
Index:
UPDATED ✅ Do you want to improve the security of your documents and personal files on Linux? ⭐ ENTER HERE ⭐ and Learn Everything FROM ZERO!
Yes ok Linux it is one of the most secure operating systems, do not let your guard down or be careless in protecting your computer and files that we have stored in it. The reason is that there are also ways that it can be compromised, putting privacy at risk.
To protect its users, Linux makes different tools available that prevent unauthorized people from using or violating personal files. Some of the applications are installed from the beginning and only need to be configured. In other cases, must be downloaded and added to the distribution.
In the rest of this tutorial, we are going to spend time indicate the main dangers in terms of security when using Linuxthe basic configurations that must be made to the computer and the distributions specialized in taking care of the privacy of the users.
What are the main security risks you should protect yourself from in Linux?
As more users join Linux, cybercriminals take advantage to create more resources that tarnish the progress of free software, focusing mainly on the weak points to attack there. The idea is to know the main security problems and know how to configure the computer properly so that it defends itself when a threat occurs.
Here we list some of the risks that occur most frequently:
- Install any app: the lack of security in the tools that are downloaded for the distributions leads to opening the door to many attacks. One of the most common mistakes is not putting reliable serials.
- Configuring the software incorrectly: place weak passwords, expose networks or files open to the public.
- Get infected by malware: the components of this family are diverse, but one of the most popular is Ransomware. Its creators see in Linux a way to generate thousands of euros by launching an attack.
- Have outdated applications: if a distribution has a bug, the next update fixes it, but if we become outdated and don’t install the new version, it opens a loophole for anyone to enter the system without authorization.
Learn step by step how to configure your Linux computer to make it a security fortress
As in other aspects of life, if we neglect security we will have to pay the consequences. In the case at hand, keeping the computer where we have Linux installed protected is our responsibility.
For this reason, we indicate below the basic configurations that must be applied:
Update OS
Have the most recent version of the distribution of Linux prevents others from taking advantage of security gaps or bugs that may have existed at a given time and have been corrected.
To update the operating system follow these steps:
- open the command terminal on your computer.
- Enter the following command
sudo apt-get updateand press the key “Enter”. - Now, add again
sudo apt-get upgrade. - At the end, restart the computer.
The procedure usually fast, though it largely depends on how many files you have to update. The good thing is that you do not have to renew one by onewith the indicated commands the development is automatic.
Use VPN
a VPN helps protect the operating system from computer attacks, since it provides an anonymous but at the same time encrypted online connection, preventing the data from being seen, used or violated by third parties.
The steps to install a virtual private network on the computer are as follows:
- The first thing is to choose the VPN to use, there are paid and free ones. Find one that is reliable.
- Enter the website and start the download. Options are available from 32 bit and 64 bit.
- In many current Linux distributionsit is allowed to run the installer directly without going to the commands.
- If you need to do it via terminal, run the following command:
cd ~/Downloads/. - If you’re using Mint, Ubuntu, or Debian, enter this code:
sudo dpkg -i [nombre del archivo]. - On the other hand, if you work with CentOS either Fedora, add these lines:
sudo yum install [nombre del archivo]. - After the installation is finished, it’s time to activate the VPN.
- To do it, open the terminal again and add:
expressvpn activate. - With these steps, You will have the security that a virtual network gives you.
Use antivirus
There are opinions all types about the use or not of antivirus in Linux. And although we could consider various factors, the truth is that using it has its advantages and helps protect.
To install it you must follow these steps:
- In this case, we will use as an example Clam AV.
- We enter your website
clamav.netand look for the tab “Download”. - Every time the download is finished, We type the following command:
# apt-get install clamavand install automatically. - If you want to do it manually, enter
freshclamIn the terminal. - Once installed, you can scan the whole computer with this code:
clamscan –ri.
Encrypt important files and disks
Although for some it may be tedious put passwords on documents and foldersit is something necessary to take care of the security of the system, since nothing can be modified or changed unless it has your authorization.
To encrypt the files follow these steps:
- If the system does not have it installed by default, add LUKS app by entering this command:
sudo apt install cryptsetup. - Before encrypting, It is recommended to make a backup of the files because we need to format the partition.
- In case we do not want to do the formatting, we must encrypt from another computer.
- To create the partition, We add this command:
sudo fdisk /dev/sdb. - We type “n” for the new partition and “p” to indicate that it is primary.
- If we agree with the values that the system gives us, we give it “To accept”, otherwise we modify the size of the partition.
- Now We mount the partition with this code:
sudo cryptsetup luksFormat /dev/sdb1. - When the window appears, we place “AND IT IS” in capital letters and add the encryption key.
- To see the partitions, we entered
lsblk –f. - To enter the partition that we have created with LUKS, enter
cryptsetup luksOpen /dev/sdb1 particioncifrada. - We place the password that you ask us and we execute
lsblk –fso that the encrypted partition that we have created appears. - It’s time to format the partition with this code:
mkfs.ext4 /dev/mapper/particioncifrada. - Once this step is done, we will have the files “EXT4” on the partition we have encrypted.
- Let’s now create the mount point
mkdir -p /home/bron/particioncifrada/archivos. - And to mount it we type:
mount /dev/mapper/particioncifrada /home/bron/particioncifrada/archivos. - When accessing the directory, we will have the possibility of encrypting all the data we want.
- It is important to know that every time we restart the system, to enter the encrypted partition You must type this command:
cryptsetup luksOpen /dev/sdb1 particioncifrada. - It will ask us for the password and then We will mount the unit again with this command:
mount /dev/mapper/particioncifrada /home/bron/particioncifrada/archivos. - instead of doing it automatic, it is more recommended Follow the manual steps to always stay safe.
Limit system users
set limits in the functions that other system users have is useful to protect personal information that is stored there.
It is recommended to only grant access to those who need to enter the computer, to do so follow these steps:
- Assign a password to each user with the command
passwdso that he is bound to authenticate when logging into the computer. - Use the command
sudoto know who has entered the system. - disable accounts not used with this command:
userdel. - block the accounts for limited times with this command:
usermod --lock NOMBRE-USUARIO.
List of the best security tools to install on Linux and make it more secure
The tools listed below are necessary to increase the security parameters of the computer with a Linux distribution installed. All of them can be obtained in the different application stores and we will search for them according to our operating system.
Let’s see below:
ClamAV.net

East free antivirus is one of the most famous for the platform Linux and it has the advantage that being in the official repositories its installation is very easy. It is used to analyze the system completely or partially in search of various types of viruses.
PrivacyBadger.org
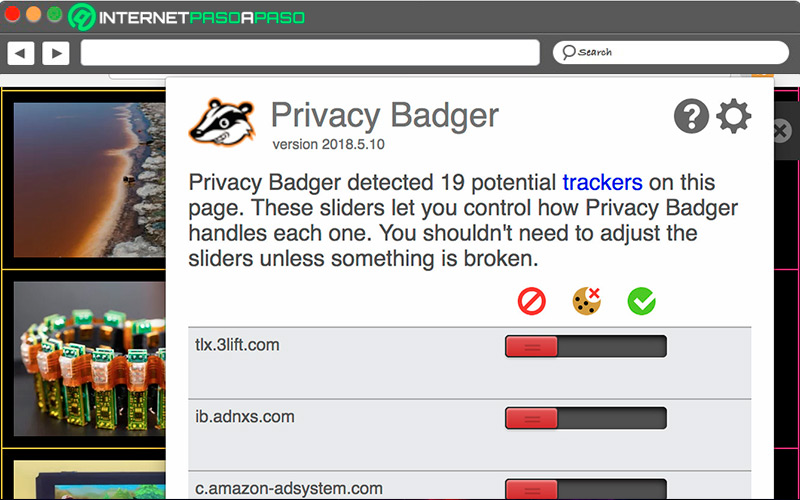
Is about a security guard for web browsers and prevents others from tracking the activity you do when you connect to the internet. By not collecting information, third parties cannot use it. It is compatible with Chrome and Firefoxand requires little space on the hard drive.
chkrootkit
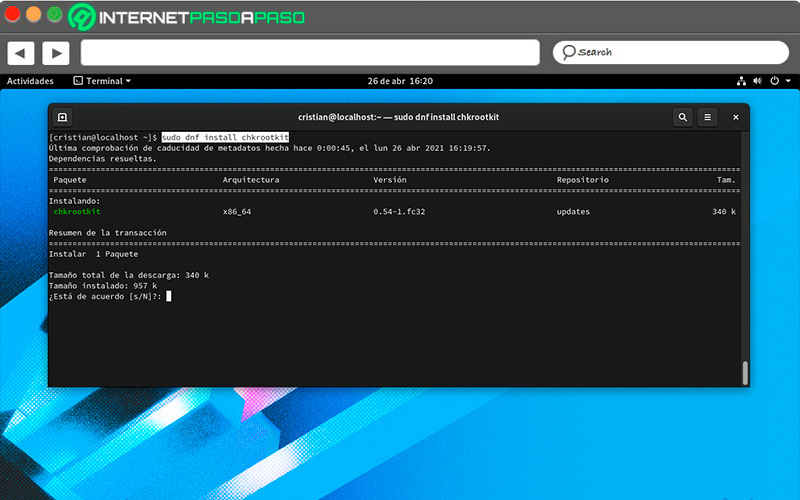
This application helps detect whether rootkits are hosted on the system, some programs in which viruses are hidden that put the operation at risk. Checking the official repositories of your distribution, you will find Chkrootkit and to install it you must grant user permissions.
LUKS
Its main objective is contribute to the encryption of files and disks on your computer. Among its features, it stands out that it stores all the information in such a way that its migration can be easy. Likewise, it provides protection against different types of attacks and saves multiple passwords.
Tiger Kali Linux
One of its main purposes is detect security breaches that the system may have. To do this, it frequently performs checks using Shell scripts, in which it is informed if an intruder has tried to penetrate the computer. You can add it through a package manager.
These are the safest Linux distributions you can install to keep your data protected
Maybe for a new user, the following distributions are not the easiest to use and installr, but for security lovers and those looking to protect their computer they are the most suitable.
We have prepared five Linux distros designed for privacy:
Qubes OS
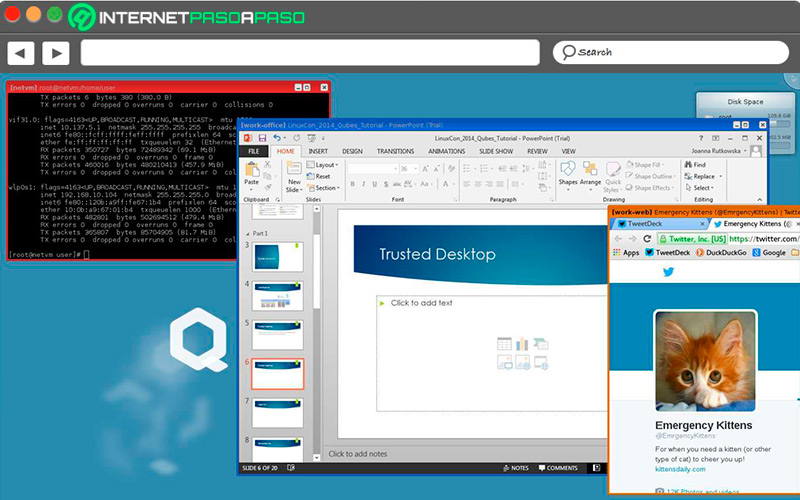
According to experts, this is one of the safest Linux distributions. One of its features is the use of virtualization tools to protect the files stored on the computer. Your protection is not based on an antivirus, but on a tool called XenHypervisor that intervenes in the mechanisms to be executed. By default, all these details are configured, which makes it easy to use and install. It can be downloaded from qubes-os.org for free.
Whonix
This distro which is based on Debian has two main approaches, anonymity in Internet browsing and the security of the operating system. It is not possible for anyone to track our activity, since the connections are scanned through the Tor network, preventing identity from being revealed. It also uses isolation through virtual machines and apart from Linux it is available for other operating systems.
Parrot Os
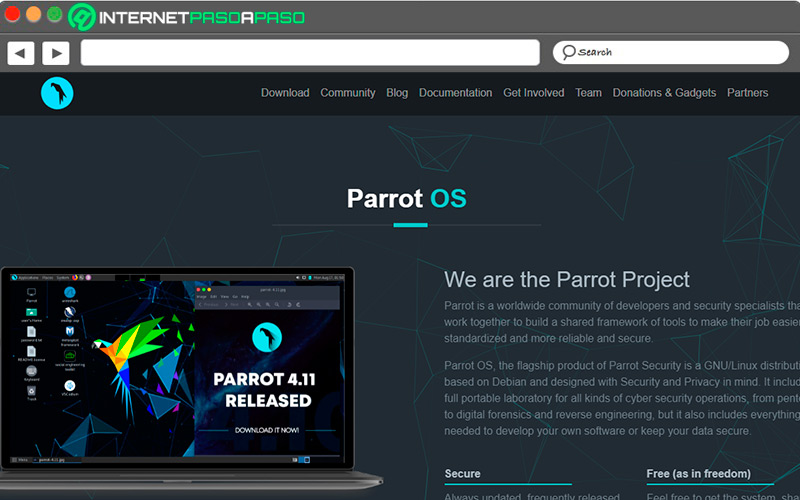
Although it is a very safe distro, that is not why it is neglected in its visual aspect, showing several environments to choose the one we like. Offers programs that are configured to make security tasks more effective. With Parrot, it is possible to analyze the stability of your Wi-Fi network or run penetration tests. At the time of installation, you can choose between the distribution dedicated to security or one that can work in any daily task.
Pure OS

this distro uses I2P to encrypt connections allowing access through Tor. It also has network verification tools in which you can instantly see the traffic between your computer and the Internet. The system works quite well, but you have to have some computer knowledge at least in the installation so that there are no errors. Its graphic elements are similar to Windows, so a new user will easily adapt.
tails

Maintain anonymity and security is achieved with this distribution on your computer. Does not leave any trace of the activity carried out no matter where you are. It works from a USB device, regardless of the operating system you have installed. The web browser, email, instant messaging and office automation have been designed with privacy in mind. Also, when in use it forces all network connections to work anonymously.
There is no doubt that protecting security is also an important element in Linux. New technologies and methods lead to the appearance of risks that perhaps did not exist a few years ago. If you always want to keep your important documents and prevent others from violating your privacy, at all times you should find a way to protect yourself.
Informatic security