Keylogger malware is and how to protect ourselves from it? ⭐ ENTER HERE ⭐ and discover how to do it
Keyloggers are highly dangerous viruses, which can generate copies of all our writings. We must take care of these and protect ourselves against any attack, so it is very important to know what they are and how they act.
In this post, we will teach you very important features that will allow us to quickly identify a keylogger, as well as show you what to do in their presence. If you do not take into account everything that we leave later, you can expose yourself to great danger.
Let us remember that computer thievesthey are not fairy tales and their purpose is to obtain income by stealing from other people, and they really are experts in what they do, but if we have good protection and prudence in what we do, they will not affect any file or personal data.
What is a Keylogger and how does this type of computer virus work?

When we talk about keylogger, we are talking about software that infects our devices for the sole purpose of recording every write What do we do with our keyboard? In other words, a Keylogger is a virus that is sent or installed is a hardware that allows save a file with each key pressed by means of our physical keyboard.
This malware is of the daemon type, and it automatically sends data, which informs other users of all our information, such as: bank password, telephone numbers, credit card numbers or any other.
These types of files can be installed on our PC through an external device (USB) or through a download that we do on the Internet. A antivirus can identify it as either a Trojan or a worm, although can sometimes go unnoticed.
What are the main characteristics of a keylogger file?
Keyloggers are highly dangerous, not because they can damage the behavior of our PC, but because they steal all our personal information. That is why we must always be vigilant when we see unusual behavior on our computer, and quickly identify a computer virus.
If you see that a program has the following characteristics, you should act quickly:
- A keylogger is software that is designed under the visual Basic v5 Programming Language, and is approximately 920576 bytes in size.
- It is mostly presented as software that directly infects our PC, identifying itself as a Trojan.
- It is activated after four restarts or power on of our computer.
- Generates email shipments with encrypted data.
- Record all the keystrokes that we use during the day.
- If we look for its address, we will see that it is always hosted within the Windows system, obtaining a directory guide as follows: HKEY_LOCAL_MACHINE SOFTWARE Microsoft Windows CurrentVersion Run
%Trojan name% = %sysdir%%Trojan name%
where %sysdir% is the Windows system directory.
Objectives of a keylogger What is a hacker looking for with them on our devices?
Keyloggers are created by hackers to get all the information that we write, and the truth is that we write much more than just words, and they know that. As we already mentioned the keylogger its main function is to record each keystroke of our physical keyboardso even our bank passwords or credit card numbers are in danger from this virus.
We well know that on a day-to-day basis, we enter our virtual banking, or constantly make purchases over the Internet, and to make each purchase we write passwords or any other information, such as a telephone number or email. This data in the presence of a keylogger they are not suresince it generates a copy of them and sends it to its creator, which allows the hacker, extract our money or buy with our cards without our consent.
How has a keylogger entered my computer or mobile? Main methods of contagion
This is a program that does not randomly contaminate any user, is sent or obtained by downloading filesor in the most common cases by clicking on emails that include really attractive offers.
Due to viruses like these, we should not rely too much on pirate sites, because if we want to download a software, game, movie or photo, it can also make us unknowingly download a keylogger. Another method of infection is insert external storage disks in our PCas well as USB flash drives.
These types of viruses are very famous, so it is highly recommended to avoid downloading from the Internet as much as possible, using file transfers via FTP, IRC channels, social networks or by peer-to-peer (P2P) sharing.
Removing Keylogger What should I do to get rid of this malware?
Keyloggers are not very difficult to eliminate, in itself by having an antivirus installed on our PC it detects it, and disables or uninstalls it from our computer, although if we are not using any antivirus we can uninstall or eliminate it with the same Windows tools.
Follow the instructions:
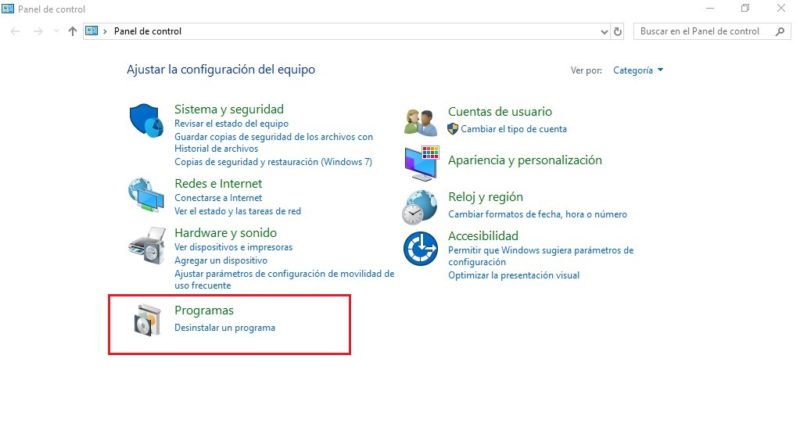
- To do this we must first go to “Control Panel”, there we will see the option of “Uninstall Program or Add or Remove Program”. What the option is called depends on the version of Windows that we are using.
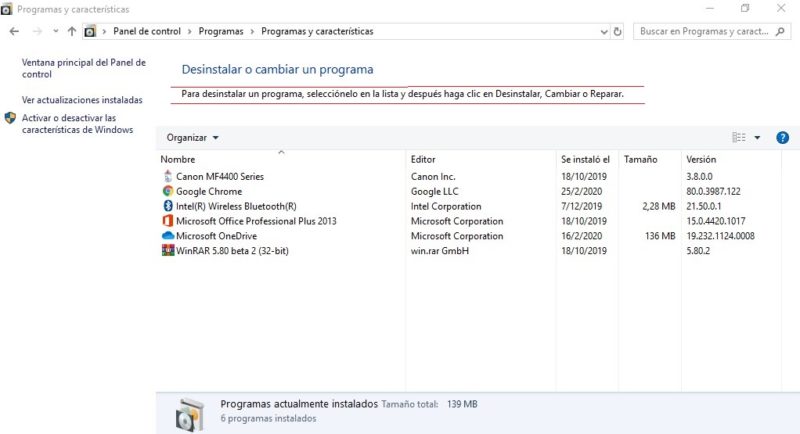
- Then it will open a list of applications and software installed on our computer, if we see that there is an application on that list that we do not know about, because we never installed it, we must eliminate it since it is a possible virusor a Keylogger in this case.
- To eliminate it, we only have to click on that suspicious software, and at the top we will see that some options appear, among them we will select where it says “Uninstall”, and then we will be shown a dialog box, asking us if we really are sure to delete itwe click on “To accept” and the elimination of it will proceed.
We must do this with all the files and applications that we consider to be suspicious. After this, we must turn off and turn on our PC so that changes made are updated.
Tips to improve the security of all your computers and avoid keyloggers
In short, a keylogger is an infectious software that steals all typed data through keystrokes. It is a threat that may not seem like a big deal, but in itself, it is really dangerous for us.
To prevent it, it is highly recommended to do the following:
- Do not download any files from the Internet
- Block all spam emails, and avoid clicking on them
- Don’t let yourself be fooled by flashy promotions on the Internet.
- Use a powerful antivirus such as Avast or AVG.
If we suspect the presence of one of these viruses on our PC, it is best to attack it, although if we only suspect and do not want to act immediately, it is better to apply the following tips to avoid data theft:
- Must install an antivirus extension in our browseras this will detect any data movement in an unusual way.
- If we enter our online banking, avoid writing the passwords with our physical keyboard. Currently, many banks require their users to write their secret keys and passwords with a virtual keyboard that they themselves offer.
- Use the tool in our browser that allows us to save everything we write, known as Autocomplete, so that we avoid typing a password or important data again. This advice applies if we use our own computer, since it is not recommended to do it on other people’s or public PCs.
If we get to the point where, if we want to remove the virus, In the previous section of this post we explained how to do it..
Computing