
Index:
UPDATED ✅ Do you want to know what are all the threats facing cybersecurity these days? ⭐ ENTER HERE ⭐ and know all
The cybersecurity threats nowadays they are quite frequent due to the use of the Internet that all the activities we carry out require. For this reason, being attacked virtually is a fairly high possibility.
So that you know what a computer security threat is and what its objective is, we have prepared this article. In it you can find all the information related to this important topic.
You can also read a complete list of the main threats to information security that we face today. Do not miss anything if you want to have your data protected.
What is a computer security threat and what is its objective?

We consider a computer security threat to any strategy or action capable of going beyond the protection protocols of a device or network. Whether these are aimed at protecting the computer equipment or sensitive information of a large company, SMEs or individuals. Said threats they can have an external or internal origin and can be intentional or due to user carelessness.
For example, natural disasters, inexperience with technological means and damage to infrastructure. All of these factors are potential unplanned threats. Nevertheless, planned (or intentional) threats they are a predominant risk and the most frequent. This is due to the way it works. The more connected a person is to the webthe more you will be exposed to cyberattacks.
As there is a strong combination of skills related to the advanced programming knowledge of hackers and the social engineering it’s much easier spot and profit from cybersecurity vulnerabilities. Considering these as failures or weak points in the processing, exchange and storage of data.
For this reason, these attacks are aimed at impair the proper management of information or systems. Bringing with it great economic losses for the companies that depend on it. They also have the purpose steal private information to receive financial compensation. You must not forget that the blackmail and extortion They are also methods used whenever private data is obtained from people.
List of the top information security threats facing us today
Staying vigilant is part understand what threats you may face every time you browse the Internet. Then it is appropriate to know the main techniques used by cyber attackers.
Here is a list of the main threats:
malware
constitute a set of malicious software that is created with the purpose of infiltrating a person’s devices, regardless of the operating system they have and whether it is a mobile or computer.
The main malicious programs are:
- Virus: are the most common malicious codes. They are able to spread easily on technological devices. They put computers to sleep, send spam, generate abnormal traffic and steal information, among other actions.
- logic bombs: also called “of time” they are a subtype of virus that have the peculiarity of being activated by means of a certain command executed by the user, when a date arrives or when a specific action is carried out. This causes devastating effects, which range from the deletion of files to its use for DDoS cyberattacks.
- worms: worms or computer worms are malware that have a great capacity to reproduce themselves without the need for user action. They hide in the automated functions of the OS to go unnoticed. In general, they are not easy to detect except when their reproduction affects the computer’s resources too much. They mainly aim to attack the network using email and programs to make copies of themselves.
- Trojans: its name is due to the Trojan horse of Mythology and is based on its particular harmless appearance and its ability to hide in some computer element. Therefore, the user confidently downloads it and inadvertently authorizes hackers to enter his entire computer. When executed, they generally destroy files, send data to remote sites, and gain full control of the computer.
- root kit: This refers to a group of software that nest in the OS to give remote access to an intruder. They are very elusive, which is why they usually go beyond the controls of antivirus and other security systems. Depending on the authorization level you have achieved, you may have access to all computer administration.
Ransomware
One of the most feared computer viruses due to its ability to “hijack” the device. As an obstacle, they impose an access password that only intruders know. With this they make sure that you cannot use your computer until you release funds or carry out the task that they indicate.
It is common for them to ask credit cards and bank account passwords, among other data. The key to their success is the computers without updates, with detectable vulnerabilities and without reliable antivirus. ransomware Petya Y Wannacry they are well known as those who have caused the most havoc.
Adware
If when you browse the net you find endless ads, pop-ups and pop-ups it is very likely that you are in the presence of adware software. Although many take it as a less harmful malware, it significantly affects the performance of the computer. It even gives rise to harmful spam and phishing.
spam

A spam is it a message or email for advertising or malicious purposes Usually shipped in bulk. Through this method, the frauds of the Phishing. That’s not counting the thousands of viruses it spreads to devices. Therefore, far from being harmless emails that fill your mailbox, they are more dangerous than they seem. Try to remove them immediately. every time you see one in some folder of your mail.
phishing
Widely used to execute financial fraud, Phishing disguises an email as coming from a legitimate source and installs the malicious code on your device. They can pass themselves off as banks, insurance or public services to generate confidence in the user who will open the mail. In this way, they manage to access private data that may be sensitive in aspects personal and financial. It is considered a class of Spam.
Social engineering
They are a broad set of practices that seek to exploit the weaknesses in the business human component. They appeal to the desire for growth and look for weaknesses to extract relevant corporate information. Yet they profit from employees’ computer inexperience and job dissatisfaction. Later use other techniques to access the network and thus obtain benefits.
Advanced Persistent Threats
also called ATPs. Contrasting with those random attacks, ATPs are highly organized hacking strategies. They are characterized by exploring with time the vulnerabilities of a certain entity to develop tailored malware so that they can penetrate the protection barriers.
Using in turn social engineering techniques to achieve their goals, direct their “computer assault” with the help of a human component that is responsible for monitoring its progress. This helps to correct deviations and thus be able to continue obtaining for a long period. data and cause damage.
DoS and DDoS attacks
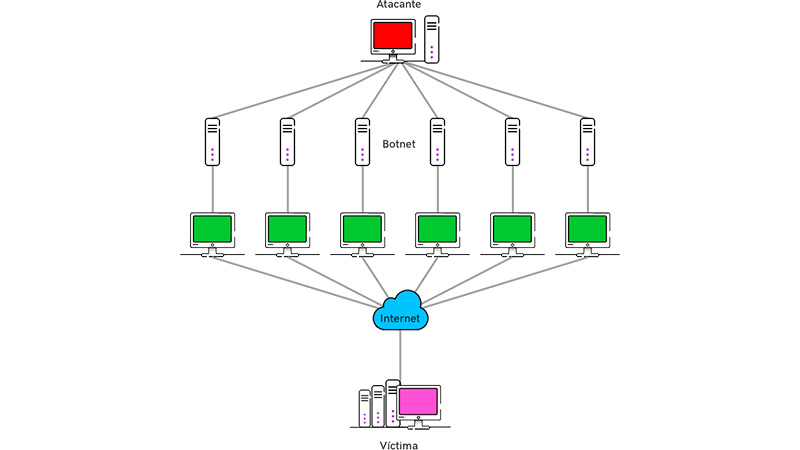
In this kind of server intrusion it is observed a continuous denial of services to those users who have legitimate access. With this it is possible to hinder different actions. For example, online shopping, cloud platforms or services. Logically, every minute with the server down generates monetary losses.
Its operation is based on flood the hosting with requests to overload the server and in this way to the websites that are hosted on them. This prevents normal operation by denying access to people who want to enter as they always do. while the threat Two is carried out from a single machine, the DDoS act different.
This latest cyberattack can use the famous “zombie network” or “Botnets” which are a set of infected computers that constantly attack. Since this overloaded traffic is carried out from multiple computers scattered around the world, it is more complicated to exterminate. It should be noted that the targets always in sight are online stores and casinos. Without forgetting the companies that use their website to sell.
Brute force
This is one of the most classic modalities where the attacker employs various tools to crack a user key. Using dictionary or inverse techniques, they try combinations until they find the correct password, giving the cracker access to banking platforms, online services, files, WiFi networks and encrypted files.
In fact, they have specialized in creating automated software such as John the Ripper, Brutus either THC Hydra for easy identification of credentials. That is why, when users create a weak password or repetitive increases the risk of being attacked. An example of this is the stuffing where they use username and password games.
sniffing
Another technique that has undermined cybersecurity is sniffing. With it the malicious agents They use a software or hardware component to “listen” for web traffic. only the advanced encryption tactics can make this danger disappear from an infected computer or mobile.
trashing
Until the data you discard can be used against youthis is the origin of the term trashing. This cyber attack refers to a computer-type crime that extracts personal or private data directly from the recycle bin. Therefore, every password, browsing history or file that passes through there could be analyzed by intruders.
farming
Such a method of cybercrime goes unnoticed by most people. The farming is the action of lure visitors to tainted or fraudulent websites. They generally use redirection from secure web pages, and by doing so they trick the unsuspecting visitor into giving up valuable personal information.
Intrusion into Cloud services

Most companies do not stop to make a proper study of the cloud technologies next to the CSPs. Cloud services are still considered as means that can be vulnerable to cybercriminals due to the possibility that exists in this type of data hosting. For this reason, you must know what security measures your provider takes before storing data there. For this reason, it is always advisable to use supports known as OneDrive either iCloud.
manipulation of social networks
The social networks that exist can make you become one victim of information manipulation through a cyber attack. For experienced hackers it is quite easy to enter one of them and extract the information they want.
of course these they obtain files, data or images that they later manipulate at will they can be protected if you take the time to shield your account and follow the advice that we always mention. You must take this seriously because it is at stake your own reputation and the image of your family or your company. Not counting the legal sanctions or economic problems that this could lead to.
MITM (Man in the middle)
Through this strategy an intermediary is placed (the virtual criminal himself or a malware) between the data source and the attacked user to perform any cyber attack they want. They can be from spoofing, the kidnapping of SSL, the HTTPS Spoofing or the IP Spoofing. It is best to prevent with an armored security system totally reliable and always browse with HTTPS protocols.
Informatic security