
Index:
UPDATED ✅ Do you want to learn about the different techniques used in computer security? ⭐ ENTER HERE ⭐ and find out what they are ✅ EASY and FAST ✅
Security, security, security. This is undoubtedly one of the biggest concerns of any Internet user in the world. It is normal, Nowadays, computers and smartphones have become so essential that we store extremely intimate information on them..
Fortunately, there is a sector that specializes precisely in our security when using any device: cybersecurity. Thanks to it there are firewalls, antivirus and other programs for the protection of your computers against attacks of any kind.
In this article we are going to talk about the main strategies used by professionals to keep their computers safeso that you can follow the example to do the same on your computer either on a smaller or larger scale.
What is computer security and what is it for?
The cybersecurity or computer security Information security is an area that focuses on the protection of data stored on a computer or flowing through a computer network. This is responsible for guaranteeing 3 fundamental things: the privacy of the data, the encryption of these and above all keep them out of risk of being damaged.
Data privacy is a matter of life or death in computing, since the information we store on our computer can only be seen by us, and anyone who wants to do so must have our consent. This usually involves encrypting the data so that anyone trying to acquire it must first decrypt it..
On the other hand, it is important to keep the data away from viruses or other factors that can damage it, making it unreadable by any program on the computer. This is very important, since a damaged data can cause a chain reaction that affects the operation of a softwarean operating system and even the entire computer.
Types of computer security: What are they and what does each one guarantee?
There are several types of computer security, since it has diversified to provide support in everything that has to do with the computer as computer equipment.
Here we tell you what they are and what each one specializes in:
software security
When computers were born, so was the concept of software security. It could be said that this is the main computer security since it focuses on protecting the programs and the files that make up these. Over the years it has evolved to the point that each software has its own data protection systemthanks to certain internal protocols of this.
hardware security
Over the years, we realized that it wasn’t just the software that needed protection, but the hardware as well. Many people who hear the term think that it strays from the main idea of cybersecurity.but the reality is that it could not be more related.
One of the most important terms in digital information security is undoubtedly firewalls. These were created to control the flow of data that goes through the hardware, so that it has to make less effort and have greater control over the data it handles to increase its security.
online security
Finally, there is that cybersecurity that is responsible for keeping us protected from the dangers of the internet. It is thanks to this that tools such as antiviruses begin to be developed, to protect data from malicious files that can damage it, and antispyware, to keep those who want to snoop on it at bay.
It is in this where the purest essence of computer security is found, and it is also the one that has been studied the most since the term was invented.
What are the main strategies used in digital security and their benefits?
A word that perfectly defines what computer security is is “strategy”. The reality is that this area is based on a set of strategies that reinforce each other to keep a computer or network of these completely safe in every way.
Here we present what are the main security strategies that you should take into account and you can never ignore:
Information Backup
One of the most used techniques in the world of information security is undoubtedly its backup. Think wisely. If you’re going to keep the evidence of a trial safe, the first thing you should do is back them up in a safe place with a backup. This is precisely what is done with this strategy.
The idea is simply to take the most important data (they all are) and make a copy of it and save it to a safe place that can later be accessed to recover the data that is necessary.
This idea is simple and quite effective, but to be efficient it must have the following characteristics:
- Automatic: a data backup system must be able to be performed continuously automatically every so often. Larger companies need this to be done on a daily basis.
- Encryption: To keep the information completely safe after the backup, it is important that these are encrypted so that no unauthorized third party can access them.
- Remote: it is also vital that the backed up data is stored remotely in a location off the main computer. Currently, one of the most used is cloud storage.
- Access to old versions: Finally, the user must be able to access previous versions of the backed up information. For example, if you have a document in Excel, it is backed up, then the next day you modify it, and the system makes another copy. The idea is that you can also have access to the version of the backup which was done before it was edited.
These are just some basic features to consider when choosing a backup system. Obviously there are programs that offer certain extras that make them even safer.
malware protection
A constant threat in the computer world are viruses or malicious files, which can cause many problems in a database, both for raw information (videos, photos, audio), and for the data that makes up a program or File System.
In this sense, the most important elements to take into account are:
- Anti virus: antiviruses are programs specially developed to detect malicious files that try to enter our computer, blocking them and sending them directly to a safe location where they are not spread (quarantine), to later eliminate them. They are very complex and are made up of other security elements such as firewalls.
- software control: another thing important is to have more control over the installed programs. If we have only the tools we need on our computer, and not one that we use once every 2000 years, we will undoubtedly be more protected against threats.
spy protection

Antispyware are those that specialize in preventing a third party, by means of a virus, from having access to the information on our computer, a constant threat especially when we surf the Internet.
To meet this goal, priority is given to:
- wired networks: old school hackers used to be close to server buildings and with certain devices connected to network cabling, intercept its communications. Currently this method is less used, but it is still a threat, so it is important to secure physical communications.
- Wireless networks: In the new school, with the rise of wireless connections, hackers They use devices to intercept the signal and obtain the data that flows through it.so it is extremely important to ensure this as well.
data cleansing
This cybersecurity strategy is based on the theory that some data is more sensitive than others, which in turn makes it more vulnerable to attacks of all kinds. That is why what is involved in this sense is to clean the system of these files that may represent a risk to the security of others.
In this sense, one of the most related terms is what is known as “secure erase”, which is based on simply eliminating irrelevant data that does not represent a serious loss of information for the company or the system as such.
System monitoring and analysis
Finally, there is the constant analysis of the system to verify that there are no vulnerabilities in it, so a program is necessary to take care of it. This is such an essential strategy, many programs such as antivirus or antispyware have their own risk analysis and reporting system.
Steps to configure the security of your computer and make it impossible to hack
Although in the previous step we named the different cybersecurity strategies separately, it is important that you know that applying only one of them is not enough. To have a perfectly insured device it is necessary to apply all of them, or at least most of them.
Based on this, we are going to teach you how to apply several of these strategies on your computer or mobile, in order to have a top-level personalized security system. In this way the information of all your devices will be more than assured.
Set a password
This is one of the things that computer users ignore, but it is very childish to try to apply cybersecurity to your computer when anyone can access it just by turning it on. Therefore, the first thing you should do is set a user lockso that every time someone wants to use the equipment, they run into this barrier.
With the mobile we are much more aware and almost 100% of users have the screen lock active. This is the first line of defense between prying eyes and your private information.
In this sense, mobile devices have come a long way, offering various ways of unlocking such as:
- PIN: allows you to set a password 4 numeric digits to unlock the smartphone screen. It is a very basic concept, like that of your bank’s debit cards, and therefore it is also the weakest.
- Password: it allows you set a code that can combine numbers, letters and symbols and have the extension what you wish. It is also a very basic concept, but if a good password is devised it can become one of the most secure.
- Pattern: It shows you nine points on the screen that you must join in a sequence, without having to touch a previous point again. Its security is intermediate, since the number of possible pattern combinations is quite limited.
- face unlock: it allows you scan your face to unlock screen. At the time it was an experiment and the sensors were not as reliable, but today they are much more precise.
- Fingerprint: it allows you register your fingerprint to unlock the screen. Current sensors are very accurate and it is by far the safest method of all.
In this way you will have established a protection mechanism against those who want to snoop on your smartphone, a full-fledged antispyware, or at least one of its most important elements.
Install antivirus
The next thing is to protect your information against those malicious files. For this you will need the most symbolic program of computer security such as an antivirus. At the time these were exclusive to computers, but the most famous developers now also have a mobile version.
The ideal in this sense is to have an antivirus from the same developer for PC and mobile, since some are even including synchronization and remote access functions between devices of the same owner. Some of the brands that have a presence in both devices are:
- Avira Antivirus: on desktop it offers a complete program that offers antispyware and other functions to make your computer a fortress. On mobile, its reputation is not as well known, but it allows you to protect your device from any threat you download, and allows you to customize other security elements such as screen lock.
- McAfee: one of the most important computer security firms in the world, with it you can keep all your devices fully secured and receive reports from each of them constantly.
- AVG Antivirus: For several years now, it has been one of the best computer security programs in the world, allowing you to keep all your computers free of viruses and other threats.
check firewall
Firewall or firewall is one of the first lines of defense against viruses. It is important that it is always active since it identifies threats as if it were an antivirus. In Windows what you should do to check it is:
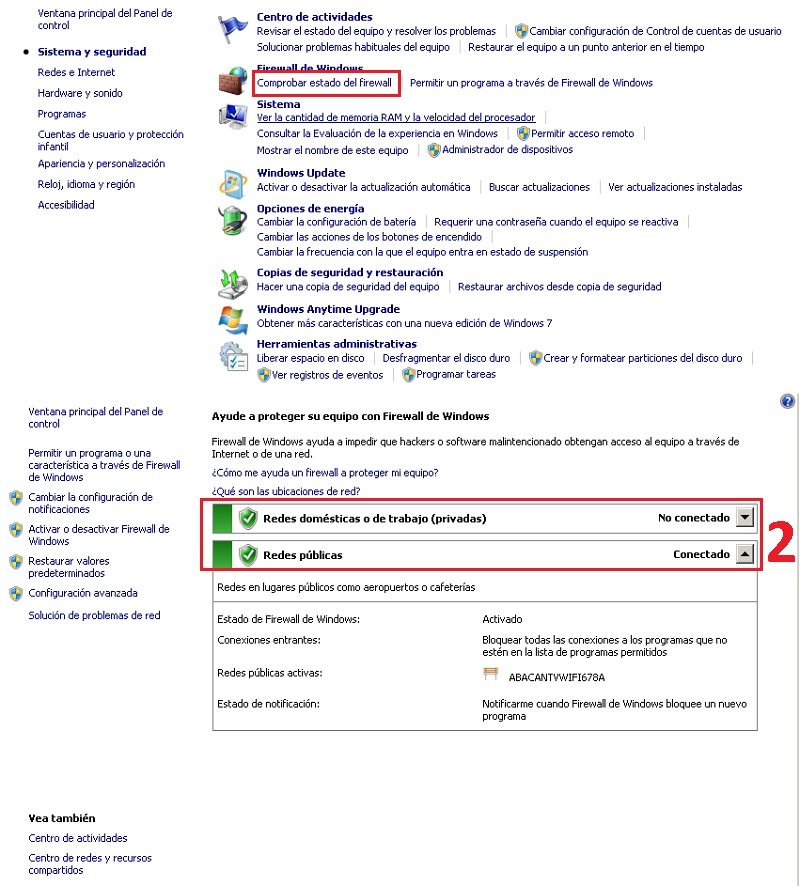
- Go to the “Control Panel” and go to “Security system“.
- Later you must touch in the section “Windows firewall”.
- After that you will be directed to a screen in which you can see the status of the firewall as you see in the image.
Optimize device
At this point, what it is about is keeping the equipment at its maximum capacity, so that it is less vulnerable to failures. To do this you will have to carry out actions as essential as cleaning your computer and smartphone. In this sense, there are programs like CCleaner that will help you in this task perfectly.
Informatic security