
Index:
UPDATED ✅ Do you have doubts about what types of hackers there are and want to know the differences and similarities between all of them? ⭐ ENTER HERE ⭐ and discover which one is better ✅ EASY and FAST ✅
surely you know the term hackersince it is quite common to hear of this type of people who do illicit activities online. But surely you do not know or have little knowledge of crackers, these types of people are quite common in the world of the Internet and both differ from each other. Although the difference is small, It is important to clarify that a hacker and a cracker are not the samebecause these terms in today’s news media tend to be confused or misuse these terms.
What generates confusion or misinformation in the population. Note that a hacker can break into computerized systems remotely Without complications and without having any authorization to do so, it can also steal information and manipulate systems. A cracker performs these same actions, but for profit, like extortion, for example.
In this guide we are going to explain the concept of a hacker and what is a cracker? Their differences and even talk about possible motivations, so that you can be more informed about this group of individuals that lurk in the world of cyberspace.
What types of hackers or crackers exist in the digital world?
There is a wide variety of hackers and crackers, these can be classified into their specialties as well as the level of skills they have to enter into the computerized systems.
types of hackers
Among the types of hackers the following can be named:
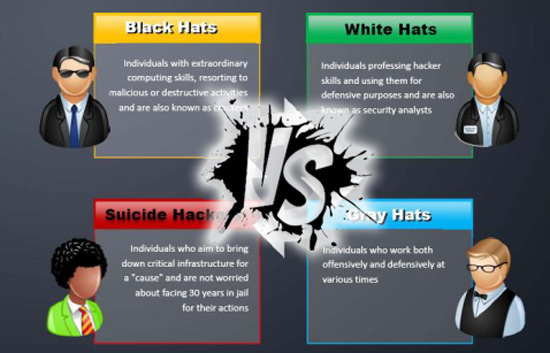
- BlackHat: These are the most dangerous among the types of hackers. They use their highly specialized techniques to gain access to computer systems and in this way take control of them, obtain their data, in order to destroy or sell them, among others.
- WhiteHat: These can be called ethical hackers, since they work generating security and protecting IT (Information Technology) systems. They commonly work for information security companies, whether governmental or private, reporting possible vulnerabilities in the company’s systems in order to take corrective measures.
- Gray Hat: These types of hackers can be considered as a kind of hybrid, since they can act illegally, but with good intentions. These individuals may enter systems and disclose information that is useful to the general public. An example of this could be that they spread cases of large companies for the unauthorized collection of data from their users.
types of crackers
Among the types of crackers are the following:

- carder: They are people who have become experts in credit card fraud. These can generate fake numbers and access codes that can successfully breach control systems, thereby stealing and cloning cards.
- Farmer: These people are dedicated to carrying out attacks of Phishing, that is, they make the user believe that they are entering a real site. People enter their personal details on the site created by the hacker and then use the credentials to steal money from their victims’ accounts.
- war drivers: They are crackers that take advantage of existing vulnerabilities in all types of networks in the mobile connection.
- deface: This group of people look for bugs in web pages on the internet in order to infiltrate them and thus modify them.
- Spammer and Spyware disseminators: There are companies that pay these types of people to create spam for their main products and in other cases seek to profit from illegal advertising.
What is a Hacker and what are its origins?
The denomination Hacker refers to that person specialized in one or several branches of computing such as: programming, computer networks, operating systems, voice/network hardware, among others. Actions performed by a hacker are called hacking or hacking.
The word hacker is believed to It was born from the people who worked as programmers at the Massachusetts Institute of Technology (MIT). This group of people during the 60s had a tradition of playing innocent jokes which they called hacks, acquiring for themselves the term hackers as a way of calling the group they formed within the institute.
Characteristics of a Hacker
You are a person who enjoys the exploration and details contained in programmable operating systems, as well as other programs. Looking for a way to take advantage of their possibilities, obtain greater knowledge of them and new ways to apply said knowledge. Other features that can be named are the following:
- whenever they program They do it enthusiastically. (It even becomes an obsession with some).
- Its programming speed is very advanced compared to a normal user or an amateur in the world of programming.
- They can specialize in one program in particular or have great skills for different programs.
- They tend to have the belief that sharing information is a great job and a powerful and precious asset.believing that it is an ethical obligation for hackers to share their experiences and knowledge using open source (Open source). In this way they facilitate the use of the information to all who want to know more. They also believe that breaking into systems, whether for fun or exploration, is ethically well-accepted as long as the hacker does not commit theft, vandalism, or violate people’s sensitive data.
What is a Cracker and what are his abilities?
A cracker is defined as a person who uses his or her great knowledge and skills in computing and informatics as a motivation to fight against what society defines as prohibited. Modern crackers like to use their own programs or, in some cases, use those that are distributed free of charge on specialized websites. in the distribution of these and other illegal information on the internet.
These tools include the following: programs to unlock or copy access codes, use number generators that by random and running automatically can manage to violate system access codes.
Characteristics of a cracker
Crackers mostly focus and specialize in theft and vandalism, either for their own reasons, or with the intention of causing damage no matter how serious it may be. They commonly tend to band together in small, secret, and private groups.
Crackers perform the following activities:
- Crack: It is a created program, which has the functionality of introducing a modification to software, probably with the intention of disabling its protection.
- Warez: It is a type of illegally obtained software.
- KeyGen: This is a program that generates keys which can be used to override the anti-copy security measures of the software.
- Piracy: It is what we currently know as illegal copies of software or audio.
Main differences between a hacker and a cracker in computing

Basically a cracker and a hacker, perform the same activities and have an equal level of skill (of equal proportion). Nevertheless, What sets them apart is what they do with those skills.
while a hacker use your skills, to discover system failures and in this way provide corrections and increase computer security. A crackers use these glitches, to increase errors in the system, damage them or render them completely unusable. They even use it to steal information in order to extort or sell the data to other people and thus make a profit.
Hackers act under a belief and an ethic where all information if it is stolen, it is to demonstrate illicit activities of governments, companies or individuals. Sharing it to the public to expose the real criminals.
Like the hacker, the cracker is also passionate about the computer world. Their difference is that a cracker tries to damage systems and computers. That’s where the English term “Cracker” comes from, meaning “Breaker”, and its objective is to break or damage systems and computers.
Informatic security