
Index:
UPDATED ✅ Do you want to know more about identity theft and all the types of attacks that exist? ⭐ ENTER HERE ⭐ and discover what they are
It is no secret to anyone that the technologies of the present have increased the ease and immediacy of interpersonal relationships. Which is not always beneficial for users, since will have the ability to contact unknown people and so, they are the perfect target for the various threats that exist on the network.
In this sense, currently it is very common to read or hear certain terms such as “social engineering” or “phishing”, which are fully linked with scams and data theft. Therefore, can cause economic losses, lower productivity and increased resource consumption of corporate networks.
That is why it is truly essential to know what this type of fraud on the Internet is all about, in order to prevent any risk as far as possible. Therefore, we proceed to explain what is phishing and what are all the forms of identity theft that are now handled.
What is Phishing and how does this type of computer attack work?
Basically, phishing is defined as a scamming technique that is carried out through some form of social engineering. So, traditionally, it consists of sending emails that come from apparently reliable sources in order to try to trick the recipient into accessing it, follow their instructions and reveal your sensitive data.
This means that it is a digital practice whose main objective is, obtain personal, private or intimate information, illegally, from the manipulation of users. Well, using social engineering tools, cybercriminals get the affected person to reveal sensitive data in order to being able to carry out some type of fraud afterwards.
Now, with respect to its operation, we emphasize that it is an act carried out by a criminal known as a “phisher” that impersonates a recognized personal brand, company or organization to acquire the desired information fraudulently (stealing or spoofing email addresses). Therefore, the practice of this type of attack usually starts with receiving a direct message or email.
In such a way, once the victim chooses to open said message, it will contain links to a website where personal data is requested, imitating the portal of the legitimate company. With this, as soon as the person enters that information, the cybercriminals will be ready to commit the fraud immediately and, as a consequence, the affected user you will lose access to your email or suffer substantial financial loss.
Due to the methods and tools used by all “phishing”it is really difficult to recognize that it is a message received by cybercriminals, since its appearance can be very professional. However, in case there are inconsistencies, errors or misspellingsit is a great indication to know that it is not a trustworthy email and with it, You will avoid doing any unfavorable reason.
List of all types of phishing attacks that exist with examples
Although, in a general way, it can be stated that all phishing or identity theft practices are linked to social engineeringthere are actually several types of attacks that steal confidential information.
To learn more about them, we invite you to read the following list:
spear phishing

It is considered the most common type of phishing attack and consists of a scam executed via email or social media on specific individuals, companies, or organizations. In other words, it is a much more personalized threat because includes the identification of the victim, his position, his telephone number, etc..
In this way, it is characterized by being a type of phishing that is only aimed at a small number of people. with a certain profile within a company or company, whereas, it is normally directed at the weakest link. Thus, its main purpose is steal data for malicious purposes and install malware on the victim’s computer.
URL Phishing
Another of the techniques most popular phishingconsists of the one that deals with trick the user through a URL belonging to a malicious site which, at first glance, looks like that of a trustworthy website. Usually, this type of deception gets the victim to enter inadvertently to that website using Unicode characters similar to the original link.
It should be noted that the phishing URL is most effective on mobile devices, especially those with small screens or low resolution. Now, a clear example of this is this URL “http://[email protected]” that appears to be a website available in Google, but in reality it is responsible for sending the browser to the page in question, which is prepared for request the user’s personal information and carry out identity theft.
Phishing Card
Basically, it is similar to traditional phishing, since consists of the massive emission of electronic mails to different users. But, in this case and as a distinguishing factor, only focus on simulating the identity of a trusted banking organization.
Thus, once the user chooses to access links corresponding to malicious domains, cybercriminals will have everything ready to request the data of any of your cards from your bank, whether credit or debit. From this deception, they will proceed to make purchases online or withdraw money from your accounts onlinecausing significant economic losses.
email phishing
This is the type of attack also known as “phishing email” and is defined as a digital deception technique that consists of misrepresenting users to steal your confidential information. Thus, depending on the goals of cybercriminals, they will choose to request intimate data, access codes or bank information.
As we have pointed out throughout the post, this type of phishing focuses on add links or attachments in the emails they send, to transfer the victim to the website from where they carry out the misdeeds. Which, can be a copy of the original and thus, they manage to deceive the most trusting users.
Phishing Gmail
During recent years, it has been shown the rise of phishing attacks on Gmail accounts, that is to say that, in this case, cybercriminals do not focus on imitating banking sites to obtain an economic benefit, for example. Rather, it is a threat that only is addressed to Google’s renowned free email service.
This, due to its great popularity and with the aim of taking control of a gmail account so, have access to other services managed by the Username. Since, in most cases, Internet users use a Gmail account to sign up on other platforms or recover passwords. For this reason, they are the perfect target for many phishers who bet on this new technique.
instagram phishing
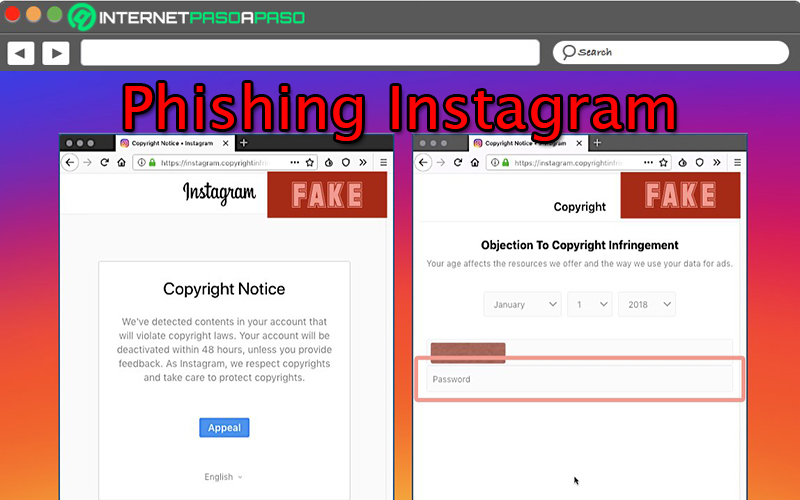
As well as gmail has become a potential platform for phishing practices, Instagram is the new target of this class of digital criminals. Therefore, at present, there have been massive kidnappings of accounts of Instagram with phishing emails.
In this way, the perpetrators proceed to send an official-looking email (with the Instagram logo and header) and issue information based on the following message “Your account will be permanently deleted for copyright violation”. But, it is actually a trick for the user to access a link with “more information” where you will have to enter your social network credentials and with that, they achieve their goal to be able to enter to steal information.
Facebook Phishing
Facebook is another of the social platforms on which more phishing attacks are happening, lately. Therefore, it has become a useful online site for digital criminals who design such scams.
Which, are based on the impersonation of the image of a person or service registered on Facebookto deceive other users and being able to steal your sensitive data. In this sense, phishers are in charge of intervening in any vulnerable account active in the social network, to proceed to alter your profile data (i.e. your name and photo). This done, they write messages to all their contacts posing as Facebook, in order to obtain personal information and even credit card numbers.
PayPal Phishing
As if that were not enough, there is a new phishing campaign that attempts to impersonate PayPal, through emails. In this way, the attack begins with an email in which an alleged unusual activity in a user’s account is reported and there, provide a link that the owner must use to verify their identity.
Then, when the victim clicks on the link in question, they will be redirected to a web page that, while visually resembling PayPal’s official site, It’s actually an imitation of it.. Thus, from there, they will ask you to secure your account and enter your personal data, in order to “prevent unauthorized access”. Once that is done, the criminal will have obtained everything necessary to make your digital scam come true.
Amazon Phishing
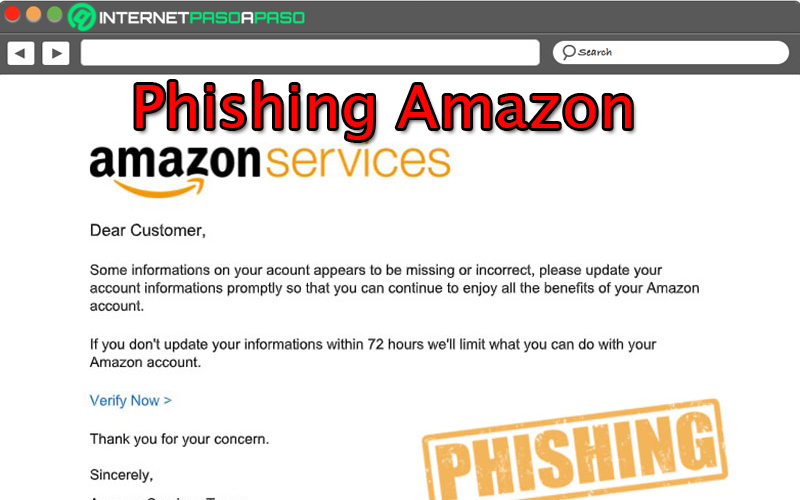
Since the beginning of 2020, the Spanish police authorities have alerted society about a new type of phishing attack that many Internet users and refers to an apparent email issued by Amazon that requests users to log in to said online portal, “for security”. However, it is only a deception by a group of cybercriminals who are betting on this new technique.
In this way, if the victim user trusts and provides the personal information in question, they will not actually be logged into the application, but rather you will only have given your data to the attacker. Some phishers even target obtain information about your bank card with the reason that “everything works fine again” and thus, to be able to undertake substantial economic scams.
Santander Bank Phishing
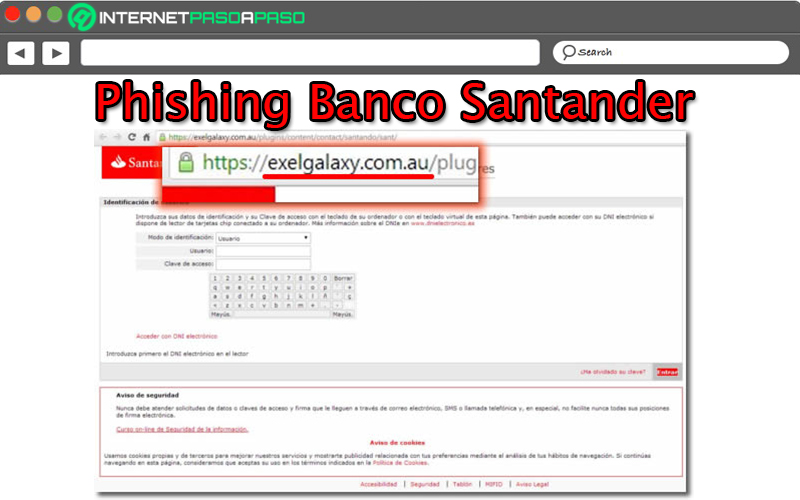
Another powerful phishing campaign has also emerged supplants the identity of the famous Banco Santander. Which, as in almost all cases of this type, begins with the receipt of a massive email that has this bank as the sender. But, although it seems a legitimate action, in reality the header of your email allows you to verify that it is not completely reliable.
However, it is very likely that the client is not very detailed and will not find this type of fault, so he will opt for access normally and enter the URL provided; which is simply an online platform controlled by the hackers in question. So, on the first screen, request the identity document and the access code; with this, the phishers begin to require the card data without any verification of its legitimacy.
smishing
This is a fraudulent action very similar to traditional phishing, but with the only difference being that originates through text messages, either via SMS or by instant messaging service such as WhatsApp. In other words, it is based on a phishing technique that is related to the use of another digital channel, especially mobile phones.
In this case, digital criminals pose as recognized entities and report that the victim has won a prize or, pretend to be a bank to notify you that a suspicious purchase has been made with your credit card. In this way, they request that you communicate to a false number and from there, they ask for confidential information to “withdraw your prize” or “cancel the purchase” and it’s not really like that.
Vishing
It refers to another variant of common phishing that, although it also occurs over the phone, does not operate the same as the “Smishing”. Because instead of texting, is based on making phone calls to communicate with the victim and obtain any private information. Taking into account that it is usually related to another attack to achieve greater credibility and effectively fool people.
Now, this type of digital fraud, in most cases, is undertaken when the cybercriminal has already carried out his attack through traditional phishing tools, but you need to validate some operation through an SMS key. Therefore, they choose to call the victim by phone (as an apparent worker of the organization or company) and, alarmingly with social engineering techniquesrequest these codes to authorize the transaction.
Informatic security