
Cybercriminals every day are looking for what new tactic exists to carry out any illegal act through the web, currently being one of the most popular spoofing. This means impersonate another person’s identity .
Through this technique the person invades the world of computer security with the intention of posing as another person, in order to perform any type of malicious act. Everything will depend on the technology you use, since there are different ways of doing spoofing .
That is why security is a fundamental element when we browse the web, because such situations can cause any kind of damage on a personal level , and even become our worst nightmare .
Index:
What is an impersonation or spoofing attack?
Spoofing is a method by which a third party proceeds to supplant the identity of another person with the intention of carrying out a malicious act. This means that another person proceeds to falsify the victim’s data and even the programs he downloads so that he thinks they come from a reliable host.
This package supplants the data chain and its address, so that with this the information obtained can be manipulated and thus falsify the data , as well as make other people believe that the destination host belongs to us.
In this case, the bandit, the application that is supplanted and the victim intervene, with the intention that the attacker obtains each of the data required and thus can use the device that has supplanted; in addition to having the target linked to a fake connection .
Spoofing methodology How are these computer attacks carried out?
Regularly when a computer lunge is carried out, in parallel a criminal activity is executed against a system, a program, an application or any type of tool at the computer level . Through these activities, any type of benefit is obtained for the person who carries out the attack at the expense of the attacked person. There are different types of computer attacks and different targets to attack.
For example, there are attacks that make a system not work properly, attacks that are made with the intention of compromising the victim, attacks to steal personal information that is within a system or where the company owns.
There are also cyberactivism attacks , which are carried out for any type of campaign or cause of communication or information.
Usually these are done to attack any economic or data flow and are usually called “ Man-In-The-Middle”, which means “intermediary attack” , this with the intention of attacking fundamental websites . Or even its databases to steal any type of bank instrument or data.
What are all types of spoofing or impersonation that exist until now?
Spoofing has several faces and then you will know them all in detail. Keep in mind that cybercriminals are always innovating and creating new ways to attack us:
IP impersonation
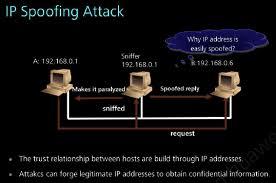
Using this methodology, the «source IP address of a TCP / IP packet» is supplanted by an IP address that you want to usurp. This is done by installing programs that have been created essentially for these purposes, and so that the impersonated host can receive the packets that have been altered, so they will go to an IP that has been forged.
Impersonation of ARP
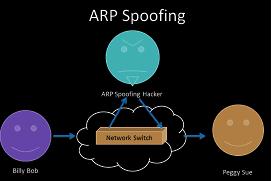
Using this system, the ARP entries are supplanted, with the intention of sending the host of the attacked equipment, and where the data of the equipment will be in the hands of the criminal. This is achieved when a hacker multiplies the tables that have ACR frames , which helps to send packages from the host that has been manipulated by the attacker.
DNS impersonation

Here we proceed to impersonate the IP through a DNS name. Through this, a server is compromised and its cache is infected , thus transforming server entries.
Web impersonation
Here the real pages are supplanted by false ones, in order to obtain user data. Through this the page that has been supplanted behaves like a proxy, with the intention of being able to request the information that the victim has requested from the original server, thus avoiding protection SSL .
Mail impersonation electronic
Using this technique, email addresses are supplanted, with the intention of sending «hoax emails» to be able to use «phishing and SPAM» .
GPS impersonation
Through this type of impersonation the person making the attack can handle the navigation systems in the way they want best , as well as replace the GPS inputs.
GPS tools are used by many users worldwide, as they often use mobile devices to perform their activities. There are several programs that depend on the use of a GPS , and that is why every day they are used by more people. That is why it is not surprising that they have become an attraction for cybercriminals, with the intention of obtaining the information they want.
This type of attack is serious , because GPS navigation systems are widely used by several drivers on the roads. Being in fact essential tool for many steering wheel workers.
As mentioned in the previous points, spoofing is used to be able to supplant the identity of another person and thus get the information needed to commit any type of illegal activity.
Currently using this technique you can get several options to get money or a service easily, and of course illegal . That is why every time you go to perform any type of procedure via online you must use antivirus, even every time you go to download any file. Likewise, it is not other that you use the following tips so you can navigate 100% safe and avoid any inconvenience .
Check each source of information
Every time you need to use a source of information or download a file from your email, even check your bank accounts, you should verify your system very well . That is why you should never give any answer to doubtful questions, and in case you have any doubt you should immediately contact the company of the website you are going to use .
Typically, viruses are used by “OS holes” , as well as browsers that have been infected on the devices. Reason why manufacturers constantly make updates of their applications with the intention that their customers are as protected as possible.
That is why you should not forget to activate updates automatically on your devices, computers or in your browser plugins, as well as in each of the updates you have for personal use .
Take care of passwords.
When you are going to enter any type of password do not forget to be sure that it is the official page of the service, because there are pages that can be equal to the original ones and be a spoofing . Never use the same password in the services you use, because if they take that password they can enter each of your services .
Never share your passwords with another subject, much less with those people who tell you that they are company technicians, motivated that they are not authorized to do this on their own .
Never trust the websites
Always you must is pending when entering any type of web page, because there are many who have misleading messages . When you have any doubt, you should verify the information with a source that you trust.
Never click on a link that you think is suspicious .
You should always be cautious when using an internet link, instant messaging, email or a social network . There are messages that are false and may be accompanied by several mishaps. When they create them they make them as convincing as possible, in order to be able to get the user’s attention and thus direct them to pages that are not legal.