
Index:
UPDATED ✅ Want to protect your personal information and improve your privacy in Windows 10? ⭐ ENTER HERE ⭐ and discover how to do it ✅ EASY and FAST ✅
There is constant talk about our privacy on the Internet and that Windows 10 is not one of the best browsers in terms of security. We will show you in this article that it is not, Windows 10 is a very reliable operating system. and it can be shielded so that our privacy is in the best hands.
In this article we will talk about everything related to our computer security when we use this operating system. We will show you which tools are the most vulnerable that exist in Windows 10.
We will analyze each one of them and we will show you all the necessary steps to be able to configure each of the weak points that we often leave activated without our knowledge.
Why is it important to maintain our privacy on the Internet?

By maintaining privacy on the Internet we are basically protecting our personal data, our tastes, our families and also our system.
We say that we protect our personal data because there are Internet sites in which, when we are browsing, they extract information from us. making us fill out formsfor example, in which we have to dump each of them in detail and then they will use them for bad intentions.
We protect our tastes when we maintain privacy on the Internet, since by installing spy files they can know what pages we frequently visit, what newspapers we like to read, from here they will also get our level of education and also our political inclination.
This data will be used by companies, which will send us advertisements every time we browse those sites.
We also say that we have to take care of privacy to protect our operating systemsince if we do not have a good antivirus with a firewall that works correctly, malicious files can be installed that can start destroying the folder directory and even the system kernel.
Identifying the issues, which tools are most vulnerable to privacy violations in W10?
As they exist in all computer topics, there are elements that are more vulnerable than others in terms of security.
We will immediately introduce you to each of these tools:
The operating system
Windows operating system vulnerabilities are often generated by errors in the program update, such as there is a code in the update that is incompatible with some other function that is already installed or designed in a previous directory.
This class of vulnerabilities also known as “exploit”, are corrected through patches that we call “hotfixes”, from here arises the criterion that we must always have our operating system updated, because with the update the hotfixes can be installed.
We can classify vulnerabilities according to their degree of danger that they can generate in the operating system. Many of them owe their origin to:
Buffer overload, this occurs when the operating system can not control an application which overloads data buffer and causes it to overflow itself and start copying that data to other storage locations that are empty. Top can generate executing scripts that can give an attacker administrator privileges.
Another error that the operating system has that makes it vulnerable is when it shares two or more processes with the same resource at the same time. This increases the probability of an attack from a stranger.
The networks
There are two ways that an operating system can be damaged analyzed from the point of view of virus entry, one is that we install that malware through an external storage device.
And the other front door it is through the connection to the networkswhich can be of Internet or private networkswith which remote access is shared with other members of the same network.
For this last option In particular, it is very important to have a good firewall permanently active so that it can filter all kinds of harmful information.
If we talk about the Internet it is par excellence the network that most attacks the vulnerability in our operating system
The Navigator
Another vulnerable point that an operating system has is the browser, with the aggravating circumstance that it is regularly used by the user. It will depend a lot on the technological development of the browser.
through the computer, this risk decreases when it is a safe software and we have it updated, different malware can be infiltrated that can harm the system. It is estimated that more than 90% of attacks come from URLs that contain malware.
For all this, we recommend the use of recognized browsers and also the installation of “secure plugins”, which will detect the trust and security of the sites we visit, that is, with this we create extensions to increase security.
The cookies
Cookies are data that are stored through Internet browsing in our browser and that can cause very large damage to our system.
This information has a system of third-party codes that help them to be installed in our operating system and hence be able to execute actions that can significantly damage our operating system.

the scripts
A script is a program that is inserted through an HTML file, which enters through the browser and works on it. These files are executed when we open a page through the browser, they are not located on our hard drive.
It is here that a hole of vulnerability occurs, called “Cross Site Scripting (XSS)”because if that is written they have embargo codes our operating system is at risk.
That is, for these files the “phishing”which basically consists of supplanting an original website for a visually identical one and that has the possibility of being able to steal passwords or other data that is needed to enter the real site.
Announcements
Advertisements are the most common and famous vulnerabilities that exist on websites. This technique is known aswindow spoofing”, which consists of display windows containing fake notification messagesfor example, we have won a prize money.
Clicking on them immediately installs codes into our operating system and can cause extensive damage. This can be detected with antivirus in addition to the recommendation not to open these windows.
To prevent these unpleasant advertisements, We recommend the installation of ghostery.
Cortana
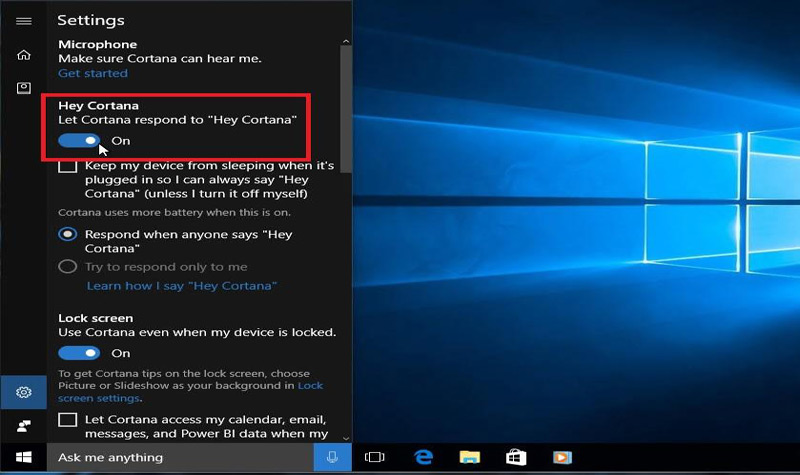
Cortana is the voice assistant that Windows offers to interact with users, it is activated through “Hey Cortana”you can access our computer when it is locked through it.
While it is true Microsoft has already made a hotfix or patch in its latest updates, it is recommended not to have Cortana activated because there is a possibility that when you start listening to the user’s voice, the computer is unlocked and it is the moment in which harmful files can enter without the other security systems that the operating system has been put into operation.
Is Windows the operating system with the most privacy vulnerabilities out there? Should I consider changing it?
Although it is true that they are considered safer to Linux that has an open source system, or to macOS that does not allow certain codes in your system, Windows can be considered as a safe operating system, as long as we take into account some actions to shield it.
Windows is developed with closed source so that no one outside of Microsoft can audit or modify it, even if vulnerabilities have been discovered by people outside the company. The distributions that Windows has are through a payment system, so there are fewer users who access the product activation.
All operating systems have security flaws, Windows is the exception so it is not exempt from so-called “attacks from day zero”, that is, it is exposed to those attacks until Microsoft engineers make the changes and release the updates. The problem is that many people do not carry out these updates, leaving the computers with a high probability of being compromised.
Another problem for which Windows can be considered vulnerable is due to the number of applications that can be installed on it, being very rarely controlled in terms of security.
With the above we can decide that it is not necessary to migrate from Windows we simply have to protect it force it in a better way so that your security level is highly reliable.
Next, we will detail what are the steps that you must take into account to make it a private fortress.
Steps to configure Windows 10 and make it a private fortress
We show you the details to configure Windows 10 and make it highly resistant to different vulnerabilities:
Disable Cortana assistant
To deactivate Cortana we will follow these steps:
- We’re going to “Start”
- We select “Setting”
- We write on the bar “Cortana”
- We click on “Search and Cortana settings”
- We deactivate “Allow Cortana to respond when you say Hi Cortana”
- We deactivate “Allow Cortana to listen to my commands when I press the Windows logo key + C”
- We deactivate “Use Cortana even if the device is locked”
Advertising ID
In order to deactivate the advertising identifier we will follow these steps:
- We’re going to “Start”
- We select “Setting”
- We click on “Privacy”
- we choose “General”
- We deactivate “Permissions for apps to use the advertising identifier…”
- We deactivate “Let websites offer relevant content…”
- We deactivate “Allows Windows to track application launches…”
- We deactivate “Show me suggested content in the Settings app”
Set activity history
To deactivate the configuration of the search history in Google we will have to do these indications one by one.
The first thing we will do is delete the history that we have so far, for this we will carry out these steps in Google Chrome:
- We open the browser
- we choose “Record”
- We select “Delete navigation data”
- we choose “Basic”
- We select “Time interval”
- We click on “All”
Once we have already deleted the data, what we will do is configure it so that we automatically have no browsing history.
In order to perform this action we will do the following steps:
- We enter the browser
- we choose “Data and personalization”
- We select “Activity Controls”
- We look for the optionWeb & App Activity”
- We click on “Manage Activity”
- we seek “Plus”
- And we select “Save activity for”
- We choose the time “Never”
- We click on “Following”
- and we choose “To accept”
When our browser is Firefox we will perform these steps:
- We select “Menu”
- we choose “Privacy & Security”
- We click on “Record”
- We select the option “Use custom settings for history”
- We activate the box “Clear history when Firefox closes”
If we need to decide what type of history we can delete we will do these additional cases:
- We’ll go to “Setting…”
- We select “Clear history when Firefox closes”
- and we choose “Preferences for cleaning history”
- We write what we need
- We click on “To accept”
- We squeeze “Preferences for cleaning history”
- We select what we need
- We click on “To accept”
Check diagnostic data
Windows diagnostic data is data collected by Microsoft to keep your operating system up-to-date. This is regulated in the Microsoft privacy terms.
When we need to control the diagnostic data we will perform these steps:
- We’re going to “Start”
- We will select “Computer Configuration”
- We click on “Administrative Templates”
- We select “Windows Components”
- Next, we choose “Data Collection and Preliminary Versions”
- we choose “Allow Telemetry”
- We click on option number 2
Set location history
When we need to configure the location history we will need to carry out this guide:
- We select “Start”
- We click on “Setting”
- We select “Privacy”
- We look for the option “Location”
- We deactivate “Location Service”
- We select “Location History”
- We click on “Erase”
- We also deactivate all the applications that can have a precise location of our equipment
Encrypt online communications
With the encryption of online communications we will have the advantage that only authorized people can access them and they will be encrypted.
The first thing we will have to do is activate the encryption of the device.
For this to happen we will need to do these Steps:
- We’re going to “Start”
- we seek “Setting”
- We click on “Update and security”
- We select “Device Encryption”
- we choose “Activate”
The next thing we are going to do is activate BitLocker.
To do this we will do these steps:
- First we will have to create a local user account or Windows 10 administrator.
- Then we will go to “Start”
- We select “Windows system”
- We click on “Control Panel”
- We look for the option “Security system”
- We press on “BitLocker Drive Encryption”
- we choose “Manage BitLocker”
- And then we click on “Manage BitLocker”
- We follow the authorization instructions
Choose a safe browser
We can name these browsers as those that have great security when it comes to third-party threats, we remind you that they are not 100% secure but they have a high degree of confidence.
They are:
- Google Chrome: It offers safe browsing and has the Sandbox option so that an extra layer of protection can be added and protect us from different malware. In addition, it provides constant updates automatically.
- Opera: The great feature of this browser is that it has a built-in VPN, which allows us to navigate with great confidence and security on different sites.
- Epic Privacy Browser: It has open source development based on Chromium, which makes it a browser that disables the services offered by Google. Another great feature of this browser is that we always browse in private or hidden mode, thus avoiding great possibilities of tracking.
- Mozilla Firefox: It is considered a safe browser because tell me a protection against third-party search tracking by blocking the components of the pages in which we browse and its control center allows us to customize settings to improve our security is related to the Tor browser, you simply have to enable it add-on Tor.
Completely block cookies
To block cookies we will have to follow these steps for a Chrome browser:
- We’re going to “Plus”
- We select “Setting”
- We look for the option “Advanced configuration”
- We click on “Privacy & Security”
- we choose “Content Settings”
- We select “Cookies”
- We look for the option “Deactivate cookies”
- We choose to disable “Allow sites to save and read cookie data”
When our browser is Firefox we will perform these steps:
- We click on “Tools”
- We choose “Options”
- We select “Privacy”
- We click on “Privacy settings”
- We choose the option “Delete cookies and site data when I close Firefox”
- click on “To accept”
If our browser is Opera, we will follow this guide:
- We select “Tools”
- we click “Preferences”
- we seek “Go to browser settings”
- We look for the option “Advanced”
- we choose “Privacy & Security “
- We look for the option “Site Settings”
- we seek “Edit”
- We select “Cookies”
Block third party scripts
When we need to block the Scripts we will do these steps in Google Chrome:
- We will go to “Menu”
- We select “Tool”
- we choose “Options”
- We click on “Advanced”
- We squeeze “Content Settings”
- we choose javascript
- We select “Do not allow any site to run JavaScript”
To block script in our opera browser we will do these steps:
- We download the extension “Opera Addons”
- We follow the installation instructions
- Once we have installed. this program will work automatically with our browser
block ads

In order to block advertising in our Google Chrome browser, we are going to carry out these steps:
- We will have to go to “Start”
- We select “Setting”
- We click on “Advanced configuration”
- We squeeze “Sync and services”
- We select “Synchronization”
- we choose “Control how your browsing history is used to personalize Search, ads, and more”
- We look for the option “Show all activity controls”
- we choose “Manage Activity”
- we seek “Related Settings”
- We click on “Advertisements”
- We choose the option “Deactivate”
List of the best programs to keep privacy intact in Windows 10
Next, we will detail the best programs so that our Windows 10 operating system is maintained with the highest privacy:
W10Privacy
This program offers to change the most important settings that Windows 10 has to turn it into a fortress.
Its configurations are simple and can have the option that is needed through a custom configuration its designer reports that it fulfills the intended purpose to have the vulnerabilities of an operating system controlled.
Download W10Privacy Windows
Anti Spy for Windows 10
This tool can activate and deactivate different privacy functions, which is much more comfortable not to make mistakes, and thus have an appropriate configuration.
It is designed to identify advertisements, to retain harmful scripts, and to block cookies.
Download Anti Spy Windows
NoScript 10 “Quantum”
Extension for Firefox provides additional privacy as it can block Javascript, Flash, Java and other plugins that can be set such as XSS and Clickjacking.
You just have to follow the installation instructions and we will be able to enjoy a good and reliable tool.
Webutation
This extension also works for Chrome and Firefox, in which its work is designed to collect data from different sites and assign a certain score to those sites so that their codes are better developed according to the database that is collected. .
Do Not Track Me
Another extension that also works for chrome and firefox.
With it we will be able to block advertisements and it also blocks files originating from Javascript, Flash or Java.
Operating systems